Feedback Feedback
|
Table Of Contents
Implementing Tunneling for IPv6
Restrictions for Implementing Tunneling for IPv6
Information About Implementing Tunneling for IPv6
IPv6 Manually Configured Tunnels
GRE/IPv4 Tunnel Support for IPv6 Traffic
How to Implement Tunneling for IPv6
Configuring Manual IPv6 Tunnels
Configuring Automatic 6to4 Tunnels
Verifying IPv6 Tunnel Configuration and Operation
Configuration Examples for Implementing Tunneling for IPv6
Example: Configuring Manual IPv6 Tunnels
Example: Configuring GRE Tunnels
Example: Tunnel Destination Address for IPv6 Tunnel
Example: Configuring 6to4 Tunnels
Example: Configuring 6RD Tunnels
Example: Configuring IPv4-Compatible IPv6 Tunnels
Example: Configuring ISATAP Tunnels
Feature Information for Implementing Tunneling for IPv6
Implementing Tunneling for IPv6
First Published: May 5, 2008Last Updated: June 24, 2011This module describes how to configure overlay tunneling techniques used by the Cisco IOS XE software to support the transition from IPv4-only networks to integrated IPv4- and IPv6-based networks. Tunneling encapsulates IPv6 packets in IPv4 packets and uses the IPv4 network as a link-layer mechanism.
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest feature information and caveats, see the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the "Feature Information for Implementing Tunneling for IPv6" section.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Contents
•
Information About Implementing Tunneling for IPv6
•
Restrictions for Implementing Tunneling for IPv6
•
How to Implement Tunneling for IPv6
•
Configuration Examples for Implementing Tunneling for IPv6
•
Feature Information for Implementing Tunneling for IPv6
Restrictions for Implementing Tunneling for IPv6
•
The IPv6 rapid deployment (6RD) feature is supported in an ethernet-only topology.
•
IPv6 VRF is not supported with the 6RD feature.
•
The Cisco ASR 1000 Series Aggregation Services Routers support as many as 2000 6RD tunnel interfaces.
Information About Implementing Tunneling for IPv6
•
IPv6 Manually Configured Tunnels
•
GRE/IPv4 Tunnel Support for IPv6 Traffic
•
IPv6 Rapid Deployment Tunnels
Overlay Tunnels for IPv6
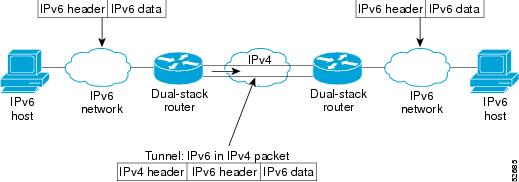
Overlay tunneling encapsulates IPv6 packets in IPv4 packets for delivery across an IPv4 infrastructure (a core network or the Internet (see Figure 1). By using overlay tunnels, you can communicate with isolated IPv6 networks without upgrading the IPv4 infrastructure between them. Overlay tunnels can be configured between border routers or between a border router and a host; however, both tunnel endpoints must support both the IPv4 and IPv6 protocol stacks. Cisco IOS IPv6 supports the following types of overlay tunneling mechanisms:
•
Manual
•
Generic routing encapsulation (GRE)
•
IPv4-compatible
•
6to4
•
Intrasite Automatic Tunnel Addressing Protocol (ISATAP)
Figure 1 Overlay Tunnels
)
Note
Overlay tunnels reduce the maximum transmission unit (MTU) of an interface by 20 octets (assuming the basic IPv4 packet header does not contain optional fields). A network using overlay tunnels is difficult to troubleshoot. Therefore, overlay tunnels connecting isolated IPv6 networks should not be considered as a final IPv6 network architecture. The use of overlay tunnels should be considered as a transition technique toward a network that supports both the IPv4 and IPv6 protocol stacks or just the IPv6 protocol stack.
Use Table 1 to help you determine which type of tunnel you want to configure to carry IPv6 packets over an IPv4 network.
Individual tunnel types are discussed in detail in this document. We recommend that you review and understand the information about the specific tunnel type that you want to implement. When you are familiar with the type of tunnel you need, see Table 2 for a summary of the tunnel configuration parameters that you may find useful.
IPv6 Manually Configured Tunnels
A manually configured tunnel is equivalent to a permanent link between two IPv6 domains over an IPv4 backbone. The primary use is for stable connections that require regular secure communication between two edge routers or between an end system and an edge router, or for connection to remote IPv6 networks.
An IPv6 address is manually configured on a tunnel interface, and manually configured IPv4 addresses are assigned to the tunnel source and the tunnel destination. The host or router at each end of a configured tunnel must support both the IPv4 and IPv6 protocol stacks. Manually configured tunnels can be configured between border routers or between a border router and a host.
