-
Cisco IOS Software Configuration Guide for Cisco Aironet 1300 Series Outdoor Access Point/Bridge 12.3(7)JA
-
Preface
-
Overview
-
Configuring the Access Point/Bridge for the
-
Using the Web-Browser Interface
-
Using the Command-Line Interface
-
Administering the Access Point/Bridge
-
Configuring Radio Settings
-
Configuring Multiple SSIDs
-
Configuring Spanning Tree Protocol
-
Configuring Cipher Suites and WEP
-
Configuring Authentication Types
-
Configuring WDS, Fast Secure Roaming, Radio Management, and Wireless Intrusion Detection Services
-
Configuring RADIUS and TACACS+ Servers
-
Configuring VLANs
-
Configuring QoS
-
Configuring Filters
-
Configuring CDP
-
Configuring SNMP
-
Managing Firmware and Configurations
-
Configuring System Message Logging
-
Configuring Repeater and Standby Access Points and Workgroup Bridge Mode
-
Troubleshooting
-
Protocol Filters
-
Supported MIBs
-
Error and Event Messages
-
Glossary
-
Table Of Contents
Using the Web-Browser Interface
Using the Web-Browser Interface for the First Time
Using the Management Pages in the Web-Browser Interface
Character Restrictions in Entry Fields
Enabling HTTPS for Secure Browsing
Changing the Location of Help Files
Disabling the Web-Browser Interface
Using the Web-Browser Interface
This chapter describes the web-browser interface that you can use to configure the access point/bridge. It contains these sections:
•
Using the Web-Browser Interface for the First Time
•
Using the Management Pages in the Web-Browser Interface
•
Enabling HTTPS for Secure Browsing
•
Disabling the Web-Browser Interface
The web-browser interface contains management pages that you use to change access point/bridge settings, upgrade firmware, and monitor and configure other wireless devices on the network.
Note
The access point/bridge web-browser interface is fully compatible with these browsers: Microsoft Internet Explorer versions 6.0 on Windows 98, 2000, and XP platforms, and with Netscape version 7.0 on Windows 98, Windows 2000, and Solaris platforms.
Note
Avoid using the CLI and the web-browser interfaces to configure the access point/bridge. Use one or the other. If you configure the access point/bridge using the CLI, the web-browser interface might display an inaccurate interpretation of the configuration. However, the inaccuracy does not necessarily mean that the access point/bridge is misconfigured.
Using the Web-Browser Interface for the First Time
Use the access point/bridge's IP address to browse to the management system. See the "Obtaining and Assigning an IP Address" section for instructions on assigning an IP address to the access point/bridge.
Follow these steps to begin using the web-browser interface:
Step 1
Start the browser.
Step 2
Enter the access point/bridge's IP address in the browser Location field (Netscape Communicator) or Address field (Internet Explorer) and press Enter.
Step 3
Enter the administrator username and password and press Enter. The default username is Cisco and the default password is Cisco. The Summary Status page appears.
