Table Of Contents
Supported Standards, MIBs, and RFCs
Verifying the Open Garden Configuration
Monitoring and Maintaining Open Garden
SSG Open Garden
Feature History
12.1(5)DC
This feature was introduced on the Cisco 6400 node route processor.
12.2(4)B
This feature was integrated into Cisco IOS Release 12.2(4)B.
This document describes the SSG Open Garden feature in Cisco IOS Release 12.2(4)B. It includes the following sections:
•
Supported Standards, MIBs, and RFCs
•
Monitoring and Maintaining Open Garden
Feature Overview
The SSG Open Garden feature enables you to use Cisco Service Selection Gateway (SSG) to implement open gardens. An open garden is a collection of domains that a subscriber can access without providing authentication information.
SSG
SSG is a switching solution for service providers who offer intranet, extranet, and Internet connections to subscribers using broadband access technology such as digital subscriber lines, cable modems, or wireless to allow simultaneous access to network services.
SSG works in conjunction with the Cisco Service Selection Dashboard (SSD) or its successor product, the Cisco Subscriber Edge Services Manager (SESM). Together with the SESM or SSD, SSG provides subscriber authentication, service selection, and service connection capabilities to subscribers of Internet services. Subscribers interact with an SESM or SSD web application using a standard Internet browser.
SSG acts as a central control point for Layer 2 and Layer 3 services. These can include services available through ATM virtual circuits (VCs), virtual private dial-up networks (VPDNs), or normal routing methods.
SSG communicates with the authentication, authorization, and accounting (AAA) management network where RADIUS, Dynamic Host Configuration Protocol (DHCP), and Simple Network Management Protocol (SNMP) servers reside and with the Internet service provider (ISP) network, which may connect to the Internet, corporate networks, and value-added services.
A licensed version of SSG works with the SESM or SSD to present to subscribers a menu of network services that can be selected from a single graphical user interface (GUI). This functionality improves flexibility and convenience for subscribers and enables service providers to bill subscribers for connect time and services used, rather than charging a flat rate.
For more information about SSG, refer to the Service Selection Gateway feature module in the "New SSG Features in Release 12.2(4)B" area of Cisco.com.
Open Gardens
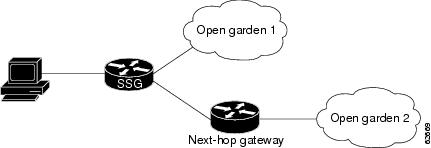
An open garden is a collection of websites or networks that subscribers can access as long as they have physical access to the network. Subscribers do not have to provide authentication information before accessing the websites in an open garden. In contrast, walled garden refers to a collection of websites or networks that subscribers can access after providing minimal authentication information. Figure 1 shows a network topology that includes open gardens.
Figure 1 Open Garden Network Topology
When SSG receives DNS requests, the DNS packets are first processed for the user connection. If the domain match is not found, the packets are processed for open gardens.
In the upstream direction, SSG handles DNS packets by first looking up the domain in the connected-service list. If a match is not found in the connected-service list, the open garden service list is checked. If the domain is not found in the open garden service list and the user has a connected Internet service (0.0.0.0/0), then the DNS request is forwarded to that domain. If the user is not connected to an Internet service and there is an open garden internet service, the DNS request is forwarded to the open garden Internet domain.
In the downstream direction, SSG handles DNS response packets in the same order as they are handled in the upstream direction.
Note
DNS packet processing in an open garden configuration was handled differently by SSG in Cisco IOS Release 12.2(2)B and earlier releases. In the prior releases, DNS domain lookup was performed first in the domains configured in the open garden services. If a match was not found, DNS domain lookup was performed in the connected services of the user.
If SSG receives a packet that is not destined for the open garden, SSG checks the source IP address of the packet to see if the subscriber is authenticated. If SSG recognizes the IP address, the subscriber is authenticated and SSG forwards the packet. If the subscriber is not authenticated and the packet is not a Domain Name Server (DNS) packet, SSG drops the packet.
