Table Of Contents
Managing and Auditing Service Requests
Verifying QoS Service Requests
Changing Service Request Parameters
Viewing QoS Service Request Details
Managing and Auditing Service Requests
Each time a QoS service request is deployed in the Cisco IP Solution Center (ISC), a configuration audit occurs. You can view the results of these in QoS configuration audit reports. Use configuration audits and reports to verify that the ISC generated configlet represents the correct QoS configuration to download to the network device.
This chapter describes how to generate and view a configuration audit, how to manage QoS service requests, and how to access task logs.
The chapter includes the following sections:
QoS Configuration Auditing
A configuration audit occurs automatically each time you deploy a QoS service request. During this configuration audit, ISC verifies that all Cisco IOS commands are present and that they have the correct syntax. An audit also verifies that there were no errors during deployment.
The configuration audit verifies the service request deployment by examining the commands configured by the QoS service request on the target devices. If the device configuration does not match what is defined in the service request, the audit flags a warning and sets the service request to a Failed Audit or Lost state.
You can create audit reports for new or existing QoS service requests.
•
Audit new services—This type of audit is for service requests that have just been deployed. This type of audit identifies problems with the configuration files downloaded to the devices.
•
Audit existing services—This type of audit checks and evaluates the configuration of deployed service requests to see if the service request is still in effect.
We recommend that you schedule a service request audit on a regular basis to verify the state of the network provisioning requests.
This section describes how to manually generate a configuration audit and view the audit report.
To manually generate a configuration audit:
Step 1
Select Service Inventory > Inventory and Connection Manager > Service Requests.
Step 2
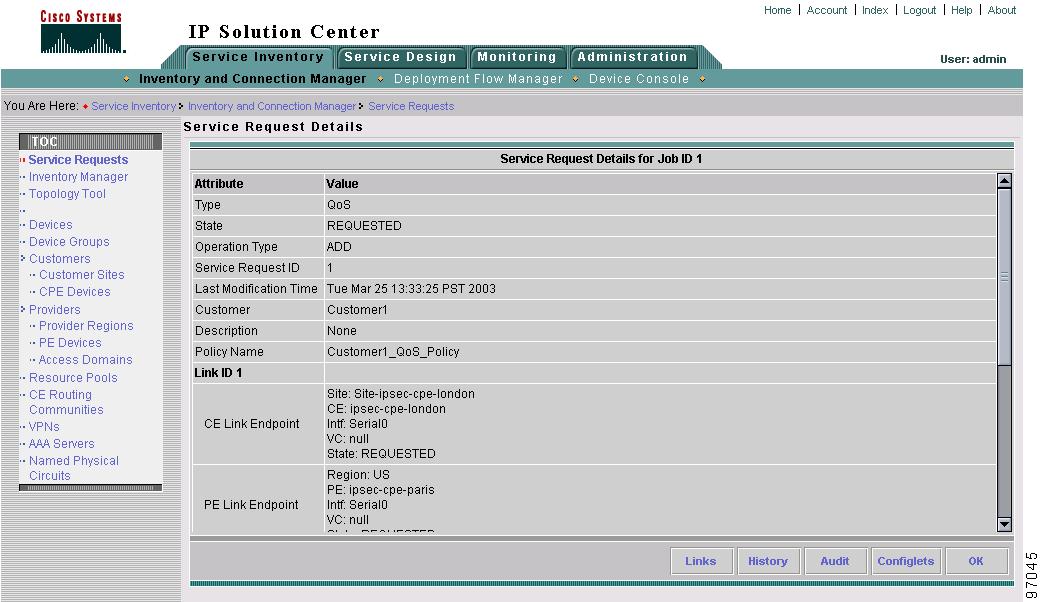
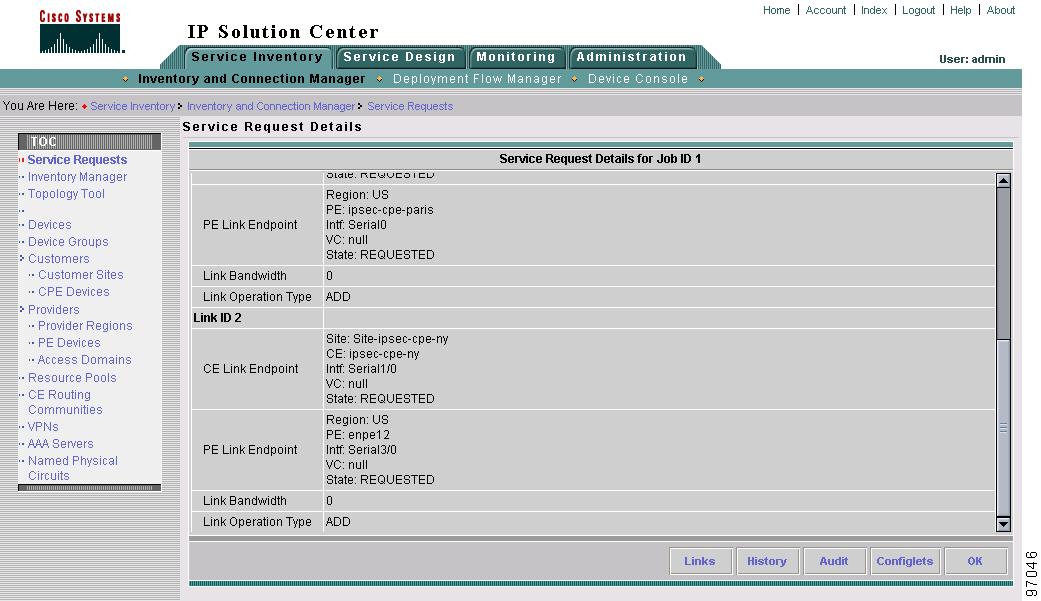
Select a QoS service request for the configuration audit and click Details. The Service Request Details window appears as shown in Figure 8-1.
Figure 8-1 Service Request Details
Step 3
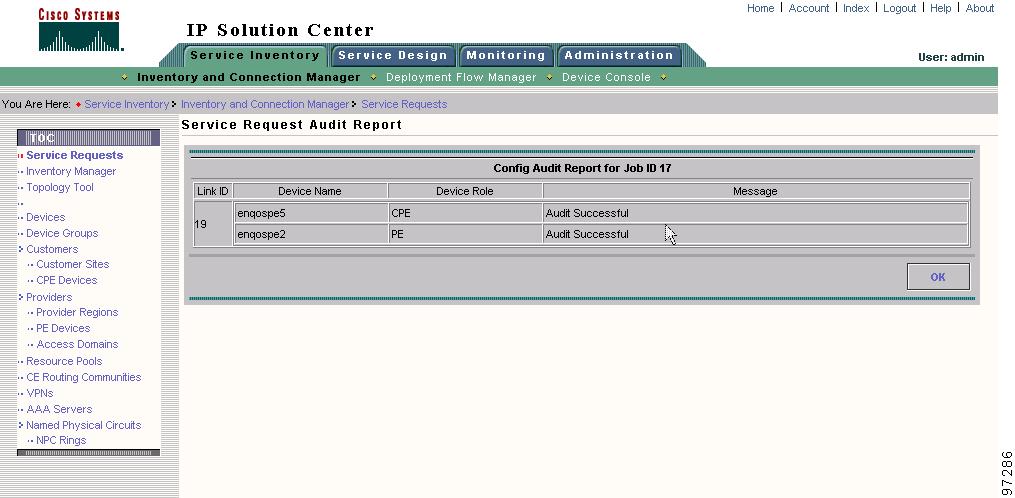
Click Audit. The Service Request Audit Report window appears. Figure 8-2 shows an example of a successful configuration audit.
Figure 8-2 Service Request Audit Report—Successful
This window shows the device name and role, and a message regarding the status of your configuration audit.
