-
Cisco IP Solution Center Traffic Engineering Management User Guide, 4.0
-
Index
-
About This Guide
-
Introduction to ISC TEM
-
Setting Up the Service
-
TE Network Discovery
-
TE Resource Management
-
Basic Tunnel Management
-
Advanced Primary Tunnel Management
-
Protection Planning
-
Traffic Admission
-
Administration
-
Task Monitoring
-
TE Topology
-
Traffic Engineering Management GUI
-
Warnings and Violations
-
Document Type Definition (DTD) File
-
Table Of Contents
Managed/Unmanaged Primary Tunnels
Conformant/Non-Conformant Tunnels
Introduction to ISC TEM
This guide contains a detailed description of the Cisco IP Solution Center Traffic Engineering Management (ISC TEM) product, including the various features, the GUI, and the step-by-step processes needed to perform various traffic engineering management tasks.
This chapter contains the following sections:
•
Prerequisites and Limitations
–
Managed/Unmanaged Primary Tunnels
–
Conformant/Non-Conformant Tunnels
ISC TEM Overview
ISC TEM is the Traffic Engineering Management module of IP Solution Center. It is a tool for managing Multiprotocol Label Switching Traffic Engineering (MPLS TE) primary tunnels and backup tunnels for the purpose of offering traffic Service Level Agreement (SLA) guarantees. It provides bandwidth protection management, network discovery, and support for configuring MPLS TE. It includes a number of powerful planning tools, including a sophisticated primary path calculation tool and backup tunnel calculation for element protection.
MPLS TE mechanisms are provided to support requirements for predictability, traffic flow matched to QoS requirements, and Fast Restoration with Guaranteed Bandwidth, ensuring that strict SLA performance criteria (availability, delay, jitter) are met.
Features in ISC TEM
ISC TEM adds a range of MPLS TE primary tunnel management features:
•
Tunnel Audit—finding inconsistencies after making tunnel modifications
•
Tunnel Admission—admitting new tunnels onto the network
•
Tunnel Repair—fixing tunnel inconsistencies after network and service changes
•
Network Grooming—optimizing global network utilization.
In addition, ISC TEM offers interaction and integration with ISC features:
•
Service activation focus
•
Integration with other ISC modules (MPLS VPN, IPsec VPN, L2VPN, QoS)
•
Data Persistence
•
Logging of user intent
•
Service state management
•
Service auditing
•
Web-based GUI
•
Role-Based Access Control (RBAC)
Prerequisites and Limitations
See Cisco IP Solution Center Installation Guide for general system recommendations.
A number of requirements are associated with the TE Discovery task. These are described in TE Discovery Prerequisites.
Some features might only be available with a particular license. For more information, see Licensing Schemes.
The number of nodes provided by the license limits the size of the network.
In the Planning portion of the current implementation of ISC TEM, concurrent use is not recommended as users working simultaneously risk being unable to commit their changes.
ISC TEM Topology and Java Webstart requires JRE version 1.4.2_04.
Supported Platforms
For supported IOS platforms, see Cisco IP Solution Center Installation Guide.
Supported hardware platforms:
•
12xxx
•
75xx
•
72xx
Licensing Schemes
The ISC TEM installation comes with three types of licenses, TE, TE/RG, and TE/BRG, that gives access to all ISC TEM features, including Planning Tools for protection planning (backup tunnels).
The licensing for the TE license is based specifically on the scale of the MPLS-TE network, that is the number of nodes.
Ranges are as follows:
•
Up to 20 (starter pack)
•
Up to 50
•
Up to 100
•
Up to 150
For a larger number of nodes, please contact your Cisco sales representative.
ISC TEM Basics
To understand how ISC TEM works, certain key concepts must be explained.
Managed/Unmanaged Primary Tunnels
In ISC TEM, the concept of managed tunnels is at the center of TE planning activities.
It is important to understand the differences:
•
Managed TE tunnels:
–
(setup/hold) priority zero
–
non-zero RSVP bandwidth
–
explicit first path option
–
auto bandwidth must have a max value
•
Unmanaged tunnels: All other tunnels.
In the ISC TEM Graphical User Interface (GUI), there is a separate entry point for dealing with managed and unmanaged tunnels. The GUIs are very similar and the differences are described in Create Unmanaged TE Tunnel.
Conformant/Non-Conformant Tunnels
In the ISC TEM design, a sharp distinction has been made between conformant and non-conformant tunnels:
•
Conformant tunnel—A well-behaved tunnel that meets ISC TEM's TE management paradigm (described below). A managed tunnel can only be a conformant tunnel. A non-zero priority unmanaged tunnel would also be a conformant tunnel. However, a conformant tunnel is not necessarily a managed tunnel.
