Table Of Contents
Release Notes for Network Admission Control, Release 1.0
Protection Against Denial-of-Service Attacks
Cisco Access Control Server (ACS)
System Caveats and Performance
Language Support for Operating Systems
Release Notes for Network Admission Control, Release 1.0
Contents
•
IOS
•
Cisco Access Control Server (ACS)
•
System Caveats and Performance
Introduction
The following release notes apply to Network Admission Control (NAC), Release 1.0 (formerly referred to as Phase One or Phase 1 Solution). NAC was released in June, 2004.
Document Purpose
This document describes the limitations of Network Admission Control, Release 1.0. For detailed release notes about the individual NAC components, refer to the links in Table 1.
Audience
The target audience for this document is the system engineers and network administrators responsible for the implementation of Network Admission Control (NAC).
NAC Overview
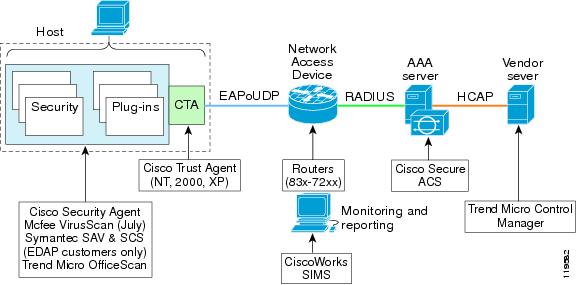
Virus infection on data networks has become an increasingly serious problem. The resources consumed during just one disinfection process are much greater than the resources necessary to implement an anti-virus feature in the network such as Network Admission Control. Cisco's Network Admission Control (NAC) is such a feature and is deployed to ensure the health of all client workstations prior to those workstations being granted network access. NAC is a technology that works in conjunction with anti-virus vendor's software to assess the condition or "posture" of a client prior to granting network access. This ensures a workstation has an up-to-date virus signature set and has not been infected prior to gaining access to a data network. If the workstation requires a signature update an action is sent back to the workstation directing it to complete the update or, if the workstation has been compromised or a network outbreak has occurred, places it into a quarantined network segment until the update or disinfection process can be completed.
Figure 1 NAC Solution Architecture
IOS
Production Enhancements
While 12.3(8)T was released with NAC support in May, 2004 and is currently available, the first IOS rebuild (12.3(8)T.1) has several enhancements and is the version that customers should look at for production deployment.
Auth Proxy
See also the AAA Release Notes located at: http://www.cisco.com/univercd/cc/td/doc/product/software/ios122/122cgcr/fsecur_c/ftrafwl/scfauthp.htm#1001143)
Protection Against Denial-of-Service Attacks
NAC proxy monitors the level of incoming hosts.. For each request, NAC requests the host for posture information. A high number of open requests could indicate that the router is the subject of a denial-of-service (DoS) attack. The authentication proxy limits the level of open requests and drops additional requests until the number of open requests has fallen below 100.
If the router is experiencing a high level of host connection requests requiring posture validation, legitimate hosts may experience delays before posture validation completes.
Risk of Spoofing with NAC
When NAC succeeds, it creates a temporary dynamic access control entry for the host. While this entry exists, another host might spoof the validated host's address to gain access behind the router. NAC does not cause the address spoofing problem; the problem is only identified here as a matter of concern to the user. Spoofing is a problem inherent to all access lists, and NAC does not specifically address this problem.
NAT and NAC
Because EAPoUDP is initiated from a router rather than a host, NAT issues may arise where NAT is deployed between host and router. NAT implementations that depend on a host first having sent an EAPoUDP packet before forwarding an EAPoUDP request from the router are not supported.
However, NAC and NAT can co-exist on the same router.
PAT and NAC
NAC does not support deployments where PAT is enabled between host and the router.
Cisco Trust Agent (CTA)
There have been several minor improvements made to CTA. To take full advantage of these improvements, we strongly recommend that you use CTA version 1.0 or later for production deployments.
Cisco Access Control Server (ACS)
ACS version 3.3 is available on www.cisco.com for upgrades. Refer to Table 1 for links to more information. The ACS Appliance is scheduled to be available in July, 2004.
CiscoWorks SIMS
Ciscoworks SIMS version 3.1.2 is available on www.cisco.com for upgrades. Refer to Table 1 for links to more information. The Ciscoworks SIMS appliance is scheduled to be delivered at a later date.
Cisco Security Agent (CSA)
CSA can protect the other NAC components on the host (posture plug-ins and CTA) and requires a special configuration. Refer to Table 1 for links to more information.
System Caveats and Performance
Language Support for Operating Systems
Currently the US English version of the supported Microsoft operating systems has been fully qualified1 . The following additional language versions of the supported Microsoft operating systems will be qualified in the Summer 2004 timeframe:
•
UK
•
French, Italian, German, Spanish
•
Japanese
•
Chinese
•
Korean
Additional Information
Table 1 Links to Code and Documentation
Software Version Matrix
Refer to the following table to find the system requirements for NAC.
Table 2
System Requirements
Cisco NAC Platform Support
Refer to Table 3 to find the platforms supported by NAC. Table 4 lists specific platforms that are not supported by the current solution.
Table 3 Supported Platforms
Table 4 Platforms Not Supported
Cisco 17XX
1750, 1720, 1710
Cisco 26XX
2600 non-XM models
Cisco 36XX
3620, 3660-CO series
This document is to be used in conjunction with the documents listed in the "Additional Information" section.
Copyright © 2004 Cisco Systems, Inc. All rights reserved.
1 Cisco intends to support (through TAC) CTA on any of the supported Microsoft operating1 systems, not just those that are qualified.