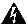-
Cisco Unified Communications Manager Express System Administrator Guide
-
Feature Map
-
Feature History
-
Cisco Unified CME Overview
-
Before You Begin
-
Installing and Upgrading Cisco Unified CME Software
- Setting Up Basic Configuration
-
Configuring Dialing Plans
-
Configuring Localization Support
-
Configuring Transcoding Resources
-
Configuring Video Transcoding
-
Configuring Toll Fraud Prevention
-
Enabling the GUI
-
Integrating Voice Mail
-
Configuring Security
-
Adding Features
-
Configuring Automatic Line Selection
-
Configuring Barge and Privacy
-
Configuring Call Blocking
-
Configuring Call Park
-
Call Restriction Regulations
-
Configuring Call Transfer and Forwarding
-
Configuring Call-Coverage Features
-
Configuring Caller ID Blocking
-
Configuring Conferencing
-
Configuring Video Conferences
-
Configuring Voice and Video Hardware Conferencing
-
Configuring Directory Services
-
Configuring Do Not Disturb
-
Configuring Enhanced 911 Services
-
Configuring Extension Mobility
-
Configuring Fax Relay
-
Configuring Feature Access Codes
-
Configuring Forced Authorization
-
Configuring Headset Auto-Answer
-
Configuring Intercom Lines
-
Configuring Loopback Call Routing
-
Configuring MLPP
-
Configuring Music on Hold
-
Configuring Paging
-
Configuring Presence Service
-
Configuring Ring Tones
-
Configuring Single Number Reach
-
Customizing Soft Keys
-
Configuring Speed Dial
-
Configuring Video Support
-
Configuring SSL VPN Client for SCCP IP Phones
-
-
Creating Templates
-
Modifying Cisco Unified IP Phone Options
-
Configuring Interoperability with Cisco Unified CCX
-
Configuring the CTI CSTA Protocol Suite
-
Configuring SRST Fallback Mode
-
Configuring VRF Support on Cisco Unified CME
-
Configuring the XML API
-
Index
-
Table Of Contents
Configuring Forced Authorization Code (FAC)
Information About Forced Authorization Code
Forced Authorization Code Overview
How to Configure Forced Authorization Code
Enabling Forced Authorization Code (FAC) on LPCOR Groups
Defining Parameters for Authorization Package
Configuration Examples for Forced Authorization Code
Feature Information for Forced Authorization Code
Configuring Forced Authorization Code (FAC)
Last Updated: February 2, 2010
This chapter describes the Forced Authorization Code (FAC) feature in Cisco Unified Communications Manager Express (Cisco Unified CME) 8.5 and later versions.
Contents
•
Information About Forced Authorization Code
•
How to Configure Forced Authorization Code
•
Configuration Examples for Forced Authorization Code
•
Feature Information for Forced Authorization Code
Information About Forced Authorization Code
To configure SNR, you should understand the following concept:
Forced Authorization Code Overview
Forced Authorization Code Overview
Cisco Unified CME 8.5 allows you to manage call access and call accounting through the Forced Authorization Code (FAC) feature. The FAC feature regulates the type of call a certain caller may place and forces the caller to enter a valid authorization code on the phone before the call is placed. FAC allows you to track callers dialing non-toll-free numbers, long distance numbers, and also for accounting and billing purposes.
In Cisco Unified CME and Cisco Voice Gateways, devices and endpoints are logically partitioned into different logical partitioning class of restriction (LPCOR) groups. For example, IP phones, Analog phones, PSTN trunks, and IP (h323/SIP) trunks as shown in Figure 39, are partitioned into five LPCOR groups under the voice lpcor custom mode, such as:
•
voice lpcor custom
–
group 10 Manager
–
group 11 LocalUser
–
group 12 RemoteUser
–
group 13 PSTNTrunk
–
group 14 IPTrunk
Figure 39 Forced Authorization Code Network Overview
For each group, the LPCOR group policy of a routing endpoint is enhanced to define incoming calls from individual LPCOR groups that are restricted by FAC. A LPCOR group call to a destination is accepted only when a valid FAC is entered. FAC service for a routing endpoint is enabled through the service fac defined in a LPCOR group policy. For more information, see Enabling Forced Authorization Code (FAC) on LPCOR Groups.
The following are the group policy rules applicable to the PSTNTrunk LPCOR group:
–
FAC is required by PSTNTrunk if a call is initiated from either LocalUser or RemoteUser group.
–
Any calls from Manager group are allowed to terminate to PSTNTrunk without restriction.
–
Any incoming calls from either IPTrunk or PSTNTrunk group are rejected and terminated to PSTNTrunk group.
For information on configuring LPCOR groups and associating LPCOR group with different device types, see Call Restriction Regulations.
FAC Call Flow
FAC is required for an incoming call based on the LPCOR policy defined for the call destination. Once the authentication is finished, the success or failure status and the collected FAC digits are saved to the call detail records (CDRs).
Calls are handled by a new built-in application authorization package which first plays a user-prompt for the caller to enter a username (in digits) then, the application plays a passwd-prompt for the caller to collect the password (in digits). The collected username and password digits are then used for FAC, see Defining Parameters for Authorization Package.
When FAC authentication is successful, the outgoing call setup is continued to the same destination. If FAC authentication fails, the call is then forwarded to the next destination. FAC operations are invoked to the call if FAC service is enabled in the next destination and no valid FAC status is saved for the call.