SSG handles open gardens as services that have associated domain names and DNS addresses. As many as 100 domains can be associated with an open garden. When SSG receives a DNS request for one of the open garden domain names, SSG forwards the request to the open garden DNS server, where the domain name is resolved.
While most SSG services must be bound to an interface or next hop, it is not necessary to bind open garden services that are directly connected to the SSG router. Service binding is mandatory, however, for open garden services that are routed through a next hop.
Benefits
The SSG Open Garden feature gives service providers flexibility in the way they control access to networks and services by allowing them to specify domains that subscribers can access without service subscription.
Restrictions
•
RADIUS accounting records are not created for open garden services.
•
Open garden services can be created by using local profiles only; RADIUS profiles cannot be used.
•
Overlapping open garden service networks are not supported.
•
Overlapping users are not supported.
Related Documents
For more information about SSG, see the following document:
•
Service Selection Gateway, Cisco IOS Release 12.2(4)B feature module
For information about other supported SSG features, see the following documents:
•
Hierarchical Policing for Service Selection Gateway, Cisco IOS Release 12.2(4)B feature module
•
SSG Autodomain, Cisco IOS Release 12.2(4)B feature module
•
SSG AutoLogin Using Proxy Radius, Cisco IOS Release 12.2(4)B feature module
•
SSG Autologoff, Cisco IOS Release 12.2(4)B feature module
•
Service Selection Gateway Accounting Update Interval per Service, Cisco IOS Release 12.2(4)B feature module
•
SSG Port-Bundle Host Key, Cisco IOS Release 12.2(4)B feature module
•
SSG Prepaid, Cisco IOS Release 12.2(4)B feature module
•
SSG TCP Redirect for Services, Cisco IOS Release 12.2(4)B feature module
For information on configuring SSD and SESM, see the following documents:
•
Cisco Subscriber Edge Services Manager and Subscriber Policy Engine Installation and Configuration Guide
•
Cisco Service Selection Dashboard Installation and Configuration Guide
•
Cisco Service Selection Dashboard Web Developer Guide
Supported Platforms
•
Cisco 6400 series
•
Cisco 7200 series
•
Cisco 7401 ASR
Availability of Cisco IOS Software Images
Platform support for particular Cisco IOS software releases is dependent on the availability of the software images for those platforms. Software images for some platforms may be deferred, delayed, or changed without prior notice. For updated information about platform support and availability of software images for each Cisco IOS software release, refer to the online release notes or Cisco Feature Navigator.
Supported Standards, MIBs, and RFCs
Standards
No new or modified standards are supported by this feature.
MIBs
No new or modified MIBs are supported by this feature.
To obtain lists of supported MIBs by platform and Cisco IOS release, and to download MIB modules, go to the Cisco MIB website on Cisco.com at the following URL:
http://www.cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml
RFCs
No new or modified RFCs are supported by this feature.
Prerequisites
The tasks in this document assume that you have configured SSG.
Configuration Tasks
See the following sections for configuration tasks for the SSG Open Garden feature. Each task in the list is identified as either required or optional.
•
Configuring an Open Garden (required)
•
Verifying the Open Garden Configuration (optional)
Configuring an Open Garden
To configure an open garden, use the following commands beginning in global configuration mode:
Step 1
Router(config)# local-profile profile-name
Creates a local service profile and enters profile configuration mode.
Step 2
Router(config-prof)# attribute 26 9 251 "Rip-address;subnet-mask"
(Repeat step as necessary.)
(Service Route attribute) Specifies the network available to the service. You can add multiple networks to an open garden service.
Step 3
Router(config-prof)# attribute 26 9 251 "Dip-address"
(DNS Server Address attribute) Specifies the DNS server for the service.
Note
Enter this command twice to specify two DNS servers for DNS fault tolerance. SSG will send DNS requests to the first DNS server in its list. If the first server does not respond to the requests, SSG will send the requests to the second DNS server.
Step 4
Router(config-prof)# attribute 26 9 251 "Odomain-name"
(Repeat step as necessary.)