GRE/IPv4 Tunnel Support for IPv6 Traffic
IPv6 traffic can be carried over IPv4 GRE tunnels using the standard GRE tunneling technique that is designed to provide the services necessary to implement any standard point-to-point encapsulation scheme. As in IPv6 manually configured tunnels, GRE tunnels are links between two points, with a separate tunnel for each link. The tunnels are not tied to a specific passenger or transport protocol, but in this case carry IPv6 as the passenger protocol with the GRE as the carrier protocol and IPv4 or IPv6 as the transport protocol.
The primary use of GRE tunnels is for stable connections that require regular secure communication between two edge routers or between an edge router and an end system. The edge routers and the end systems must be dual-stack implementations.
GRE has a protocol field that identifies the passenger protocol. GRE tunnels allow Intermediate System-to-Intermediate System (IS-IS) or IPv6 to be specified as a passenger protocol, which allows both IS-IS and IPv6 traffic to run over the same tunnel. If GRE did not have a protocol field, it would be impossible to distinguish whether the tunnel was carrying IS-IS or IPv6 packets. The GRE protocol field is why it is desirable that you tunnel IS-IS and IPv6 inside GRE.
Automatic 6to4 Tunnels
An automatic 6to4 tunnel allows isolated IPv6 domains to be connected over an IPv4 network to remote IPv6 networks. The key difference between automatic 6to4 tunnels and manually configured tunnels is that the tunnel is not point-to-point; it is point-to-multipoint. In automatic 6to4 tunnels, routers are not configured in pairs because they treat the IPv4 infrastructure as a virtual nonbroadcast multiaccess (NBMA) link. The IPv4 address embedded in the IPv6 address is used to find the other end of the automatic tunnel.
An automatic 6to4 tunnel may be configured on a border router in an isolated IPv6 network, which creates a tunnel on a per-packet basis to a border router in another IPv6 network over an IPv4 infrastructure. The tunnel destination is determined by the IPv4 address of the border router extracted from the IPv6 address that starts with the prefix 2002::/16, where the format is 2002:border-router-IPv4-address::/48. Following the embedded IPv4 address are 16 bits that can be used to number networks within the site. The border router at each end of a 6to4 tunnel must support both the IPv4 and IPv6 protocol stacks. 6to4 tunnels are configured between border routers or between a border router and a host.
The simplest deployment scenario for 6to4 tunnels is to interconnect multiple IPv6 sites, each of which has at least one connection to a shared IPv4 network. This IPv4 network could be the global Internet or a corporate backbone. The key requirement is that each site have a globally unique IPv4 address; the Cisco IOS XE software uses this address to construct a globally unique 6to4/48 IPv6 prefix. As with other tunnel mechanisms, appropriate entries in a Domain Name System (DNS) that map between hostnames and IP addresses for both IPv4 and IPv6 allow the applications to choose the required address.
IPv6 Rapid Deployment Tunnels
The 6RD feature is an extension of the 6to4 feature. The 6RD feature allows a service provider (SP) to provide a unicast IPv6 service to customers over its IPv4 network by using encapsulation of IPv6 in IPv4.
The main differences between 6RD and 6to4 tunneling are as follows:
•
6RD does not require addresses to have a 2002::/16 prefix; therefore, the prefix can be from the SP's own address block. This function allows the 6RD operational domain to be within the SP network. From the perspective of customer sites and the general IPv6 internet connected to a 6RD-enabled SP network, the IPv6 service provided is equivalent to native IPv6.
•
All 32 bits of the IPv4 destination need not be carried in the IPv6 payload header. The IPv4 destination is obtained from a combination of bits in the payload header and information on the router. Furthermore, the IPv4 address is not at a fixed location in the IPv6 header as it is in 6to4.
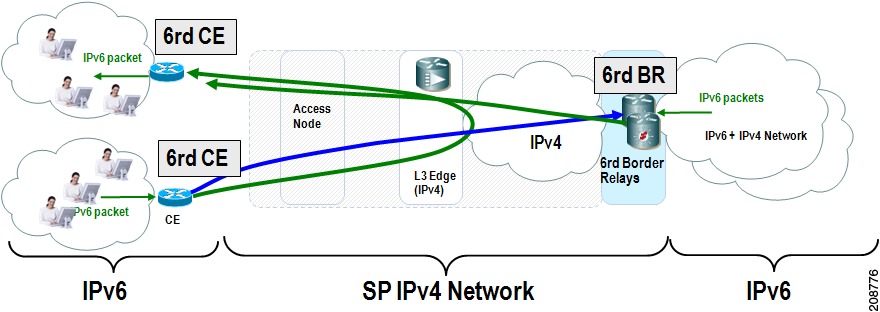
The 6RD SP prefix was selected by the SP for the IPv6 deployment shown in Figure 2. The 6RD delegated prefix is derived from the SP prefix and the IPv4 address bits, and is used by the CE for hosts within its site.
