Table Of Contents
Viewing SBC Properties
User Roles Required to View SBC Properties
Viewing SBC Properties in Logical Inventory
Viewing SBC DBE Properties
Viewing Media Address Properties
Viewing VDBE H.248 Properties
Viewing SBC SBE Properties
Viewing AAA Properties
Viewing H.248 Properties
Viewing Policy Properties
Viewing SIP Properties
Viewing SBC Properties
This topic identifies and describes the properties for Session Border Controllers (SBCs) that appear in Cisco Prime Network Vision (Prime Network Vision)logical inventory.
An SBC can provide the following types of services:
• Protocol and media interworking
Protocol and media interworking
• Session routing
Session routing
• Hosted Network Address Translation (NAT) and firewall traversal
Hosted Network Address Translation (NAT) and firewall traversal
• Security and AAA
Security and AAA
• Intra- and inter-VPN interconnections and optimization
Intra- and inter-VPN interconnections and optimization
• Media transcoding with an external media server
Media transcoding with an external media server
SBC services are divided into the following components:
• Data Border Element (DBE)—Responsible for media-related functions.
Data Border Element (DBE)—Responsible for media-related functions.
• Signaling Border Element (SBE)—Responsible for call signaling-related functions.
Signaling Border Element (SBE)—Responsible for call signaling-related functions.
Note  The existing Cisco SBC platforms support only DBE.
The existing Cisco SBC platforms support only DBE.
An SBC itself consists of the combined DBE and SBE functionality.
In addition, the SBC can operate in the following deployment models:
• Distributed Model (DM)—Contains only the SBE or DBE, resulting in a distributed SBC.
Distributed Model (DM)—Contains only the SBE or DBE, resulting in a distributed SBC.
• Unified Model (UM)—Contains both the SBE and DBE, thereby implementing the SBE and DBE as a single device.
Unified Model (UM)—Contains both the SBE and DBE, thereby implementing the SBE and DBE as a single device.
The following topics describe the SBC properties that are displayed in Prime Network Vision logical inventory:
• User Roles Required to View SBC Properties
User Roles Required to View SBC Properties
• Viewing SBC Properties in Logical Inventory
Viewing SBC Properties in Logical Inventory
• Viewing SBC DBE Properties
Viewing SBC DBE Properties
• Viewing SBC SBE Properties
Viewing SBC SBE Properties
User Roles Required to View SBC Properties
This topic identifies the GUI default permission or scope security level that is required to view SBC properties in Prime Network Vision. Prime Network determines whether you are authorized to perform a task as follows:
• For GUI-based tasks (tasks that do not affect elements), authorization is based on the default permission that is assigned to your user account.
For GUI-based tasks (tasks that do not affect elements), authorization is based on the default permission that is assigned to your user account.
• For element-based tasks (tasks that do affect elements), authorization is based on the default permission that is assigned to your account. That is, whether the element is in one of your assigned scopes and whether you meet the minimum security level for that scope.
For element-based tasks (tasks that do affect elements), authorization is based on the default permission that is assigned to your account. That is, whether the element is in one of your assigned scopes and whether you meet the minimum security level for that scope.
For more information on user authorization, see the Cisco Prime Network 3.8 Administrator Guide.
The following tables identify the tasks that you can perform:
• Table 19-1 identifies the tasks that you can perform if a selected element is not in one of your assigned scopes.
Table 19-1 identifies the tasks that you can perform if a selected element is not in one of your assigned scopes.
• Table 19-2 identifies the tasks that you can perform if a selected element is in one of your assigned scopes.
Table 19-2 identifies the tasks that you can perform if a selected element is in one of your assigned scopes.
By default, users with the Administrator role have access to all managed elements. To change the Administrator user scope, see the topic on device scopes in the Cisco Prime Network 3.8 Administrator Guide.
