-
Cisco IP Solution Center Traffic Engineering Management User Guide, 4.0
-
Index
-
About This Guide
-
Introduction to ISC TEM
-
Setting Up the Service
-
TE Network Discovery
-
TE Resource Management
-
Basic Tunnel Management
-
Advanced Primary Tunnel Management
-
Protection Planning
-
Traffic Admission
-
Administration
-
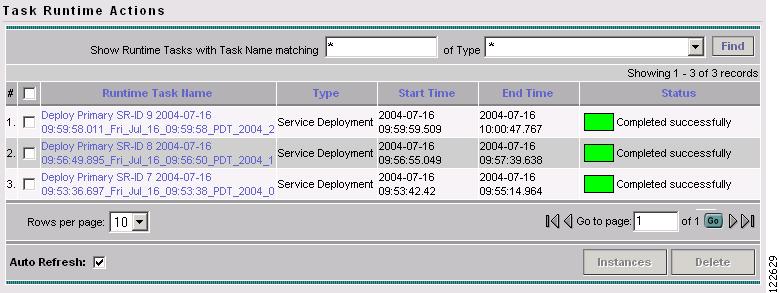
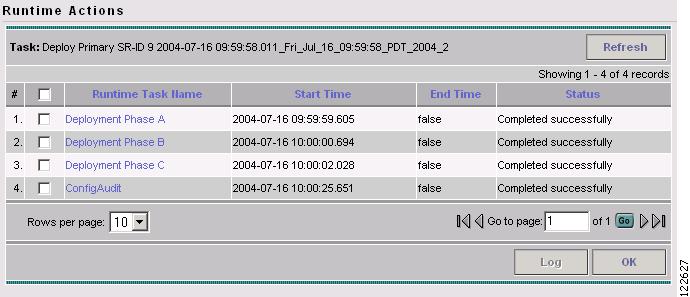
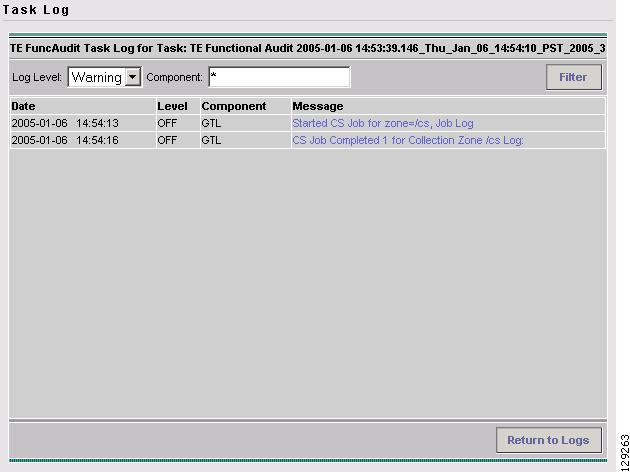
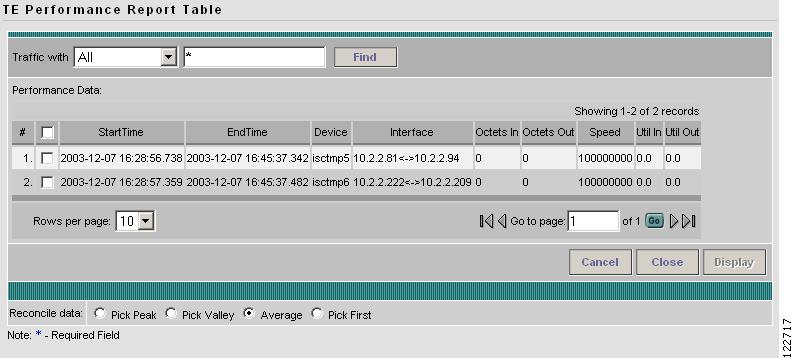
Task Monitoring
-
TE Topology
-
Traffic Engineering Management GUI
-
Warnings and Violations
-
Document Type Definition (DTD) File
-
Table Of Contents
Traffic Engineering Management GUI
Accessing Protection Management
View Managed Primary Tunnel Details
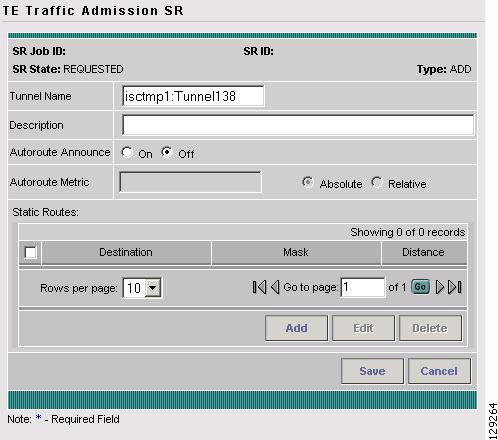
Create TE Managed Primary Tunnel SR
Edit TE SR (Primary or Backup)
Movable Tunnel Selection Window
TE Primary Tunnel Computation SR - Changes Window
TE Primary Tunnel Computation Results - Report
Create TE Backup Tunnel Window
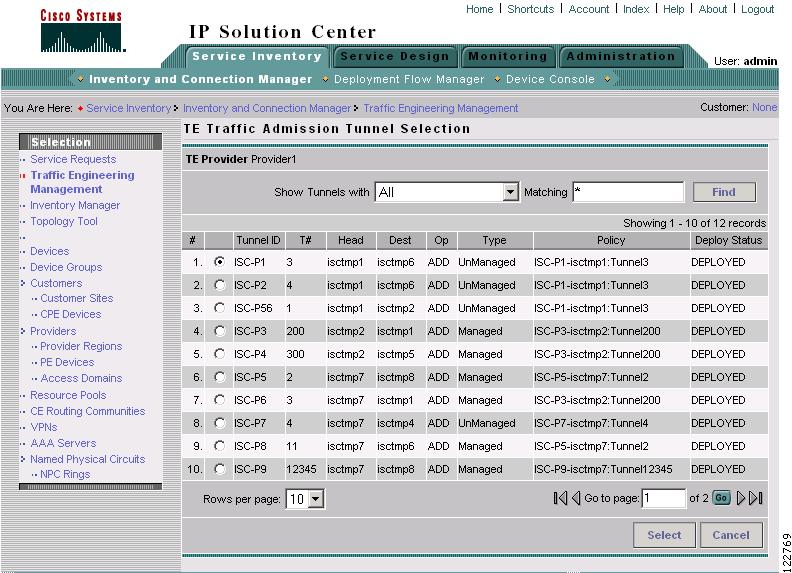
Select TE Tunnel for Admission
Traffic Engineering Management GUI
This chapter describes the Cisco IP Solution Center Traffic Engineering Management (ISC TEM) GUI and provides an explanation of the various fields, buttons, and other GUI elements. For a detailed description of the process flows for the various ISC TEM services, see the respective chapters and sections elsewhere in this user guide.
In this chapter, the parts of the ISC GUI used by the ISC TEM component are described:
Accessing the TEM GUI
The Traffic Engineering Management GUI forms part of the general Cisco ISC GUI.
This section describes the GUI elements in the Traffic Engineering Management Services window.
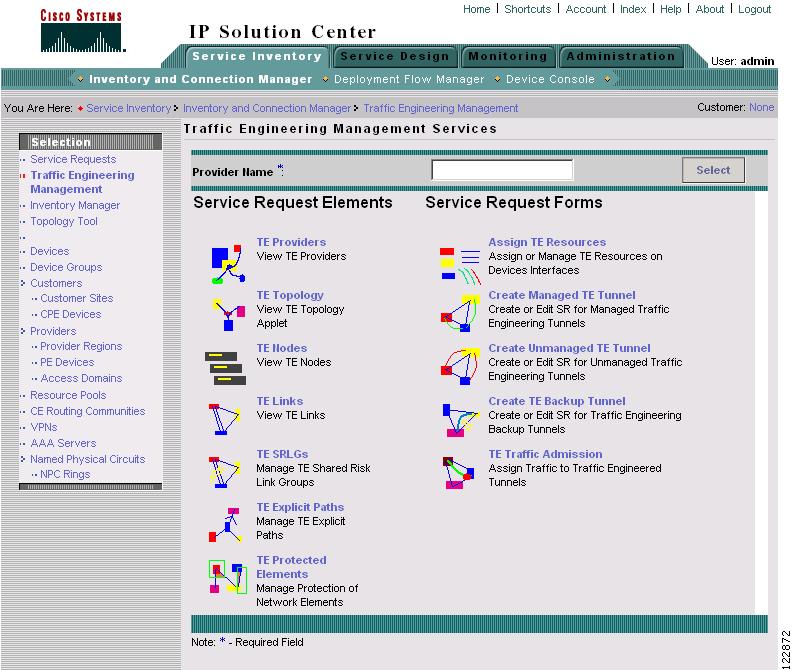
To access the TEM GUI, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management. The Traffic Engineering Management Services window in Figure A-1 appears.
Figure A-1 Traffic Engineering Management Services
The main ISC TEM window includes the following service elements:
•
Service Request Elements
–
TE Providers—Create and manage TE Providers.
–
TE Topology—View the ISC TEM application through a topology interface.
–
TE Nodes—View TE nodes and node details.
–
TE Links—View TE links.
–
TE SRLGs—Create and manage Shared Link Risk Groups (SRLGs).
–
TE Explicit Paths—Create and manage TE explicit paths.
–
TE Protected Elements—Manage protection of network elements.
•
Service Request Forms
–
Assign TE Resources—Assign or manage TE resources on device interfaces.
–
Create Managed TE Tunnel—Create or edit SRs for managed TE tunnels.
–
Create Unmanaged TE Tunnel—Create or edit SRs for unmanaged TE tunnels.
–
Create TE Backup Tunnel—Create or edit SRs for TE backup tunnels .
–
TE Traffic Admission—Assign traffic to traffic-engineered tunnels.
TE Providers
This section describes the GUI elements in the TE Providers tool.
To create a TE Provider, see Creating a TE Provider.
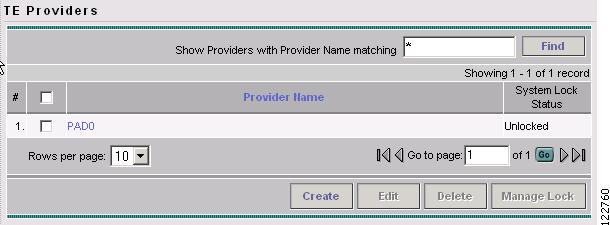
To access the TE Providers window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Providers. The TE Providers window in Figure A-2 appears.
Figure A-2 TE Providers
The TE Providers window contains the following fields:
•
Provider Name—Name of TE provider.
•
System Lock Status—Indicates whether or not the system lock is activated (Locked or Unlocked).
The following actions can be performed:
•
Create—Create a TE provider.
•
Edit—Edit the TE provider details.
•
Delete—Delete a TE provider.
•
Manage Lock—Manage the system lock status (see Manage Lock, page 9-18).
Create/Edit TE Provider
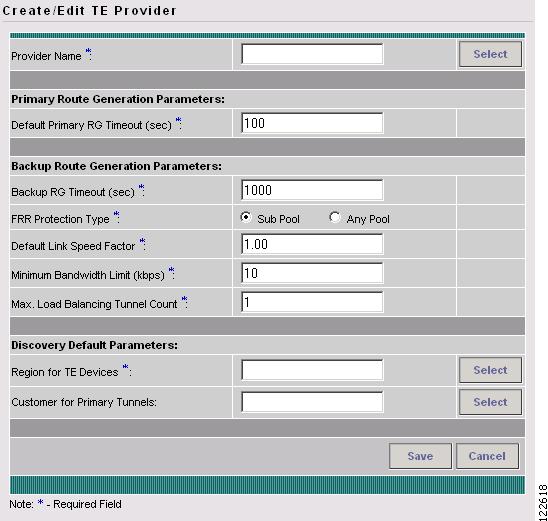
To access the Create/Edit TE Provider window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Providers and click Create.
The Create/Edit TE Provider window in Figure A-3 appears.
Figure A-3 Create/Edit TE Provider
The Create/Edit TE Provider window contains the following fields:
•
Provider Name—Name of the provider to be associated with the TE provider.
•
Default Primary RG Timeout—Default computation timeout for primary tunnels.
•
Backup RG Timeout—Computation timeout for backup tunnels.
•
FRR Protection Type—Fast Re-Route (FRR) protection type:
–
Sub Pool—Bandwidth section nested inside the Global Pool part of the total bandwidth.
–
Any Pool—Sub Pool or Global Pool. Global Pool is the section of the total link bandwidth containing all Sub Pools for the link.
•
Default Link Speed Factor—Default multiplication factor to be applied to the link speed in order to determine the amount of bandwidth that needs to be protected.
•
Minimum Bandwidth Limit—Minimum bandwidth allowed for backup tunnels.
•
Max. Load Balancing Tunnel Count—Maximum number of tunnels to be generated for protecting an element.
•
Region for TE Devices—Name of provider region.
•
Customer for Primary Tunnels—Customer for primary TE tunnels.
For step-by-step instructions on how to create or edit TE providers, go to Creating a TE Provider.
TE Topology
This section describes the various fields, buttons, and other GUI elements in the TE Topology GUI. For instructions on how to use the TE Topology tool, see Chapter 11, "TE Topology".
ISC TEM includes a TE Topology tool that is accessed as a TE Topology Interface Applet that displays the TE topology through a Java applet within the browser.
For specific instructions on how to use the topology applet, see Using the TE Topology Interface Applet, page 11-2.
Note
There are several ways to access the TE Topology tool, among others by using Inventory and Connection Manager > Topology Tool and Inventory and Connection Manager > Traffic Engineering Management > Topology Tool. In this section, it is assumed that the TE tools are accessed from the Traffic Engineering Management Services page.
