-
Cisco 10000 Series Router Software Configuration Guide
-
About This Guide
-
Broadband Aggregation and Leased-Line Overview
-
Scalability and Performance
-
Configuring Remote Access to MPLS VPN
-
Configuring Multiprotocol Label Switching
-
Configuring the Layer 2 Tunnel Protocol Access Concentrator and Network Server
-
Configuring PPPoE over Ethernet and IEEE 802.1Q VLAN
-
Configuring IP Unnumbered on IEEE 802.1Q VLANs
-
Configuring ATM Permanent Virtual Circuit Autoprovisioning
-
Configuring the Multihop Feature
-
Configuring Address Pools
-
Configuring Local AAA Server, User Database--Domain to VRF
-
Configuring Traffic Filtering
-
Unicast Reverse Path Forwarding
-
Configuring Automatic Protection Switching
-
Configuring IP Multicast
-
Configuring RADIUS Features
-
Cisco 10000 Series Router PXF Stall Monitor
-
SSO - BFD
-
Configuring Link Noise Monitoring
-
Configuring L2 Virtual Private Networks
-
Configuring L2VPN Interworking
-
Configuring Multilink Point-to-Point Protocol Connections
-
Configuring Gigabit EtherChannel Features
-
Configuring IP Version 6
-
Configuring Template ACLs
-
Protecting the Router from DoS Attacks
-
IP Tunneling
-
RADIUS Attributes
-
Glossary
-
Table Of Contents
Configuring Local AAA Server, User Database—Domain to VRF
Feature History for Local AAA Server, User Database—Domain to VRF
Prerequisites for Local AAA Server, User Database—Domain to VRF
Converting from RADIUS Format to Cisco IOS AAA Format
Configuration Tasks for Local AAA Server, User Database—Domain to VRF Using Local Attributes
Defining RADIUS and Enabling NAS-PORT
Applying AAA to a Virtual Template
Defining an AAA Attribute List
Verifying Local AAA Server, User Database—Domain to VRF Using Local Attributes
Configuration Example for Local AAA Server, User Database—Domain to VRF
Monitoring and Maintaining Local AAA Server, User Database—Domain to VRF
Configuring Local AAA Server, User Database—Domain to VRF
The Local AAA Server, User Database—Domain to VRF feature extends the Cisco IOS AAA Authorization to local AAA profiles on the router without using an AAA Server. The local user database acts as a local AAA server, and is fully compatible with any external AAA Server. If you want to maintain your user database locally or provide a failover local mechanism, you no longer have to sacrifice policy options when defining local users.
This flexibility allows you to provide complete user authentication and authorization locally within Cisco IOS without using an AAA Server, provided the local username list is relatively small. While authentication can be done on the router for a limited number of user names, it might make more sense and be much more scalable to use an AAA Server. Note that accounting is still be done on an AAA server and is not be supported on the router.
The key function that this feature provides is a mapping of user domain names to local AAA profiles. This allows AAA attributes to be applied to the PPP session as part of the PPP session establishment. These local AAA attributes are RADIUS attributes that would normally be defined on a Radius Server but now are defined locally on the router.
Subscriber profiles are used to match user domain names, and on a match to use a defined AAA attribute list. The AAA attribute list contains a list of valid Cisco IOS format AAA attributes.
Note
Domain to subscriber profile matching is a global match. Limiting which domains are permitted or denied per PPPoE bba-group or PVC is not supported.
This chapter describes the Local AAA Server, User Database—Domain to VRF feature in the following topics:
•
Feature History for Local AAA Server, User Database—Domain to VRF
•
Prerequisites for Local AAA Server, User Database—Domain to VRF
•
Establishing a PPP Connection
•
Configuration Tasks for Local AAA Server, User Database—Domain to VRF Using Local Attributes
•
Verifying Local AAA Server, User Database—Domain to VRF Using Local Attributes
•
Configuration Example for Local AAA Server, User Database—Domain to VRF
•
Monitoring and Maintaining Local AAA Server, User Database—Domain to VRF
Feature History for Local AAA Server, User Database—Domain to VRF
12.3(7)XI1
This feature was introduced on the Cisco 10000 series router.
PRE2
12.2(28)SB
This feature was integrated into Cisco IOS Release 12.2(28)SB.
PRE2
Prerequisites for Local AAA Server, User Database—Domain to VRF
The Local AAA Server, User Database—Domain to VRF feature has the following requirements:
•
Configure an external AAA as described in Cisco IOS Security Configuration Guide, Cisco IOS Release 12.2.
Establishing a PPP Connection
The following example describes the sequence of events involved in setting up AAA authentication, authorization, and accounting when a PPP connection is established and a local AAA server is used.