Table 19-1 Default Permission/Security Level Required for Viewing SBC Properties - Element Not in User's Scope
Task
|
Viewer
|
Operator
|
OperatorPlus
|
Configurator
|
Administrator
|
Viewing SBC properties
|
—
|
—
|
—
|
—
|
X
|
Table 19-2 Default Permission/Security Level Required for Viewing SBC Properties - Element in User's Scope
Task
|
Viewer
|
Operator
|
OperatorPlus
|
Configurator
|
Administrator
|
Viewing SBC properties
|
X
|
X
|
X
|
X
|
X
|
Related Topics
• Viewing SBC Properties in Logical Inventory
Viewing SBC Properties in Logical Inventory
• Viewing SBC DBE Properties
Viewing SBC DBE Properties
• Viewing SBC SBE Properties
Viewing SBC SBE Properties
Viewing SBC Properties in Logical Inventory
To view SBC properties in Prime Network Vision logical inventory, right-click the element configured for SBC, then choose Inventory > Logical Inventory > Session Border Controller.
The SBC properties are displayed as shown in Figure 19-1.
Figure 19-1 SBC Properties in Logical Inventory
Table 19-3 describes the general SBC properties displayed in logical inventory.
Table 19-3 SBC Properties
Field
|
Description
|
Process
|
Process name, such as Session Border Controller.
|
Process Status
|
Status of the process, such as Running.
|
Application Version
|
SBC version number.
|
Mode
|
Mode in which the SBC is operating:
• Unified Unified
• Distributed DBE Distributed DBE
|
SBC Service Name
|
Name of the service.
|
Related Topics
• Viewing SBC DBE Properties
Viewing SBC DBE Properties
• Viewing SBC SBE Properties
Viewing SBC SBE Properties
• Viewing AAA Properties
Viewing AAA Properties
• Viewing H.248 Properties
Viewing H.248 Properties
• Viewing Policy Properties
Viewing Policy Properties
• Viewing SIP Properties
Viewing SIP Properties
Viewing SBC DBE Properties
The DBE controls media packet access to the network, provides differentiated services and QoS for different media streams, and prevents service theft.
To view SBC DBE properties, choose Logical Inventory > Session Border Controller > DBE.
Table 19-4 describes the DBE properties that appear in logical inventory.
Table 19-4 SBC DBE Properties
Field
|
Description
|
Process
|
Process name, such as DBE.
|
Process Status
|
Status of the process, such as Running.
|
Name
|
Name assigned to the DBE.
|
Type
|
Type of DBE, either DBE or virtual DBE (vDBE).
|
DBE Location Id
|
Unique identifier configured on each vDBE within a UM DBE.
|
Related Topics
• Viewing Media Address Properties
Viewing Media Address Properties
• Viewing VDBE H.248 Properties
Viewing VDBE H.248 Properties
Viewing Media Address Properties
A DBE uses a pool of sequential IPv4 media addresses as local media addresses.
To view SBC media address properties, choose Logical Inventory > Session Border Controller > DBE > Media Address.
Table 19-5 describes the SBC media address properties that are displayed in logical inventory.
Table 19-5 Media Address Properties
Field
|
Description
|
Address Range
|
IP addresses defined for the pool.
|
Port Range Lower
|
Lower end of the port range for the interface. If no range is specified, all possible Voice over IP (VoIP) port numbers are valid.
|
Port Range Upper
|
Upper end of the port range for the interface.
|
VRF Name
|
VRF that the interface is assigned to.
|
Service Class
|
Class of service (CoS) for each port range, such as fax, signaling, voice, or any.
|
Related Topics
• Viewing VDBE H.248 Properties
Viewing VDBE H.248 Properties
• Viewing SBC Properties in Logical Inventory
Viewing SBC Properties in Logical Inventory
• Viewing SBC SBE Properties
Viewing SBC SBE Properties
Viewing VDBE H.248 Properties
To view VDBE H.248 properties, choose Logical Inventory > Session Border Controller > DBE > VDBE.
Table 19-6 describes the VDBE H.248 properties that are displayed in logical inventory.
Table 19-6 VDBE H.248 Properties
Branch
|
Description
|
H248 Controller
|
H.248 controller used by the DBE.
The Media Gateway Configuration (MGC) table displays the following information:
• Index—The number of the H.248 controller. The profile is used to interoperate with the SBE. Index—The number of the H.248 controller. The profile is used to interoperate with the SBE.