Any calls failing because of FAC blocking are disconnected with a LPCOR Q.850 disconnect cause code. Once the FAC is invoked for a call, the collected authorization digits and the authentication status information is collected by call active or call history records. You can retrieve the FAC information through the show call active voice and show call history voice commands.
Forced Authorization Code Specification
The authorization code used for call authentication must follow these specifications:
•
The authorization code must be in numeric (0 - 9) format.
•
A digit collection operation must be completed if either one of the following conditions occur:
–
maximum number of digits are collected
–
digit input times out
–
a terminating digit is entered
Once digit collection is completed, the authentication is done by either the external Radius server or Cisco Unified CME or Cisco Voice Gateways by using AAA Login Authentication setup. For more information on AAA login authentication methods, see Configuring Login Authentication Using AAA.
When authentication is done by local Cisco Unified CME or Cisco Voice Gateways, the username ac-code password 0 password command is required to authenticate the collected authorization code digits.
FAC data is stored through the CDR and new AAA fac-digits and fac-status attributes and are supported in a CDR STOP record. This CDR STOP record is formatted for file accounting, RADIUS or Syslog accounting purpose.
FAC Requirement for Different Types of Calls
Table 57 shows FAC support for different types of calls.
How to Configure Forced Authorization Code
This section contains the following task:
•
Enabling Forced Authorization Code (FAC) on LPCOR Groups
•
Defining Parameters for Authorization Package
Enabling Forced Authorization Code (FAC) on LPCOR Groups
To enable FAC, perform the following steps.
Prerequisites
•
You must enable the voice lpcor enable command before configuring FAC.
•
Trunks (IP and PSTN) must be associated with phones into different LPCOR groups. See the Associating a LPCOR Policy with Analog Phone or PSTN Trunk Calls for more information.
Restrictions
•
Authenticated FAC data is saved to a call-leg from which the authorization code is collected. When a call-forward or blind transfer call scenario triggers a new call due to the SIP notify feature, the same caller is required to enter the authorization code again for FAC authentication.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
voice lpcor enable
4.
voice lpcor custom
5.
group number lpcor-group
6.
exit
7.
voice lpcor policy lpcor-group
8.
accept lpcor-group fac
9.
service fac
10.
end
DETAILED STEPS
Examples
Router# show voice lpcor policy
voice lpcor policy PSTNTrunk (group 13):
service fac is enabled
( accept ) Manager (group 10)
( reject ) LocalUser (group 11)
( reject ) RemoteUser (group 12)
( accept ) PSTNTrunk (group 13)
( reject ) IPTrunk (group 14)
Defining Parameters for Authorization Package
To define required parameters for user name and password, follow these steps:
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
application
4.
package auth
5.
param passwd string
6.
param user-prompt filename
7.
param passwd-prompt filename
8.
param max-retries
9.
param term-digit
10.
param abort-digit
11.
param max-digits
12.
exit
DETAILED STEPS
Configuration Examples for Forced Authorization Code
This section provides configuration example for Forced Authorization Code.
!
gw-accounting aaa
!
aaa new-model
!
aaa authentication login default local
aaa authentication login h323 local
aaa authorization exec h323 local
aaa authorization network h323 local
!
aaa session-id common
!
voice lpcor enable
voice lpcor custom
group 11 LocalUser
group 12 AnalogPhone
!
voice lpcor policy LocalUser
service fac
accept LocalUser fac
accept AnalogPhone fac
!
voice lpcor policy AnalogPhone
service fac
accept LocalUser fac
accept AnalogPhone fac
!
application
package auth
param passwd-prompt flash:en_bacd_welcome.au
param passwd 54321
param user-prompt flash:en_bacd_enter_dest.au
param term-digit #
param abort-digit *
param max-digits 32
!
username 786 password 0 54321
!
voice-port 0/1/0
station-id name Phone1
station-id number 1235
caller-id enable
!
voice-port 0/1/1
lpcor incoming AnalogPhone
lpcor outgoing AnalogPhone
!
dial-peer voice 11 pots
destination-pattern 99329
port 0/1/1
!
ephone-dn 102 dual-line
number 786786
label HussainFAC
!
!
ephone 102
lpcor type local
lpcor incoming LocalUser
lpcor outgoing LocalUser
device-security-mode none
mac-address 0005.9A3C.7A00
type CIPC
button 1:102
!
Additional References
The following sections provide references related to Cisco Unified CME features.
Related Documents
Cisco Unified CME configuration
•
Cisco Unified CME Command Reference
Cisco IOS commands
•
Cisco IOS Voice Command Reference
Cisco IOS configuration
•
Cisco IOS Voice Configuration Library
Phone documentation for Cisco Unified CME
Technical Assistance
Feature Information for Forced Authorization Code
Table 58 lists the features in this module and enhancements to the features by version.
To determine the correct Cisco IOS release to support a specific Cisco Unified CME version, see the Cisco Unified CME and Cisco IOS Software Version Compatibility Matrix at http://www.cisco.com/en/US/docs/voice_ip_comm/cucme/requirements/guide/33matrix.htm.
Use Cisco Feature Navigator to find information about platform support and software image support. Cisco Feature Navigator enables you to determine which Cisco IOS software images support a specific software release, feature set, or platform. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Note
Table 58 lists the Cisco Unified CME version that introduced support for a given feature. Unless noted otherwise, subsequent versions of Cisco Unified CME software also support that feature.
Table 58 Feature Information for Single Number Reach
Forced Authorization Code
8.5
Introduced the FAC feature.

 Feedback
Feedback