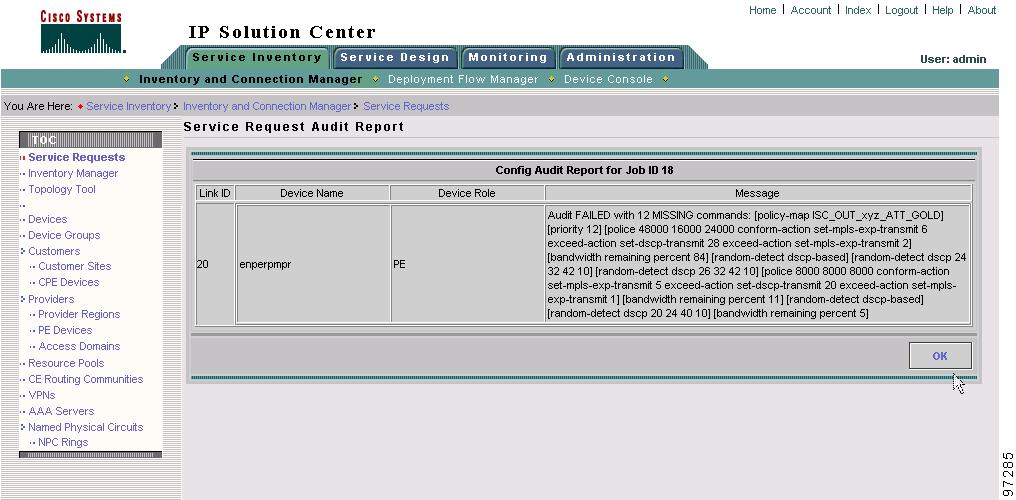
If the audit is unsuccessful, the message field shows details on the failed audit. Figure 8-3 shows an example of a failed audit message for a QoS service request.
Figure 8-3 Service Request Audit Report—Failed
The audit failure message indicates missing commands and configuration issues. Carefully review the information in the message field. If the audit fails, you must correct all errors and redeploy the service request.
Step 4
Click OK to return to the Service Request Details window.
QoS Service Requests
A QoS service request contains one or more QoS links. Each link can optionally be associated with a QoS link setting. A QoS policy can be associated with a QoS service request.
A QoS service request should:
•
Contain a QoS policy
•
Contain one or more QoS links
•
All links in the service request can be associated with a QoS link setting
To apply QoS policies to network devices, you must deploy the QoS service request. When you deploy a QoS service request, ISC compares the device information in the Repository (the ISC database) with the current device configuration and generates a configlet.
Use a QoS service request to apply a QoS policy to a network or to an existing L2VPN, MPLS, or VPLS service request.
The following sections describe:
Verifying QoS Service Requests
Changing Service Request Parameters
Note
See Creating the QoS Service Request and Deploying the QoS Service Request for more information on the create and deploy operations.
Managing QoS Service Requests
To manage QoS service request, select Service Inventory > Inventory and Connection Manager > Service Requests.
From the Service Requests window you can perform the following operations for QoS service requests:
•
Create
•
View Details
•
Edit
•
Deploy
•
Decommission
•
Purge
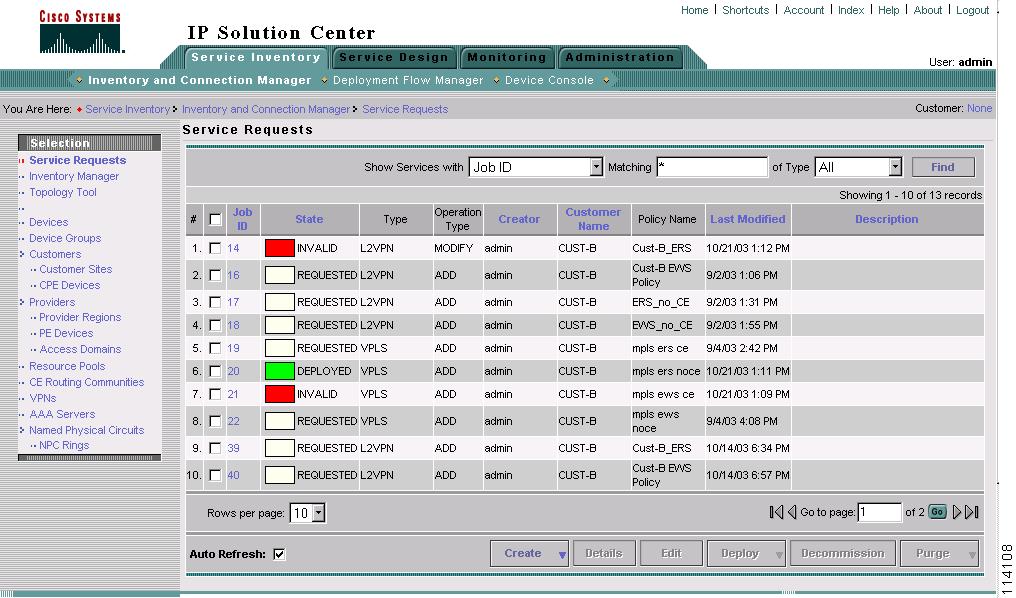
Figure 8-4 shows an example of the Service Requests window.