• Remote IP—The remote IP address for the H.248 controller. Remote IP—The remote IP address for the H.248 controller.
• Remote Port—The remote port for the H.248 controller. Remote Port—The remote port for the H.248 controller.
• Transport—The transport for communications with the remote device. Transport—The transport for communications with the remote device.
|
H248 Interface
|
The SBC H248 Control Interface table displays the following information:
• IP Address: IP Address:
– In DM mode, the local IP address of the DBE used to connect to the SBE. In DM mode, the local IP address of the DBE used to connect to the SBE.
– In UM mode, the local IP address used to connect to the media gateway. In UM mode, the local IP address used to connect to the media gateway.
• Port—The port for the H.248 controller interface. Port—The port for the H.248 controller interface.
• Transport—The transport the H.248 controller interface uses. Transport—The transport the H.248 controller interface uses.
• Association—The relationship between the SBE and the media gateway. Association—The relationship between the SBE and the media gateway.
|
Related Topics
• Viewing SBC SBE Properties
Viewing SBC SBE Properties
• Viewing SBC Properties in Logical Inventory
Viewing SBC Properties in Logical Inventory
• Viewing SBC DBE Properties
Viewing SBC DBE Properties
Viewing SBC SBE Properties
The SBE controls the access of VoIP signaling messages to the network core and manipulates the contents of these messages. It does this by acting as a SIP B2BUA or H.323 gateway.
To view SBC SBE properties, choose Logical Inventory > Session Border Controller > SBE.
Table 19-7 describes the information displayed in logical inventory for an SBE.
Table 19-7 SBC SBE Properties
Field
|
Description
|
Process
|
Name of the process, such as SBE.
|
Process Status
|
Status of the process, such as Running or Idle.
|
Name
|
Name assigned to this SBE.
|
Call Redirect Limit
|
Maximum number of times a call is redirected before the call is declared failed. The range is 0 to 100 with a default of 2.
|
On Hold Timeout
|
Amount of time, in milliseconds, that the SBE waits after receiving a media timeout notification from the DBE for an on-hold call before tearing down the call.
|
Related Topics
• Viewing AAA Properties
Viewing AAA Properties
• Viewing H.248 Properties
Viewing H.248 Properties
• Viewing Policy Properties
Viewing Policy Properties
• Viewing SIP Properties
Viewing SIP Properties
Viewing AAA Properties
For devices that support local and remote billing, the SBC can send billing records to a AAA server using the RADIUS protocol.
To view AAA properties, choose Logical Inventory > Session Border Controller > SBE > AAA.
Table 19-8 describes the AAA properties that appear in logical inventory for the SBC SBE.
Table 19-8 AAA Properties
Branch
|
Description
|
AAA Interface
|
The SBE AAA Interface table displays the following information:
• AAA Address—The local AAA interface address. AAA Address—The local AAA interface address.
• Network ID—A unique identifier for the SBE. Network ID—A unique identifier for the SBE.
|
Accounting
|
The Accounting Radius Client table displays the following information:
• Name—The name of the accounting client. Name—The name of the accounting client.
• Client Type—The type of client, either Accounting or Authentication. Client Type—The type of client, either Accounting or Authentication.
|
Authentication
|
The Authentication Radius Client table displays the following information:
• Name—The name of the authentication client. Name—The name of the authentication client.
• Client Type—The type of client, either Accounting or Authentication. Client Type—The type of client, either Accounting or Authentication.
|
Billing
|
The SBE Billing table displays the following information related to billing:
• LDR Check Time—The time of day (local time) to run the long duration record check. LDR Check Time—The time of day (local time) to run the long duration record check.
• Local Billing Address—The local IP address for SBE billing. This IP address can be different from the local AAA IP address and is the IP address written in the bill records. Local Billing Address—The local IP address for SBE billing. This IP address can be different from the local AAA IP address and is the IP address written in the bill records.
• Admin Status—The configuration status, available with the running-config command. Admin Status—The configuration status, available with the running-config command.