AAA Authentication
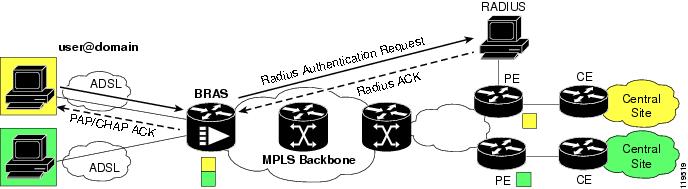
Figure 11-1 shows the AAA authentication set up when establishing a PPP connection.
Figure 11-1 AAA Authentication
In the figure, the PPP client attempts to establish a PPP session with user@domain. This PAP or CHAP user name request is forwarded to the broadband remote access server (BRAS) for authentication. Authentication could be done locally on the BRAS, but in most cases the authentication is forwarded to a RADIUS server. The RADIUS server looks up the user@domain or user (if the BRAS strips off the domain), and if found sends a RADIUS ACK back to the BRAS. The BRAS sends a PAP or CHAP ACK back to the PPP client.
AAA Authorization
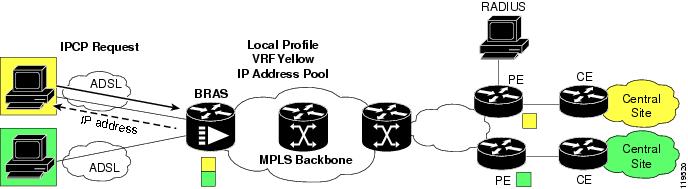
Figure 11-2 shows the AAA authorization set up when establishing a PPP connection.
Figure 11-2 AAA Authorization
In the figure, the PPP client requests an IP address using PPP IPCP to the BRAS. The BRAS does a match of the domain to a local profile. This local profile contains the VRF to assign to this PPP session. The BRAS replies back to the PPP client with an IP address from the defined IP address pool in the local profile.
AAA Accounting
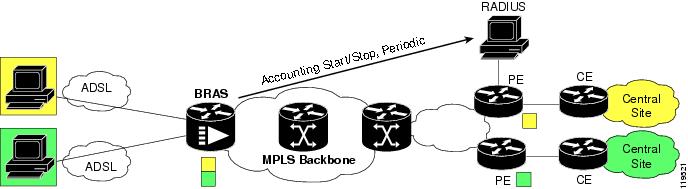
Figure 11-3 shows the AAA accounting set up when establishing a PPP connection.
Figure 11-3 AAA Accounting
In the figure, the BRAS can be configured to provide AAA accounting start/stop and periodic records for each PPP session. The BRAS can also be configured to provide NAS-Port information in the accounting records that will detail the slot/card/interface and VPI/VCI or VLAN.
AAA Attribute Lists
AAA Attribute Lists are used by the subscriber profiles when there is a match of the user name domain. These lists define RADIUS user profiles local to the router. The attributes are available for configuration using the aaa attribute list name global configuration command. Every attribute known to AAA is made available for configuration.
The AAA attributes that are defined in the AAA attribute list are standard RADIUS attributes, however they are in the Cisco IOS AAA format of the attribute. You must convert the attributes from RADIUS format to Cisco IOS AAA format.
Converting from RADIUS Format to Cisco IOS AAA Format
Use the show aaa attribute protocol radius command to get the Cisco IOS AAA format of the IETF RADIUS Attribute. This provides a complete list of all the aaa attributes supported. The following is an example where you need to convert the RADIUS attribute Filter-Id to Cisco IOS AAA format. This example represents part of the output of the show aaa attribute protocol radius command.
IIETF defined attributes:
Type=4 Name=acl Format=UlongProtocol:RADIUSUnknown Type=11 Name=Filter-Id Format=BinaryCisco IOS converts the IETF RADIUS attribute 11 (Filter-Id) of type Binary into an internal attribute named acl of type Ulong. Now you can configure this attribute locally using the attribute type acl.
Note
You cannot add new AAA attributes during the conversion process. The conversion is only making the attributes configurable and usable locally on the router. The defined local AAA attributes must be supported RADIUS attributes.
Defining AAA Attribute Lists
Typically, you define an AAA attribute list for each user name domain. Cisco IOS Release 12.3(7)XI1 introduces the following two new commands to define local AAA attribute lists and attribute types:
The following is an example of the commands you use to configure method lists:
aaa attribute list <name>attribute type <name> <value> <service> <protocol> <tag>Subscriber Profiles
Subscriber profiles are used to match user domain names, and on a match to use a defined AAA attribute list. Cisco IOS Release 12.3(7)XI1 introduces the following new command to define subscriber profiles:
The following is an example of the commands you use to configure a subscriber profile:
subscriber authorization enablesubscriber profile domain-nameservice localaaa attribute list aaa attribute list nameAAA Method Lists
The AAA method lists are defined to use RADIUS for authentication and accounting. Authorization is done locally using the AAA attribute lists. Defining the AAA attribute lists for PPP under the virtual template no longer requires defining the AAA lists. Instead, a default authentication and authorization list can be defined on the virtual template and the AAA method lists can be defined in the AAA attribute lists. 2000 method lists are supported.