Figure 8-4 Service Requests List
The Service Requests window shows the current list of service requests for this user name. The list includes the following information about each service request:
•
JobID—The job number assigned to the service request by ISC. Table 8-1 describes ISC service request states.
•
State—The transition state for the service request. See Service Request States for more information.
•
Type—The type of service request. For example, QoS, MPLS, IPsec, L2VPN, NAT, or Firewall. - IPsec, NAT, and Firewall are not supported in this release. -
•
Operation Type—The operation type for the service request. For example, ADD means that you are adding this service request, and DELETE means that you are decommissioning this service request.
•
Creator—Username identity of person who created or last modified the service request.
•
Customer Name—Customer name for the service request.
•
Policy Name—Name of policy assigned to this service request.
•
Last Modified—Date and time the service request was created or last modified.
•
Description—Optional text description of the service request.
Verifying QoS Service Requests
After you deploy a QoS service request, you should verify that there were no errors.
You can verify a QoS service request through the following:
•
Transition state—The transition state of a QoS service request is listed on the Service Requests window in the State column. See Service Request States for more information.
•
View service request details—From the Service Requests Details window, you can view the QoS link endpoints and the QoS configlets for this service request. See Changing Service Request Parameters for more information.
•
Task Logs—Access the task logs from the Monitoring tab to help you troubleshoot a failed service request or to view more details about a service request. See QoS Task Logs for more information.
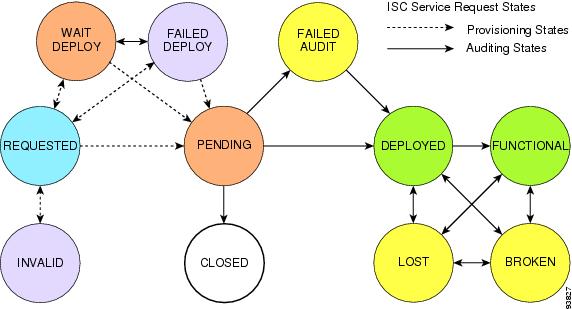
Service Request States
A service request transition state describes the different stages a service request enters during the QoS provisioning process.
For example, when you deploy a QoS service request, ISC compares the device information in the Repository (the ISC database) with the current device configuration and generates a QoS configlet for each device. When the configlets are generated and downloaded to the devices, the QoS service request enters the Pending state. When the devices are audited, the QoS service request enters the Deployed state.
Table 8-1 describes the transition states for an ISC service request.
Figure 8-5 illustrates which service request states relate to the QoS configuration auditing process, and which states relate to the provisioning process.
Figure 8-5 Service Requests States
Changing Service Request Parameters
You can change the QoS parameters associated with a deployed service request without decommissioning the service. For example, you might want to change a configuration to increase the bandwidth on the UNI interface.
To change the parameters, use the following procedure:
Step 1
Create a new QoS policy that represents the new level of service.
Step 2
Select the existing QoS service and edit that service request.
Step 3
Select the new policy (created in Step 1) and save the service request.
The QoS service request goes from deployed state to requested state with the new QoS policy displayed.
Step 4
Deploy the QoS service request.
