Feedback Feedback
|
Table Of Contents
Overview of Access VPNs and Tunneling Technologies
Benefits to the Enterprise Customers
L2F Tunnel Authentication Process
Three-Way CHAP Authentication Process
Overview of Access VPNs and Tunneling Technologies
Introduction
A virtual private network (VPN) is a network that extends remote access to users over a shared infrastructure. VPNs maintain the same security and management policies as a private network. They are the most cost effective method of establishing a point-to-point connection between remote users and an enterprise customer's network.
There are three main types of VPNs: access VPNs, intranet VPNs, and extranet VPNs.
•
Access VPNs—Provide remote access to an enterprise customer's intranet or extranet over a shared infrastructure. Access VPNs use analog, dial, ISDN, DSL, mobile IP, and cable technologies to securely connect mobile users, telecommuters, and branch offices.
•
Intranet VPNs—Link enterprise customer headquarters, remote offices, and branch offices to an internal network over a shared infrastructure using dedicated connections. Intranet VPNs differ from extranet VPNs in that they only allow access to the enterprise customer's employees.
•
Extranet VPNs—Link outside customers, suppliers, partners, or communities of interest to an enterprise customer's network over a shared infrastructure using dedicated connections. Extranet VPNs differ from intranet VPNS in that they allow access to users outside the enterprise.
This document focuses solely on access VPNs.
Access VPNs
The main attraction of access VPNs is the way they delegate responsibilities for the network. The enterprise customer outsources the responsibility for the information technology (IT) infrastructure to an Internet service provider (ISP) that maintains the modems that the remote users dial into (called modem pools), access servers, and internetworking expertise. The enterprise customer is then only responsible for authenticating its users and maintaining its network.
Instead of connecting directly to the enterprise network by using the expensive public switched telephone network (PSTN), access VPN users only need to use the PSTN to connect to the ISP's local point of presence (POP). The ISP then uses the Internet to forward users from the POP to the enterprise customer network. Forwarding a user's call over the Internet provides dramatic cost saving for the enterprise customer. Access VPNs use layer 2 tunneling technologies to create a virtual point-to-point connection between users and the enterprise customer network. These tunneling technologies provide the same direct connectivity as the expensive PSTN by using the Internet. This means that users anywhere in the world have the same connectivity as they would at the enterprise customer's headquarters.
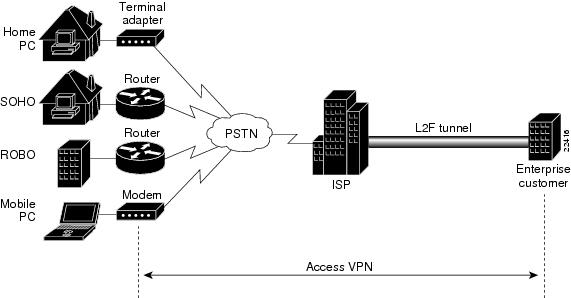
Access VPNs connect a variety of users: from a single, mobile employee to an entire branch office. illustrates the following methods of logging on to access VPNs:
•
Home PC by using a terminal adapter
•
Small office/home office (SOHO) by using a router
•
Remote office/branch office (ROBO) by using a router
•
Mobile PC by using a modem
Figure 1 Logging on to Access VPNs
The access VPN extends from the user to the enterprise customer. The Layer 2 Forwarding (L2F) tunnel is what makes access VPNs unique: Once the tunnel is established, the ISP is transparent to the user and the enterprise customer. The tunnel creates a secure connection between the user and the enterprise customer's network over the insecure Internet and is indistinguishable from a point-to-point connection.
This document describes three end-to-end access VPN case studies, which are primarily intended for ISPs who want to provide access VPN services to enterprise customers. The case studies are also useful to enterprise customers who want to establish access VPNs.
This document does not provide information on the entire spectrum of VPNs, nor does it cover all the details necessary to establish a network. Instead, this document focuses on a specific Layer 2 Forwarding (L2F) case study.
Access VPN Architectures
Access VPNs are designed based on one of two architectural options: client-initiated or network access server (NAS)-initiated access VPNs. A NAS is an access server, maintained by the ISP, that users dial in to and that forwards the call to the enterprise network.
•
Client-initiated access VPNs—Users establish an encrypted IP tunnel across the ISP's shared network to the enterprise customer's network. The enterprise customer manages the client software that initiates the tunnel. The main advantage of client-initiated VPNs is that they secure the connection between the client and the ISP. However, client-initiated VPNs are not as scalable and are more complex than NAS-initiated VPNs.