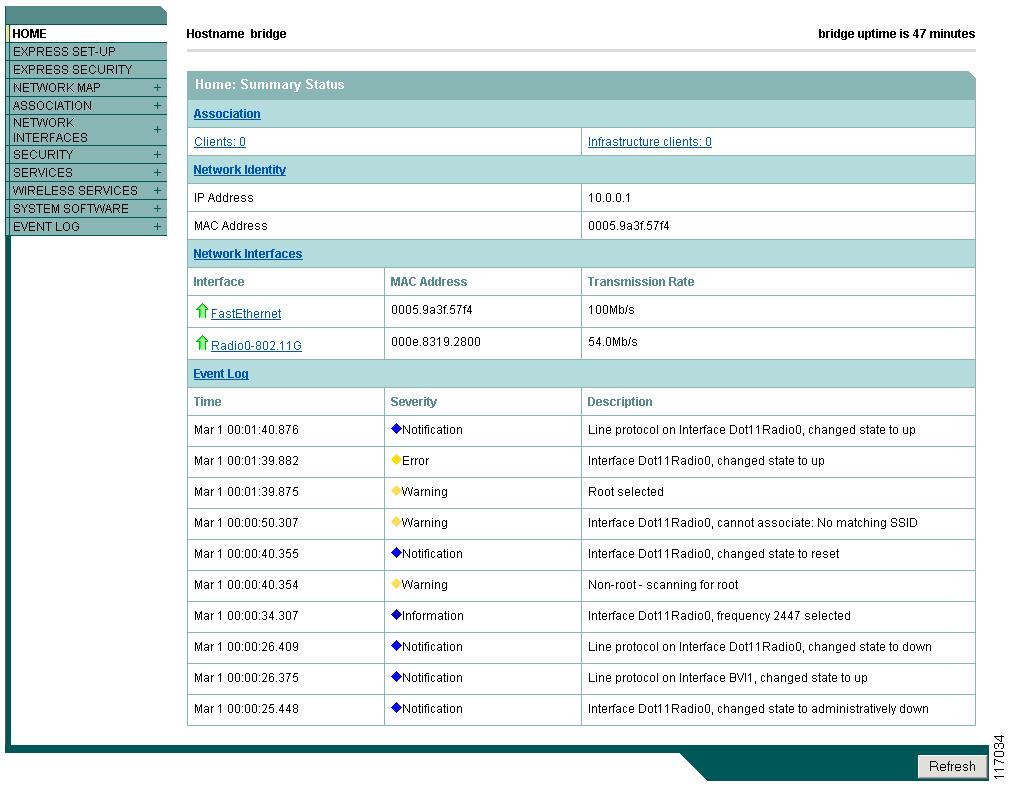
Using the Management Pages in the Web-Browser Interface
The system management pages use consistent techniques to present and save configuration information. A navigation bar is on the left side of the page, and configuration action buttons appear at the bottom. You use the navigation bar to browse to other management pages, and you use the configuration action buttons to save or cancel changes to the configuration.
Note
It is important to remember that clicking your browser's Back button returns you to the previous page without saving any changes you have made. Clicking Cancel cancels any changes you made on the page and keeps you on that page. Changes are only applied when you click Apply.
Figure 3-1 shows the web-browser interface home page.
Figure 3-1 Web-Browser Interface Home Page
Using Action Buttons
Table 3-1 lists the page links and buttons that appear on most management pages.
Character Restrictions in Entry Fields
Because the 1300 series access point/bridge uses Cisco IOS software, there are certain characters that you cannot use in the entry fields on the web-browser interface. You cannot use these characters in entry fields:
"
]
+
/
Tab
Trailing spaceEnabling HTTPS for Secure Browsing
You can protect communication with the access point/bridge web-browser interface by enabling HTTPS. HTTPS protects HTTP browser sessions by using the Secure Socket Layer (SSL) protocol.
Note
When you enable HTTPS, your browser might lose its connection to the access point/bridge. If you lose the connection, change the URL in your browser's address line from http://ip_address to https://ip_address and log into the access point again.
Note
When you enable HTTPS, most browsers prompt you for approval each time you browse to a device that does not have a fully qualified domain name (FQDN). To avoid the approval prompts, complete Step 2 through Step 9 in these instructions to create an FQDN for the access point. However, if you do not want to create an FQDN, skip to Step 10.
Follow these steps to create an FQDN and enable HTTPS:
Step 1
If your browser uses popup-blocking software, disable the popup-blocking feature.
