-
Voice and Video Enabled IPSec VPN (V3PN) Solution Reference Network Design
-
Preface
-
V3PN SRND Introduction
-
V3PN Solution Overview and Best Practices
-
V3PN Solution Components
-
Planning and Design
-
Product Selection
-
Implementation and Configuration
-
Verification and Troubleshooting
-
Network Diagram Scalability Testbed and Configuration Files
-
Configuration Supplement--Voice Module, EIGRP Stub, DSCP, HDLC
-
Configuration Supplement--Dynamic Crypto Maps, Reverse Route Injection
-
Table Of Contents
Configuration Supplement—Voice Module, EIGRP Stub, DSCP, HDLC
Router Configuration—vpn18-2600-2
Router Configuration—vpn18-2600-3
Router Configuration—vpn18-2600-4
Router Configuration—vpn18-2600-8
Router Configuration—vpn18-2600-9
Router Configuration—vpn18-2600-10
Router Configuration—vpn18-2600-6
Configuration Supplement—Voice Module, EIGRP Stub, DSCP, HDLC
This appendix contains supplemental configurations used during a V3PN performance and scalability evaluation. Specific configurations address the following devices and supporting networking functions:
•
Router Configuration—vpn18-2600-2
•
Router Configuration—vpn18-2600-3
•
Router Configuration—vpn18-2600-4
•
Router Configuration—vpn18-2600-8
•
Router Configuration—vpn18-2600-9
•
Router Configuration—vpn18-2600-10
•
Router Configuration—vpn18-2600-6
Voice Module Configuration
The full-scale solution test was designed to validate a site-to-site VoIP over IPSec solution where the voice bearer traffic would be received on the LAN interface rather than generated locally by the router from a voice network module.
The purpose of this appendix is to create a single rack (small scale) configuration to supplement the main design guide to include the follow capabilities:
•
IPSec transport mode configuration example
•
EIGRP stub configuration
•
Redundant configuration for dual WAN aggregation routers in addition to dual IPSec/GRE head-end routers
•
Implement DSCP based class-map
HDLC sample configuration for a point-to-point WAN link
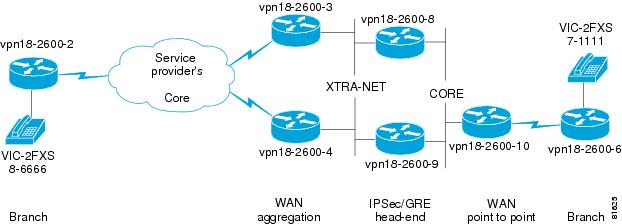
Figure B-1 illustrates an example network configuration.
Figure B-1 Topology Diagram
These configuration examples do not include class-map, policy-map or ISAKMP policy configurations unless they differ from the configurations illustrated previously in this design guide.
To simplify the topology drawing, the interface descriptions in the following router configurations include the keywords XTRA-NET and CORE or in the case of serial links, the router on the opposite end of the link is listed. The addressing scheme is configured such that the 192.168.x.0 subnets would represent routable addresses (Non-RFC 1918) and the 10.0.0.0 address space would be representative of where an enterprise might deploy that address space.
The third octet of the loopback 0 interface on the devices shown is the same as the last digit of the host name. For example, router vpn18-2600-8 has the loopback address of 192.168.8.1.
It should be noted, that while IPSec transport mode decreases the WAN interface bandwidth requirements, it does not decrease the number of packets per second, which in most cases, is the limiting factor of a router's performance. The priority keyword of the voice class in the policy-map was not decreased from the value used in the design guide—bandwidth not used by the priority, or low-latency queue, is not wasted; it is available to the bandwidth classes.
In IPSec transport mode, a G.729 voice call uses 48,000 bps (Layer 3 - 120 bytes * 50 pps * 8 = 48,000) verses 54,400 bps (Layer 3 - 136 bytes * 50 pps * 8 = 54,400). With one voice call active between the two handsets and VAD disabled, the following is an example show interface display output:
vpn18-2600-6#show interface se 0/1 | include rateQueueing strategy: weighted fair30 second input rate 50000 bits/sec, 50 packets/sec30 second output rate 50000 bits/sec, 50 packets/secIn these configuration examples, the alternate or backup path is not used unless the primary path is unavailable. Both the logical path (the GRE tunnel) and the physical path are similar. Router vpn18-2600-3 and vpn18-2600-8 are the primary logical and physical path and vpn18-2600-4 and vpn18-2600-9 are the backup logical and physical path.