Topology Display
To access the TE Topology tool, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Topology and select ISC-TEM Topology Interface Applet
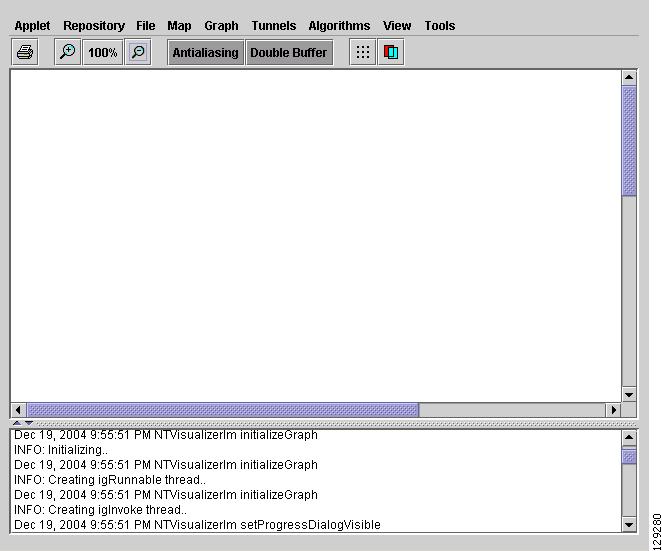
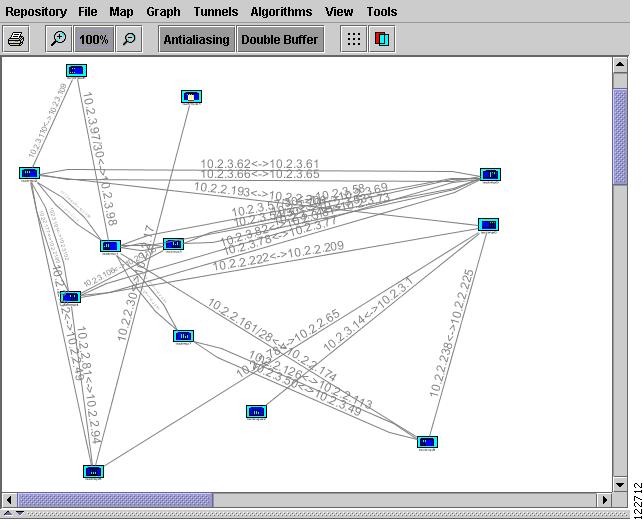
The topology display appears immediately as an separate window as shown in Figure A-4.
Figure A-4 Topology Display Window
The Topology Display window contains the following menus:
•
Repository—Discard or save the layout graph.
•
File—Gain access to the print functionality.
•
Map—Load or clear maps. Is used to associate a map with a view.
•
Graph—Access a range of tools to manage and manipulate graphs.
•
Tunnels—View or update the tunnel layout.
•
Algorithms—Randomize or optimize links and set spring settings.
•
View—Modify the zoom level in the current view.
•
Tools—Modify the magnetic grid settings and the layer visibility.
The menus in the Topology Display window are described in more detail below with definitions for individual entries.
The Topology Display window toolbar contains the elements shown in Table A-1.
For instructions on how to use the Topology Display, see Using the TE Topology Interface Applet, page 11-2.
Repository
The Repository menu in Figure A-5 serves to discard or save the layout graph.
Figure A-5 Repository Menu
The Repository menu contains the following elements:
•
Layout Graph—If a graph layout is already present, the layout is cleared. If not, the layout of the elements in the repository is drawn. If a layout has previously been saved, the saved layout is re-created. Otherwise, a random layout is generated.
•
Save Graph Layout—Save the current graph layout. Doing so ensures that whenever the graph layout is cleared with Layout Graph or the Topology Display applet is closed, the same layout is created when the applet is restarted.
File
The File menu in Figure A-6 provides access to the print functionality.
Figure A-6 File Menu
The File menu contains the following element:
•
Print—Print the current topology view.
Map
The Map menu in Figure A-7 serves to load or clear maps.
Figure A-7 Map Menu
The Map menu contains the following elements:
•
Load—Opens the Map Chooser for selecting a topology map.
•
Clear—Clears the current topology map.
Load Map
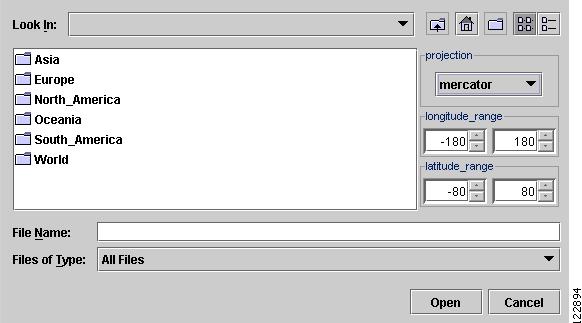
When selecting Load from the Map menu, the Map Chooser window in Figure A-8 appears.
Figure A-8 Map Chooser
The Map Chooser window contains the following elements:
•
Look In—Change the location from where to load the map.
•
File Name—Specify the desired file name.
•
Files of Type—Select the file type of the files to be displayed.
•
Open—Open the selected directory or a topology map.
•
Cancel—Close the Map Chooser window.
•
File Dialog Commands—Serves to determine the desired directory and level of detail of data files.
The Map Chooser window navigation toolbar contains the elements shown in Table A-2.
•
Projection—Choose the projection in which a map is shown. A map projection is a projection which maps a sphere onto a plane. Typical projections are Mercator, Lambert, and Stereographic.
•
Longitude Range—Choose a geographical longitude range.
•
Latitude Range—Choose a geographical latitude range.
Graph
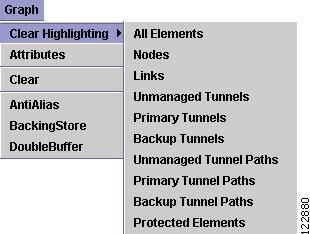
The Graph menu in Figure A-9 provides access to a range of tools to manage and manipulate graphs.
Figure A-9 Graph Menu
The Graph menu contains the following elements:
•
Clear Highlighting—Remove the highlighting of selected elements in the graph layout:
–
All elements—Highlighting of all network elements in the graph is cleared.
–
Nodes—Highlighting of all nodes in the graph is cleared.
–
Links—Highlighting of all links in the graph is cleared.
–
Primary Tunnels—Highlighting of all primary tunnels in the graph is cleared.
–
Backup Tunnels—Highlighting of all backup tunnels in the graph is cleared.
–
Unmanaged Tunnel Paths—Highlighting of all unmanaged tunnel paths in the graph is cleared.
–
Primary Tunnel Paths—Highlighting of all primary tunnel paths in the graph is cleared.
–
Backup Tunnel Paths—Highlighting of all backup tunnels paths in the graph is cleared.
–
Protected Elements—Highlighting of all protected elements in the graph is cleared.
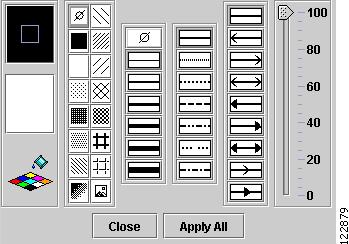
•
Attributes—Opens the Graphics Attributes window in Figure A-10.
Figure A-10 Graphics Attributes Window
To understand the tools in the Graphics Attributes window, mouse over the various attributes. Choose the desired settings for line color, fill color and pattern, line thickness and style, arrow, and transparency.
Click Apply All to activate your selections or Close to quit the Graphics Attributes window.
•
Clear—As opposed to the Layout Graph item in the Repository menu, which also clears the current graph from the topology display, the Clear function in the Graph menu only clears the graph from the current view without re-creating it.
•
AntiAlias—Activate antialiasing to smooth lines in the layout.
•
BackingStore—Store graphics content when moved to the background and regenerate it when moved to the foreground. This helps avoid superfluous refreshing.
•
DoubleBuffer—Start/stop double buffering. Smoothes the lines when dragging elements.
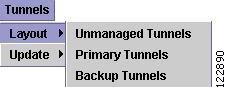
Tunnels
The Tunnels menu in Figure A-11 is used to highlight TE tunnels in the network.
Figure A-11 Tunnels Menu
The Tunnels menu contains the following elements:
•
Layout—Use Layout the first time you want to highlight tunnels using the repository.
–
Unmanaged Tunnels—Highlight unmanaged tunnels only.
–
Primary Tunnels—Highlight primary tunnels only.
–
Backup Tunnels—Highlight backup tunnels only.
Note
Selecting Layout repeatedly does not update the display.
•
Update—Use Update to update tunnels in the display with the last instance of the repository.
–
Unmanaged Tunnels—Update the highlighting of unmanaged tunnels.
–
Primary Tunnels—Update the highlighting of primary tunnels.
–
Backup Tunnels—Update the highlighting of backup tunnels.
Algorithms
In the Algorithms menu in Figure A-12 various algorithms can be used to enhance and otherwise alter the graph layout.
Figure A-12 Algorithms Menu
The Algorithms menu contains the following elements:
•
Spring—Applies the Spring algorithm to the current graph layout using the attribute settings in the Spring Settings window.
•
Randomize—Applies the Randomize algorithm to the nodes in the current topology layout.
•
Optimize Links—This feature is used to move overlapping links apart when multiple links are present between nodes using the Links Optimization algorithm.
•
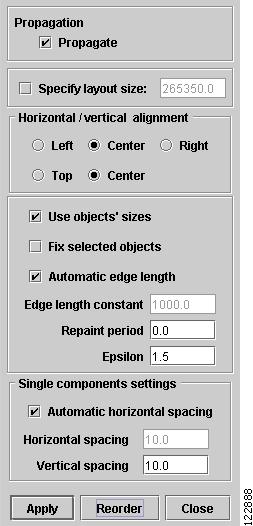
Spring Settings—The spring settings are used to enhance the appearance of the topology display by setting attributes according to user preferences. When selecting Spring Settings, the Spring Settings window in Figure A-13 appears.
Figure A-13 Spring Settings
The Spring Settings menu contains the following elements:
•
Propagate—Propagate the various settings in the Spring Settings window to all child layouts.
•
Specify layout size—Specify the layout size in pixels.
•
Horizonal / vertical alignment—Align the topology graph in the Topology Display.
•
Use objects' sizes—Use the objects' actual layout sizes without scaling.
•
Fix selected objects—Fix the location of selected objects in the Topology Display.
•
Automatic edge length—Allow the topology application to automatically assign an appropriate length to each link.
•
Edge length constant—If Automatic edge length is not selected, you can specify a fixed edge length here.
•
Repaint period—Sets the period (number of loops) used to repaint objects when the objects are being laid out in a graph.
•
Epsilon—The epsilon constant determines when the iterative process for the Spring algorithm should stop. The greater this constant, the faster the layout, but the more distant the final position from the optimal layout.
•
Automatic horizontal spacing—Let the topology application automatically determine the horizontal spacing between the devices in the graph.
•
Horizontal spacing—Specify a fixed horizontal spacing between the devices in the graph.
•
Vertical spacing—Specify a fixed vertical spacing between the devices in the graph.
Once you have made your selections, you can do any of the following:
•
Apply—Save the Spring settings.
•
Reorder—Rerun the Spring algorithm to reorder the graph elements based on the Spring settings.
•
Close—Close the Spring Settings window without saving the selections.
View
The View menu in Figure A-14 allows zooming in the current view.
Figure A-14 View Menu
The View menu contains the following elements:
•
Zoom In—Increases the magnification level.
•
Zoom Normal—Resets the magnification level to the default setting.
•
Zoom Out—Decreases the magnification level.
Tools
The Tools menu in Figure A-15 allows you to modify the magnetic grid settings and the layer visibility. Different network elements are drawn in different layers. Individual layers can be turned on or off using the Layers menu.
Figure A-15 Tools Menu
The Tools menu contains the following elements:
•
Grid—Allows you to add a background grid to the graph based on the selections in the Magnetic Grid window.
•
Layers—Allows you to select the layers to be dispayed in the graph using the Layer Visibility window.
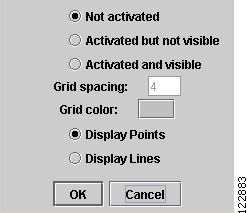
Grid
The Magnetic Grid window in Figure A-16 allows you to modify the magnetic grid settings. An activated grid appears under the graph layout in the Topology Display.
Figure A-16 Magnetic Grid
The Grid window contains the following elements:
•
Not activated—Tells the application not to place a magnetic grid in the Topology Display.
•
Activated but not visible—The network elements are not visible but still snaps to grid.
•
Activated and visible—Make the grid active and visible in the Topology Display.
•
Grid spacing—Set the spacing between the lines in the grid.
•
Grid color—Click the square to open the color palette to set the grid line color as described in Grid Color.
•
Display points—Display links using dotted lines.
•
Display lines—Display links using solid lines.
Click OK to apply the settings or click Cancel to cancel the operation and return to the Topology Display window.
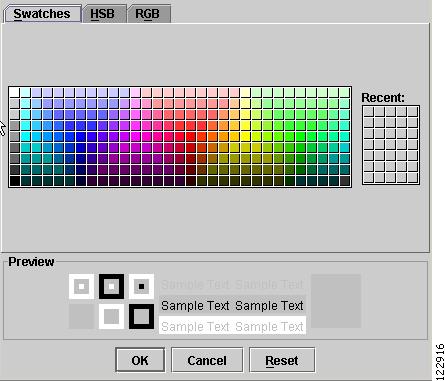
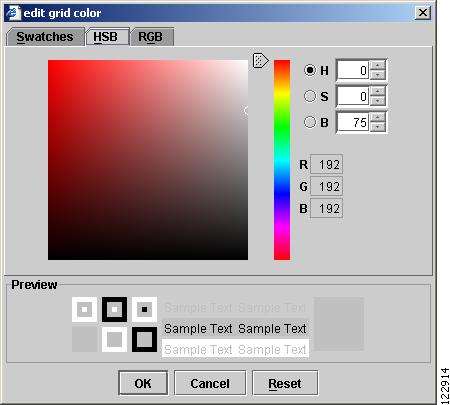
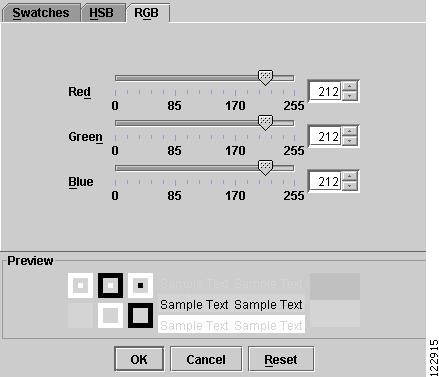
Grid Color
The Grid Color window in Figure A-17 has three tabs:
Swatches—The Swatches palette (shown) provides color swatches for making rapid color choices.
HSB—The HSB palette in Figure A-18 is used to set hue, saturation, and brightness.
RGB—The RGB window in Figure A-19 is used to set the color intensity for red, green, and blue, respectively.
Figure A-17 Edit Grid Color - Swatches
Figure A-18 Edit Grid Color - HSB Settings
Figure A-19 Edit Grid Color - RGB Settings
Make the desired changes and click OK.
Click Reset to reapply the default settings.
Layers
The various network elements are organized into layers that can be turned on and off to display only the part of the TE network that you want to see.
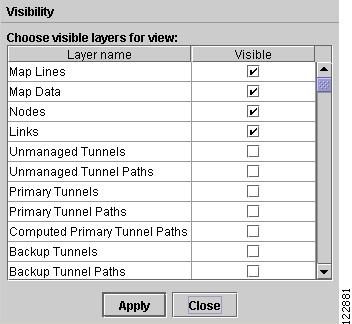
Select Tools > Layers to access the Layer Visilibity window shown in Figure A-20.
Figure A-20 Layer Visibility
In the Layer Visibility window, specify which layers should be visible by clicking the corresponding check boxes in the Visible column:
•
Map Lines—Select to display map lines.
•
Map Data—Select to display map data.
•
Nodes—Select to display TE nodes.