Figure 2 6RD Deployment
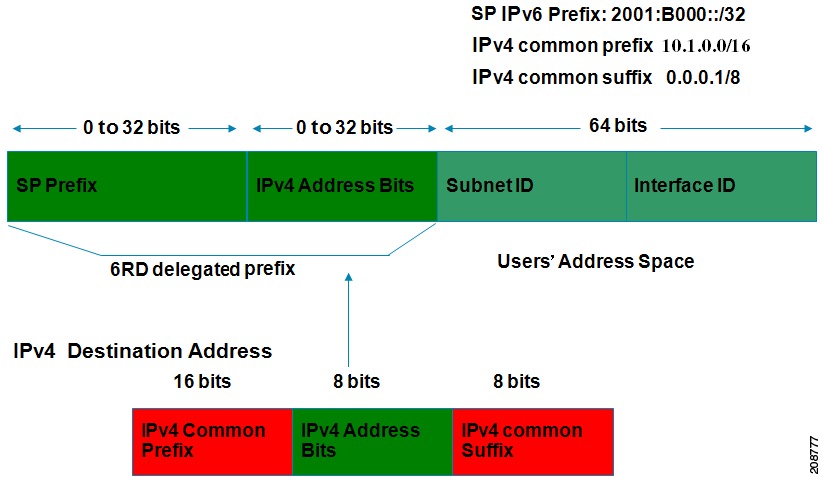
Figure 3 shows how 6RD prefix delegation works.
Figure 3 6RD Prefix Delegation Explanation
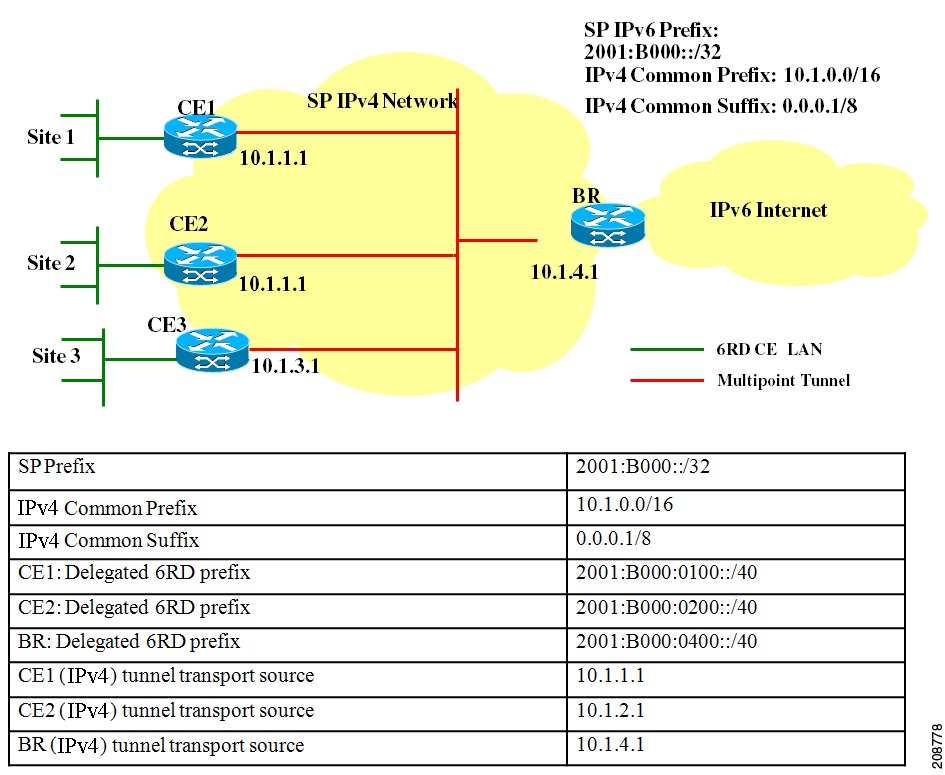
Figure 4 shows a 6RD prefix delegation topology.
Figure 4 6RD Prefix Delegation and Explanation
ISATAP Tunnels
ISATAP is an automatic overlay tunneling mechanism that uses the underlying IPv4 network as a NBMA link layer for IPv6. ISATAP is designed for transporting IPv6 packets within a site where a native IPv6 infrastructure is not yet available; for example, when sparse IPv6 hosts are deployed for testing. ISATAP tunnels allow individual IPv4 or IPv6 dual-stack hosts within a site to communicate with other such hosts on the same virtual link, basically creating an IPv6 network using the IPv4 infrastructure.