Step 2
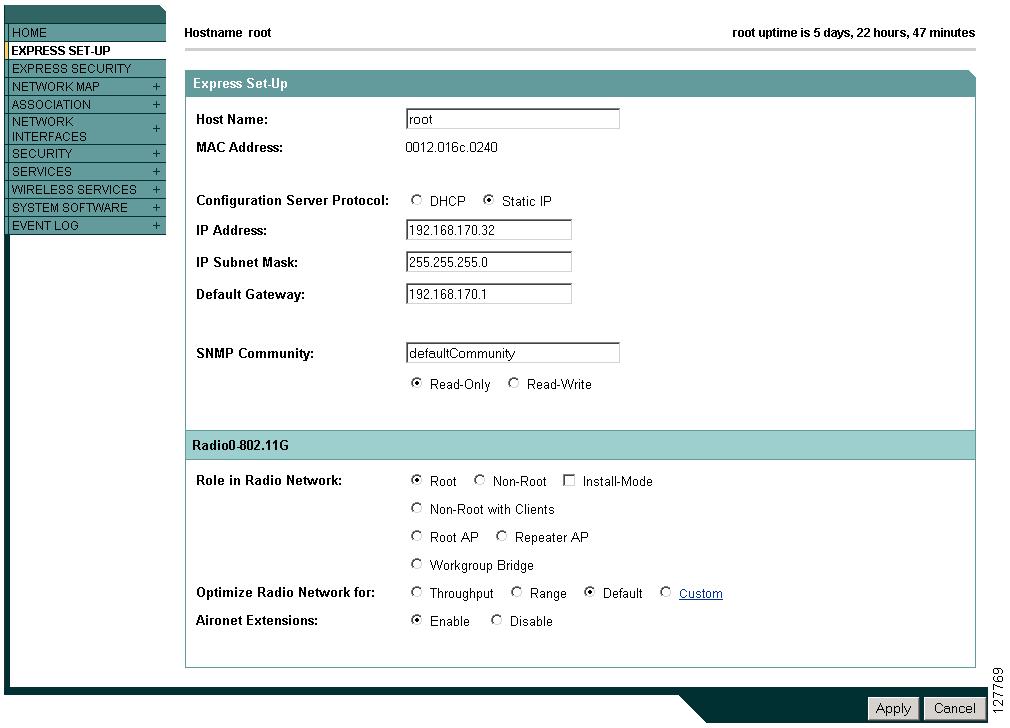
Browse to the Express Setup page. Figure 3-2 shows the Express Setup page.
Figure 3-2 Express Setup Page
Step 3
Enter a name for the access point/bridge in the System Name field and click Apply.
Step 4
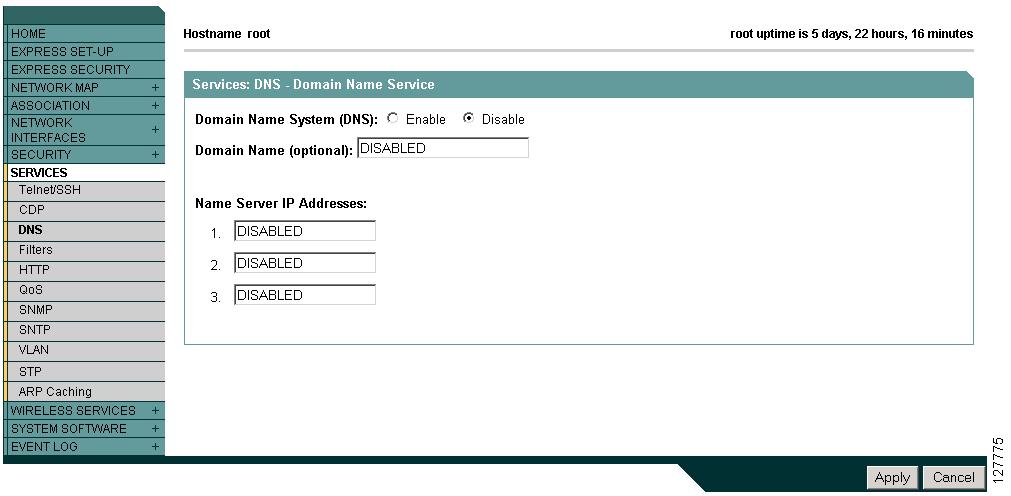
Browse to the Services - DNS page. Figure 3-3 shows the Services - DNS page.
Figure 3-3 Services - DNS Page
Step 5
Select Enable for Domain Name System.
Step 6
In the Domain Name field, enter your company's domain name. At Cisco Systems, for example, the domain name is cisco.com.
Step 7
Enter at least one IP address for your DNS server in the Name Server IP Addresses entry fields.