•
Links—Select to display TE links.
•
Unmanaged Tunnels—Select to display TE unmanaged tunnels.
•
Unmanaged Tunnel Paths—Select to display TE unmanaged tunnel paths.
•
Primary Tunnels—Select to display TE primary tunnels.
•
Primary Tunnel Paths—Select to display TE primary tunnel paths.
•
Computed Primary Tunnel Paths—Select to display paths for computed primary tunnels.
•
Backup Tunnels—Select to display TE backup tunnels.
•
Backup Tunnel Paths—Select to display TE backup tunnel paths.
Click Apply to apply the settings or click Close to cancel the changes and quit the Layer Visibility window.
TE Nodes
This section describes the GUI elements in the TE Nodes tool.
The nodes of the TE network can be viewed after running a TE Discovery task. For instructions on how to run a TE Discovery task, see Chapter 3, "TE Network Discovery."
The TE Nodes tool gives access to both textual and visual information about the nodes discovered in the TE network.
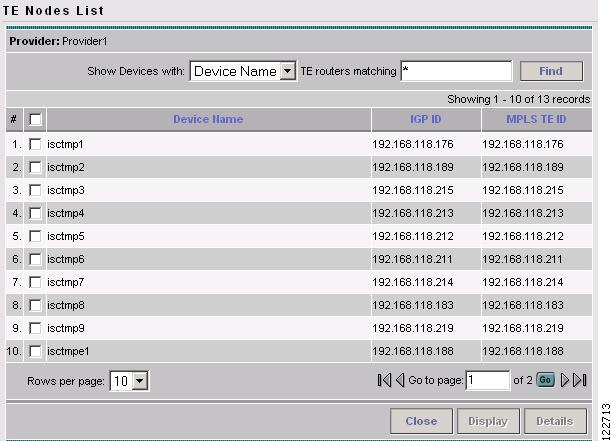
To access the TE Nodes window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Nodes. The TE Nodes List window in Figure A-21 appears.
Figure A-21 TE Nodes List
The following actions can be performed:
•
Close—Close the Topology Display, if open.
•
Display—Show the topology for one or more nodes in the TE network.
•
Details—Show details for a selected node.
•
Find—You can search for particular devices by selecting the device type in the drop-down menu Show Devices with and specify matching criteria in the TE routers matching field.
Display TE Nodes
The Topology Display can be invoked to highlight selected nodes.
Go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management. Click TE Nodes. Select one or more devices by clicking the corresponding check boxes. Click the Display button. The Topology Display applet in Figure A-22 appears.
Figure A-22 TE Nodes Topology Display
For a description of how to use the Topology Display features, see Topology Display.
View Node Details
To view the detailed information about a particular node, use the following steps, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Nodes.
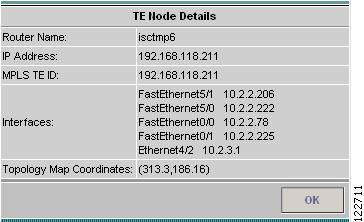
Select a device by clicking the corresponding check box. Click the Detail button. The TE Node Details window in Figure A-23 appears.
Figure A-23 TE Node Details
The TE Node Details window contains the following fields:
•
Router Name—Hostname of the router
•
IP Address—IP address of the router
•
MPLS TE lD—TE ID assigned by the router
•
Interfaces—TE interfaces on the routers
•
Topology Map Coordinates—Coordinates of the nodes in the Topology Display.
Click OK to close the TE Node Details window.
TE Links
This section describes the GUI elements in the TE Links tool.
The links of the TE network can be viewed after running a TE Discovery task. For instructions of how to run a TE Discovery task, see Chapter 3, "TE Network Discovery."
The TE Links window gives access to both textual and visual information about the links discovered in the network.
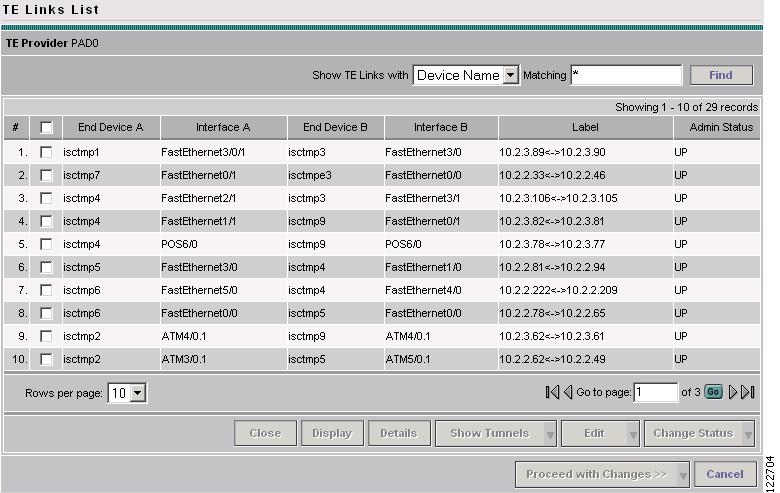
To access the TE Links window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Links. The TE Links List window in Figure A-24 appears.
Figure A-24 TE Links List
The columns in the links list table provides the following information:
•
End Device A—Hostname on endpoint A of the link.
•
Interface A—Interface name on endpoint A of the link.
•
End Device B—Hostname on endpoint B of the link.
•
Interface B—Interface name on endpoint B of the link.
•
Label—IP addresses of the interfaces on the link.
•
Admin Status—Indicates whether the link is UP or DOWN.
Note
This is local to ISC TEM. It is not the network interface status.
The following actions can be performed:
•
Close—Close the Topology Display applet if open.
•
Display—Open the Topology Display applet to visualize one or more links in the TE network.
•
Details—Show link details.
•
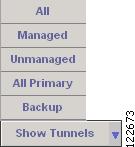
Show Tunnels—Display only tunnels that meet the following criteria (see Figure A-25):
–
All—Show all tunnels.
–
Managed—Show managed tunnels.
–
Unmanaged—Show unmanaged tunnels.
–
All Primary—Show all primary tunnels.
–
Backup—Show backup tunnels.
For more information about the Show Tunnels feature, see Show Tunnels.
Figure A-25 Show Tunnels Options
•
Edit:
–
Interface A—Edit the resources associated with interface A on the link.
–
Interface B—Edit the resources associated with interface B on the link.
•
Change Status:
–
Enable—Make a link active (UP in the Admin Status column).
–
Disable—Deactivate a link (DOWN in the Admin Status column).
•
Proceed with Changes >> (see Figure A-26): For verifying a committing resource change that might impact tunnel placement.
–
Tunnel Audit—If you disable an interface, Tunnel Audit checks if the status change affects Tunnel Placement.
–
Tunnel Repair—If Tunnel Audit reveals that Tunnel Placement is affected, Tunnel Repair can be used to move the tunnel away from the links to be disabled.
Figure A-26 TE Links List - Proceed with Changes
•
Cancel—Cancel the operation and return to the Traffic Engineering Management Services window.
•
Find—You can search for particular links by specifying a device type or a label in the drop-down menu Show TE Links with and specifying matching criteria in the Matching field.
Display TE Links
The Topology Display can be invoked to highlight selected links.
Go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Links. Select one or more devices by clicking the corresponding check boxes. Click the Display button. The Topology Display Applet in Figure A-4 appears.
For a description of how to use the Topology Display features, see Using the TE Topology Interface Applet, page 11-2.
For an explanation of the GUI elements in the TE Topology Display applet, see Topology Display.
View Link Details
To view the detailed information about a particular link, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Links. Select a device by clicking the corresponding check box. Click the Detail button. The TE Objects Details window in Figure A-27 appears.
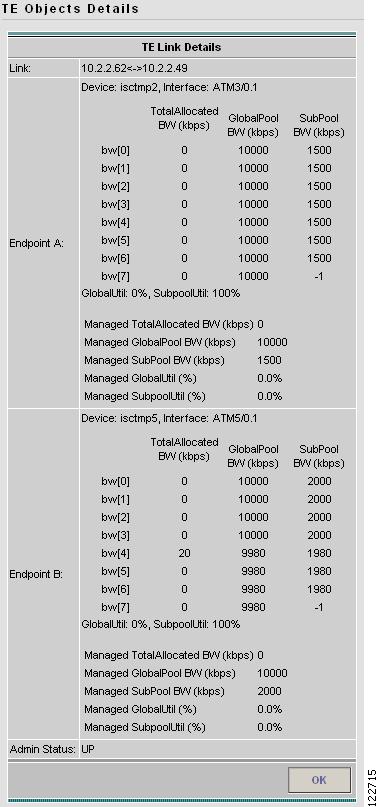
Figure A-27 TE Objects Details
The TE Links Details contains the following fields:
•
Link—IP addresses of Endpoint A and Endpoint B.
•
Endpoint A/Endpoint B:
–
Device—Hostname of the device.
–
Interface—Interface name.
–
TotalAllocated BW—The total amount of allocated bandwidth on the link by tunnel hold priority (bw[0]-bw[7]).
–
GlobalPool BW—The allocated Global Pool bandwidth on the link by tunnel hold priority (bw[0]-bw[7]).
–
SubPool BW—The allocated Sub Pool bandwidth on the link by tunnel hold priority (bw[0]-bw[7]).
–
GlobalUtil—Global Pool bandwidth utilization percentage.
–
SubpoolUtil—Sub Pool bandwidth utilization percentage.
–
Managed TotalAllocated BW—The total amount of allocated managed bandwidth (hold priority 0).
–
Managed GlobalPool BW—The total amount of allocated managed bandwidth (hold priority 0) in the Global Pool.
–
Managed SubPool BW—The total amount of allocated managed bandwidth (hold priority 0) in the Sub Pool.
–
Managed GlobalUtil (%)—Global Pool bandwidth utilization percentage for a managed tunnel.
–
Managed SubpoolUtil (%)—Sub Pool bandwidth utilization percentage for a managed tunnel.
•
Admin Status—Indicates whether the link is Up or Down.
Show Tunnels
This feature allows you to display which TE tunnels (primary and/or backup) a particular TE Link is using and helps facilitate the tunnel planning and placement processes. In addition, you can see which tunnels are impacted when an interface (or link) in the TE network is shut down.
To view specific types of tunnels using the Show Tunnels button, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Links. Select the desired link in the TE Links List (Figure A-24) and click Show Tunnels and select the type of tunnel you want to list.
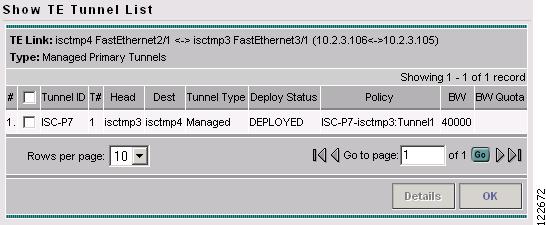
The Show TE Tunnel List window in Figure A-28 appears.
Figure A-28 Show TE Tunnel List
The TE Managed Primary Tunnels SR window contains the following elements:
The columns in the tunnel list provides the following information:
•
Tunnel ID—Unique tunnel identifier used within ISC TEM.
•
T#—Tunnel number on the head router.
•
Head—Hostname of the head router.
•
Dest—Hostname of the destination router.
•
Tunnel Type—Type of tunnel (managed or unmanaged).
•
Deploy Status—Tunnel deployment status.
•
Policy—TE policy for the tunnel.
•
BW—Tunnel bandwidth. If the tunnel is auto-bw enabled, BW shows the higher of tunnel bandwidth and maximum automatic bandwidth.
•
BW Quota—The amount of bandwidth this backup tunnel can protect. The router limits the LSPs that can use this backup tunnel so that the sum of the bandwidth of the LSPs does not exceed the specified amount of bandwidth. If there are multiple backup tunnels, the router will use the best-fit algorithm.
To view the tunnel details for a particular tunnel, select the tunnel in question and click Detail.
Figure A-29 Show Tunnels - TE Objects Details
For an explanation of the various GUI elements, see View Managed Primary Tunnel Details.
Edit Interface
To edit information about a particular link, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Links. Select the desired link in the TE Links List (Figure A-24). Click Edit > Interface A or Edit > Interface B to edit one of the interfaces on the link.
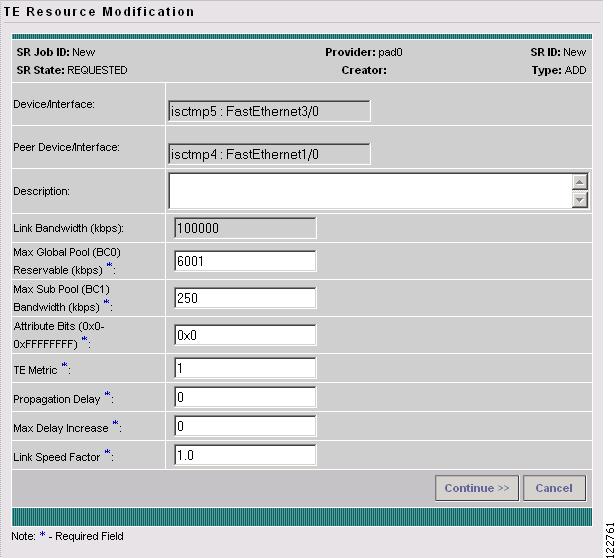
The TE Resource Modification window in Figure A-30 appears.
Figure A-30 TE Resource Modification
The TE Resource Modification window contains the following fields:
•
Device/Interface—Name of device and interface.
•
Peer Device/Interface—Name of device and interface for the other endpoint of the link.
•
Description—Service request description.
•
Link Bandwidth—Total bandwidth of the link.
•
Max Global (BC0) Reservable—Maximum amount of bandwidth, in kbps, that might be allocated by Resource Reservation Protocol (RSVP) flows.
•
Max Sub Pool (BC1) Bandwidth—Maximum amount of bandwidth in kbps to be reserved to a portion of the total. The range is from 1 to the value of Max Global Reservable.
•
Attribute Bits—Links attributes to be compared to a tunnel's affinity bits during selection of a path. Valid values are from 0x0 to 0xFFFFFFFF, representing 32 attributes (bits) where the value of an attribute is 0 or 1.
•
TE Metric—Metric used to override the Interior Gateway Protocol (IGP) administrative weight (cost) of the link.
•
Propagation Delay—The time it takes for traffic to travel along a link from the head interface to the tail interface.
•
Max Delay Increase—Used in computations of FRR backup-tunnels to constrain the propagation delay of a backup-tunnel for the link.
•
Link Speed Factor—Multiplication factor to be applied to the link speed in order to determine the amount of bandwidth that needs to be protected.
The following actions can be performed:
•
Continue >>—Proceed to the confirmation page shown in Figure A-31.
•
Cancel—Cancel the operation and return to the TE Links List window.