• Operational Status—The running status, available from the CLI. This entry indicates whether or not the billing interface is up. The status is derived from the interworking of the SBC and the AAA server. Operational Status—The running status, available from the CLI. This entry indicates whether or not the billing interface is up. The status is derived from the interworking of the SBC and the AAA server.
|
Related Topics
• Viewing H.248 Properties
Viewing H.248 Properties
• Viewing SBC Properties in Logical Inventory
Viewing SBC Properties in Logical Inventory
• Viewing SBC SBE Properties
Viewing SBC SBE Properties
Viewing H.248 Properties
The H.248 interface is used for signaling between an SBE and a DBE in distributed mode and between an SBE and a transcoding media gateway. The SBE or SBC acts as an H.248 MGC, and the transcoding device acts as an H.248 media gateway. The connection between the MGC and the media gateway is an H.248 link.
To view H.248 properties, choose Logical Inventory > Session Border Controller > H248.
Table 19-9 describes the H.248 properties that appear in logical inventory for the SBC SBE.
Table 19-9 H.248 Properties
Branch
|
Description
|
H248 Interface
|
The SBC H248 Control Interface table displays the following information:
• IP Address: IP Address:
– In DM mode, the IP address used to connect the DBE and the MGC. In DM mode, the IP address used to connect the DBE and the MGC.
– In UM mode, the IP address used to connect the SBC and the media gateway. In UM mode, the IP address used to connect the SBC and the media gateway.
• Port—The port for the H.248 controller interface. Port—The port for the H.248 controller interface.
• Transport—The transport the H.248 controller interface uses. Transport—The transport the H.248 controller interface uses.
• Association—The relationship between the SBE and the media gateway. Association—The relationship between the SBE and the media gateway.
|
Media Gateway
|
The Media Gateway table displays the following information:
• IP Address—The IP address of the media gateway. IP Address—The IP address of the media gateway.
• Codec List—A comma-separated list of the codecs supported. Codec List—A comma-separated list of the codecs supported.
|
Related Topics
• Viewing Policy Properties
Viewing Policy Properties
• Viewing SIP Properties
Viewing SIP Properties
• Viewing AAA Properties
Viewing AAA Properties
Viewing Policy Properties
An SBC policy is a set of rules that define how the SBC treats different kinds of VoIP events. An SBC policy allows control of the VoIP signaling and media that pass through the SBC at an application level.
A policy set is a group of policies that can be active on the SBC at any one time. If a policy set is active, the SBC uses the rules defined within it to apply policy to events. Multiple policies can be set on a single SBC.
To view policy properties, choose Logical Inventory > Session Border Controller > Policy.
Table 19-10 describes the policy properties that appear in logical inventory for the SBC SBE.
Table 19-10 Policy Properties
Branch
|
Description
|
Blacklist
|
The Blacklists table contains the following information:
• Name—The blacklist name. Name—The blacklist name.
• Type—The type of source that this blacklist applies to, such as critical or normal. Type—The type of source that this blacklist applies to, such as critical or normal.
|
CAC Policy
|
A Call Admission Control (CAC) policy is used to define admission control.
The SBE CAC Policy Set table contains the following information:
• Policy Set Number—An identifying number the SBE has assigned to the policy set. Policy Set Number—An identifying number the SBE has assigned to the policy set.
• First Table—A CAC policy table. First Table—A CAC policy table.
• Status—Whether the policy is active or inactive. If the policy is active, the SBC applies the defined rules to events. Status—Whether the policy is active or inactive. If the policy is active, the SBC applies the defined rules to events.
• First CAC Scope—The scale that the CAC applies for, such as source adjacency or destination adjacency. This is the first CAC table used for CAC policy match. First CAC Scope—The scale that the CAC applies for, such as source adjacency or destination adjacency. This is the first CAC table used for CAC policy match.
• Description—A brief description of the policy set. Description—A brief description of the policy set.
|
Call Policy
|
A call policy set is used for number analysis and routing.
The SBE Call Policy Set table contains the following information:
• Policy Set Number—An identifying number the SBE has assigned to the policy set. Policy Set Number—An identifying number the SBE has assigned to the policy set.