Step 8
Click Apply. The access point/bridge's FQDN is a combination of the system name and the domain name. For example, if your system name is br 1310 and your domain name is company.com, the FQDN is br1310.company.com.
Step 9
Enter the FQDN on your DNS server.
Tip
If you do not have a DNS server, you can register the access point/bridge's FQDN with a dynamic DNS service. Search the Internet for dynamic DNS to find a fee-based DNS service.
Step 10
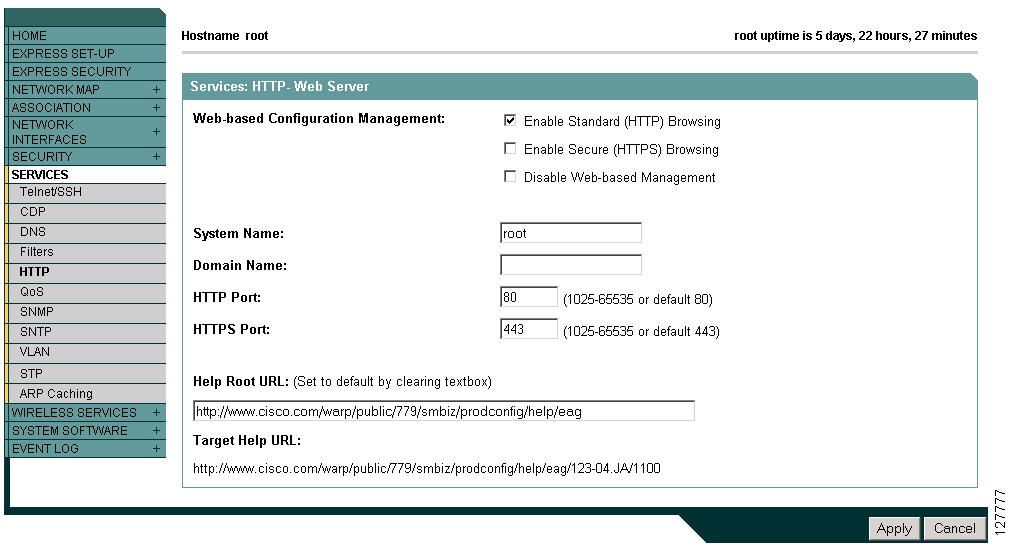
Browse to the Services: HTTP Web Server page. Figure 3-4 shows the HTTP Web Server page:
Figure 3-4 Services: HTTP Web Server Page
Step 11
Select the Enable Secure (HTTPS) Browsing check box and click Apply.
Note
Although you can enable both standard HTTP and HTTPS, Cisco recommends that you enable one or the other.
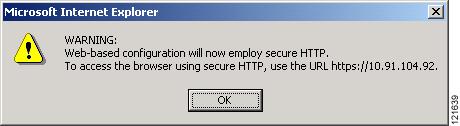
A warning window appears stating that you will use HTTPS to browse to the access point. The window also instructs you to change the URL that you use to browse to the access point/bridge from http to https. Figure 3-5 shows the warning window:
Figure 3-5 HTTPS Warning Window
Step 12
Click OK. The address in your browser's address line changes from http://ip-address to https://ip-address.
Step 13
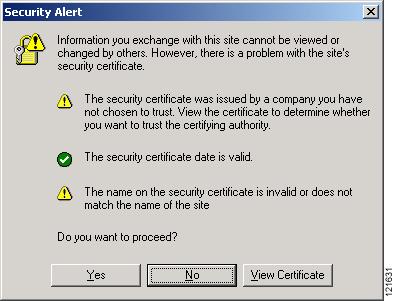
Another warning window appears stating that the access point's security certificate is valid but is not from a known source. However, you can accept the certificate with confidence because the site in question is your own access point. Figure 3-6 shows the certificate warning window:
Figure 3-6 Certificate Warning Window
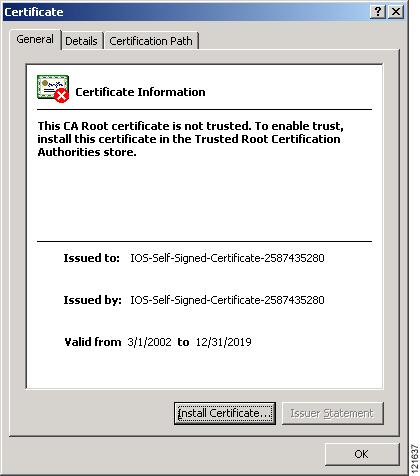
Step 14
Click View Certificate to accept the certificate before proceeding. (To proceed without accepting the certificate, click Yes, and skip to Step 23 in these instructions.) Figure 3-7 shows the Certificate window.