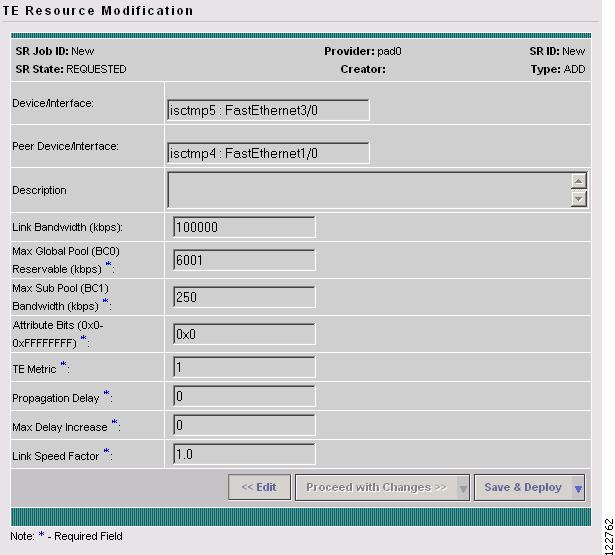
Figure A-31 TE Resource Modification (Confirmation Page)
The Confirmation Page provides a view-only snapshot of the SR data and offers the following options:
•
<< Edit—Return to the TE Resource Modification window.
•
Proceed with Changes >> (Figure A-32)—For verifying a committing resource change that can impact tunnel placement.
–
Tunnel Audit—If you change a resource, Tunnel Audit checks if the change affects Tunnel Placement.
–
Tunnel Repair—If Tunnel Audit reveals that Tunnel Placement is affected, Tunnel Repair can be used to move the affected tunnel.
Figure A-32 TE Links List - Proceed with Changes
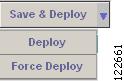
•
Save & Deploy (Figure A-33)—For committing resource changes that do not impact tunnel placement. There are two options for saving and deploying the resource modification SR to the network:
–
Deploy—Use Deploy when the service request state is Requested or Invalid. This places the Resource Modification SR in the deployment queue.
–
Force Deploy—Use Force Deploy when the service request state is Deployed or Failed Audit. This could be useful when the provisioning failed, so that you need to force through the deployment of the Resource Modification SR for this provider to the network.
Figure A-33 TE Links List - Save & Deploy Tunnels
TE SRLGs
This section describes the GUI elements in the TE SRLGs tool. It is used to manage Shared Risk Link Groups (SRLGs) as part of ISC TEM protection management.
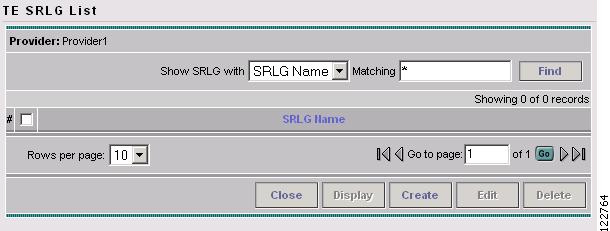
To access the TE SRLGs window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE SRLGs. The TE SRLG List window in Figure A-37 appears.
Figure A-34 TE SRLG List
The TE SRLG List window lists SRLGs by name.
The following actions can be performed:
•
Close—Close the Topology Display.
•
Display—Open the Topology Display applet to visualize the SRLG.
•
Create—Create an SRLG.
•
Edit—Edit an SRLG.
•
Delete—Delete one or more SRLGs.
•
Show SRLG with—You can search for particular SRLGs by specifying matching criteria in the Matching field and clicking Find.
Create/Edit TE SRLG
This section describes the GUI elements in the TE SRLG Editor, which is used to both create and edit SRLGs.
The process of creating an SRLG is described in Create SRLG.
To access the TE SRLG Editor, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE SRLGs. In the TE SRLGs window, to create an SRLG click Create or to edit or select an SRLG that you want to edit by clicking the corresponding check box and clicking Edit.
In either case, the TE SRLG Editor window in Figure A-35 appears.
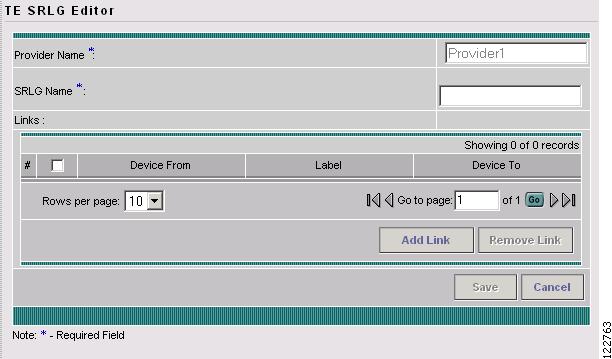
Figure A-35 TE SRLG Editor
The TE SRLG Editor window contains the following GUI elements:
•
Provider Name—Name of the TE provider.
•
SRLG Name—Unique name to identify the SRLG.
The columns in the TE SRLG Editor provide the following information:
•
Device From—Hostname of the TE device that the path originates from.
•
Label—IP addresses of the source and destination interfaces.
•
Device To—Hostname of the TE destination device.
The following actions can be performed:
•
Add Link—Add a link to the SRLG.
•
Remove Link—Remove selected links from the SRLG.
•
Save—Save the created or modified SRLG.
•
Cancel—Cancel the operation and return to the TE SRLG List window.
Step 4
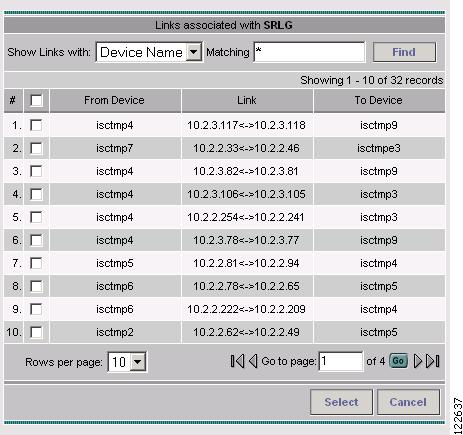
When clicking Add Link to associate a link with the SRLG, the links associated with the SRLG window in Figure A-36 appears. This table displays links that can be added to the SRLG.
Figure A-36 Links associated with SRLG
The columns in the TE SRLG Editor provide the following information:
•
From Device—Hostname of the TE device that the path originates from.
•
Link—IP addresses of the source and destination devices.
•
To Device—Hostname of the TE destination device.
The following actions can be performed:
•
Select—Add selected links to the SRLG.
•
Cancel—Cancel the operation and return to the TE SRLG Editor window.
•
Show Links with—You can search for particular links by specifying matching criteria in the Matching field and clicking Find.
TE Explicit Paths
This section describes the GUI elements in the TE Explicit Path tool.
TE explicit paths can be created after the execution of a TE Discovery task. For instructions on how to create an explicit path, see Create Explicit Path.
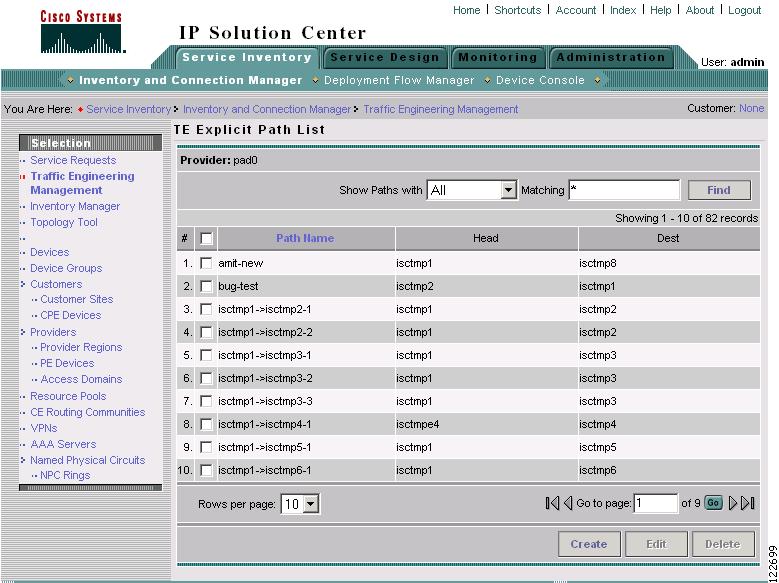
To access the TE Explicit Path List window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Explicit Paths. The TE Explicit Path List window in Figure A-37 appears.
Figure A-37 TE Explicit Path List
The columns in the TE Explicit Path list provides the following information:
•
Path Name—Name of the explicit path.
•
Head—Hostname of the head router.
•
Dest—Hostname of the destination router.
The following actions can be performed:
•
Create—Create an explicit path.
•
Edit—Edit an explicit path.
•
Delete—Delete an explicit path.
•
Find—You can search for particular links by selecting the search variable in the drop-down menu Show Paths with and specify matching criteria in the Matching field.
Create/Edit Explicit Path
This section describes the elements in the create and edit explicit path windows.
To create or edit an explicit path, see Create Explicit Path.
To create or modify an explicit path, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Explicit Paths. In the TE Explicit Path List window, click Create to create an explicit path. To edit an explicit path, select the explicit path that you want to edit by clicking the corresponding check box and clicking Edit.
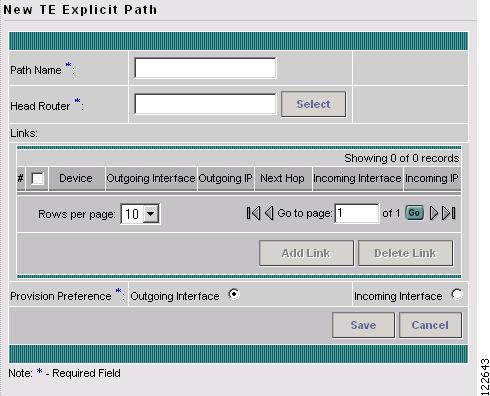
When clicking the Create button, the New TE Explicit Path window in Figure A-38 appears. A similar window appears when clicking the Edit button.
Figure A-38 New TE Explicit Path
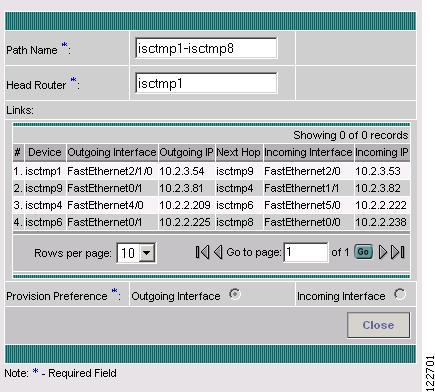
The New TE Explicit Path window contains the following GUI elements
•
Path Name—Name of explicit path.
•
Head Router—Name of the head router.
•
Links (table)—Lists the links added for the current path and contains the following information:
–
Device—Hostname of the TE device that the path originates from.
–
Outgoing Interface—Interface name of the outgoing interface from the originating device.
–
Outgoing IP—IP address of the outgoing interface.
–
Next Hop—Hostname of the next hop device.
–
Incoming Interface—Incoming interface name on the next hop device.
–
Incoming IP—Incoming interface IP address on the next hop device.
•
Provision Preference—Preference for provisioning the next-address subcommand of the ip explicit-path command. Choose between Outgoing Interface and Incoming Interface.
–
Outgoing Interface—Outgoing interface on the router.
–
Incoming Interface—Incoming interface on the router.
The following actions can be performed:
•
Add Link—Add a link to the explicit path.
•
Delete Link—Delete a link in the explicit path.
•
Save—Save all the explicit path data entered.
•
Cancel—Cancel the operation and return to the TE Explicit Path List window.
Step 5
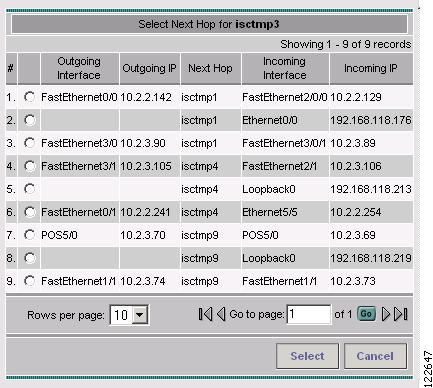
When clicking Add Link to add a blank line to the hop list table, the Select Next Hop window in Figure A-39 appears.
Figure A-39 Select Next Hop
The columns in the TE Explicit Path list provide the following information:
•
Outgoing Interface—Interface name of the outgoing interface from the originating device.
•
Outgoing IP—IP address of the outgoing interface.
•
Next Hop—Hostname of the next hop device.
•
Incoming Interface—Incoming interface name on the next hop device.
•
Incoming IP—Incoming interface IP address on the next hop device.
TE Protected Elements
This section describes the TE Protected Elements GUI.
For instructions on how to configure protected elements, see Configure Element Protection.
Accessing Protection Management
To access the TE Protection Management window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management. Click TE Protected Elements.
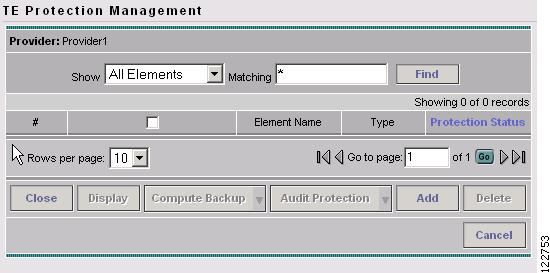
The TE Protection Management window in Figure A-40 appears.
Figure A-40 TE Protection Management
The columns in the TE Protection Management table provide the following information:
•
Element Name—Name of the network element to be protected.
•
Type—Network element type (node, link, or SRLG).
•
Protection Status—The protection status displayed is determined from the last time an audit was performed. The audit is performed either explicitly by the user or when the protection SR is deployed. The protection status is stated for each network element as either Protected, Not Fully Protected, or Unknown. Click on the column header, Protected, to sort elements according to protection status.
The following actions can be performed:
•
Close—Close topology.
•
Display—Open the Topology Display applet to visualize one or more protected elements.
Figure A-41 Compute Backup Button
•
Compute Backup (Figure A-41)—Automatically calculate the optimal backup tunnel for:
–
All Elements—all network elements listed, whether selected or not.
–
Selected Elements—all selected network elements.
Figure A-42 Audit Protection
•
Audit Protection (Figure A-42)—Perform a protection audit on:
–
All Elements—all network elements listed, whether selected or not.
–
Selected Elements—all selected network elements.
•
Add—Add a new protection element.
•
Delete—Delete a protection element.
•
Cancel—Cancel the operation and return to the Traffic Engineering Management Services window.
•
Find—You can search for particular elements by selecting the All, Node, Link, or SRLG in the Show drop-down menu and specify matching criteria in the Matching field.
Compute Backup
This section describes the Compute Backup GUI.
For instructions on how to run Compute Backup on all or selected elements, see Configure Element Protection.
To run Compute Backup, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Protected Elements. The TE Protection Management window in Figure A-40 appears.
In the TE Protection Management window, select one or more elements for which you want ISC TEM to calculate a backup path.