The ISATAP router provides standard router advertisement network configuration support for the ISATAP site. This feature allows clients to automatically configure themselves as they would do if they were connected to a GigabitEthernet or FastEthernet. It can also be configured to provide connectivity out of the site. ISATAP uses a well-defined IPv6 address format composed of any unicast IPv6 prefix (/64), which can be link local, or global (including 6to4 prefixes), enabling IPv6 routing locally or on the Internet. The IPv4 address is encoded in the last 32 bits of the IPv6 address, enabling automatic IPv6-in-IPv4 tunneling.
Although the ISATAP tunneling mechanism is similar to other automatic tunneling mechanisms, such as IPv6 6to4 tunneling, ISATAP is designed for transporting IPv6 packets within a site, not between sites.
ISATAP uses unicast addresses that include a 64-bit IPv6 prefix and a 64-bit interface identifier. The interface identifier is created in modified EUI-64 format in which the first 32 bits contain the value 000:5EFE to indicate that the address is an IPv6 ISATAP address. Table 3 describes an ISATAP address format.
Table 3 IPv6 ISATAP Address Format
link local or global IPv6 unicast prefix
0000:5EFE
IPv4 address of the ISATAP link
As shown in Table 3, an ISATAP address consists of an IPv6 prefix and the ISATAP interface identifier. This interface identifier includes the IPv4 address of the underlying IPv4 link. The following example shows what an actual ISATAP address would look like if the prefix is 2001:DB8:1234:5678::/64 and the embedded IPv4 address is 10.173.129.8. In the ISATAP address, the IPv4 address is expressed in hexadecimal as 0AAD:8108:
2001:DB8:1234:5678:0000:5EFE:0AAD:8108
How to Implement Tunneling for IPv6
•
Configuring Manual IPv6 Tunnels
•
Configuring Automatic 6to4 Tunnels
•
Verifying IPv6 Tunnel Configuration and Operation
Configuring Manual IPv6 Tunnels
Prerequisites
With manually configured IPv6 tunnels, an IPv6 address is configured on a tunnel interface, and manually configured IPv4 addresses are assigned to the tunnel source and the tunnel destination. The host or router at each end of a configured tunnel must support both the IPv4 and IPv6 protocol stacks.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface tunnel tunnel-number
4.
ipv6 address {ipv6-address/prefix-length | prefix-name sub-bits/prefix-length}
5.
tunnel source {ip-address | interface-type interface-number}
6.
tunnel destination ip-address
7.
tunnel mode ipv6ip [6rd | 6to4 | auto-tunnel | isatap]
DETAILED STEPS
Step 1
enable
Example:Router> enable
Enables privileged EXEC mode.
•
Enter your password if prompted.
Step 2
configure terminal
Example:Router# configure terminal
Enters global configuration mode.
Step 3
interface tunnel tunnel-number
Example:Router(config)# interface tunnel 0
Specifies a tunnel interface and number, and enters interface configuration mode.
Step 4
ipv6 address {ipv6-address/prefix-length | prefix-name sub-bits/prefix-length}
Example:Router(config-if)# ipv6 address 3ffe:b00:c18:1::3/127
Specifies the IPv6 network assigned to the interface and enables IPv6 processing on the interface.
Note
Refer to the Implementing IPv6 Addressing and Basic Connectivity module for more information on configuring IPv6 addresses.
Step 5
tunnel source {ip-address | interface-type interface-number}
Example:Router(config-if)# tunnel source gigabitethernet 0/0/0
Specifies the source IPv4 address or the source interface type and number for the tunnel interface.
•
If an interface is specified, the interface must be configured with an IPv4 address.
Step 6
tunnel destination ip-address
Example:Router(config-if)# tunnel destination 192.168.30.1
Specifies the destination IPv4 address or hostname for the tunnel interface.
Step 7
tunnel mode ipv6ip [6rd | 6to4 | auto-tunnel | isatap]
Example:Router(config-if)# tunnel mode ipv6ip
Specifies a manual IPv6 tunnel.
Note
The tunnel mode ipv6ip command specifies IPv6 as the passenger protocol and IPv4 as both the encapsulation and transport protocol for the manual IPv6 tunnel.
•
The auto-tunnel keyword is not supported on Cisco ASR 1000 series routers.
Configuring GRE IPv6 Tunnels
GRE tunnels can be configured to run over an IPv6 network layer and to transport IPv6 packets in IPv6 tunnels and IPv4 packets in IPv6 tunnels.