(Domain Name attribute) Specifies the domain name that gets DNS resolution from the DNS server specified in Step 3. You can add multiple domain names to an open garden service.
Step 5
Router(config-prof)# exit
Returns to global configuration mode.
Step 6
Router(config)# ssg open-garden profile-name
Designates the service as an open garden service.
Step 7
Router(config)# ssg bind service service {ip-address | ATM atm-interface | Async async-interface | BVI bvi-interface | Dialer dialer-interface | Ethernet ethernet-interface | FastEthernet fastethernet-interface | Group-Async group-async-interface | Lex lex-interface | Loopback loopback-interface | Multilink multilink-interface | Null null-interface | Port-channel port-channel-interface | Tunnel tunnel-interface | Virtual-Access virtual-access-interface | Virtual-Template virtual-template-interface | Virtual-TokenRing virtual-tokenring-interface}
Specifies the interface for a service.
Note
This step is required only if the open garden is routed through a next-hop gateway.
Note
Routes to the open garden network must be added to the routing table.
Verifying the Open Garden Configuration
Step 1
Use the show ssg open-garden privileged EXEC command to list all configured open garden services:
Router# show ssg open-gardennrp1-nrp2_og1nrp1-nrp2_og2nrp1-nrp2_og3nrp1-nrp2_og4Step 2
Use the show ssg service command to display detailed information for one of the open garden services:
Router# show ssg service nrp1-nrp2_og110------------------------ ServiceInfo Content -----------------------Uplink IDB: gw:0.0.0.0Name:nrp1-nrp2_og110Type:PASS-THROUGHMode:CONCURRENTService Session Timeout:0 secondsService Idle Timeout:0 secondsAuthentication Type:CHAPDNS Server(s):Primary:10.13.1.5Included Network Segments:10.1.1.0/255.255.255.0Excluded Network Segments:ConnectionCount 0Full User Name not usedDomain List:opengarden110.com;------------------------ End of ServiceInfo Content ----------------
Monitoring and Maintaining Open Garden
To monitor and maintain open garden services, use the following commands in privileged EXEC mode:
Configuration Example
This section provides the following configuration example:
SSG Open Garden Example
In the following example, two services, called "og1" and "og2", are defined and added to the open garden.
!ssg open-garden og1ssg open-garden og2!local-profile og1attribute 26 9 251 "Oopengarden1.com"attribute 26 9 251 "D10.13.1.5"attribute 26 9 251 "R10.1.1.0;255.255.255.0"local-profile og2attribute 26 9 251 "Oopengarden2.com"attribute 26 9 251 "D10.14.1.5"attribute 26 9 251 "R10.2.1.0;255.255.255.0"attribute 26 9 251 "R10.3.1.0;255.255.255.0"!ssg bind service og2 10.5.5.1Command Reference
This section documents modified commands. All other commands used with this feature are documented in the Service Selection Gateway feature module for Cisco IOS Release 12.2(4)B or the Cisco IOS Release12.2 command reference publications.
clear ssg open-garden
To remove open garden configurations and all open garden service objects, use the clear ssg open-garden command in privileged EXEC mode.
clear ssg open-garden
Syntax Description
This command has no keywords or arguments.
Defaults
No default behavior or values.
Command Modes
Privileged EXEC
Command History
12.1(5)DC
This command was introduced on the Cisco 6400 series node route processor.
12.2(4)B
This command was integrated into Cisco IOS Release 12.2(4)B.
Usage Guidelines
This command removes the open garden configuration by deleting all instances of the ssg open-garden global configuration command. This command also removes the service object of all the open garden services. The local service profiles of the open garden services are not deleted from the configuration.
Examples
In the following example, all open garden services are displayed and then removed:
Router# show ssg open-gardennrp1-nrp2_og1nrp1-nrp2_og2nrp1-nrp2_og3nrp1-nrp2_og4Router# clear ssg open-garden
Router# show ssg open-gardenRouter#Related Commands
Configures a local service profile.
Displays a list of all configured open garden services.