Click Compute Backup and select one of the following:
•
All Elements
•
Selected Elements
The window in Figure A-43 appears.
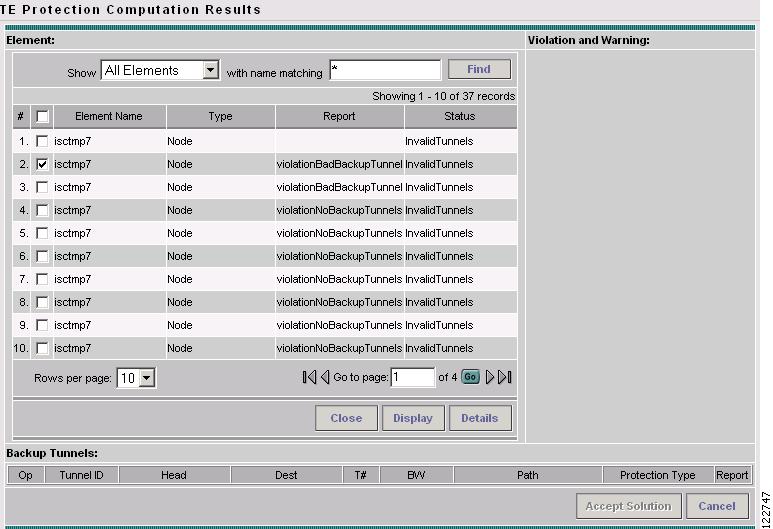
Figure A-43 TE Protection Computation Results
The Element: table displays the outcome of the computation for each element in the protection computation. The status for each element is indicated by at least one row per element in the table. If the status is not valid, the table will contain one row per warning or violation.
The Element: table contains the following columns:
•
Element Name—Name of the network element to be protected.
•
Type—Network element type (node, link, or SRLG).
•
Report—Warning or computation on the network element reported by the computation engine.
•
Status—Computation status of the network element.
The following actions can be performed:
•
Close—Close the Topology Display applet if open.
•
Display—Open the Topology Display applet to visualize one or more protected elements and their protection tunnel(s). The Topology Display is shown in Figure A-4.
•
Details—List backup tunnels and violations/warnings for the selected network element. The information is displayed in the Backup Tunnels: section and the Violation and Warning: section, if applicable, as shown in Figure A-44.
Violation and Warning: pane—Describes the selected violation/warning and any relevant details about the corresponding link or flow.
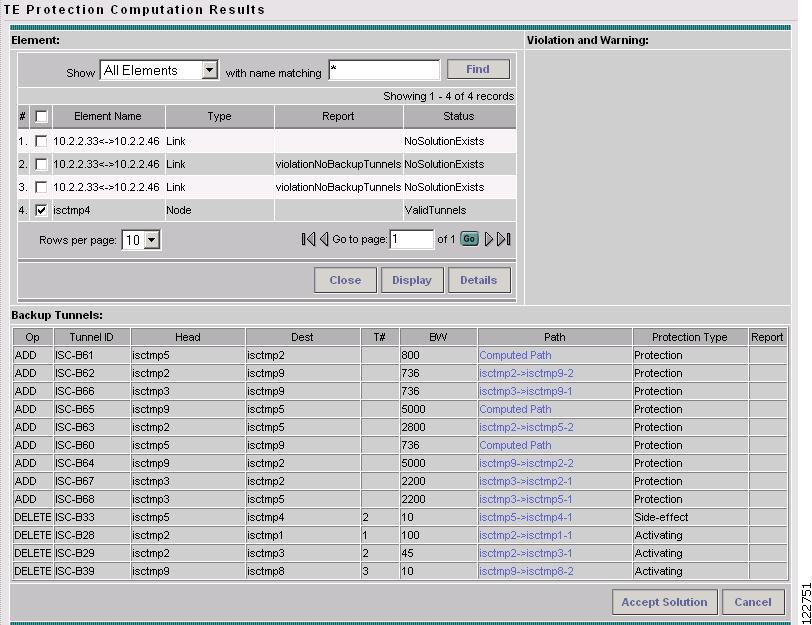
Figure A-44 TE Protection Computation Results with Backup Tunnels
The columns in the tunnel list provide the following information:
•
Op—SR operation on the tunnel. This can be either of the following:
–
ADD—Indicates a new tunnel calculated by the computation.
–
DELETE—Signifies that the computation found an existing backup tunnel that do not provide adequate protection on the element and, therefore, should be deleted.
•
Tunnel ID—Unique tunnel identifier used within ISC TEM.
•
Head—Hostname of the head router.
•
Dest—Hostname of the destination router.
•
T#—Tunnel number on the head router.
•
BW—The amount of bandwidth this backup tunnel can protect. The router limits the LSPs that can use this backup tunnel so that the sum of the bandwidth of the LSPs does not exceed the specified amount of bandwidth. If there are multiple backup tunnels, the router will use the best-fit algorithm.
•
Path—Tunnel path in the form of either a computed path or an existing path . Click to view the path.
•
Protection Type—Protection side-effect from activating the tunnel.
•
Report—If it says yes in the Report field, the tunnel is associated with the selected violation/warning. A blank field indicates that no report was generated.
The following actions can be performed (buttons):
•
Accept Solution—Accept the proposed element protection solution and place the backup tunnels in the TE Protection SR window for further action.
•
Cancel—Discard the proposed element protection solution and return to the TE Protection Management window.
•
Find—You can search for particular elements by selecting the element type in the drop-down menu Show and specifying matching criteria in the with name matching field.
Audit Protection
This section describes the Audit Protection GUI.
For instructions on how to run Audit Protection on all or selected elements, see Configure Element Protection.
To run Audit Protection, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Protected Elements. The TE Protection Management window in Figure A-40 appears.
In the TE Protection Management window, select one or more elements for which you want ISC TEM to perform an Audit Protection computation.
Click Audit Protection and select one of the following:
•
All Elements
•
Selected Elements
ISC TEM reports FRR Audit Protection in progress and the same computation result window as for Compute Backup in Figure A-43 appears.
The GUI for the rest of the process is identical to that described for Compute Backup.
Assign TE Resources
To access the TE Resource Management part of the TEM GUI, click Assign TE Resources in the Traffic Engineering Management Services window (see Figure A-1).
The graphical user interface for Assign TE Resources is identical to that of TE Links. For an explanation of the GUI elements of this window, see TE Links.
The process of assigning TE resources is explained in Chapter 4, "TE Resource Management."
Create Managed TE Tunnel
In this section, the GUI used to create managed traffic engineering tunnels is explained. For step-by-step instructions on how to create a managed TE tunnel, see "Basic Tunnel Management."
To access the Create Managed TE Tunnel window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > Create Managed TE Tunnel.
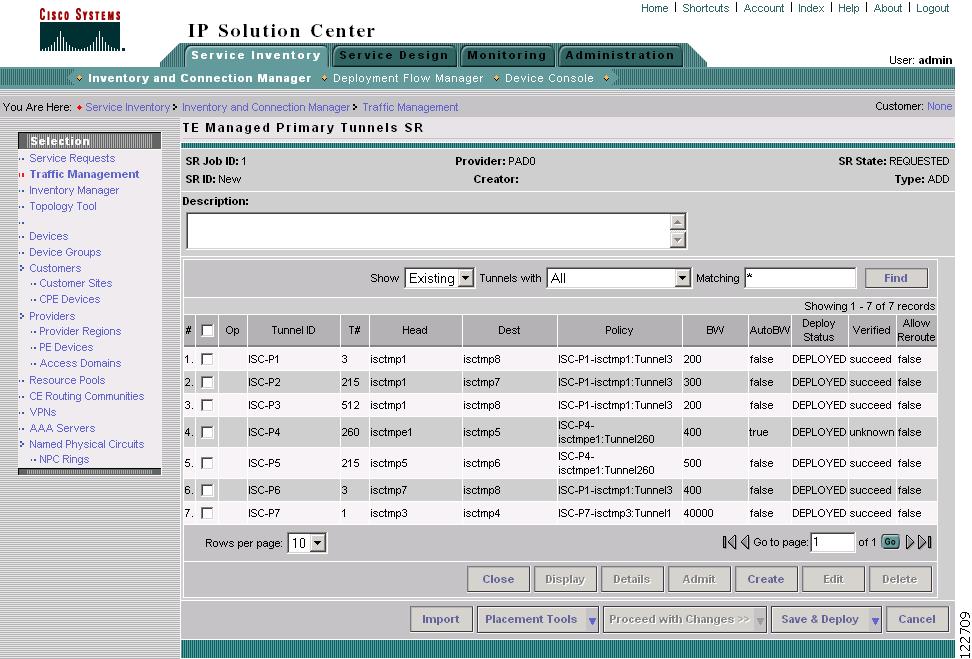
The TE Managed Primary Tunnels SR window in Figure A-45 appears.
Figure A-45 TE Managed Primary Tunnels SR
The TE Managed Primary Tunnels SR window contains the following elements:
The columns in the tunnel list provides the following information:
•
Op—SR operation on the tunnel. This can be one of the following:
–
ADD—Indicates a newly added tunnel.
–
MODIFY—Indicates a modified existing tunnel.
–
DELETE—Indicates an existing tunnel to be deleted.
–
ADMIT—Indicates an existing tunnel to be admitted by tunnel computation.
•
Tunnel ID—Unique tunnel identifier used within ISC TEM.
•
T#—Tunnel number on the head router.
•
Head—Hostname of the head router.
•
Dest—Hostname of the destination router.
•
Policy—TE policy for the tunnel.
•
BW—The amount of bandwidth this backup tunnel can protect. The router limits the LSPs that can use this backup tunnel so that the sum of the bandwidth of the LSPs does not exceed the specified amount of bandwidth. If there are multiple backup tunnels, the router will use the best-fit algorithm. If the tunnel is auto-bw enabled, BW shows the higher of tunnel bandwidth and maximum automatic bandwidth.
•
AutoBW—Auto Bandwidth enabled if true, otherwise false.
•
Deploy Status—Tunnel deployment status.
•
Verified—Indicates whether tunnel verification was successful (succeed, failed, or unknown).
•
Allow Reroute—Specifies whether reroute is allowed (true or false). If reroute is not allowed, the tunnel cannot be set to movable, and hence cannot be rerouted by the repair operation.
The following actions can be performed (buttons):
•
Close—Close the Topology Display applet if open.
•
Display—Open a Topology Display for the network and highlight the selected primary tunnel(s). Selected tunnels are marked in color with directional arrows.
•
Details—Open the TE Tunnel Details window, which provides type, status, LSP, and other information about the tunnel.
•
Admit—Admit selected tunnels not previously verified into the managed topology. This feature is used only for discovered tunnels that failed verification or for migrating unmanaged tunnels.
•
Create—Create a managed primary tunnel.
•
Edit—Edit a selected primary tunnel.
•
Delete—Delete selected primary tunnels.
•
Import—Import tunnel data from import XML file.
•
Placement Tools—These tools are available only when no change has been made to the tunnels. Apply the following functions against the current topology and tunnels:
–
Groom—Analyze elements (nodes, links, or SRLGs) in the TE network and optimize the way they handle the network traffic.
–
Tunnel Audit—Determine if any inconsistencies exist in the TE network.
–
Tunnel Repair—Resolve inconsistencies in the TE network by moving as few existing tunnels as possible to accomodate the changes.
The Placement Tools GUI is described in Planning Tools.
•
Proceed with Changes >>—For verifying changes in tunnels. When tunnels have been created, deleted, admitted, or their attributes altered, you can proceed with one of the following placement tools:
–
Tunnel Audit—Determine what inconsistencies modifications to tunnels or network elements might cause.
–
Tunnel Placement—Admit new tunnels and modify tunnels already admitted into the network.
–
Tunnel Repair—Resolve inconsistencies caused by changes to bandwidth requirements or delay parameters of existing tunnels by moving as few existing tunnels as possible to accomodate the changes.
•
Save & Deploy (Figure A-46)—For committing tunnel changes that do not impact tunnel placement. There are two options for saving and deploying SR tunnels to the network:
–
SR Tunnels Only—Deploy all tunnel changes that does not impact tunnel placement, or if no changes were made to the SR, use this to re-deploy the SR that was in Requested or Invalid state.
–
Force Deploy All Tunnels—Force deployment of all tunnels in this SR. This could be useful when previous provisioning of the SR has failed, so that it is necessary to force through the deployment of all tunnels in the SR.
Figure A-46 Save & Deploy Tunnels
•
Cancel—Cancel the operation and return to the Traffic Engineering Management Services window.
The tunnel SR search tool allows you to look for particular tunnels by selecting tunnel characteristics in the drop-down menu tunnels with and specify matching criteria in the Matching field:
•
Show:
–
Existing—Show existing tunnels already deployed in the TE network.
–
SR—Show tunnels not yet deployed in the TE network.
•
Tunnels with:
–
All—Show all managed tunnels under the current provider.
–
Tunnel Number—Tunnel number on the head router.
–
Head Device—Full or partial name of the tunnel head device.
–
Destination Device—Full or partial host name of the tail device of the tunnel.
–
Head, Dest Devices—Exact host name of the head and tail devices of the tunnel.
–
Deploy Status—Tunnel deployment status.
–
Policy Name—Name of the TE policy.
•
Matching/Equal—Specify matching criteria for your search. Wildcards are accepted. Matching changes to Equal if Head, Dest Device is selected in the drop-down menu. For Equal, the exact host name of the head or tail device must be entered (wildcards not accepted).
•
Find—Click the Find button when the search criteria has been entered.
View Managed Primary Tunnel Details
This section describes the elements in the TE Managed Primary Tunnel Details window.
To view the details of a TE managed primary tunnel, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management. > Create Managed TE Tunnel. The TE Managed Primary Tunnels SR window in Figure A-45 appears.
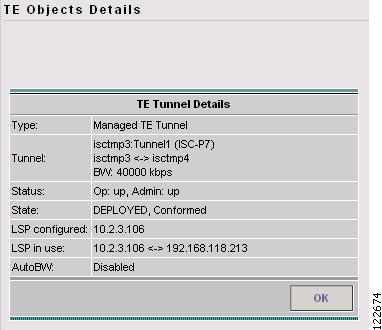
To view the details of a particular managed primary tunnel, select the desired tunnel by first clicking the corresponding check box and then clicking the Details button. When clicking Details, the TE Tunnel Details window in Figure A-47 appears.
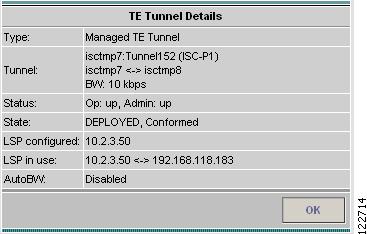
Figure A-47 TE Tunnel Details
The TE Tunnel Details window contains the following elements:
•
Type—Managed or unmanaged.
•
Tunnel—Tunnel name, head and destination routers, and total bandwidth.