Prerequisites
When GRE IPv6 tunnels are configured, IPv6 addresses are assigned to the tunnel source and the tunnel destination. The tunnel interface can have either IPv4 or IPv6 addresses assigned (this is not shown in the task). The host or router at each end of a configured tunnel must support both the IPv4 and IPv6 protocol stacks.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface tunnel tunnel-number
4.
ipv6 address {ipv6-address/prefix-length | prefix-name sub-bits/prefix-length}
5.
tunnel source {ip-address | ipv6-address | interface-type interface-number}
6.
tunnel destination {host-name | ip-address | ipv6-address}
7.
tunnel mode {aurp | cayman | dvmrp | eon | gre | gre multipoint | gre ipv6 | ipip [decapsulate-any] | iptalk | ipv6 | mpls | nos}
DETAILED STEPS
Configuring Automatic 6to4 Tunnels
Prerequisites
With 6to4 tunnels, the tunnel destination is determined by the border router IPv4 address, which is concatenated to the prefix 2002::/16 in the format 2002:border-router-IPv4-address::/48. The border router at each end of a 6to4 tunnel must support both the IPv4 and IPv6 protocol stacks.
Restrictions
The configuration of only one IPv4-compatible tunnel and one 6to4 IPv6 tunnel is supported on a router. If you choose to configure both of those tunnel types on the same router, we strongly recommend that they do not share the same tunnel source.
The reason that a 6to4 tunnel and an IPv4-compatible tunnel cannot share an interface is that both of them are NBMA "point-to-multipoint" access links and only the tunnel source can be used to reorder the packets from a multiplexed packet stream into a single packet stream for an incoming interface. So when a packet with an IPv4 protocol type of 41 arrives on an interface, that packet is mapped to an IPv6 tunnel interface based on the IPv4 address. However, if both the 6to4 tunnel and the IPv4-compatible tunnel share the same source interface, the router is not able to determine the IPv6 tunnel interface to which it should assign the incoming packet.
IPv6 manually configured tunnels can share the same source interface because a manual tunnel is a "point-to-point" link, and both the IPv4 source and IPv4 destination of the tunnel are defined.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface tunnel tunnel-number
4.
ipv6 address {ipv6-address/prefix-length | prefix-name sub-bits/prefix-length}
5.
tunnel source {ip-address | interface-type interface-number}
6.
tunnel mode ipv6ip [6rd | 6to4 | auto-tunnel | isatap]
7.
exit
8.
ipv6 route [vrf vrf-name] ipv6-prefix/prefix-length {ipv6-address | interface-type interface-number [ipv6-address]} [nexthop-vrf [vrf-name1 | default]] [administrative-distance] [administrative-multicast-distance | unicast | multicast] [next-hop-address] [tag tag]
DETAILED STEPS
Configuring 6RD Tunnels
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface tunnel tunnel-number
4.
ipv6 address {ipv6-address/prefix-length | prefix-name sub-bits/prefix-length}
5.
tunnel mode ipv6ip [6rd | 6to4 | auto-tunnel | isatap]
6.
tunnel 6rd prefix ipv6-prefix/prefix-length
7.
tunnel 6rd ipv4 {prefix-length length} {suffix-length length}
DETAILED STEPS
Configuring ISATAP Tunnels
Prerequisites
The tunnel source command used in the configuration of an ISATAP tunnel must point to an interface with an IPv4 address configured. The ISATAP IPv6 address and prefix (or prefixes) advertised are configured as for a native IPv6 interface. The IPv6 tunnel interface must be configured with a modified EUI-64 address because the last 32 bits in the interface identifier are constructed using the IPv4 tunnel source address.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
interface tunnel tunnel-number
4.
ipv6 address {ipv6-address/prefix-length | prefix-name sub-bits/prefix-length}
5.
no ipv6 nd ra suppress
6.
tunnel source {ip-address | interface-type interface-number}
7.
tunnel mode ipv6ip [6rd | 6to4 | auto-tunnel | isatap]
DETAILED STEPS
Verifying IPv6 Tunnel Configuration and Operation
SUMMARY STEPS
1.
enable
2.
show interfaces tunnel number [accounting]
3.
ping [protocol] destination
4.
show ip route [address [mask]]
5.
show tunnel 6rd [interface-type interface-number]
6.
show tunnel 6rd destination ipv6-prefix tunnel-interface interface-number
7.
