-
Cisco Prime Access Registrar 6.1 User Guide
-
Preface
-
Overview
-
Using the aregcmd Commands
-
Using the Graphical User Interface
-
Cisco Prime Access Registrar Server Objects
-
Using the radclient Command
-
Configuring Local Authentication and Authorization
-
RADIUS Accounting
-
Diameter
-
Extensible Authentication Protocols
-
Using WiMAX in Cisco Prime Access Registrar
-
Using Extension Points
-
Using Replication
-
Using On-Demand Address Pools
-
Using Identity Caching
-
Using Trusted ID Authorization with SESM
-
Using Prepaid Billing
-
Using Cisco Prime Access Registrar Server Features
-
Directing RADIUS Requests
-
Using FastRules to Process Packet Flow
-
Wireless Support
-
Using LDAP
-
Using Open Database Connectivity
-
SIGTRAN-M3UA
-
Using SNMP
-
Enforcement of Licensing Models
-
Backing Up the Database
-
Using the REX Accounting Script
-
Logging Syslog Messages
-
Troubleshooting Cisco Prime Access Registrar
-
Cisco Prime Access Registrar Tcl, REX and Java Dictionaries
-
Environment Dictionary
-
RADIUS Attributes
-
Glossary
-
Index
-
Table Of Contents
Using FastRules to Process Packet Flow
Using FastRules to Process Packet Flow
While using rule policy engine and scripting points to process packet flow, you need to be familiar with programming languages, and create scripts to attach them to the Prime Access Registrar configuration. FastRules concept is an easier and efficient alternative to rule policy engine and scripting points.
FastRules provides a mechanism to easily choose the right authentication, authorization, accounting, and query service(s), drop, reject, or break flows, run a script, choose a session manager and/or a chain of fast rules required for processing a packet.
FastRules has the following capabilities:
•
Provides maximum flexibility and ease in matching information in the incoming packets for choosing the appropriate service to apply
•
Provides an option to match values in AVPs based on value ranges, exact match, and simple string comparisons using regex
•
Provides easy and efficient alternative to rule/policy engine and scripting points for most common use cases—reduces the use of external scripts to choose an appropriate service
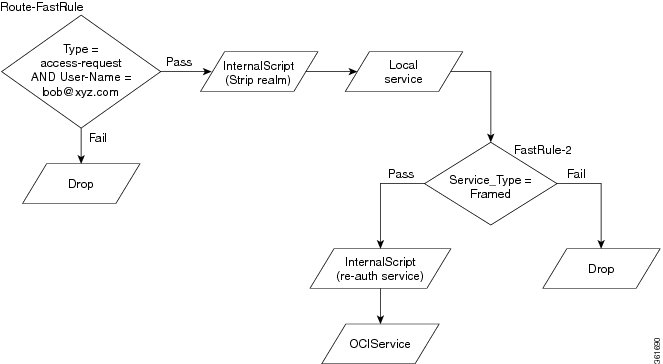
Figure 19-1 describes the workflow for FastRules.
FastRules also provides an option to use Internal Scripts as part of the workflow. Internal scripts allow you to add, modify, or delete attributes in the request, response, and environment dictionaries for RADIUS, Diameter, and TACACS+. For more information about internal scripts, see Internal Scripts.
Figure 19-1 FastRules Workflow
Configuring FastRules
FastRules can be configured either through the GUI or through a CLI. For more information on configuring fast rules through the GUI, see FastRules.
A sample CLI for configuring fast rules is given below:
[ //localhost/Radius/Fastrules]Ruledefintions\radroot\Name = radrootDesc =Protocol = RadiusCondition = A1 AND (A2 OR A3)Success = Authen(mod1)-->fr2-->Author(oci)Failure =Attributes\A1\Name = A1Attribute = Calling-station-idValue = 1.2.3.4A2\Name = A2Attribute = User-nameValue = bobA3\Name = A3Attribute = User-nameValue = BEGINS_WITH(jane)fr1\Name = fr1Desc =Protocol = RadiusCondition = Attri1Success = Authen(proxy)Failure = DROPAttributes\Attri1\Name = Attr1Attribute = Calling-station-idValue = 2.3.4.5fr2\Name = fr2Desc =Protocol = RadiusCondition = Attribute1Success = Authen(local)Failure =Attributes\Attribute1\Name = Attribute1Attribute = StatusValue = Failure.Order\Radius\1. radroot2. fr1Diameter\1.Tacacs\1.Services\mod1\Name = mod1Desc =Type = modService = ldapDictionary\+env:Calling = req:Calling-Station-Id-req:Calling-Station-Id = ""+req:Calling-Station-Id = "5.6.7.8"+res:Calling-Station-Id = env:Calling#res:Called-Station-Id = "123456789"

 Feedback
Feedback