The provisioning engine first removes the replaced policy parameters and immediately replaces them with the new policy parameters (see the following configlet).
interface Vlan201no service-policy input isc_in_Customer_A_Default_GE2/1.201no shutdown!no policy-map isc_in_Customer_A_Default_GE2/1.201!no class-map match-all Customer_ADefault_EFFORTGE2/1.201vlan201!no class-map match-all Customer_ADefaultRITICALGE2/1.201vlan201!no class-map match-all Customer_ADefaultAVVIDGE2/1.201vlan201!no class-map match-all Customer_ADefaultCONTROLGE2/1.201vlan201!class-map match-all Customer_Adefault2AVVIDGE2/1.201vlan201match ip precedence 5!class-map match-all Customer_Adefault2ONTROLGE2/1.201vlan201match ip precedence 3!class-map match-all Customer_Adefault2ITICALGE2/1.201vlan201match ip precedence 2!class-map match-all Customer_Adefault2EFFORTGE2/1.201vlan201match ip precedence 0 1 2 3 4 5 6 7!policy-map isc_in_Customer_A_default2_GE2/1.201class Customer_Adefault2AVVIDGE2/1.201vlan201set ip precedence 5police 40000 bps 40000 byte conform-action transmit exceed-action dropclass Customer_Adefault2ONTROLGE2/1.201vlan201set ip precedence 3police 40001 bps 40001 byte conform-action transmit exceed-action dropclass Customer_Adefault2ITICALGE2/1.201vlan201set ip precedence 2police 40002 bps 40002 byte conform-action transmit exceed-action dropclass Customer_Adefault2EFFORTGE2/1.201vlan201set ip precedence 0police 40003 bps 40003 byte conform-action transmit exceed-action drop!interface Vlan201service-policy input isc_in_Customer_A_default2_GE2/1.201!
Note
The policy parameters that were not changed (congestion management parameters in this case (tx-queue statements) are not removed, as shown in the following configlet.
interface GigabitEthernet2/1tx-queue 3bandwidth 16000 bpspriority hightx-queue 4bandwidth 16001 bpstx-queue 2bandwidth 16002 bpstx-queue 1bandwidth 16003 bps!interface Vlan201no shutdown!Viewing QoS Service Request Details
The QoS service request details include the link endpoints for the QoS service request, the history, and the QoS configlet generated during the service request deployment operation. Use the service request details to help you troubleshoot a problem or error with the service request or to check the QoS commands in the configlet.
This section describes how to view the details of a QoS service request, including the history, link details, and QoS configlets.
To view QoS service request details:
Step 1
Select Service Inventory > Inventory and Connection Manager > Service Requests.
Step 2
Select the QoS service request and click Details. The Service Request Details window appears as shown in Figure 8-6. See Figure 8-6 for Attribute details and Figure 8-7 for Link ID details.
Figure 8-6 QoS Service Request Details—Attributes
The service request attribute details include the type, transition state, operation type, ID, modification history, customer, and policy name.
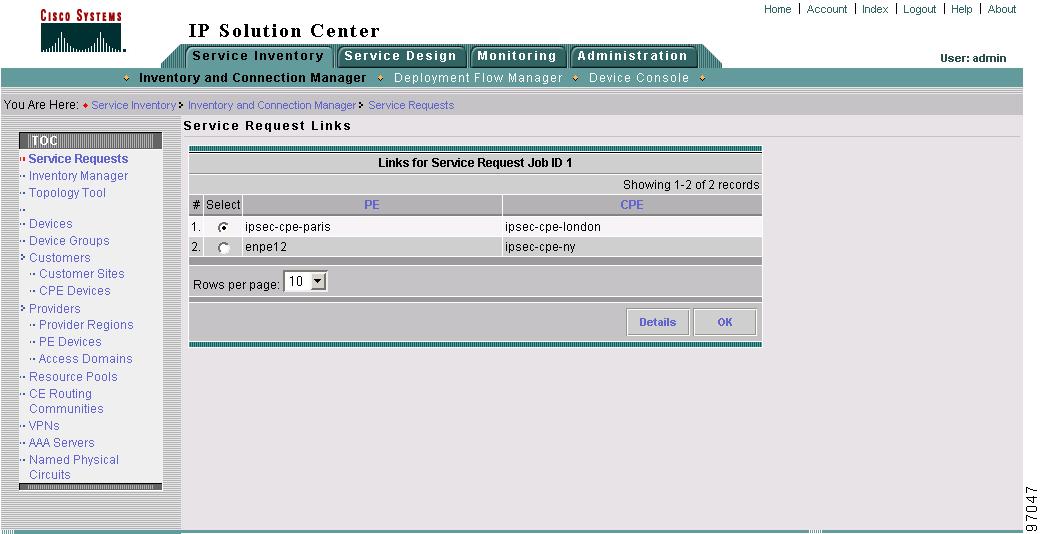
Figure 8-7 QoS Service Request Details—Link ID
The service request link ID details include the link endpoints, link bandwidth and link operation type.