Figure 3-7 Certificate Window
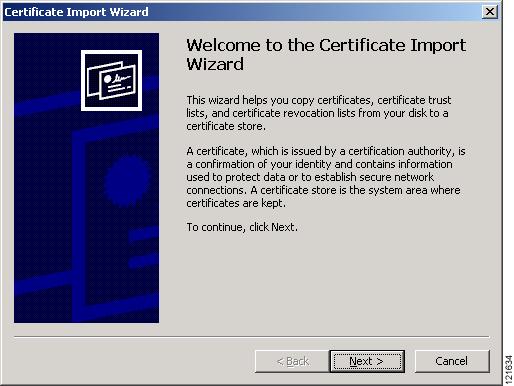
Step 15
On the Certificate window, click Install Certificate. The Microsoft Windows Certificate Import Wizard appears. Figure 3-8 shows the Certificate Import Wizard window.
Figure 3-8 Certificate Import Wizard Window
Step 16
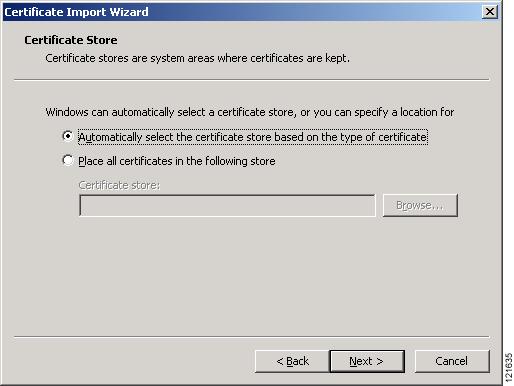
Click Next. The next window asks where you want to store the certificate. Cisco recommends that you use the default storage area on your system. Figure 3-9 shows the window that asks about the certificate storage area.
Figure 3-9 Certificate Storage Area Window
Step 17
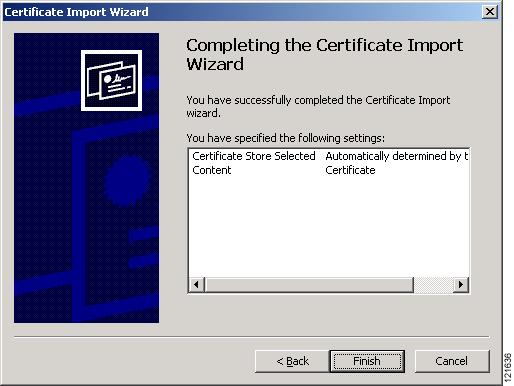
Click Next to accept the default storage area. A window appears that states that you successfully imported the certificate. Figure 3-10 shows the completion window.
Figure 3-10 Certificate Completion Window
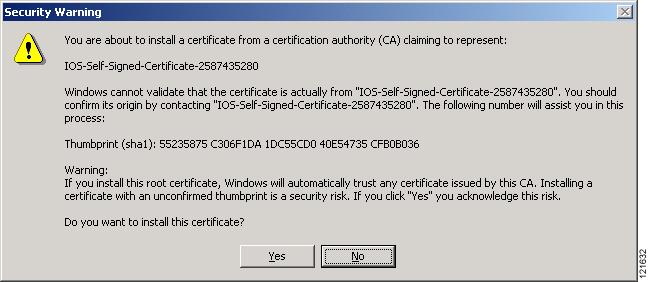
Step 18
Click Finish. Windows displays a final security warning. Figure 3-11 shows the security warning.