With this addressing scheme, recursive routing is addressed by more specific static routes targeted to the interface, while a supernet, 192.168.0.0/16 is advertised via EIGRP through the tunnel interface. Also note the core routers do not have a route to 192.168.6.1, the IPSec/GRE address for vpn18-2600-6, this is not an oversight, rather an illustration data traffic can be encrypted from network end to end without reachability to IPSec/GRE endpoints.
In the case of routers vpn18-2600-8 and vpn18-2600-9, no QoS is enabled on these IPSec/GRE endpoints, QoS is addressed by the WAN aggregation routers vpn18-2600-3 and vpn18-2600-4, as well as the remote branch router vpn18-2600-2. However, in the case of vpn18-2600-10 and vpn18-2600-6, IPSec/GRE and QoS are configured on the same router. Either configuration is valid, however, from a design standpoint, separating QoS from IPSec/GRE head-end routers should be considered a more scalable and manageable approach.
Router Configuration—vpn18-2600-2
!hostname vpn18-2600-2!boot system flash c2600-ik9s-mz.122-8.T!crypto isakmp key bigsecret address 192.168.8.1crypto isakmp key bigsecret address 192.168.9.1!crypto ipsec transform-set vpn-test esp-3des esp-sha-hmacmode transport!crypto map static-map local-address Loopback0crypto map static-map 10 ipsec-isakmpset peer 192.168.8.1set transform-set vpn-testmatch address vpn-static1crypto map static-map 20 ipsec-isakmpset peer 192.168.9.1set transform-set vpn-testmatch address vpn-static2!interface Loopback0ip address 192.168.2.1 255.255.255.252!interface Loopback1description Target address for dial peerip address 10.0.3.1 255.255.255.0!interface Tunnel0ip address 10.0.100.1 255.255.255.0ip summary-address eigrp 44 10.0.0.0 255.255.252.0 5qos pre-classifytunnel source Loopback0tunnel destination 192.168.8.1 # Primary IPSec/GRE peer vpn18-2600-8crypto map static-map!interface Tunnel1ip address 10.0.101.1 255.255.255.0ip summary-address eigrp 44 10.0.0.0 255.255.252.0 5delay 60000 # Increasing the delay makes this the! # backup peerqos pre-classifytunnel source Loopback0tunnel destination 192.168.9.1 # Backup IPSec/GRE peer vpn18-2600-9crypto map static-map!interface Serial0/0bandwidth 512no ip addressencapsulation frame-relayframe-relay traffic-shaping!interface Serial0/0.100 point-to-pointdescription Link to vpn18-2600-3bandwidth 512ip address 192.168.100.1 255.255.255.0frame-relay interface-dlci 100class ts-branchcrypto map static-map!interface Serial0/0.101 point-to-pointdescription Link to vpn18-2600-4bandwidth 512ip address 192.168.101.1 255.255.255.0frame-relay interface-dlci 101class ts-branchcrypto map static-map!router eigrp 44network 10.0.0.0no auto-summaryeigrp stub summary # EIGRP stub configuredeigrp log-neighbor-changes!! Two static routes to the head-end IPSec peers, 192.168.8.1 and! 192.168.9.1 covered by the netmask of 255.255.254.0, the primary! path to vpn18-2600-3 if available, otherwise use the second route! with its higher administrative distance.!ip route 192.168.8.0 255.255.254.0 Serial0/0.100ip route 192.168.8.0 255.255.254.0 Serial0/0.101 2!ip access-list extended vpn-static1permit gre host 192.168.2.1 host 192.168.8.1ip access-list extended vpn-static2permit gre host 192.168.2.1 host 192.168.9.1!voice-port 1/0/0description 8-6666!dial-peer voice 10 voipdestination-pattern 155467.....session target ipv4:10.251.0.1 # vpn18-2600-6ip qos dscp ef mediaip qos dscp af31 signalingno vad!dial-peer voice 1 potsdestination-pattern 15556786666port 1/0/0!endRouter Configuration—vpn18-2600-3
