-
Operations and Maintenance Release 4.5
-
Preface
-
Chapter 1 - Cisco BTS 10200 Softswitch Startup and Shutdown Procedures
-
Chapter 2 - Managing Access and Users
-
Chapter 3 - Operations
-
Chapter 4 - Maintaining the BTS 10200 Softswitch
-
Chapter 5 - Maintenance and Diagnostics for External Resources
-
Chapter 6 -- Traffic Measurements
-
Chapter 7 - SNMP Interface
-
Chapter 8 - Congestion Detection and Protection
-
Appendix A - Feature Tones
-
Table Of Contents
Logging into the EMS Using CLI
Managing Access and Users
Revised: July 21, 2009, OL-4495-10Introduction
This chapter describes the operator interfaces used for communication with the Cisco BTS 10200 Softswitch, and the procedures for managing access and users.
Note
After entering any of the commands in this chapter, press the Return or Enter key.
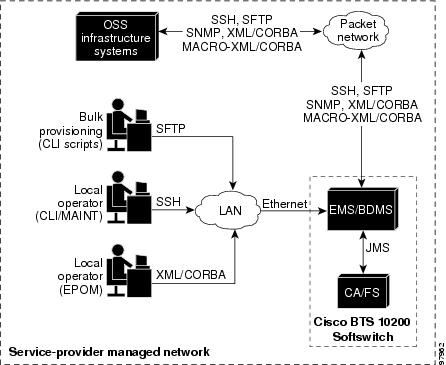
illustrates the Cisco BTS 10200 Softswitch operator interfaces of the Element Management System (EMS). These interfaces support several types of communications:
•
Local Operations Console—the following options are available:
–
Interactive CLI session—operator connects to the EMS using Secure Shell (SSH) and uses the command line interface (CLI) in an interactive session
–
Bulk Provisioning—operator connects to the EMS using FTP for batch-mode provisioning (requires highest privilege levels)
SFTP is used as of Release 4.1. The /opt/ems/ftp/deposit directory checks for files every 7 seconds and then deletes them. A report is generated and can be viewed at https://<ems ip> (see the HTML file listed in the reports index). You can move the files to a deposit directory. The file must be owned by a valid Cisco BTS 10200 user (such as optiuser or btsadmin). If you are logged in as root, you must use the command unix -p when putting the file in the deposit directory.
Note
See the Cisco BTS 10200 Softswitch Provisioning Guide for Bulk Provisioning information.
•
Network Management System—provides events, alarms, thresholds and traffic monitoring management commands into the EMS using SNMP
•
CORBA Client—provides events, alarms, thresholds and traffic monitoring management commands into the EMS via Common Object Request Broker Architecture (CORBA)
The EMS database holds up to 100 operator logins, and up to 50 user sessions can be active at any time.
The EMS interfaces internally with the Call Agent (CA) and Feature Server (FS) using the Java Message Service (JMS) protocol over IP Protocol.
Figure 2-1 Operator Interfaces (Billing interfaces also shown)
System Administrator Access
When logging in for the first time, log in as btsadmin (the default password is btsadmin). You must change the password when you take possession of the system.
Logging into the EMS Using CLI
SSH is a way to access the BTS CLI or maintenance (MAINT) modes. SSH provides encrypted communication between a remote machine and the EMS/CA for executing CLI or MAINT commands. The SSH server runs on EMSs and CAs. To connect the client and server sides run the secure shell daemon (SSHD). With SSH, new users must enter a new password and reenter that password during the first login. In future logins they are prompted once for a password only.
When logging in for the first time, system administrators log in as btsadmin (the default password is btsadmin). Change the password.
Step 1
To log in from the client side for the first time: ssh btsadmin@<ipaddress>.
Note
If you are logged in to the system as root, enter: btsadmin@0
On the first SSH login from the client side, expect a message like this:
The authenticity of host [hostname] can't be established. Key fingerprint is 1024 5f:a0:0b:65:d3:82:df:ab:42:62:6d:98:9c:fe:e9:52. Are you sure you want to continue connecting (yes/no)?Step 2
Enter yes.
The password prompt appears, now all communications are encrypted.
Step 3
Enter your password.
The system responds with a CLI> prompt. You can now send commands to the EMS.
Step 4
Enter provisioning commands.
Step 5
To log off, enter exit .
Managing Users
You must have a user privilege level of 9 or higher to add, show, change, or delete a user.
CautionDo not add, change, or delete username root, this prevents proper EMS access.
Managing Commands
Each command (verb-noun combination) has a security class of 1-10; 1 is lowest, 10 is highest. Each time a user enters a command, the system compares the user's privilege level to the command's security class. EMS denies the command if the user level is less than the command level.
The Command Level (command-level) table shows the 10 command security classes. BTS has the following presets:
•
1 (lowest level)
•
5 (mid-level)
•
10 (highest level)—These commands require a system administrator with a security level of 10 to execute.

 Feedback
Feedback