show tunnel 6rd prefix ipv4-destination tunnel-interface interface-number
DETAILED STEPS
Examples
•
Sample Output from the show interfaces tunnel Command
•
Sample Output from the ping Command When Checking the Local Endpoint
•
Sample Output from the show ip route Command
•
Sample Output from the ping Command When Checking the Remote Endpoint
Sample Output from the show interfaces tunnel Command
This example uses a generic example suitable for both IPv6 manually configured tunnels and IPv6 over IPv4 GRE tunnels. In the example, two routers are configured to be endpoints of a tunnel. Router A has GigabitEthernet interface 0/0/0 configured as tunnel interface 0 with an IPv4 address of 10.0.0.1 and an IPv6 prefix of 2001:DB8:1111:2222::1/64. Router B has GigabitEthernet interface 0/0/0 configured as tunnel interface 1 with an IPv4 address of 10.0.0.2 and an IPv6 prefix of 2001:DB8:1111:2222::2/64. To verify that the tunnel source and destination addresses are configured, use the show interfaces tunnel command on Router A.
RouterA# show interfaces tunnel 0Tunnel0 is up, line protocol is upHardware is TunnelMTU 1514 bytes, BW 9 Kbit, DLY 500000 usec,reliability 255/255, txload 1/255, rxload 1/255Encapsulation TUNNEL, loopback not setKeepalive not setTunnel source 10.0.0.1 (GigabitEthernet0/0/0), destination 10.0.0.2, fastswitch TTL 255Tunnel protocol/transport GRE/IP, key disabled, sequencing disabledTunnel TTL 255Checksumming of packets disabled, fast tunneling enabledLast input 00:00:14, output 00:00:04, output hang neverLast clearing of "show interface" counters neverInput queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0Queueing strategy: fifoOutput queue :0/0 (size/max)5 minute input rate 0 bits/sec, 0 packets/sec5 minute output rate 0 bits/sec, 0 packets/sec4 packets input, 352 bytes, 0 no bufferReceived 0 broadcasts, 0 runts, 0 giants, 0 throttles0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort8 packets output, 704 bytes, 0 underruns0 output errors, 0 collisions, 0 interface resets0 output buffer failures, 0 output buffers swapped outSample Output from the ping Command When Checking the Local Endpoint
To check that the local endpoint is configured and working, use the ping command on Router A:
RouterA# ping 2001:DB8:1111:2222::2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 2001:DB8:1111:2222::2, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/20/20 msSample Output from the show ip route Command
To check that a route exists to the remote endpoint address, use the show ip route command:
RouterA# show ip route 10.0.0.2Routing entry for 10.0.0.0/24Known via "connected", distance 0, metric 0 (connected, via interface)Routing Descriptor Blocks:* directly connected, via GigabitEthernet0/0/0Route metric is 0, traffic share count is 1Sample Output from the ping Command When Checking the Remote Endpoint
To check that the remote endpoint address is reachable, use the ping command on Router A.
Note
The remote endpoint address may not be reachable using the ping command because of filtering, but the tunnel traffic may still reach its destination.
RouterA# ping 10.0.0.2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/21/28 msTo check that the remote IPv6 tunnel endpoint is reachable, use the ping command again on Router A. The same note on filtering also applies to this example.
RouterA# ping 1::2Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 1::2, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 20/20/20 msThese steps may be repeated at the other endpoint of the tunnel.
Configuration Examples for Implementing Tunneling for IPv6
•
Example: Configuring Manual IPv6 Tunnels
•
Example: Configuring GRE Tunnels
•
Example: Configuring 6to4 Tunnels
•
Example: Configuring 6RD Tunnels
•
Example: Configuring IPv4-Compatible IPv6 Tunnels
•
Example: Configuring ISATAP Tunnels
Example: Configuring Manual IPv6 Tunnels
The following example configures a manual IPv6 tunnel between router A and router B. In the example, tunnel interface 0 for both router A and router B is manually configured with a global IPv6 address. The tunnel source and destination addresses are also manually configured.