!hostname vpn18-2600-3!boot system flash c2600-ik9s-mz.122-8.T!interface Serial0/0description link to vpn18-2600-4bandwidth 2000ip address 192.168.99.3 255.255.255.0clockrate 2000000!interface FastEthernet0/1description XTRA-NETip address 10.254.1.42 255.255.255.0!interface Serial0/1bandwidth 512no ip addressencapsulation frame-relayframe-relay traffic-shaping!interface Serial0/1.100 point-to-pointdescription Link to vpn18-2600-2bandwidth 512ip address 192.168.100.2 255.255.255.0frame-relay interface-dlci 100class ts-headend!router eigrp 44redistribute staticpassive-interface Serial0/1.100network 10.0.0.0network 192.168.99.0network 192.168.100.0default-metric 64000 20000 255 1 1500no auto-summaryeigrp log-neighbor-changes!! Create a /16 route to be advertised to vpn18-2600-6!ip route 192.168.0.0 255.255.0.0 Null0!! Redistribute the primary path into EIGRP, so vpn18-2600-4 will learn! an EIGRP external dynamically.!ip route 192.168.2.0 255.255.255.0 Serial0/1.100!endRouter Configuration—vpn18-2600-4
!hostname vpn18-2600-4!boot system flash c2600-ik9s-mz.122-8.T!interface Serial0/0description link to vpn18-2600-3bandwidth 2000ip address 192.168.99.4 255.255.255.0!interface FastEthernet0/1description XTRA-NETip address 10.254.1.46 255.255.255.0!interface Serial0/1bandwidth 512no ip addressencapsulation frame-relayframe-relay traffic-shaping!interface Serial0/1.101 point-to-pointdescription link to vpn18-2600-2bandwidth 512ip address 192.168.101.2 255.255.255.0frame-relay interface-dlci 101class ts-headend!router eigrp 44redistribute staticpassive-interface Serial0/1.101network 10.0.0.0network 192.168.99.0network 192.168.101.0default-metric 64000 20000 255 1 1500no auto-summaryeigrp log-neighbor-changes!!! Create a /16 route to be advertised to vpn18-2600-6!ip route 192.168.0.0 255.255.0.0 Null0!! Due to admin distance of 240, this route will only be placed! in the routing table if the EIGRP external (admin distance 170)! from vpn18-2600-3 is withdrawn.!ip route 192.168.2.0 255.255.255.0 Serial0/1.101 240!endRouter Configuration—vpn18-2600-8
!hostname vpn18-2600-8!boot system flash c2600-ik9s-mz.122-8.Tcrypto isakmp key bigsecret address 192.168.2.1!crypto ipsec transform-set vpn-test esp-3des esp-sha-hmacmode transport!crypto map static-map local-address Loopback0crypto map static-map 10 ipsec-isakmpset peer 192.168.2.1set transform-set vpn-testmatch address vpn-static1!interface Loopback0ip address 192.168.8.1 255.255.255.0!interface Tunnel0ip address 10.0.100.2 255.255.255.0tunnel source Loopback0tunnel destination 192.168.2.1 # vpn18-2600-2crypto map static-map!interface FastEthernet0/1description COREip address 10.254.0.48 255.255.255.0!interface Ethernet1/0description XTRA-NETip address 10.254.1.48 255.255.255.0crypto map static-map!router eigrp 44redistribute staticnetwork 10.0.0.0network 192.168.8.0default-metric 64000 20000 255 1 1500distribute-list 44 out Tunnel0no auto-summaryeigrp log-neighbor-changes!! Create a /8 route to be advertised to the remote sites!ip route 10.0.0.0 255.0.0.0 Null0!ip access-list extended vpn-static1permit gre host 192.168.8.1 host 192.168.2.1!! Only need to send a /8 and /16 across the tunnel interface!access-list 44 permit 10.0.0.0access-list 44 permit 192.168.0.0access-list 44 deny any!endRouter Configuration—vpn18-2600-9
!hostname vpn18-2600-9!boot system flash c2600-ik9s-mz.122-8.T!crypto isakmp key bigsecret address 192.168.2.1!crypto ipsec transform-set vpn-test esp-3des esp-sha-hmacmode transport!crypto map static-map local-address Loopback0crypto map static-map 10 ipsec-isakmpset peer 192.168.2.1set transform-set vpn-testmatch address vpn-static1!interface Loopback0ip address 192.168.9.1 255.255.255.0!interface Tunnel1ip address 10.0.101.2 255.255.255.0delay 60000tunnel source Loopback0tunnel destination 192.168.2.1 # vpn18-2600-2crypto map static-map!interface FastEthernet0/1description COREip address 10.254.0.49 255.255.255.0!interface Ethernet1/0description XTRA-NETip address 10.254.1.49 255.255.255.0crypto map static-map!router eigrp 44redistribute staticnetwork 10.0.0.0network 192.168.9.0default-metric 64000 20000 255 1 1500distribute-list 44 out Tunnel1no auto-summaryeigrp log-neighbor-changes!! Create a /8 route to be advertised to the remote sites!ip route 10.0.0.0 255.0.0.0 Null0!ip access-list extended vpn-static1permit gre host 192.168.9.1 host 192.168.2.1!! Only need to send a /8 and /16 across the tunnel interface!access-list 44 permit 10.0.0.0access-list 44 permit 192.168.0.0access-list 44 deny any!endRouter Configuration—vpn18-2600-10