Using method lists does require that you define aaa authentication ppp default and aaa authorization network default lists. The following is an example of the commands you use to configure method lists:
interface virtual-templateppp authentication pap chapaaa new-modelaaa authentication ppp default localaaa authorization network default localaaa authentication ppp method list name group radiusaaa authorization network method list name local if-authenticatedaaa accounting network method list name start-stop group radiusaaa attribute list <domain name>attribute type ppp-authen-list "method list name"attribute type ppp-author-list "method list name"attribute type ppp-acct-list "method list name"Configuration Tasks for Local AAA Server, User Database—Domain to VRF Using Local Attributes
To configure a user name domain to a VRF using local AAA attributes, perform the following configuration tasks:
•
Defining RADIUS and Enabling NAS-PORT
•
Applying AAA to a Virtual Template
•
Defining a Loopback Interface
•
Defining a Subscriber Profile
•
Defining an AAA Attribute List
Defining AAA
To define AAA (authentication, authorization, and accounting), enter the following commands in global configuration mode:
Defining RADIUS and Enabling NAS-PORT
To define RADIUS and enable NAS-PORT, enter the following commands in global configuration mode:
Defining a VRF
To define a VRF, enter the following commands beginning in global configuration mode:
Applying AAA to a Virtual Template
To apply AAA to a virtual template, enter the following commands in global configuration mode:
Defining a Loopback Interface
To define a loopback interface, enter the following commands in global configuration mode:
Creating an IP Address Pool
To an IP address pool, enter the following command in global configuration mode:
Step 1
Router(config)# ip local pool start address end address
Defines an IP pool from which the PPP sessions are IP addresses.
Defining a Subscriber Profile
To define a subscriber profile, enter the following commands in global configuration mode:
Defining an AAA Attribute List
To define AAA attribute list, enter the following commands in global configuration mode:
Verifying Local AAA Server, User Database—Domain to VRF Using Local Attributes
To verify domain to VRF using local attributes, use the show aaa users all command and the show running-config command. See the next section for a configuration example.
Configuration Example for Local AAA Server, User Database—Domain to VRF
The following configuration example has two subscriber profiles that match on domain cisco1.com and cisco2.com.
A subscriber with the domain name cisco1.com uses the parameters defined in the subscriber profile cisco1.com. The name of the subscriber profile must be identical to the domain part of the full username (username@domain). An attribute list cisco1.com defined in the service profile is used to reference AAA attributes for the PPP subscribers.
Subscriber cisco1.com is applied with AAA attributes from AAA attribute list cisco1.com. An attribute is applied to put the PPP session into a VRF called vrf1. An IP address is assigned from a local DHCP pool called dhcp-pool. AAA authentication, authorization, and accounting are also defined and use an AAA list called test1. These all use an AAA group server called group_server_test1.
A subscriber with the domain name cisco2.com uses the parameters defined in the subscriber profile cisco2.com. The name of the subscriber profile must be identical to the domain part of the full username (username@domain). An attribute list cisco2.com defined in the service profile is used to reference aaa attributes for the PPP subscribers.
Subscriber cisco2.com is applied with AAA attributes from AAA attribute list cisco2.com. An attribute is applied to put the PPP session into a VRF called vrf2. An IP address is assigned from a local pool called pppoe2. AAA authentication, authorization, and accounting are also defined and use an AAA list called test2. These all use an AAA group server called group_server_test2.