•
Non-conformant tunnel—A TE tunnel, which might impact ISC TEM's ability to meet bandwidth guarantees. This could be due to unknown bandwidth requirements such as no max bandwidth configured for auto-bandwidth, potential for pre-emption, dynamic paths, etc. A zero priority unmanaged tunnel would also be a non-conformant tunnel.
Conformant tunnels are preferred. They allow the system to offer bandwidth guarantees for managed tunnels. Unmanaged non-conformant tunnels might or might not provide the needed bandwidth and no bandwidth guarantees are given.
Non-conformant tunnels introduce factors that might not be accounted for during planning, which makes it difficult to offer bandwidth guarantees for managed tunnels. They represent an obstacle to meeting strict SLA guarantees due to their potential for impacting critical traffic on managed tunnels.
ISC TEM only allows the creation of conformant tunnels. Non-conformant tunnels can be introduced through the TE Discovery process (see "TE Network Discovery"). However, when a non-conformant tunnel is discovered a warning is logged. ISC TEM tracks non-conformant tunnels so that they can be decommissioned.
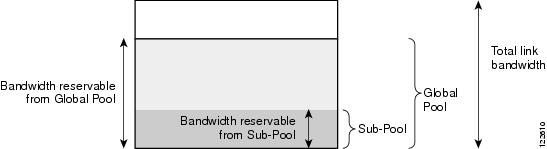
Bandwidth Pools
The bandwidth of each TE enabled interface is assigned a number of nested bandwidth pools. Currently, IOS supports two, namely Global Pool and Sub Pool.
For a better understanding of bandwidth pools, see Figure 1-1.
Figure 1-1 Bandwidth Pools
As Figure 1-1 illustrates, Sub Pool is nested inside Global Pool. Thus, if a primary tunnel reserves bandwidth from the Sub Pool, it will also reserve the same bandwidth from the Global Pool.
Bandwidth reservations (primary tunnels) from the Sub Pool must not exceed, in total, the Sub Pool size. Likewise, bandwidth reservations from the Global Pool must not exceed, in total, the Global Pool size.
Planning Tools
They are intended for evaluating planned improvements to a traffic-engineered network based on What-If scenarios .
The planning tools include the following features:
•
Primary planning tools:
–
Tunnel Audit—Audits for inconsistencies in primary placement on the existing network with or without proposed tunnel or resource changes.
–
Tunnel Placement—Usually for new tunnels. Tunnel Placement can generate a new route. It can be used for a tunnel that did not have a path before and needs to be placed.
–
Tunnel Repair—Logically performed after Tunnel Audit (if something is wrong). Tunnel Repair has re-routing capabilities and can be used to move tunnels.
–
Grooming—An optimization tool that works on the whole network. It is only available when no tunnel attributes have been changed.
•
Protection planning tools:
–
Audit SR—Audits protection for manually added, modified and deleted tunnels before they are deployed.
–
Compute Backup—Automatically calculates the optimal backup tunnel for selected network elements.
–
Audit Protection—Audits protection of the selected elements against the existing backup tunnels.
The planning tools are fully integrated within ISC TEM and are available from various locations within the GUI:
•
TE Resource Modification (Tunnel Audit, Tunnel Repair)
•
TE Protected Elements (Compute Backup and Audit Protection)
•
Create Managed TE Tunnel (Tunnel Audit, Tunnel Placement, Tunnel Repair, Grooming)
•
Create TE Backup Tunnel (Audit SR)
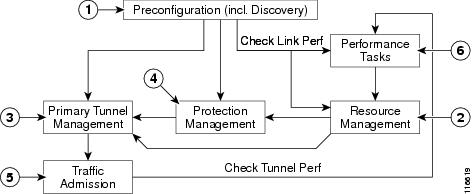
Process Flows
The following illustration shows the main components and flows in ISC TEM.
Figure 1-2 Main Process Flows in TEM
The illustration includes the following components:
•
Bootstrapping—Sets up key parameters that enable the system to collect TE network information and subsequently deploy TE configurations on the chosen network. (See "Setting Up the Service")
•
Performance Tasks—Calculates interface/tunnel bandwidth utilization using the Simple Network Management Protocol (SNMP). (See Chapter 9, "Administration")
•
Resource Management—Tuning of certain properties on the TE interfaces to optimize the tunnel placement. (See "TE Resource Management")
•
Primary Tunnel Management—Create and manage primary tunnels, either unmanaged (See "Basic Tunnel Management") or managed. (See "Basic Tunnel Management" or Chapter 6, "Advanced Primary Tunnel Management")
•
Protection Management—Protect selected elements in the network (links, routers, or SRLGs) against failure. (See "Protection Planning")
•
Traffic admission—Assign traffic to traffic-engineered tunnels. (See "Traffic Admission")

 Feedback
Feedback