Figure 3-11 Certificate Security Warning
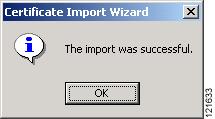
Step 19
Click Yes. Windows displays another window stating that the installation is successful. Figure 3-12 shows the completion window.
Figure 3-12 Import Successful Window
Step 20
Click OK.
Step 21
On the Certificate window shown in Figure 3-7, which is still displayed, click OK.
Step 22
On the Security Alert window shown in Figure 3-6, click Yes.
Step 23
The access point login window appears and you must log into the access point again. The default user name is Cisco (case-sensitive) and the default password is Cisco (case-sensitive).
CLI Configuration Example
This example shows the CLI commands that are equivalent to the steps listed in the "Using Online Help" section:
ap# configure terminalap(config)# hostname br1310ap(config)# ip domain name company.comap(config)# ip name-server 10.91.107.18ap(config)# ip http secure-serverap(config)# endIn this example, the access point system name is br1310, the domain name is company.com, and the IP address of the DNS server is 10.91.107.18.
For complete descriptions of the commands used in this example, consult the Cisco IOS Commands Master List, Release 12.3. Click this link to browse to the master list of commands:
http://www.cisco.com/en/US/products/sw/iosswrel/ps5187/products_product_indices_list.html
Deleting an HTTPS Certificate
The access point generates a certificate automatically when you enable HTTPS. However, if you need to change the access point's fully qualified domain name (FQDN) or you need to add an FQDN after enabling HTTPS, you might need to delete the certificate. Follow these steps:
Step 1
Browse to the Services: HTTP Web Server page.
Step 2
Uncheck the Enable Secure (HTTPS) Browsing check box to disable HTTPS.
Step 3
Click Delete Certificate to delete the certificate.
Step 4
Re-enable HTTPS. The access point generates a new certificate using the new FQDN.
Using Online Help
Click the help icon at the top of any page in the web-browser interface to display online help. Figure 3-13 shows the print and help icons.
Figure 3-13 Print and Help Icons
When a help page appears in a new browser window, use the Select a topic drop-down menu to display the help index or instructions for common configuration tasks, such as configuring VLANs.
Changing the Location of Help Files
Cisco maintains up-to-date HTML help files for access points and bridges on the Cisco web site. By default, the access point/bridge opens a help file on Cisco.com when you click the help button on the access point web-browser interface. However, you can install the help files on your network so your devices can access them there. Follow these steps to install the help files locally:
Step 1
Download the help files from the Software Center on Cisco.com. Click this link to browse to the Software Center's Wireless Software page:
http://www.cisco.com/cisco/software/navigator.html
Select the help files that match the software version on your access point.
Step 2
Unzip the help files on your network in a directory accessible to your access point/bridge. When you unzip the help files, the HTML help pages are stored in a folder named according to the help version number and access point model number.
Step 3
Browse to the Services: HTTP Web Server page in the access point web-browser interface. Figure 3-14 shows the HTTP Web Server page:
Figure 3-14 HTTP Web Server Page
Step 4
In the Default Help Root URL entry field, enter the complete path to the location where you unzipped the help files. When you click the access point help button, the access point automatically appends the help version number and model number to the path that you enter.
Note
Do not add the help version number and device model number to the Default Help Root URL entry. The access point automatically adds the help version and model number to the help root URL.
If you unzip the help files on your network file server at //myserver/myhelp, your Default Help Root URL looks like this:
http://myserver/myhelp
Table 3-2 shows an example help location and Help Root URL for an 1100 series access point.
Step 5
Click Apply.
Disabling the Web-Browser Interface
To prevent all use of the web-browser interface, select the Disable Web-Based Management check box on the Services: HTTP-Web Server page and click Apply. Figure 3-15 shows the Services: HTTP-Web Server page.
Figure 3-15 Services: HTTP-Web Server Page
To re-enable the web-browser interface, enter this global configuration command on the access point CLI:
ap(config)# ip http server

 Feedback
Feedback