aaa new-model!!aaa group server radius group_server_test1server-private 192.168.2.20 auth-port 1645 acct-port 1646 key ciscoip vrf forwarding vrf1!aaa group server radius group_server_test2server-private 192.168.2.12 auth-port 1645 acct-port 1646 key ciscoip vrf forwarding vrf2!aaa authentication ppp default localaaa authentication ppp test1 group test1aaa authentication ppp test2 group test2aaa authorization network default localaaa authorization network test1 local if-authenticatedaaa authorization network test2 local if-authenticatedaaa accounting delay-start allaaa accounting network test1 start-stop group group_server_test1aaa accounting network test2 start-stop group group_server_test2!aaa attribute list cisco1.comattribute type addr-pool "dhcp-pool" protocol ipattribute type ip-unnumbered "loopback1" service ppp protocol ipattribute type vrf-id "vrf1" service ppp protocol ipattribute type ppp-authen-list "test1"attribute type ppp-author-list "test1"attribute type ppp-acct-list "test1"!aaa attribute list cisco2.comattribute type addr-pool "pppoe2" protocol ipattribute type ip-unnumbered "loopback2" service ppp protocol ipattribute type vrf-id "vrf2" service ppp protocol ipattribute type ppp-authen-list "test2"attribute type ppp-author-list "test2"attribute type ppp-acct-list "test2"!ip dhcp pool dhcp-poolvrf vrf1network 101.1.0.0 255.255.0.0default-router 100.1.1.1lease 0 2 30!ip vrf vrf1rd 1:1route-target export 1:1route-target import 1:1!ip vrf vrf2rd 2:2route-target export 2:2route-target import 2:2!subscriber authorization enable!subscriber profile cisco1.comservice localaaa attribute list cisco1.com!subscriber profile cisco2.comaaa attribute list cisco2.com!vpdn enable!ppp hold-queue 80000no virtual-template snmp!buffers small permanent 15000buffers middle permanent 12000buffers large permanent 1000!bba-group pppoe cisco1.comvirtual-template 1!bba-group pppoe cisco2.comvirtual-template 2!interface Loopback1ip vrf forwarding vrf1ip address 100.1.1.1 255.255.255.255!interface Loopback2ip vrf forwarding vrf2ip address 101.1.1.1 255.255.255.255!interface FastEthernet0/0/0shutdown!interface ATM1/0/0no ip addressno atm pxf queuingno atm ilmi-keepalive!interface ATM1/0/0.1 multipointpvc 1/32encapsulation aal5autoppp Virtual-Template1 group cisco1.comno create on-demand!!interface ATM1/0/0.2 multipointpvc 1/33encapsulation aal5autoppp Virtual-Template2 group cisco2.com!!interface FastEthernet6/0/0ip vrf forwarding vrf1ip address 192.168.2.201 255.255.255.0duplex auto!interface FastEthernet6/0/1ip vrf forwarding vrf2ip address 192.168.2.202 255.255.255.0duplex auto!interface Virtual-Template1no ip addressno logging event link-statusno snmp trap link-statusppp mtu adaptiveppp authentication chap callin!ip local pool pppoe2 12.1.1.1 12.1.250.1!ip radius source-interface FastEthernet6/0/0.1 vrf vrf1ip radius source-interface FastEthernet6/0/0.2 vrf vrf2!radius-server attribute nas-port format dradius-server domain-strippingExample—VRF with DBS
Applying the PCR and SCR to this PPP:
aaa attribute list cisco1.comattribute type addr-pool "pppoe" protocol ipattribute type ip-unnumbered "loopback1" service ppp protocol ipattribute type vrf-id "vrf1" service ppp protocol ipattribute type peak-cell-rate 2048 protocol atmattribute type sustainable-cell-rate 1024 protocol atmExample—VRF with ACL
Applying a defined output ACL to this PPP:
aaa attribute list cisco1.comattribute type addr-pool "pppoe" protocol ipattribute type ip-unnumbered "loopback1" service ppp protocol ipattribute type vrf-id "vrf1" service ppp protocol ipattribute type outacl "101" service ppp protocol ipaccess-list 101 deny icmp any anyMonitoring and Maintaining Local AAA Server, User Database—Domain to VRF
The following debug commands can be helpful in monitoring and maintaining Local AAA Server, User Database—Domain to VRF:
•
debug aaa id—displays a unique key for a session and provides a way to track sessions
•
debug aaa authentication—displays the methods of authentication being used and the results of these methods
•
debug aaa authorization—displays the methods of authorization being used and the results of these methods
•
debug aaa per-user—displays information about per-user QoS parameters
•
debug ppp negotiation—shows PPP negotiation debug messages
•
debug ppp authen—indicates if a client is passing authentication
•
debug ppp error—displays protocol errors and error statistics associated with PPP connection negotiation and operation
•
debug ppp forward—displays who is taking control of a session
•
debug sss error—displays diagnostic information about errors that may occur during Subscriber Service Switch (SSS) call setup
•
debug radius—displays information about the RADIUS server
CautionBecause debugging output is assigned high priority in the CPU process, it can render the system unusable. For this reason, use debug commands only to troubleshoot specific problems or during troubleshooting sessions with Cisco Systems technical support personnel. Moreover, it is best to use debug commands during periods of lower network traffic and fewer users. Debugging during these periods decreases the likelihood that increased debug command processing overhead will affect system use.

 Feedback
Feedback