• Status—Whether the policy is active or inactive. If the policy is active, the SBC applies the defined rules to events. Status—Whether the policy is active or inactive. If the policy is active, the SBC applies the defined rules to events.
• First Call Table—The first call table used for call policy match. First Call Table—The first call table used for call policy match.
• Description—A brief description of the policy set. Description—A brief description of the policy set.
|
Codec List
|
The SBE Codec List table contains the following information:
• Name—The name of the codec list. Name—The name of the codec list.
• Codecs—The codecs contained in each list. Codecs—The codecs contained in each list.
|
Current Blacklisting
|
The Current Blacklistings table contains the following information:
• Type—The type of source this blacklist applies to. Blacklists are used to block certain VoIP services that meet specified conditions. Type—The type of source this blacklist applies to. Blacklists are used to block certain VoIP services that meet specified conditions.
• Event Type—The type of event this blacklist applies to, such as CORRUPT_MESSAGE. Event Type—The type of event this blacklist applies to, such as CORRUPT_MESSAGE.
• Is All Source Addresses—Whether the blacklist applies to all source IP addresses: Is All Source Addresses—Whether the blacklist applies to all source IP addresses:
– True—Ignore any IP address in the Source Address field. True—Ignore any IP address in the Source Address field.
– False—Use the IP address in the Source Address field. False—Use the IP address in the Source Address field.
• Source Address—The IP address that this blacklist applies to. Source Address—The IP address that this blacklist applies to.
• Source Port Number—The port number that this blacklist applies to. Source Port Number—The port number that this blacklist applies to.
• Source Port Type—The type of port this blacklist applies to. All is a valid entry. Source Port Type—The type of port this blacklist applies to. All is a valid entry.
• Time Remaining—The amount of time, in hours, minutes, or seconds, before the blacklist is removed. Time Remaining—The amount of time, in hours, minutes, or seconds, before the blacklist is removed.
|
Hunting Trigger
|
The hunting trigger enables the SBC to search for other routes or destination adjacencies if an existing route fails.
The Global Hunting Trigger List table contains the following information:
• Hunting Mode—Indicates the protocol to use to search for routes, such as Session Initiation Protocol (SIP). Hunting Mode—Indicates the protocol to use to search for routes, such as Session Initiation Protocol (SIP).
• Hunting Triggers—The SIP responses, such as 468 or 503, that indicate the SBC is to search for an alternate route or destination adjacency. SIP responses are defined in RFC3261. Hunting Triggers—The SIP responses, such as 468 or 503, that indicate the SBC is to search for an alternate route or destination adjacency. SIP responses are defined in RFC3261.
|
QoS Profile
|
QoS profiles can be used by CAC policies and are used exclusively for marking IP packets.
The QoS Profile table contains the following information:
• Name—The name of the QoS profile. Name—The name of the QoS profile.
• Class of Service—The type of call this profile applies to, such as voice, video, signaling, or fax. Class of Service—The type of call this profile applies to, such as voice, video, signaling, or fax.
• Marking Type—The type of marking to be applied to the IP packet. Options include Passthrough, Differentiated Service Code Point (DSCP), and IP Precedence/ToS. Marking Type—The type of marking to be applied to the IP packet. Options include Passthrough, Differentiated Service Code Point (DSCP), and IP Precedence/ToS.
• IP Precedence—If the marking type is IP Precedence, the specified precedence, either 0 or 1. IP Precedence—If the marking type is IP Precedence, the specified precedence, either 0 or 1.
• ToS—If the marking type is ToS, the ToS value. ToS—If the marking type is ToS, the ToS value.
• DSCP—If the marking type is DSCP, the DSCP value. DSCP—If the marking type is DSCP, the DSCP value.
|
SDP
|
The Session Description Protocol (SDP) content pane contains the following tabs, each with their respective table:
• SBE SDP Policy Table: SBE SDP Policy Table:
– Instance Name—The name of the policy table. Instance Name—The name of the policy table.
– SBE SDP Match Table—The name of the SDP match table. SBE SDP Match Table—The name of the SDP match table.
• SBE SDP Match Table: SBE SDP Match Table:
– Instance Name—The name of the SDP match table. Instance Name—The name of the SDP match table.