•
NAS-initiated access VPNs—Users dial in to the ISP's NAS, which establishes an encrypted tunnel to the enterprise's private network. NAS-initiated VPNs are more robust than client-initiated VPNs, allow users to connect to multiple networks by using multiple tunnels, and do not require the client to maintain the tunnel-creating software. NAS-initiated VPNs do not encrypt the connection between the client and the ISP, but this is not a concern for most enterprise customers because the PSTN is much more secure than the Internet.
This document focuses solely on NAS-initiated access VPNs.
ISPs and Enterprise Customers
Access VPNs involve the cooperation of two partners: an internet service provider (ISP) and an enterprise customer.
•
ISP—Responsible for maintaining the modem pool, access servers, and internetworking expertise. Often, the ISP will lease its IT infrastructure to smaller ISPs.
•
Enterprise Customer—Responsible for maintaining its user database and private network. Often, the enterprise customer is a smaller ISP that does not want to take on the expense and commitment of establishing its own IT infrastructure.
In this document, ISP refers to the partner that is responsible for the IT infrastructure, and enterprise customer refers to the partner that leases the IT infrastructure.
Benefits
Access VPNs benefit both ISPs and enterprise customers as described in the following sections.
Benefits to the ISPs
•
Offers end-to-end custom solutions that help differentiate the ISP in an increasingly competitive market
•
Eliminates responsibility of managing the enterprise customer's user database
•
Allows expansion to broadband technologies (such as DSL, cable, and wireless) as they become available
Benefits to the Enterprise Customers
•
Allows enterprise customers to focus on their core business responsibilities
•
Minimizes equipment costs
•
Simplifies complexity of upgrading technology
•
Eliminates need of maintaining internetworking expertise
•
Reduces long distance and 800 number costs
•
Increases flexibility and scalability of connecting and disconnecting branch offices, users, and external partners
•
Prioritizes traffic to ensure bandwidth for critical applications
Access VPN Technologies
Access VPNs use L2F tunnels to tunnel the link layer of high-level protocols (for example, PPP frames or asynchronous High-Level Data Link Control). By using such tunnels, it is possible to detach the location of the ISP's NAS from the location of the enterprise customer's home gateway, where the dial-up protocol connection terminates and access to the enterprise customer's network is provided.
ISPs configure their NASs to receive calls from users and forward the calls to the enterprise customer's home gateway. The ISP only maintains information about the home gateway—the tunnel endpoint. The enterprise customer maintains the home gateway users' IP addresses, routing, and other user database functions. Administration between the ISP and home gateway is reduced to IP connectivity.
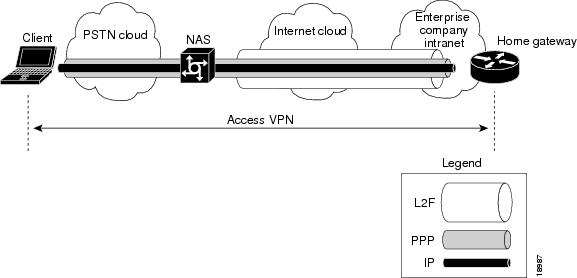
shows the PPP link running between a client (the user's hardware and software) and the home gateway. The NAS and home gateway establish an L2F tunnel that the NAS uses to forward the PPP link to the home gateway. The access VPN then extends from the client to the home gateway. The L2F tunnel creates a virtual point-to-point connection between the client and the home gateway.
Figure 2 End-to-End Access VPN Protocol Flow: L2F, PPP, and IP
The following sections give a functional description of the sequence of events that establish the access VPN:
•
Protocol Negotiation Sequence
•
L2F Tunnel Authentication Process
•
Three-Way CHAP Authentication Process
The "Protocol Negotiation Sequence" section is an overview of the negotiation events that take place as the access VPN is established. The "L2F Tunnel Authentication Process" section gives a detailed description of how the NAS and home gateway establish the L2F tunnel. The "Three-Way CHAP Authentication Process" section gives a detailed description of how the NAS and home gateway authenticate a user.