From the Service Request Details page, you can view more information about:
•
Links—The link endpoint details.
•
History—Service request history report
•
Audit—Audit reports for the link IDs
•
Configlets—View the ISC generated configlet for the QoS service request
The following sections describe the links, history, and configlet details for a QoS service request. The audit details are described in QoS Configuration Auditing.
Links
Figure 8-8 shows the Service Request Links window.
Figure 8-8 QoS Service Request Links
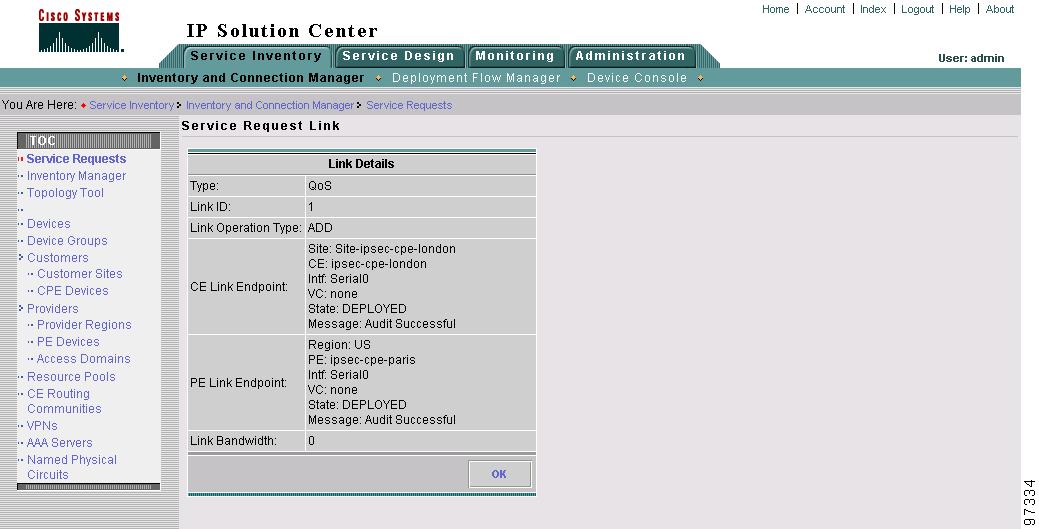
Click Details to display the devices marked with link QoS settings for this service request (Figure 8-9).
Figure 8-9 Service Request Link Details
Click OK (twice) to return to the Service Request Details page.
History
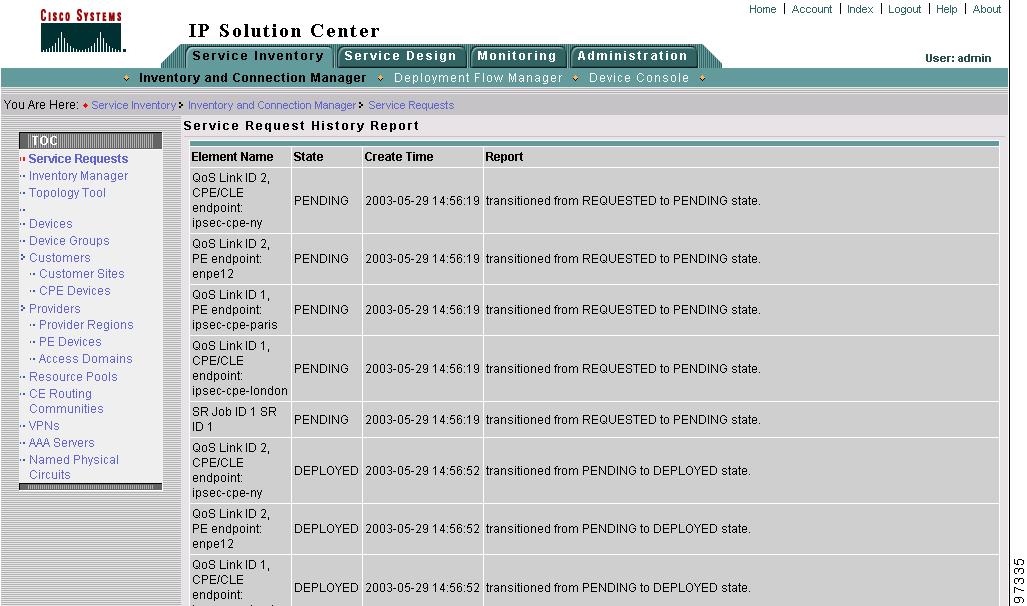
Figure 8-10 shows the Service Request History Report window.