!hostname vpn18-2600-10!boot system flash c2600-ik9s-mz.122-8.T!! Example of matching on DSCP rather than IP Precedence!class-map match-all call-setupdescription AF31match ip dscp 26class-map match-any mission-criticaldescription cs2 and cs6match ip dscp 16match ip dscp 48class-map match-all voicedescription EFmatch ip dscp 46!policy-map hdlcclass voicepriority 672class call-setupbandwidth percent 5class mission-criticalbandwidth percent 22class class-defaultfair-queue!crypto isakmp key bigsecret address 192.168.6.1!crypto ipsec transform-set vpn-test esp-3des esp-sha-hmacmode transport!crypto map HDLC local-address Loopback0crypto map HDLC 10 ipsec-isakmpset peer 192.168.6.1set transform-set vpn-testmatch address hdlc-GRE!interface Loopback0ip address 192.168.10.1 255.255.255.0!interface Tunnel1ip address 10.249.0.2 255.255.255.0tunnel source Loopback0tunnel destination 192.168.6.1 # vpn18-2600-6crypto map HDLC!interface Serial0/0description to vpn-2600-6 se0/1bandwidth 2000ip address 192.168.65.2 255.255.255.0service-policy output hdlcclockrate 2000000crypto map HDLC!interface FastEthernet0/1description COREip address 10.254.0.50 255.255.255.0!router eigrp 44passive-interface Serial0/0network 10.0.0.0network 192.168.10.0distribute-list 44 out Tunnel1no auto-summaryeigrp log-neighbor-changesno eigrp log-neighbor-warnings!! Need to know how to reach the crypto peer vpn18-2600-6!ip route 192.168.6.0 255.255.255.0 Serial0/0!ip access-list extended hdlc-GREpermit gre host 192.168.10.1 host 192.168.6.1!! Only need to send a /8 and /16 across the tunnel interface!access-list 44 permit 10.0.0.0access-list 44 permit 192.168.0.0access-list 44 deny any!endRouter Configuration—vpn18-2600-6
!hostname vpn18-2600-6!boot system flash c2600-ik9s-mz.122-8.T!policy-map hdlcclass voicepriority 672class call-setupbandwidth percent 5class mission-criticalbandwidth percent 22class class-defaultfair-queue!crypto isakmp key bigsecret address 192.168.10.1!crypto ipsec transform-set vpn-test esp-3des esp-sha-hmacmode transport!crypto map HDLC local-address Loopback0crypto map HDLC 10 ipsec-isakmpset peer 192.168.10.1set transform-set vpn-testmatch address hdlc-GRE!interface Loopback0description target for IPSecip address 192.168.6.1 255.255.255.0!interface Loopback1description target for VoIP dial-peersip address 10.251.0.1 255.255.255.0!interface Tunnel1ip address 10.249.0.1 255.255.255.0!! Summarize up to the network core!ip summary-address eigrp 44 10.248.0.0 255.248.0.0 5qos pre-classifytunnel source Loopback0tunnel destination 192.168.10.1 # vpn18-2600-10crypto map HDLC!interface Serial0/1description to vpn-2600-10 se0/0bandwidth 2000ip address 192.168.65.1 255.255.255.0service-policy output hdlccrypto map HDLC!router eigrp 44passive-interface Serial0/1network 10.0.0.0no auto-summaryeigrp stub summaryeigrp log-neighbor-changesno eigrp log-neighbor-warnings!! Need to know how to reach crypto peer vpn18-2600-10!ip route 192.168.10.0 255.255.255.0 Serial0/1!ip access-list extended hdlc-GREpermit gre host 192.168.6.1 host 192.168.10.1voice-port 1/0/0description 7-1111!dial-peer voice 10 voipdestination-pattern 155567.....session target ipv4:10.0.3.1ip qos dscp ef mediaip qos dscp af31 signalingno vad!dial-peer voice 1 potsdestination-pattern 15546771111port 1/0/0!end