Protocol Negotiation Sequence
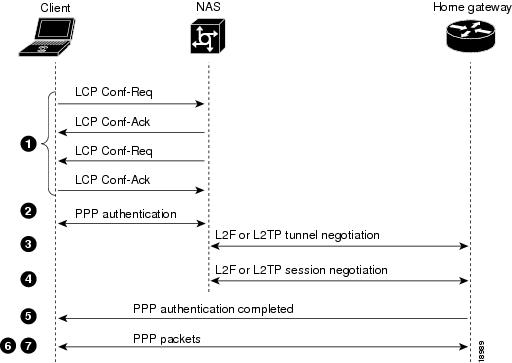
When a user wants to connect to the enterprise customer's home gateway, he or she first establishes a PPP connection to the ISP's NAS. The NAS then establishes an L2F tunnel with the home gateway. Finally, the home gateway authenticates the client's username and password, and establishes the PPP connection with the client.
describes the sequence of protocol negotiation events between the ISP's NAS and the enterprise customer's home gateway.
Figure 3 Protocol Negotiation Events Between Access VPN Devices
explains the sequence of events shown in .
L2F Tunnel Authentication Process
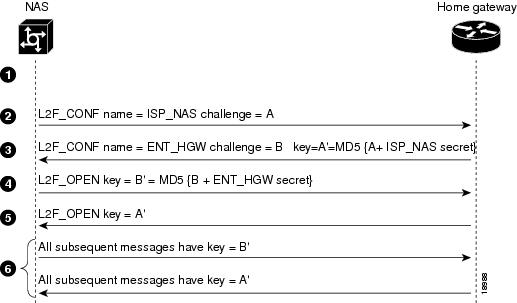
When the NAS receives a call from a client that instructs it to create an L2F tunnel with the home gateway, it first sends a challenge to the home gateway. The home gateway then sends a combined challenge and response to the NAS. Finally, the NAS responds to the home gateway's challenge, and the two devices open the L2F tunnel.
Before the NAS and home gateway can authenticate the tunnel, they must have a common "tunnel secret." A tunnel secret is a pair of usernames with the same password that is configured on both the NAS and the home gateway. By combining the tunnel secret with random value algorithms, which are used to encrypt to the tunnel secret, the NAS and home gateway authenticate each other and establish the L2F tunnel.
describes the tunnel authentication process.
Figure 4 L2F Tunnel Authentication Process
explains the sequence of events shown in .
For more information on L2F, see RFC Level Two Forwarding (Protocol) "L2F."
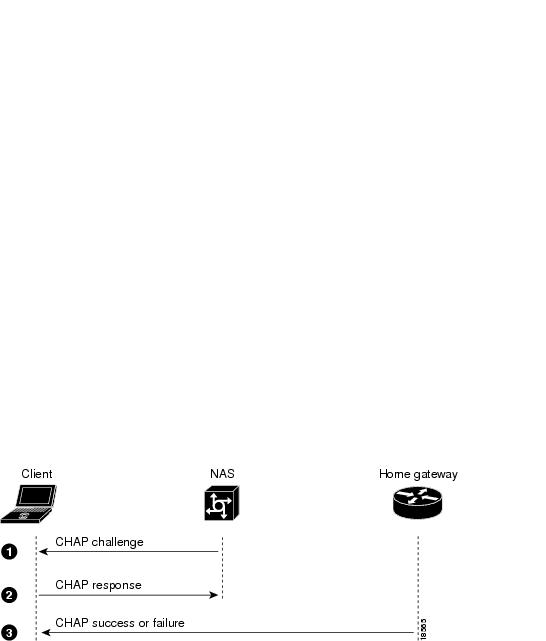
Three-Way CHAP Authentication Process
When establishing an access VPN, the client, NAS, and home gateway use three-way CHAP authentication to authenticate the client's username and password. CHAP is a challenge/response authentication protocol in which the password is sent as a 64-bit signature instead of as plain text. This enables the secure exchange of the user's password between the user's client and the home gateway.
First, the NAS challenges the client, and the client responds. The NAS then forwards this CHAP information to the home gateway, which authenticates the client and sends a third CHAP message (either a success or failure message) to the client.
describes the three-way CHAP authentication process.
Figure 5
Three-Way CHAP Authentication Process
explains the sequence of events shown in .
Table 3 CHAP Event Descriptions
Once the home gateway authenticates the client, the access VPN is established. The L2F tunnel creates a virtual point-to-point connection between the client and the home gateway. The NAS acts as a transparent packet forwarder.
When subsequent clients dial in to the NAS to be forwarded to the home gateway, the NAS and home gateway do not need to repeat the L2F session negotiation because the L2F tunnel is already open.