Designates a service, defined in a local service profile, as an open garden service.
local-profile
To configure a local service profile and enter profile configuration mode, use the local-profile command in global configuration mode. To delete the local service profile, use the no form of this command.
local-profile profile-name
no local-profile profile-name
Syntax Description
Defaults
No default behavior or values.
Command Modes
Global configuration
Command History
12.0(3)DC
This command was introduced on the Cisco 6400 series node route processor.
12.2(4)B
This command was integrated into Cisco IOS Release 12.2(4)B.
Usage Guidelines
Use this command to configure local service profiles.
Examples
The following example shows how to configure a RADIUS profile called fictitiousname.com and enter profile configuration mode:
Router(config)# local-profile fictitiousname.comRouter(config-prof)#Related Commands
show ssg open-garden
To display a list of all configured open garden services, use the show ssg open-garden command in privileged EXEC mode.
show ssg open-garden
Syntax Description
This command has no keywords or arguments.
Command Modes
Privileged EXEC
Command History
12.1(5)DC
This command was introduced on the Cisco 6400 series node route processor.
12.2(4)B
This command was integrated into Cisco IOS Release 12.2(4)B.
Examples
In the following example, all configured open garden services are displayed:
Router# show ssg open-gardennrp1-nrp2_og1nrp1-nrp2_og2nrp1-nrp2_og3nrp1-nrp2_og4Related Commands
ssg open-garden
To designate a service as an open garden service, use the ssg open-garden command in global configuration mode. To remove a service from the open garden, use the no form of this command.
ssg open-garden profile-name
no ssg open-garden profile-name
Syntax Description
Defaults
No default behavior or values.
Command Modes
Global configuration
Command History
12.1(5)DC
This command was introduced on the Cisco 6400 series node route processor.
12.2(4)B
This command was integrated into Cisco IOS Release 12.2(4)B.
Usage Guidelines
Use this command to designate a service, defined in a local service profile, as an open garden service.
Examples
In the following example, the service called "fictitiousname.com" is defined in a local service profile and added to the open garden:
Router(config)# local-profile cisco.comRouter(config-prof)# attribute 26 9 251 "Oopengarden1.com"Router(config-prof)# attribute 26 9 251 "D10.13.1.5"Router(config-prof)# attribute 26 9 251 "R10.1.1.0;255.255.255.0"Router(config-prof)# exitRouter(config)# ssg open-garden fictitiousname.comRelated Commands
Glossary
DHCP—Dynamic Host Configuration Protocol. Protocol that provides a mechanism for allocating IP addresses dynamically so that addresses can be reused when hosts no longer need them.
DNS—Domain Name Server. The part of the distributed database system used for resolving a fully qualified domain name into the four-part IP number used to route communications across the Internet.
open garden—Collection of websites or networks that users can access without having to provide authentication information.
RADIUS—Remote Authentication Dial-In User Service. A client/server security protocol. Security information is stored in a central location, known as the RADIUS server.
SESM—Subscriber Edge Services Manager. Successor product to the Cisco SSD. The SESM is part of a Cisco solution that allows subscribers of digital subscriber line (DSL), cable, wireless, and dial-up to simultaneously access multiple services provided by different Internet service providers, application service providers, and Corporate Access Servers.
SNMP—Simple Network Management Protocol. Network management protocol used almost exclusively in TCP/IP networks. SNMP provides a means to monitor and control network devices and to manage configurations, statistics collection, performance, and security.
SSD—Service Selection Dashboard. The SSD server is a customizable web-based application that works with the Cisco SSG to allow end customers to log in to and disconnect from proxy and pass-through services through a standard web browser. After the customer logs in to the service provider's network, an HTML dashboard is populated with the services authorized for that user.
SSG—Service Selection Gateway.
VPDN—virtual private dial-up network. A VPDN is a network that extends remote access to a private network using a shared infrastructure. VPDNs use Layer 2 tunnel technologies to extend the Layer 2 and higher parts of the network connection from a remote user across an Internet service provider (ISP) network to a private network.
walled garden—Collection of websites or networks that users can access after providing minimal authentication information.

 Feedback
Feedback