– Match Strings—The match criteria. Match Strings—The match criteria.
– Table Type—The type of table, either Blacklist or Whitelist. Table Type—The type of table, either Blacklist or Whitelist.
|
Related Topics
• Viewing SIP Properties
Viewing SIP Properties
• Viewing AAA Properties
Viewing AAA Properties
• Viewing H.248 Properties
Viewing H.248 Properties
Viewing SIP Properties
To view SIP properties, choose Logical Inventory > Session Border Controller > SIP.
Table 19-11 describes the SIP entries that appear in logical inventory for the SBC SBE.
Table 19-11 SIP Properties
Branch
|
Description
|
SIP Account
|
The SBE Account table contains the following information:
• Name—The name of the account associated with the adjacencies. Name—The name of the account associated with the adjacencies.
• Adjacencies—The identified adjacencies. Adjacencies—The identified adjacencies.
|
SIP Adjacency
|
An adjacency represents a signaling relationship with a remote call agent. One adjacency is defined per external call agent. Each adjacency belongs within an account. Each incoming call is matched to an adjacency, and each outgoing call is routed out over a second adjacency.
The SBC SIP Adjacencies table contains the following information:
• Name—The adjacency name. Name—The adjacency name.
• Status—The status of the adjacency, either Attached or Detached. Status—The status of the adjacency, either Attached or Detached.
• Signaling Address—The local IP address and port (optional) for communications. Signaling Address—The local IP address and port (optional) for communications.
• Signaling Peer—The remote IP address and port (optional) for communications. Signaling Peer—The remote IP address and port (optional) for communications.
• Description—A brief description of the adjacency. Description—A brief description of the adjacency.
|
SIP Adjacency Group
|
The Adjacencies Groups table contains the following information:
• Name—The name of the SIP adjacency group. Name—The name of the SIP adjacency group.
• Adjacencies—The adjacencies that belong to the group. Adjacencies—The adjacencies that belong to the group.
|
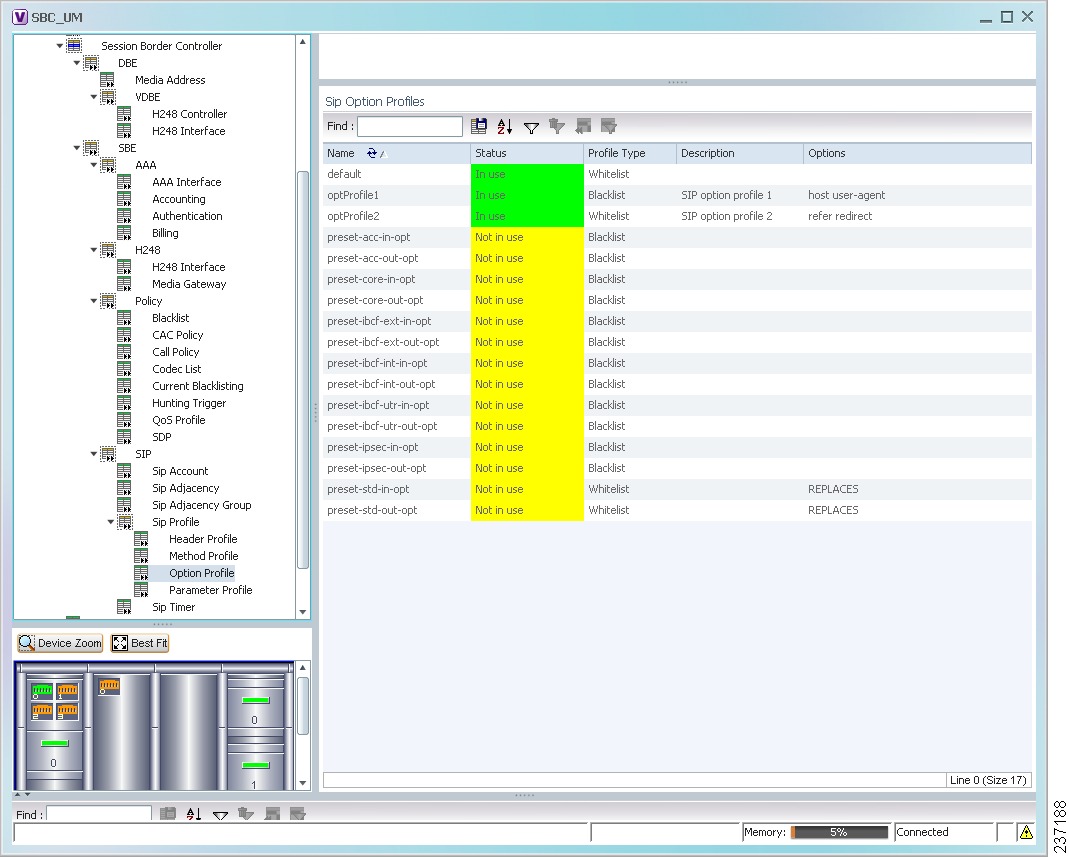
SIP Profile
|
The SBC can be configured with whitelist and blacklists profiles on SIP messages. The following types of SIP profiles are available:
• Header profile—A profile based on SIP header information. Header profile—A profile based on SIP header information.