•
Status—The operational and administrative status of the TE tunnels as of the latest TE Discovery task.
•
State—Indicates whether the tunnel state is DEPLOYED or NOT DEPLOYED and whether it is Conformed or Not Conformed.
•
LSP configured—IP address of the tunnel's Label-Switched Path (LSP) interface on the head router.
•
LSP in use—Actual LSP in the network as of the latest TE Discovery task.
•
AutoBW—Auto Bandwidth Enabled or Disabled.
Create TE Managed Primary Tunnel SR
This section describes the GUI elements in the Create TE Managed Primary Tunnel SR and Edit TE Managed Primary Tunnel windows. The create feature is here used as an example.
To create a TE Managed Primary Tunnel SR, see "Basic Tunnel Management."
To access the Create TE Managed Primary Tunnel SR window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > Create Managed TE Tunnel. The TE Managed Primary Tunnels SR window appears. Click Create, to open the Create TE Managed Primary Tunnel window as shown Figure A-48.
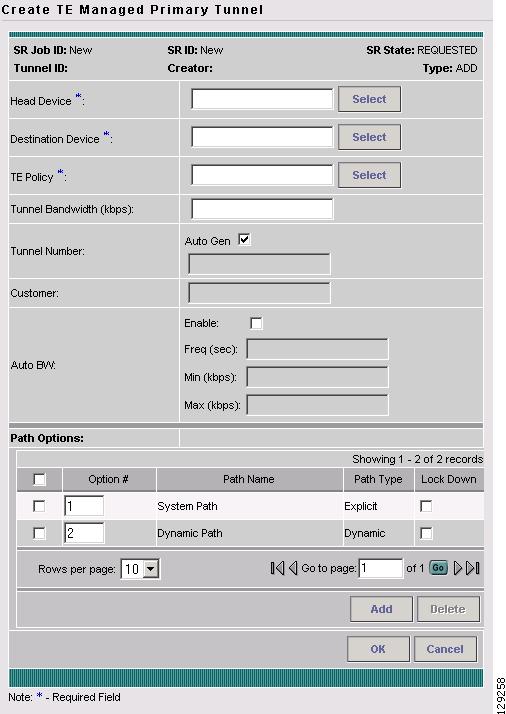
Figure A-48 Create TE Managed Primary Tunnel
The Create TE Managed Primary Tunnel window contains the following elements:
•
Head Device—Head device for the tunnel.
•
Destination Device—Destination device for the tunnel.
•
Tunnel Policy—A set of rules established for a tunnel.
•
Tunnel Bandwidth—Total allocated bandwidth of the tunnel.
•
Tunnel Number—Tunnel number corresponding to the tunnel interface name.
–
Auto Gen—Check this box to generate the tunnel number automatically. Otherwise, enter a desired number.
•
Customer—Selected customer for the tunnel.
•
Auto BW—A way to configure a tunnel for automatic bandwidth adjustment and to control the manner in which the bandwidth for a tunnel is adjusted.
–
Enable—Check this box to enable automatic bandwidth.
–
Freq—Interval between bandwidth adjustments.
–
Min—Minimum automatic bandwidth, in kbps, for this tunnel.
–
Max—Maximum automatic bandwidth, in kbps, for this tunnel.
Path options:
•
Option #—Sequential number of available explicit paths.
•
Path Name—Name of the explicit path. In case of an existing path, the name is a URL that links to the Explicit Path Viewer (see Figure 5-15).
–
System Path—ISC system generated explicit path (immovable). For managed tunnels, the first path has to be an explicit path. If a tunnel contains a system path, the planning function will generate an optimal path for the tunnel.
–
Dynamic Path—A dynamic path is provisioned by allowing the head router to find a path. The dynamic keyword is provisioned to the routers.
•
Path Type—Path option type, Explicit or Dynamic.
•
Lock Down—Disables reoptimization check on the tunnel, if checked, meaning the path cannot be changed.
The following actions can be performed:
•
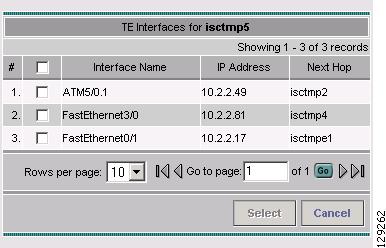
Add—Add a path option. This opens the Select TE Explicit Path window in Figure A-52.
•
Delete—Delete a path option.
•
OK—Accept all changes and return to the TE Managed Primary Tunnels SR window.
•
Cancel—Cancel the operation and return to the TE Managed Primary Tunnels SR window.
Select Devices and Policy
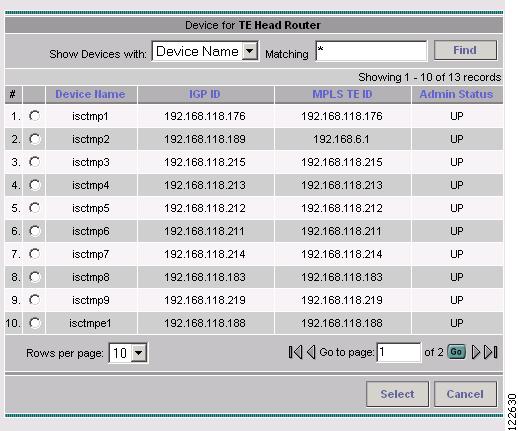
To select a Head Device in the Create TE Managed Primary Tunnel window (Figure A-48), click the corresponding Select button to open the Select Device for TE Head Router window shown in Figure A-49.
Figure A-49 Select Device for TE Head Router
The Select Device for TE Head Router window contains the following elements:
•
Device Name—Hostname for the device.
•
IGP ID—Interior Gateway Protocol (IGP) ID.
•
MPLS TE ID—TE ID assigned by the router.
•
Admin Status—Indicates whether the router is UP or DOWN.
The following actions can be performed:
•
Select—Accept the selected device and return to the previous window.
•
Cancel—Cancel the operation and return to the previous window.
•
Find—You can search for particular devices by selecting the device type in the drop-down menu Show Devices with and specify matching criteria in the Matching field.
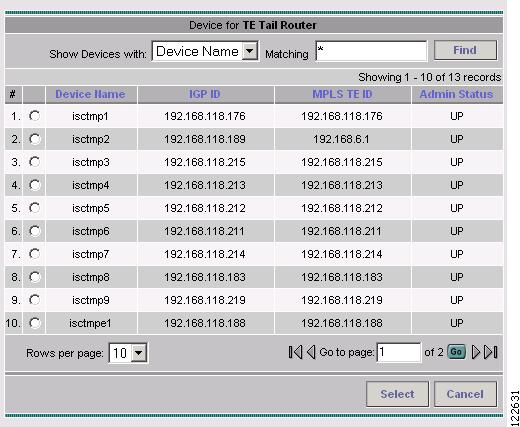
Figure A-50 Select Device for TE Tail Router
For a description of the GUI elements in the Select Device for TE Tail Router window, see the explanation for the Select Device for TE Head Router window.
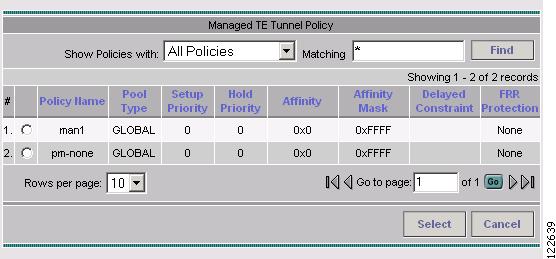
Figure A-51 Select Managed TE Tunnel Policy
The Select Managed TE Tunnel Policy window contains the following elements:
•
Policy Name—Name of the TE policy.
•
Pool Type—Tunnel bandwidth pool type.
–
SUB POOL—Bandwidth section nested inside the Global Pool part of the total bandwidth.
–
GLOBAL—Section of the total link bandwidth containing all Sub Pools for the link.
•
Setup Priority—Priority used when signaling an LSP for the tunnel to determine, which of the existing tunnels can be preempted. Valid values are from 0 to 7, where a lower number indicates a higher priority. Therefore, an LSP with a setup priority of 0 can preempt any LSP with a non-0 hold priority.
•
Hold Priority—Priority associated with an LSP for the tunnel to determine if it should be preempted by other LSPs that are being signaled. Valid values are from 0 to 7, where a lower number indicates a higher priority.
•
Affinity—Attribute values required for links carrying the tunnel (bit values are either 0 or 1).
•
Affinity Mask—Attribute values to be checked. If a bit in the mask is 0, a link's attribute value of that bit is irrelevant. If a bit in the mask is 1, the link's attribute value and the tunnel's required affinity for that bit must match.
•
Delayed Constraint—Delay constraint for the path used by the tunnel.
•
FRR Protection—Used to enable an MPLS traffic engineering tunnel to use a backup tunnel in the event of a link failure if a backup tunnel exists.
–
None—No backup tunnel needed.
–
Best Effort—Use backup tunnel if available.
–
Link and SRLG—Specifies that primary tunnels should be routed only through links and SRLGs that are protected by FRR backup tunnels.
–
Link, SRLG and Node—Specifies that primary tunnels should be routed only through links, SRLGs and nodes that are protected by FRR backup tunnels.
Select TE Explicit Path
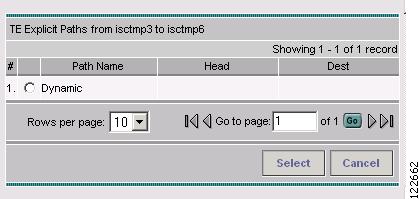
An explicit path is added to a tunnel by clicking Add in the tunnel editor. The Select TE Explicit Path window in Figure A-52 appears.
Figure A-52 Select TE Explicit Path
Two path types are available:
Explicit Path—A fixed path from a specific head to a specific destination device.
Dynamic Path—A path that is provisioned by allowing the head router to find the path. The dynamic IOS keyword is provisioned to the routers. This signifies that the router calculates a valid path.
Explicit Path Viewer
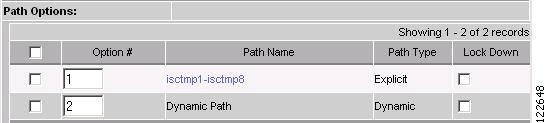
When creating a primary tunnel, the Path Options list by default suggests a System path and a Dynamic path. If an explicit path is added, this link will be selectable as shown in the Path Options section of the create window in Figure A-53. By clicking an explicit path link, a non-editable Explicit Path Viewer in Figure A-54 appears.
Figure A-53 Path Options
For an explanation of the various GUI elements, see Create Managed TE Tunnel.
Figure A-54 TE Explicit Path Viewer
For an explanation of the various GUI elements, see Create/Edit Explicit Path.
Import Tunnel
This section describes the GUI elements in the import tunnel feature.
For instructions on how to import TE tunnels, see the Import Primary Tunnel, page 6-8.
The tunnel import function is found under Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > Create Managed TE Tunnel, which opens the TE Managed Primary Tunnels SR window (see Figure A-62).
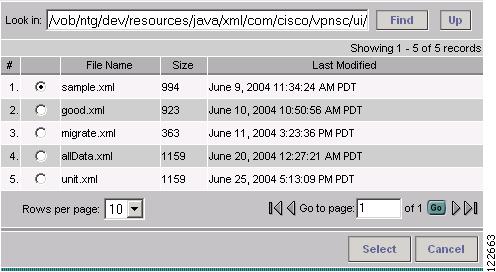
When you click Import to start the import process, the Select Import File window in Figure A-55 appears.
Note
The Import button is only enabled when there are no uncommitted new, changed, or deleted tunnels in the service request.
Figure A-55 Select Import File
The Select Managed TE Tunnel Policy window contains the following elements:
•
File Name—Name of XML file.
•
Size—Size in kilobytes of XML file.
•
Last Modified—Date and time when the file was last modified.
The following actions can be performed:
•
Select—Accept the selected XML file(s) and start the tunnel import operation.
•
Cancel—Cancel the tunnel import operation and return to the TE Managed Primary Tunnels SR window.
•
Find—Specify the directory containing the XML import files and directories to import in the Look in field and click Find. This brings up the data import directory and the XML files contained are listed in the accompanying table.
•
Up—Go to the parent directory.
Import Error Status Window
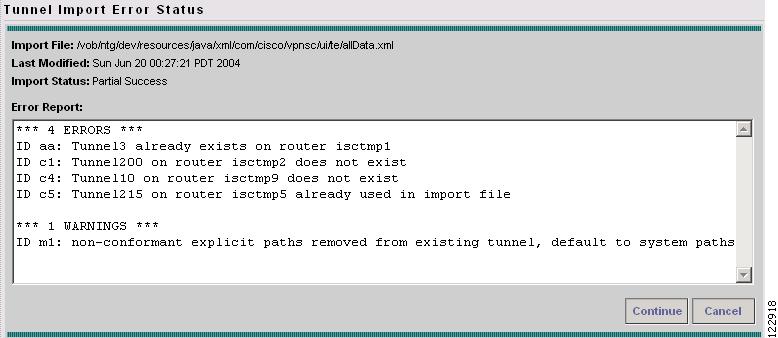
When you click Select to start the import operation, the system parses the file, and if any error is detected, it will be reported in the Tunnel Import Error Status window shown in Figure A-56.
Figure A-56 Tunnel Import Error Status
The Tunnel Import Error Status window contains the following elements:
•
Import File—Directory containing XML import files and directories.
•
Last Modified—Date and time when the file was last modified.
•
Import Status—There are two possible Import Status values:
–
Failed—Critical errors are present and the import process cannot continue.
–
Partial Success—There are either non-critical errors or warnings or both in the file. In this case the error tunnel is reported and skipped and the warning tunnel is processed with certain defaults applied. There is no "Success" status because when there are no errors or warnings, the Tunnel Import Error Status window will not appear.
The following actions can be performed:
•
Continue—If the import operation is partially successful, click Continue to accept system treatment for errors/warnings and continue with the import operation.
•
Cancel—Cancel import operation and return to the previous window.
Edit TE SR (Primary or Backup)
The tunnels editor windows differ only very slightly from the create tunnel windows. All fields in the editor windows are found in the create windows for both primary managed, primary unmanaged, and backup tunnels (see "Basic Tunnel Management").
The only difference from the create window is that the head and destination device and tunnel number fields are not editable and the Path Options table lists existing path options on the tunnel rather than the default System and Dynamic paths.
Planning Tools
This section describes the GUI elements in the sequence of windows used by the planning tools Tunnel Audit, Tunnel Placement, Tunnel Repair, and Grooming. Screenshots from Tunnel Repair has been used as an example but it covers the GUI elements for all four processes.
To use the planning tools, see Placement Tools, page 6-11
To access the Create TE Managed Primary Tunnel SR window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > Create Managed TE Tunnel. The TE Managed Primary Tunnels SR window in Figure A-62 appears.
There are two ways to activate the planning tools:
•
When one or more tunnels have been created or their attributes altered (see Create Primary Tunnel, page 6-2), Tunnel Audit, Tunnel Placement, and Tunnel Repair can be activated by selecting Proceed with Changes >>.