Figure 8-10 Service Request History Report
The history report shows the following information about the service request:
•
Element name—The device, interface, and subinterfaces participating in this service request.
•
State—The transition states the element has gone through.
•
Create Time—The time the element was created for this service request.
•
Report—The action taken by ISC for the element in this service request.
Configlets
To view QoS configlets:
Step 1
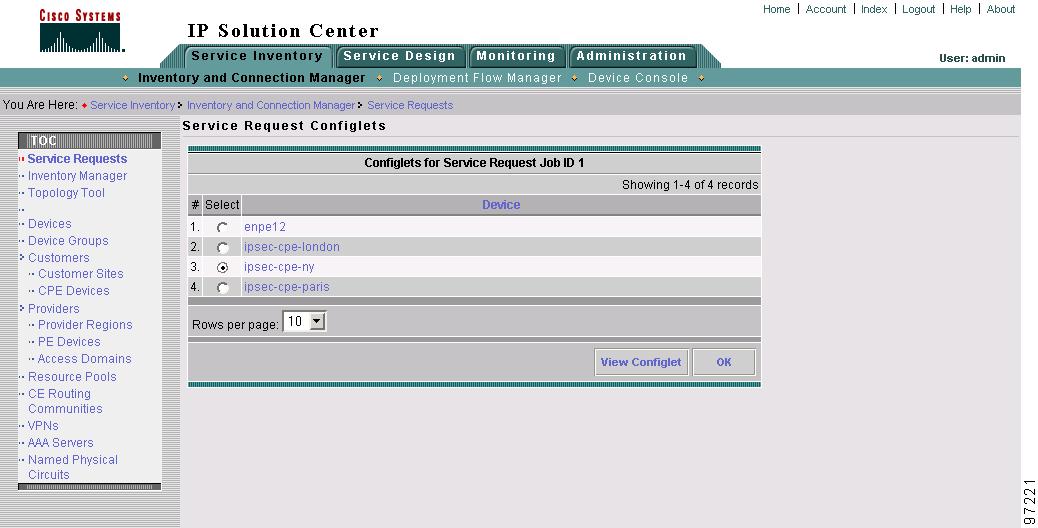
Click Configlets on the Service Request Details window. The Service Request Configlets window appears (Figure 8-11).
Figure 8-11 Service Request Configlets
This window shows all devices whose configuration is affected by the service request.
Step 2
Select the device to view the configlet.
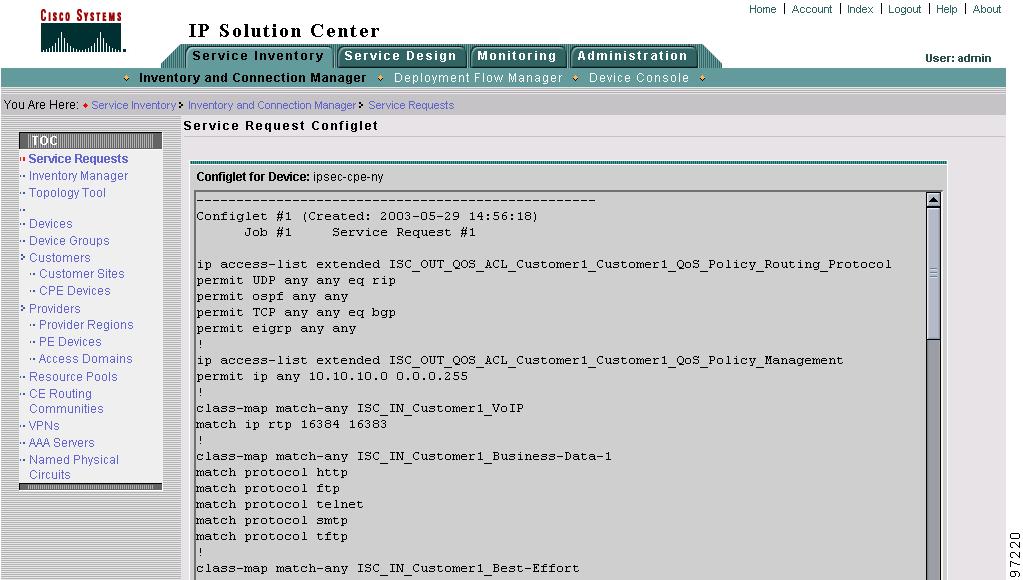
Step 3
Click View Configlet. The Configlet for Device window appears (Figure 8-12).