• Method profile—A profile based on SIP method strings. Method profile—A profile based on SIP method strings.
• Option profile—A profile based on SIP option strings. Option profile—A profile based on SIP option strings.
• Parameter profile—A profile based on SIP parameters. Parameter profile—A profile based on SIP parameters.
|
SIP Profile >
Header Profile
|
The SIP Header Profiles table contains the following information:
• Name—The name of the SIP header profile. Name—The name of the SIP header profile.
• Status—Whether or not the profile is in use. Status—Whether or not the profile is in use.
• Profile Type—The type of profile: Profile Type—The type of profile:
– Whitelist—Accepts SIP requests that match the profile. Whitelist—Accepts SIP requests that match the profile.
– Blacklist—Rejects SIP requests that match the profile. Blacklist—Rejects SIP requests that match the profile.
• Description—A brief description of the profile. Description—A brief description of the profile.
|
SIP Profile >
Method Profile
|
The SIP Method Profiles table contains the following information:
• Name—The name of the SIP method profile. Name—The name of the SIP method profile.
• Status—Whether or not the profile is in use. Status—Whether or not the profile is in use.
• Profile Type—The type of profile: Profile Type—The type of profile:
– Whitelist—Accepts SIP requests that match the profile. Whitelist—Accepts SIP requests that match the profile.
– Blacklist—Rejects SIP requests that match the profile. Blacklist—Rejects SIP requests that match the profile.
• Description—A brief description of the profile. Description—A brief description of the profile.
• Is Passthrough—Whether or not passthrough is enabled: Is Passthrough—Whether or not passthrough is enabled:
– True—Permits message bodies to be passed through for nonvital methods that match this profile. True—Permits message bodies to be passed through for nonvital methods that match this profile.
– False—Strips the message body out of any nonvital SIP messages that match this profile. False—Strips the message body out of any nonvital SIP messages that match this profile.
|
SIP Profile >
Option Profile
|
The SIP Option Profiles table contains the following information:
• Name—The name of the SIP option profile. Name—The name of the SIP option profile.
• Status—Whether or not the profile is in use. Status—Whether or not the profile is in use.
• Profile Type—The type of profile: Profile Type—The type of profile:
– Whitelist—Accepts SIP requests that match the profile. Whitelist—Accepts SIP requests that match the profile.
– Blacklist—Rejects SIP requests that match the profile. Blacklist—Rejects SIP requests that match the profile.
• Description—A brief description of the profile. Description—A brief description of the profile.
• Options—The SIP option strings that define this profile, such as host user-agent, refer redirect, or replaces. Options—The SIP option strings that define this profile, such as host user-agent, refer redirect, or replaces.
|
SIP Profile >
Parameter Profile
|
The SIP Parameter Profiles table contains the following information:
• Name—The name of the SIP parameter profile. Name—The name of the SIP parameter profile.
• Status—Whether or not the profile is in use. Status—Whether or not the profile is in use.