•
When no changes have taken place, Grooming, Tunnel Audit, and Tunnel Repair can be accessed by selecting Placement Tools.
As an example, assume that we run Tunnel Repair on a set of tunnels as described in Tunnel Repair, page 6-21.
Movable Tunnel Selection Window
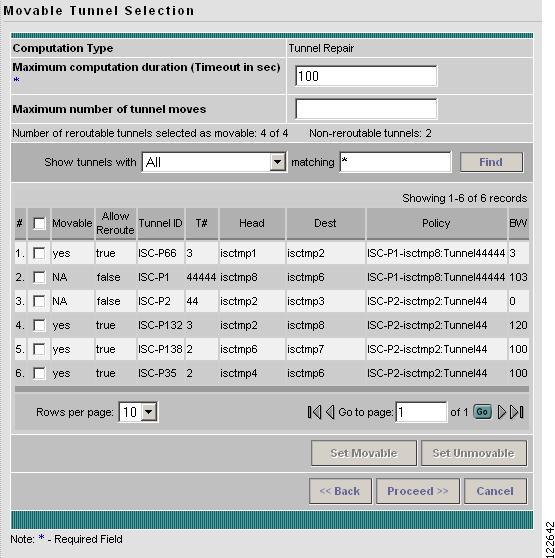
When selecting Tunnel Repair from the Placement Tools button, the Movable Tunnel Selection window in Figure A-57 appears.
Figure A-57 Movable Tunnel Selection
The Movable Tunnel Selection window contains the following elements:
•
Computation Type—Indicates which tool is used for the computation (Placement, Repair, Grooming).
•
Maximum computation duration—The maximum amount of time allowed for the computation before timeout occurs.
•
Maximum number of tunnel moves—The maximum number of tunnels that can be moved during Tunnel Repair.
•
Number of reroutable tunnels selected as movable—Indicates how many reroutable tunnels among the ones shown in the tunnel list are movable.
•
Non-reroutable—Indicates how many tunnels among the ones shown in the tunnel list are not movable. This is set in the tunnel editor.
•
Find—You can search for particular tunnels by selecting the search variable in the drop-down menu Show tunnels with, specifying matching criteria, and clicking Find.
Show tunnels with options:
–
All—Show all managed tunnels under the current provider.
–
Tunnel Number—Tunnel number on the head router.
–
Head Device—Full or partial name of the tunnel head device.
–
Destination Device—Full or partial host name of the tail device of the tunnel.
–
Head, Dest Devices—Exact host name of the head and tail devices of the tunnel.
–
Deploy Status—Tunnel deployment status.
–
Policy Name—Name of the TE policy.
matching/equal—Specify matching criteria for your search. Wildcards are accepted. matching changes to equal if Head, Dest Device is selected in the drop-down menu. For equal, the exact host name of the head or tail device must be entered (wildcards not accepted).
•
Movable—Indicates whether the tunnel is movable (yes, no or NA). This setting can is toggled by clicking Set Movable and Set Unmovable.
•
Allow Reroute—Specifies whether reroute is allowed (true or false). If reroute is not allowed, the tunnel cannot be set to movable.
•
Tunnel ID—Unique tunnel identifier used within ISC TEM.
•
T#—Tunnel number on the head router.
•
Head—Hostname of the head router.
•
Dest—Hostname of the destination router.
•
Policy—TE policy for the tunnel.
•
BW—The tunnel bandwidth. If the tunnel is auto-bw enabled, BW shows the higher of tunnel bandwidth and maximum automatic bandwidth.
The following actions can be performed:
•
Set Movable—Set selected tunnel to movable.
•
Set Unmovable—Set selected tunnel to unmovable.
•
<< Back—Return to the previous window.
•
Proceed >>—Proceed to computation.
•
Cancel—Cancel the operation and return to the previous window.
TE Primary Tunnel Computation SR - Changes Window
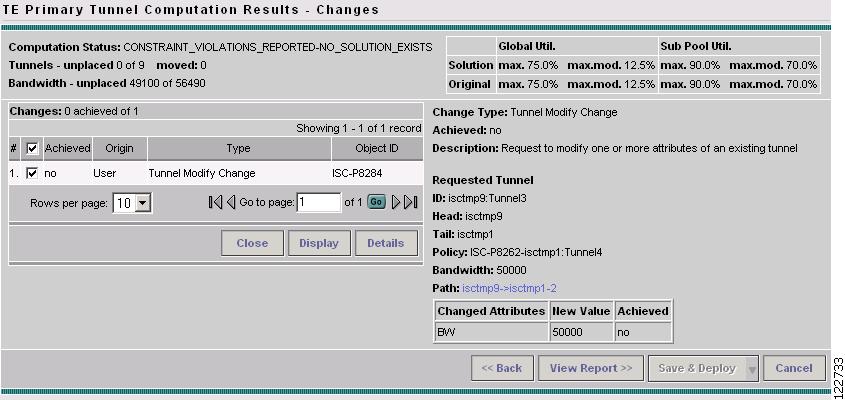
Still using Tunnel Repair as an example, after selecting Proceed >> from the Movable Tunnel Selection window, the TE Primary Tunnel Computation Results - Changes window in Figure A-58 appears.
The figure shows the computation results window after clicking Detail to obtain detailed information about the tunnel and view the status of the change request.
Figure A-58 TE Primary Tunnel Computation Results - Tunnel Repair Changes (Details)
The TE Primary Tunnel Computation Results - Changes window contains the following elements:
Status section (top):
•
Computation Status—Indicates whether the computation succeeded or failed.
•
Tunnels:
–
unplaced—Number of unplaced tunnels out of the total.
–
moved—Number of tunnels that were moved.
•
Bandwidth - unplaced—Amount of bandwidth that was not placed out of the total available bandwith.
•
Global Util.—Global Pool bandwidth utilization percentage.
•
Sub Pool Util.—Sub Pool bandwidth utilization percentage
•
Solution—Utilization for the generated solution.
•
Original—Utilization for the original solution.
Changes section (left):
•
Changes—Number of changes achieved out of the total number of changes.
–
Achieved—Indicates whether a specific change is successful (Yes or No).
–
Origin—The originator of the change. Can be user (change by user) or compute (from a computation, e.g. rerouting of a tunnel).
–
Type—The type of change requested: Tunnel Add Change, Tunnel Modify Change, Tunnel Remove Change, or Element Modify Change.
–
Object ID—A tunnel or link ID.
Information section (right):
•
Change Type—The type of change requested: Tunnel Add Change, Tunnel Modify Change, Tunnel Remove Change, or Element Modify Change.
•
Achieved—Indicates whether a specific change is successful (Yes or No).
•
Description—Description of the computation attempt.
•
ID—Tunnel ID.
•
Head—Hostname of the head router.
•
Tail—Hostname of the destination router.
•
Policy—TE policy for the tunnel.
•
Bandwidth—Bandwidth used in computation.
•
Path—Tunnel path in the form of either a computed path or an existing path . Click to view the path.
•
Changed attribute table:
–
Changed Attributes—Lists the tunnel attributes that have changed.
–
New Value—New value of the attribute.
–
Achieved—Indicates whether a specific change is successful (Yes or No).
The following actions can be performed:
•
Close—Close the Topology Display applet if open.
•
Display—Invoke the Topology Display to view selected links and/or tunnels in the network. Selected links/tunnels are displayed with a unique color.
•
Detail—Open the detail panel in the right side of the Computation Result window to see the tunnel/link information.
•
<< Back—Return to the previous window.
•
View Report >>—View a list of generated reports. The Report window appears (see Figure A-60).
•
Save & Deploy (Figure A-59)—For committing all user originated and system computed changes. There are two options for saving and deploying tunnel SRs to the network:
–
Deploy Achieved Changes—Place all achieved changes in the deployment queue.
–
Force Deploy All Tunnels—Force deployment of all elements in the SR. This could be useful when previous provisioning of the SR has failed, so that it is necessary to force through the deployment of all tunnels in the SR.
Figure A-59 Save & Deploy
•
Cancel—Cancel the operation and return to either the Links List, TE Managed Primary Tunnels SR, or the TE Resource Management SR window depending on the originating flow.
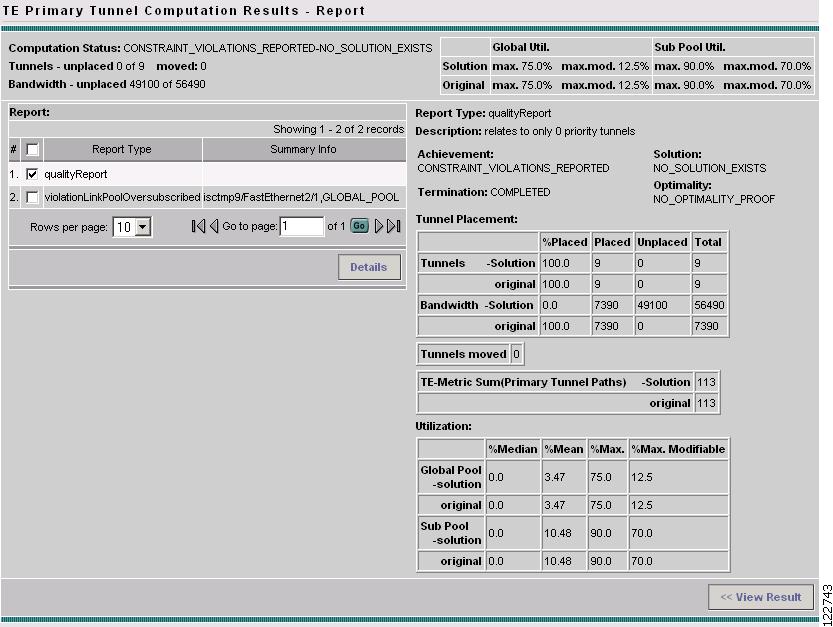
TE Primary Tunnel Computation Results - Report
To view the computation reports, click View Report >>. The TE Primary Tunnel Computation Results - Report window in Figure A-60 appears.
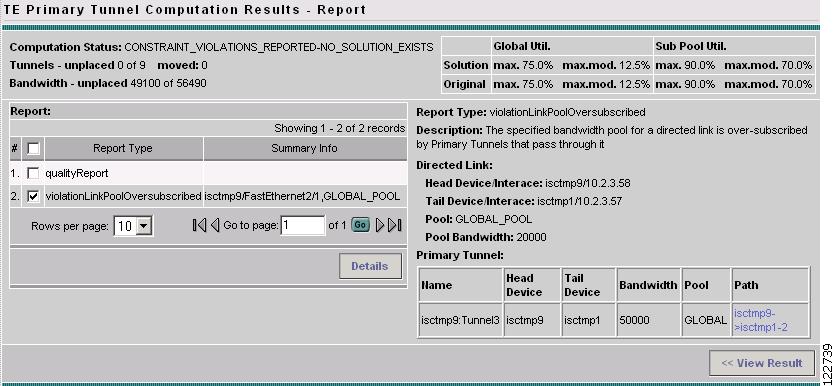
In this case, there is both a quality report and a violation report. In that case, a detail report such as the violation report in Figure A-61 will appear. Warning and violation reports have different fields and they are all described in Appendix B, "Warnings and Violations."
Select the desired report and click the Detail button
Figure A-60 TE Managed Primary Tunnels SR - Tunnel Repair Report (Details)
The TE Primary Tunnel Computation Results - Report window contains the following elements:
Status section (top): described above (Figure A-58).
Report section (left):
•
Report Type—There are three basic report types: a qualityReport (generated every time), warning reports, and violation reports.
•
Summary Info—Summary information about the findings of the report.
Information section (right):
•
Report Type—See description above.
•
Description—Specific information about the report.
•
Achievement—Success or failure of the computation attempt/solution (Yes or No).
•
Solution—Indicates whether a solution was found.
•
Termination—Indicates whether the computation was completed.
•
Optimality—Indicates whether the computation was optimal.
Tables:
•
Tunnel Placement: Tables that compares various tunnel placement attributes of the original configuration with the solution configuration.
–
Tunnels: Attributes of the original and computed tunnels.
–
Bandwidth: Attributes of the tunnel bandwidth.
–
%Placed—Percentage of tunnels that were successfully placed.
–
Placed—Number of tunnels that were successfully placed.
–
Unplaced—Number of tunnels that were not placed.
–
Total—Total number of tunnels.
–
Tunnels moved—Number of tunnels moved from their original paths.
–
TE-Metric Sum (Primary Tunnel Paths)—TE metric sum for the computed and the original paths.
•
Utilization:Table that compares various utilization measurements of the original configuration with the solution configuration
–
Global Pool—Comparison data for various Global Pool attributes.
–
Sub Pool—Comparison data for various Sub Pool attributes.
–
Median—[to be added]
–
Max. Modifiable—[to be added]
–
Mean—[to be added]
–
Max.—[to be added]
The following actions can be performed:
Changes actions (buttons, left):
•
Detail—When a report is selected, the Detail button displays the contents of the report, which can contain warnings or violations, in the right window pane.
Note
For a description of possible warnings and violations in ISC TEM, see Appendix B, "Warnings and Violations."
•
<< View Result—Return to the Changes window.
Figure A-61 TE Managed Primary Tunnels SR - Violation Report (Details)
In Figure A-61, the top status section and the left Report section contain the same fields as in Figure A-60.
Create Unmanaged TE Tunnel
The only two differences between the managed and the unmanaged tunnel GUIs is that the path option table does not automatically populate the two System/Dynamic paths and that the Conformance status is only indicated for unmanaged primary tunnels.
For a description of the rest of the GUI, see Create Managed TE Tunnel.