Figure 8-12 QoS Configlet Example
The device configlet shows all commands downloaded to the device configuration during the service request deployment operation.
Note
For Ethernet QoS, class-maps corresponding to the Traffic Classifications All IP Traffic and All Mac Traffic are generated only once for a device and not each time a service request is deployed to that device. As a result, these class-maps will not be removed from the device when you decommission a service request.
Step 4
Click OK to exit.
QoS Task Logs
Use the task logs to help you troubleshoot why a service request has failed or to find more details about a service request. This section describes how to view the task logs generated for configuration messages.
To access the task logs:
Step 1
From the Monitoring tab, click Task Manager.
Step 2
Click Logs under the TOC heading.
Step 3
Select the task to view the logs for and click Instances.
Step 4
Select the log to view and click Log. The Task Log window appears.
Step 5
Select the log level from the drop-down menu and click Filter. The log levels are All, Severe, Warning, Info, Config, Fine, Finer, Finest.
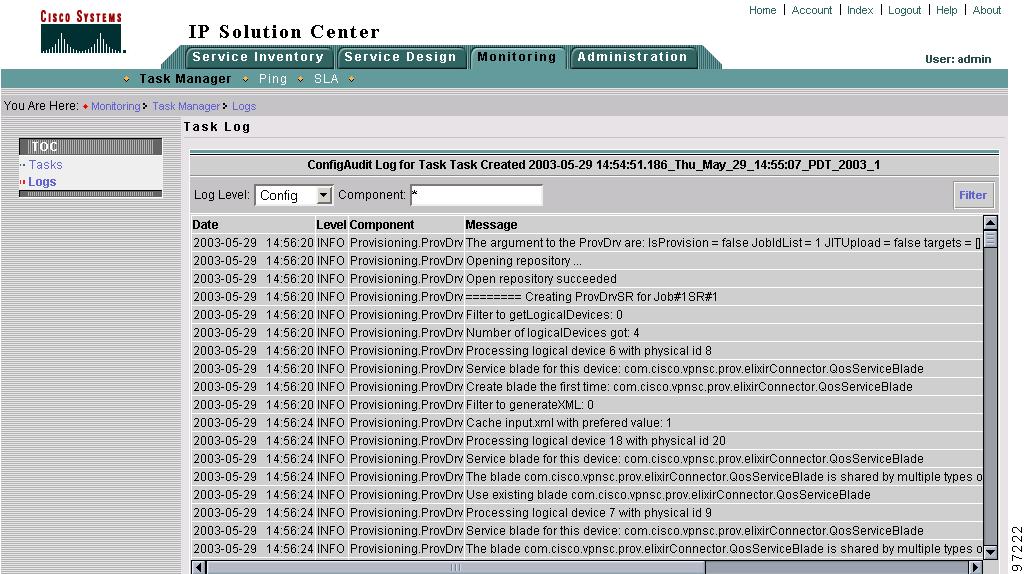
Figure 8-13 shows an example of the information contained in an ISC task log.
Figure 8-13 Task Log Example
Step 6
For example, this window shows all log entries related to the device configuration.
Step 7
To exit from task logs, you must click Task Manager above the TOC for this window.

 Feedback
Feedback