• Description—A brief description of the profile. Description—A brief description of the profile.
|
SIP Timer
|
The SBE SIP Timer table contains the following information:
• TCP Connect Timeout—The time, in milliseconds, that the SBC waits for a SIP TCP connection to a remote peer to complete before failing that connection. The default is 1000 milliseconds. TCP Connect Timeout—The time, in milliseconds, that the SBC waits for a SIP TCP connection to a remote peer to complete before failing that connection. The default is 1000 milliseconds.
• TCP Idle Timeout—The minimum time, in milliseconds, that a TCP socket does not process any traffic before it closes the connection. The default is 120000 milliseconds (2 minutes). TCP Idle Timeout—The minimum time, in milliseconds, that a TCP socket does not process any traffic before it closes the connection. The default is 120000 milliseconds (2 minutes).
• TLS Idle Timeout—The minimum time, in milliseconds, that a Transport Layer Security (TLS) socket does not process traffic before it closes the connection. TLS Idle Timeout—The minimum time, in milliseconds, that a Transport Layer Security (TLS) socket does not process traffic before it closes the connection.
• Invite Timeout—The time, in seconds, that the SBC waits for a final response to an outbound SIP invite request. The default is 180 seconds. If no response is received during that time, an internal request timeout response is generated and returned to the caller. Invite Timeout—The time, in seconds, that the SBC waits for a final response to an outbound SIP invite request. The default is 180 seconds. If no response is received during that time, an internal request timeout response is generated and returned to the caller.
• UDP First Retransmit Interval—The time, in milliseconds, that the SBC waits for a UDP response or ACK before sending the first retransmission of a signal. The default value is 500 milliseconds. UDP First Retransmit Interval—The time, in milliseconds, that the SBC waits for a UDP response or ACK before sending the first retransmission of a signal. The default value is 500 milliseconds.
• UDP Max Retransmit Interval—The maximum time interval, in milliseconds, for an SBC to retransmit a signal. The maximum retransmission interval is 4000 milliseconds (4 seconds). UDP Max Retransmit Interval—The maximum time interval, in milliseconds, for an SBC to retransmit a signal. The maximum retransmission interval is 4000 milliseconds (4 seconds).
• UDP Response Linger Period—The time, in milliseconds, for which the SBC retains negative UDP responses to invite requests. The default value is 32000 milliseconds (32 seconds). UDP Response Linger Period—The time, in milliseconds, for which the SBC retains negative UDP responses to invite requests. The default value is 32000 milliseconds (32 seconds).
|
Related Topics
• Viewing AAA Properties
Viewing AAA Properties
• Viewing H.248 Properties
Viewing H.248 Properties
• Viewing Policy Properties
Viewing Policy Properties


Protocol and media interworking
Session routing
Hosted Network Address Translation (NAT) and firewall traversal
Security and AAA
Intra- and inter-VPN interconnections and optimization
Media transcoding with an external media server
Data Border Element (DBE)—Responsible for media-related functions.
Signaling Border Element (SBE)—Responsible for call signaling-related functions.
The existing Cisco SBC platforms support only DBE.
Distributed Model (DM)—Contains only the SBE or DBE, resulting in a distributed SBC.
Unified Model (UM)—Contains both the SBE and DBE, thereby implementing the SBE and DBE as a single device.
User Roles Required to View SBC Properties
Viewing SBC Properties in Logical Inventory
For GUI-based tasks (tasks that do not affect elements), authorization is based on the default permission that is assigned to your user account.
For element-based tasks (tasks that do affect elements), authorization is based on the default permission that is assigned to your account. That is, whether the element is in one of your assigned scopes and whether you meet the minimum security level for that scope.
Table 19-1 identifies the tasks that you can perform if a selected element is not in one of your assigned scopes.
Table 19-2 identifies the tasks that you can perform if a selected element is in one of your assigned scopes.
Viewing SBC Properties in Logical Inventory
Viewing Media Address Properties
Viewing VDBE H.248 Properties
Viewing VDBE H.248 Properties
Viewing SBC Properties in Logical Inventory
Viewing SBC Properties in Logical Inventory
Viewing SBC Properties in Logical Inventory

 Feedback
Feedback