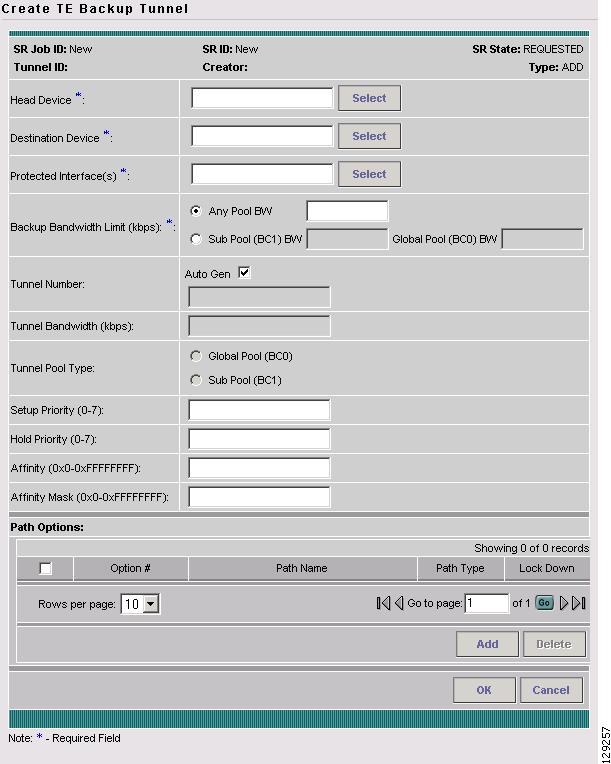
Create TE Backup Tunnel
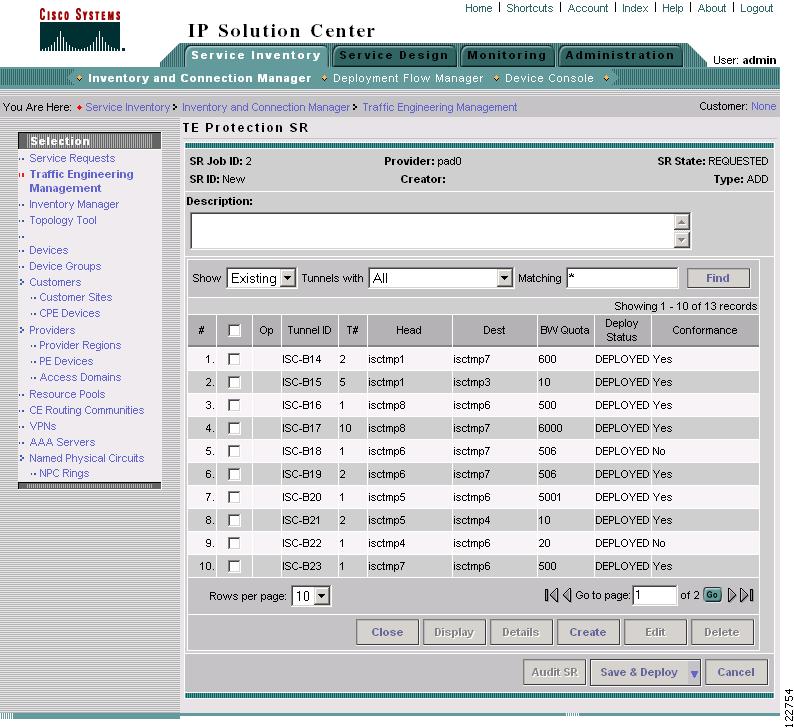
To access the TE Protection SR window for managing backup tunnels, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > Create TE Backup Tunnel. The TE Protection SR window in Figure A-62 appears.
Figure A-62 TE Protection SR
The TE Protection SR window contains the following elements:
The columns in the tunnel list provides the following information:
•
Op—Current SR operation on the tunnel. This can be one of the following:
–
ADD—Indicates a newly added tunnel, either calculated by the system or entered by the user.
–
MODIFY—Indicates a modified existing tunnel.
–
DELETE—Indicates an existing tunnel to be deleted, either computed by the system or originated by the user.
•
Tunnel ID—Unique tunnel identifier used within ISC TEM.
•
Head—Hostname of the head router.
•
Dest—Hostname of the destination router.
•
T#—Tunnel number on the head router.
•
BW Quota—The amount of bandwidth this backup tunnel can protect. The router limits the LSPs that can use this backup tunnel so that the sum of the bandwidth of the LSPs does not exceed the specified amount of bandwidth. If there are multiple backup tunnels, the router will use the best-fit algorithm.
•
Deploy Status—Tunnel deployment status.
•
Conformance—Indicates whether the tunnel is found to be conformant when running discovery. A tunnel is non-conformant if it has a non-zero bandwidth reservation and a zero hold or setup priority. If a tunnel is entered through ISC TEM, it is always conformant.
The following actions can be performed (buttons):
•
Close—Close the Topology Display applet if open.
•
Display—Open a Topology Display for the network and highlight the selected backup tunnel(s). The selected tunnel(s) is/are marked in color with directional arrows.
•
Details—Open the TE Tunnel Details window, which provides type, status, LSP, and other information about the tunnel.
•
Create—Create a backup tunnel.
•
Edit—Edit the selected backup tunnel.
•
Delete—Delete the selected backup tunnels.
•
Audit SR—Audit protection of protected elements using all existing backup tunnels and proposed changes in the SR.
•
Save & Deploy (Figure A-63)—For committing resource changes in the SR. Two options for saving and deploying Backup Tunnel SRs to the network:
–
SR Tunnels Only—Deploy all tunnel changes in the SR, or if no changes were made to the SR, use this to re-deploy the SR that was in Requested or Invalid state.
–
Force Deploy All Tunnels—Force deployment of all tunnels in this SR. This could be useful when previous provisioning of the SR has failed, so that it is necessary to force through the deployment of all tunnels in the SR.
Figure A-63 Save & Deploy Tunnels
•
Cancel—Cancel the operation and return to the Traffic Engineering Management Services window.
The tunnel SR search tool allows you to look for particular tunnels by selecting tunnel characteristics in the drop-down menu tunnels with and specify matching criteria in the Matching field:
•
Show:
–
Existing—Show existing tunnels already deployed in the network.
–
SR—Show tunnels not yet deployed in the network.
•
tunnels with:
–
All—Show all managed tunnels under the current provider.
–
Tunnel Number—Tunnel number on the head router.
–
Head Device—Full or partial name of the tunnel head device.
–
Destination Device—Full or partial host name of the tail device of the tunnel.
–
Head, Dest Devices—Exact host name of the head and tail devices of the tunnel.
–
Tunnel Status—Tunnel deployment status.
–
Conformance—Conformant or non-conformant tunnel.
•
matching/equal—Specify matching criteria for your search. Wildcards are accepted. matching changes to equal if Head, Dest Device is selected in the drop-down menu. For equal, the exact host name of the head or tail device must be entered (wildcards not accepted).
•
Find—Click the Find button when the search criteria has been entered.
Create TE Backup Tunnel Window
From the TE Protection SR window, click Create to access the Create TE Backup Tunnel window shown in Figure A-64.
Figure A-64 Create TE Backup Tunnel
The Create TE Backup Tunnel window contains the following elements:
•
Head Device—Head device for the tunnel. For selecting devices, see Figure A-49.
•
Destination Device—Destination device for the tunnel. For selecting devices, see Figure A-50.
•
Protected Interface—Interface(s) on the head router that this backup tunnel protects.
•
Backup Bandwidth Limit—Bandwidth protected by the backup tunnel.
–
Any Pool BW—Bandwidth set aside for the protection of either the Sub Pool or the Global Pool.
–
Sub Pool (BC1) BW—Bandwidth set aside for the Sub Pool.
–
Global Pool (BC0) BW—Bandwidth set aside for the Global Pool.
•
Tunnel Number—Tunnel number corresponding to the tunnel interface name.
–
Auto Gen—Check this box to generate the tunnel number at provisioning time. Otherwise, enter a desired number.
•
Tunnel Bandwidth—Total allocated bandwidth of this backup tunnel (display only).
•
Tunnel Pool Type—Tunnel bandwidth pool type (display only).
–
Global Pool (BC0)—Section of the total link bandwidth containing all Sub Pools for the link.
–
SubPool (BC1)—Bandwidth section nested inside the Global Pool part of the total bandwidth.
•
Setup Priority (0-7), Hold Priority (0-7), Affinity, Affinity Mask—Should not normally be used for backup tunnels. See definitions accompanying Figure A-51.
Path options:
•
Option #—Sequential number of available explicit paths.
•
Path Name—Name of the explicit path.
•
Path Type—Explicit path type (Explicit or Dynamic)
•
Lock Down—Disables reoptimization check on the tunnel, if checked.
The following actions can be performed (buttons):
•
Add—Add a path option. This opens the Select TE Explicit Path window in Figure A-52.
•
Delete—Delete a path option.
•
OK—Accept all changes and return to the TE Managed Primary Tunnels SR window.
•
Cancel—Cancel the operation and return to the TE Managed Primary Tunnels SR window.
Select TE Protected Interface
When clicking the Select button in the backup tunnel editor to select a TE protected interface, the window in Figure A-65 appears.
Figure A-65 Select TE Protected Interface
The Select TE Protected Interface window contains the following elements:
•
Interface Name—Name of the interface to be protected.
•
IP Address—IP address of the interface.
•
Next Hop—Name of the next hop device.
The following actions can be performed:
•
Select—Accept the selected interface and return to the previous window.
•
Cancel—Cancel the operation and return to the previous window.
TE Traffic Admission
This section describes the GUI elements in the TE Traffic Admission SR window.
To assign traffic to traffic-engineered tunnels, see "Traffic Admission."
Select TE Tunnel for Admission
To access the TE Traffic Admission SR window, go to Service Inventory > Inventory and Connection Manager > Traffic Engineering Management > TE Traffic Admission.
Prior to reaching the main TE Traffic Admission SR window, a tunnel has to be selected as shown in Figure A-66.
Figure A-66 Select TE Tunnel for Admission
The TE Traffic Admission SR list contains the following columns:
•
Op Type—SR operation on the tunnel, can be either ADD, MODIFY, DELETE, or ADMIT.
•
Tunnel ID—Unique tunnel identifier used within ISC TEM.
•
T#—Tunnel number on the head router.
•
Head—Hostname of the head router.
•
Dest—Hostname of the destination router.
•
Deploy Status—Can be Pending, Deployed, or Functional.
•
Type—Managed or unmanaged.
•
Policy—Tunnel policy.
TE Traffic Admission SR
After selecting a TE tunnel by clicking the corresponding radio button and clicking Select, the TE Traffic Admission SR window in Figure A-67 appears.
Figure A-67 TE Traffic Admission SR
The main TE Traffic Admission SR window contains the following fields:
•
Tunnel—Tunnel name.
•
Description—Service request description.
•
Autoroute announce—Used to specify that the Interior Gateway Protocol (IGP) should use the tunnel (if the tunnel is up) in its enhanced shortest path first (SPF) calculation.
–
On—Autoroute announce is enabled.
–
Off—Autoroute announce is disabled.
•
Autoroute Metric—Used to specify the Multiprotocol Label Switching (MPLS) traffic engineering tunnel metric that the Interior Gateway Protocol (IGP) enhanced shortest path first (SPF) calculation uses.
–
Absolute—Absolute metric mode; you can enter a positive metric value.
–
Relative—Relative metric mode; you can enter a positive, negative, or zero value.
•
Static Routes—Lists any static routes that the tunnel uses.
•
Destination—Name of the static route for the tunnel destination.
•
Mask—Prefix mask for the destination.
•
Distance—Administrative distance (cost).
The following actions can be performed:
•
Add—Add static route.
•
Edit—Edit selected static route.
•
Delete—Delete selected static routes.
•
Save SR—Save service request to the SR pool.
•
Cancel—Cancel the operation and return to the previous window.
Adminstration
As the administrative features of ISC TEM are general to ISC, some features are described in Chapter 9, "Administration", others in Cisco IP Solution Center Infrastructure Reference, 4.0.
For further clarification, see Chapter 9, "Administration".
Monitoring
This section describes the GUI elements in the following windows:
•
TE Task Logs (see also TE Task Logs, page 10-1)
•
TE Performance Reports (see also TE Performance Reports, page 10-4).
TE Task Logs
The TE task logs are used to view the result of running one or more TE tasks as described in TE Task Logs, page 10-1.
To view the task log for a TE task, three sequential steps are required:
1.
Access the Task Runtime Actions window.
2.
Select a runtime action to reach the Runtime Actions window.
3.
Select the desired log in the Task Log window.
Each window in this process is described as follows.
Note
Specific instructions for how to view a task log for a TE Discovery task are found in the TE Discovery Task Logs, page 3-6.
Task Runtime Actions
To access the Task Runtime Actions window, go to Monitoring > Task Manager. Select Logs in the table of contents on the left side of the Tasks window. The Task Runtime Actions window in Figure A-68 appears.
Figure A-68 Task Runtime Actions
The Task Runtime Actions window contains the following GUI elements:
•
Runtime Task Name—Automatically attributed task name specifying when the runtime task was created.
•
Type—Type of task, either TE Discovery, TE Functional Audit, or TE Interface Performance.
•
Start Time—The date and time when the runtime task was started.
•
End Time —The date and time when the runtime task ended.
•
Status—Indicates the result of the runtime task.
Search fields:
•
Show Runtime Tasks with Task Name matching—Type a filter string matching part of the desired Runtime Task Name.
•
of type—The type of task created using the Task Manager. The following types are available:
–
TE Discovery—Search for a TE Discovery task.
–
TE Functional Audit—Search for a TE Functional Audit task.
–
TE Interface Performance—Search for a TE Interface Performance task.
Runtime Actions
To access the Runtime Actions window, go to the Task Runtime Actions window and click the desired task in the Runtime Task Name field. This open the Runtime Actions window shown in Figure A-69.
Figure A-69 Runtime Actions
The Runtime Actions window contains the following GUI elements:
•
Refresh—Refresh the Runtime Actions table to list recently completed tasks.
•
Action—Name of the Runtime Actions log.
•
Start Time—The date and time when the runtime task was started.
•
End Time —The date and time when the runtime task ended.
•
Status—Indicates the result of the runtime task.
Task Log
To access the Task Log window, go to the Runtime Actions window and click the desired log in the Action field or select a check box and click Log. The Task Log window in Figure A-70 appears.
Figure A-70 Task Log
How the log is structured depends on the type of task that was run.
The following actions can be performed:
•
Filter—Select the desired log level, optionally enter exact Component name, and click Find.
•
Return to Logs—Return to the Runtime Actions window.
TE Performance Reports
Performance reports are created when you run a TE Interface Performance task as described in Creating a TE Interface Performance Task, page 9-11.
To view a performance report, go to Monitoring > TE Performance Report. The TE Performance Report Table in Figure A-71 appears.
Figure A-71 TE Performance Report Table
The TE Performance Report Table window contains the following GUI elements:
•
Report table—The table shows a list of Interface Performance tasks
–
Start Time—The date and time when the runtime task was started.
–
End Time—The date and time when the runtime task ended.
–
Device—Name of the device.
–
Interface—IP addresses of the interfaces on the link.
–
Octets In—Number of inbound octets of traffic.
–
Octets Out—Number of outbound octets of traffic.
–
Speed—Speed of the interface.
–
Util In—Interface utilization for inbound traffic.
–
Util Out—Interface utilization for outbound traffic
•
Reconcile Data—When an Interface Performance task has been run multiple times on an interface, you can choose to reconcile the data according to the following criteria:
–
Pick Peak—Select the highest interface utilization.
–
Pick Valley—Select the lowest interface utilization.
–
Average—Select the average interface utilization.
–
Pick First—Select the first occurrence of interface utilization.
You can perform the following actions:
•
Find—Filter out performance data according the criteria selected in the drop-down menu.
•
Cancel—Quit the report page.
•
Close—Close the Topology Display applet if open.
•
Display—Invoke the Topology Display to view selected links and/or tunnels in the network. Selected links/tunnels are displayed with a unique color.

 Feedback
Feedback