Router A Configuration
interface gigabitethernet 0/0/0ip address 192.168.99.1 255.255.255.0interface tunnel 0ipv6 address 3ffe:b00:c18:1::3/127tunnel source gigabitethernet 0/0/0tunnel destination 2001:DB8:1111:2222::1/64tunnel mode ipv6ipRouter B Configuration
interface gigabitethernet 0/0/0ip address 192.168.30.1 255.255.255.0interface tunnel 0ipv6 address 3ffe:b00:c18:1::2/127tunnel source gigabitethernet 0/0/0tunnel destination 2001:DB8:1111:2222::2/64tunnel mode ipv6ipExample: Configuring GRE Tunnels
The following example configures a GRE tunnel running both IS-IS and IPv6 traffic between router A and router B:
Router A Configuration
ipv6 unicast-routingclns routing!interface tunnel 0no ip addressipv6 address 2001:DB8:1111:2222::1/64ipv6 router isistunnel source GigabitEthernet 0/0/0tunnel destination 10.0.0.2tunnel mode gre ipv6!interface GigabitEthernet0/0/0ip address 10.0.0.1 255.255.255.0!router isisnet 49.0000.0000.000a.00Router B Configuration
ipv6 unicast-routingclns routing!interface tunnel 0no ip addressipv6 address 2001:DB8:1111:2222::2/64ipv6 router isistunnel source GigabitEthernet 0/0/0tunnel destination 10.0.0.1tunnel mode gre ipv6!interface GigabitEthernet0/0/0ip address 10.0.0.2 255.255.255.0!router isisnet 49.0000.0000.000b.00address-family ipv6redistribute staticexit-address-familyExample: Tunnel Destination Address for IPv6 Tunnel
The following example shows how to configure the tunnel destination address for GRE tunneling of IPv6 packets:
Router(config)# interface Tunnel0Router(config-if)# ipv6 address 2001:1:1::1/48Router(config-if)# tunnel source GigabitEthernet 0/0/0Router(config-if)# tunnel destination 10.0.0.2Router(config-if)# tunnel mode gre ipv6Router(config-if)# exit!Router(config)# interface GigabitEthernet0/0/0Router(config-if)# ip address 10.0.0.1 255.255.255.0Router(config-if)# exit!Router(config)# ipv6 unicast-routingRouter(config)# router isisRouter(config)# net 49.0000.0000.000a.00Example: Configuring 6to4 Tunnels
The following example configures a 6to4 tunnel on a border router in an isolated IPv6 network. The IPv4 address is 192.168.99.1, which translates to the IPv6 prefix of 2002:c0a8:6301::/48. The IPv6 prefix is subnetted into 2002:c0a8:6301::/64 for the tunnel interface: 2002:c0a8:6301:1::/64 for the first IPv6 network, and 2002:c0a8:6301:2::/64 for the second IPv6 network. The static route ensures that any other traffic for the IPv6 prefix 2002::/16 is directed to tunnel interface 0 for automatic tunneling.
interface GigabitEthernet0/0/0description IPv4 uplinkip address 192.168.99.1 255.255.255.0!interface GigabitEthernet1/0/0description IPv6 local network 1ipv6 address 2002:c0a8:6301:1::1/64!interface GigabitEthernet2/0/0description IPv6 local network 2ipv6 address 2002:c0a8:6301:2::1/64!interface Tunnel0description IPv6 uplinkno ip addressipv6 address 2002:c0a8:6301::1/64tunnel source GigabitEthernet0/0/0tunnel mode ipv6ip 6to4!ipv6 route 2002::/16 tunnel 0Example: Configuring 6RD Tunnels
The following example shows the running configuration of a 6RD tunnel and the corresponding output of the show tunnel 6rd command:
interface Tunnel1ipv6 address 2001:B000:100::1/32tunnel source loopback 1tunnel mode ipv6ip 6rdtunnel 6rd prefix 2001:B000::/32tunnel 6rd ipv4 prefix-len 16 suffix-len 8endRouter# show tunnel 6rd tunnel 1Interface Tunnel1:Tunnel Source: 10.1.1.16RD: Operational, V6 Prefix: 2001:B000::/32V4 Common Prefix Length: 16, Value: 10.1.0.0V4 Common Suffix Length: 8, Value: 0.0.0.1Example: Configuring IPv4-Compatible IPv6 Tunnels
The following example configures an IPv4-compatible IPv6 tunnel that allows Border Gateway Protocol (BGP) to run between a number of routers without having to configure a mesh of manual tunnels. Each router has a single IPv4-compatible tunnel, and multiple BGP sessions can run over each tunnel, one to each neighbor. GigabitEthernet interface 0/0/0 is used as the tunnel source. The tunnel destination is automatically determined by the IPv4 address in the low-order 32 bits of an IPv4-compatible IPv6 address. Specifically, the IPv6 prefix 0:0:0:0:0:0 is concatenated to an IPv4 address (in the format 0:0:0:0:0:0:A.B.C.D or ::A.B.C.D) to create the IPv4-compatible IPv6 address. GigabitEthernet interface 0/0/0 is configured with a global IPv6 address and an IPv4 address (the interface supports both the IPv6 and IPv4 protocol stacks).
Multiprotocol BGP is used in the example to exchange IPv6 reachability information with the peer 10.67.0.2. The IPv4 address of GigabitEthernet interface 0/0/0 is used in the low-order 32 bits of an IPv4-compatible IPv6 address and is also used as the next-hop attribute. Using an IPv4-compatible IPv6 address for the BGP neighbor allows the IPv6 BGP session to be automatically transported over an IPv4-compatible tunnel.
interface tunnel 0tunnel source GigabitEthernet 0/0/0tunnel mode ipv6ip auto-tunnelinterface Gigabitethernet 0/0/0ip address 10.27.0.1 255.255.255.0ipv6 address 3000:2222::1/64router bgp 65000no synchronizationno bgp default ipv4-unicastneighbor ::10.67.0.2 remote-as 65002address-family ipv6neighbor ::10.67.0.2 activateneighbor ::10.67.0.2 next-hop-selfnetwork 2001:2222:d00d:b10b::/64Example: Configuring ISATAP Tunnels
The following example shows the tunnel source defined on GigabitEthernet 0/0/0 and the tunnel mode command used to configure the ISATAP tunnel. Router advertisements are enabled to allow client autoconfiguration.
ipv6 unicast-routinginterface tunnel 1tunnel source Gigabitethernet 0/0/0tunnel mode ipv6ip isatapipv6 address 2001:DB8::/64 eui-64no ipv6 nd ra suppressexitWhere to Go Next
•
If you have configured an automatic 6to4 tunnel you can design your IPv6 network around the /48 6to4 prefix you have created from your IPv4 address.
•
If you want to implement IPv6 routing protocols, refer to the Implementing RIP for IPv6, Implementing IS-IS for IPv6, Implementing OSPF for IPv6, or Implementing Multiprotocol BGP for IPv6 module.
Additional References
Related Documents
IPv6 supported feature list for Cisco IOS XE software
Start Here: Cisco IOS XE Software Release Specifics for IPv6 Features
IPv6 commands: complete command syntax, command mode, defaults, usage guidelines, and examples
Cisco IOS master command list, all releases
Standards
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature.
—
MIBs
None
To locate and download MIBs for selected platforms, Cisco software releases, and feature sets, use Cisco MIB Locator found at the following URL:
RFCs
Technical Assistance
Feature Information for Implementing Tunneling for IPv6
Table 4 lists the features in this module and provides links to specific configuration information.
Use Cisco Feature Navigator to find information about platform support and software image support. Cisco Feature Navigator enables you to determine which software images support a specific software release, feature set, or platform. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Note
Table 4 lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Table 4 Feature Information for Implementing Tunneling for IPv6
IPv6 Tunneling—6RD IPv6 Rapid Deployment
Cisco IOS XE Release 3.1S
The 6RD feature allows a service provider to provide a unicast IPv6 service to customers over its IPv4 network by using encapsulation of IPv6 in IPv4.
The following sections provide information about this feature:
•
IPv6 Rapid Deployment Tunnels
IPv6 Tunneling—Automatic 6to4 Tunnels
Cisco IOS XE Release 2.1
An automatic 6to4 tunnel allows isolated IPv6 domains to be connected over an IPv4 network to remote IPv6 networks.
The following sections provide information about this feature:
IPv6 Tunneling—Automatic IPv4-Compatible Tunnels
Cisco IOS XE Release 2.1
Automatic IPv4-compatible tunnels use IPv4-compatible IPv6 addresses.
The following sections provide information about this feature:
IPv6 Tunneling—IP over IPv6 GRE Tunnels
Cisco IOS XE Release 2.4
GRE tunnels are links between two points, with a separate tunnel for each link.
The following sections provide information about this feature:
•
GRE/IPv4 Tunnel Support for IPv6 Traffic
IPv6 Tunneling—IPv4 over IPv6 Tunnels
Cisco IOS XE Release 2.1
IPv6 supports this feature
The following sections provide information about this feature:
•
IPv6 Manually Configured Tunnels
IPv6 Tunneling—IPv6 over IPv4 GRE Tunnels
Cisco IOS XE Release 2.1
GRE tunnels are links between two points, with a separate tunnel for each link. The tunnels are not tied to a specific passenger or transport protocol, but in this case carry IPv6 as the passenger protocol with the GRE as the carrier protocol and IPv4 or IPv6 as the transport protocol.
The following sections provide information about this feature:
•
GRE/IPv4 Tunnel Support for IPv6 Traffic
IPv6 Tunneling—ISATAP Tunnel Support
Cisco IOS XE Release 2.1
ISATAP is an automatic overlay tunneling mechanism that uses the underlying IPv4 network as a NBMA link layer for IPv6.
The following sections provide information about this feature:
IPv6 Tunneling—Manually Configured IPv6 over IPv4 Tunnels
Cisco IOS XE Release 2.1
A manually configured tunnel is equivalent to a permanent link between two IPv6 domains over an IPv4 backbone.
The following sections provide information about this feature:
•
IPv6 Manually Configured Tunnels
•
Configuring Manual IPv6 Tunnels
Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1005R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2001-2011 Cisco Systems, Inc. All rights reserved.