PB661245
This product bulletin introduces Cisco IOS® Software Release 12.2(50)SY and includes the following sections:
• Cisco IOS Software Release 12.2(50)SY Introduction
• Packaging
• Hardware
• Service Module Support
• New Features
• Additional Information
• Support
Cisco IOS Software Release 12.2(50)SY Introduction
• http://www.cisco.com/en/US/products/ps6017/tsd_products_support_series_home.html
• http://tools.cisco.com/ITDIT/CFN/jsp/index.jsp
Packaging
Figure 1. Cisco IOS feature set map starting from 12.2(50)SY

Hardware
• Cisco Catalyst 6500 Series Supervisor Engine 2T
Figure 2. Cisco Catalyst 6500 Supervisor Engine 2T

• 6900 Series Ethernet Interface Module for Cisco Catalyst 6500 Series Switches
Figure 3. 6900 Series 8-Port 10 Gigabit Ethernet Fiber Module

• http://www.cisco.com/en/US/products/hw/switches/ps708/prod_bulletins_list.html.
• 6800 Series Ethernet Interface Module for Cisco Catalyst 6500 Series Switches
• http://www.cisco.com/en/US/products/hw/switches/ps708/prod_bulletins_list.html.
Service Module Support
Table 1. Supported Service Modules
• http://www.cisco.com/go/packaging
New Features
Table 2. New Features and Enhancements
Application Performance
• Flexible Netflow: Flexible NetFlow is the next-generation in flow technology. It allows optimization of the network infrastructure, reducing operation costs, improved capacity planning and security incident detection with increased NetFlow flexibility and scalability beyond other flow based technologies available today. Flexible NetFlow advantages include:
– Flexibility, scalability, and customization of flow data
– The ability to monitor a wider range of packet information
– Enhanced network anomaly and security detection
– User configurable flow information to perform customized traffic identification and the ability to focus and monitor specific network behavior
– Convergence of multiple accounting technologies into one accounting mechanism
– Multiple configurable flow caches
Flexible Netflow in 12.2(50)SY takes advantage of the increased Netflow table of Sup2T as well as the improved hash efficiency. The system is able to monitor up to 13 million flows on a 13 slots chassis. Flexible netflow on Supervisor Engine 2T enables application visibility per flow.
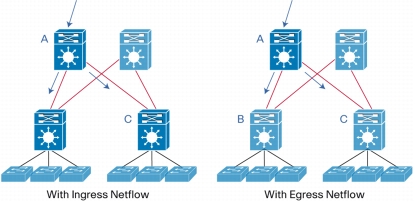
• Egress Netflow: Traditionally netflow could only be applied at the ingress. Supervisor Engine 2T gives more flexibility to the user and allows monitoring flow at the egress as well as the ingress interfaces. In Figure 4, if the user wants to monitor traffic going to B and C with ingress netflow, he has to configure the feature on 2 interfaces on 2 different systems (B and C). With egress netflow, he only needs to configure on it on 1 system (A). This simplifies management as well as network operations cost. Egress netflow also allows the user to monitor each multicast flow egressing the system, so the user gets a deeper visibility of the network multicast traffic.
Figure 4. Ingress Netflow points of management compared to Egress Netflow
• Sampled Netflow: The Supervisor Engine 2T for the Cisco Catalyst 6500 Series Switch supports the ability to perform Netflow sampling in the hardware. Prior to the introduction of the Supervisor Engine 2T, all PFC3-based supervisor engines for the Cisco Catalyst 6500 Series Switch performed Netflow sampling in the software, without preventing population of the Netflow Table. The most common use case to use sampling is in an environment where the number of flows far exceeds the number of Netflow Entries supported by the system. In such a case, sampling gives a better representation of the overall traffic.
• CPU friendly NDE export: Netflow export is a very CPU intensive application. Controlling CPU utilization is key to protect against undesirable side effects on the network. This helps ensure that the NDE process will not affect other functions, such as the processing of Layer 2 protocols, Layer 3 protocols, or other system management processes. This new feature introduced on Supervisor Engine 2T allows a user to control the CPU utilized by the Netflow Data Export process when Netflow records are being exported to a collector. Netflow statistics collection is performed in the hardware, with no effect on forwarding performance.
• Netflow on Control Plane interface: Properly configuring control plane policing is very important to ensure scalability with stability of the system. Using Flexible Netflow (FNF), the user can monitor control-plane traffic on a per flow basis to develop realistic traffic rates which can then be used in developing custom control-plane service-policies. Flexible Netflow provides granular traffic classification and allows for policies which target specific traffic flows without affecting other legitimate control-plane traffic.
• QoS Distributed Policer: Supervisor Engine 2T based systems support an optional distributed policing capability where multiple forwarding engines can communicate and synchronize the amount of traffic transmitted for a specific policer. The Supervisor Engine 2T supports up to 16,384 (16K) total policers; 4096 (4K) of these can be distributed policers. The distributed policing functionality provides a significant benefit for a Cisco Catalyst 6500 with multiple DFCs installed. The distributed policing functionality reduces if not eliminates the need for the software-based policing associated with the non-distributed implementation. The distributed policing functionality is an optional feature and can be enabled using a global command.
• Monitoring with third party applications: Supervisor Engine 2T supports the mini protocol analyzer. With this feature, the user can capture traffic in hardware and send it to the control plane for analysis. The command line interface allows for deep packet inspection, or alternatively the user can decide to export the captured buffer to a pcap file for off the box analysis with a network analyzer like Wireshark.
Security and Identity
• Authenticated networking infrastructure with 802.1X: 12.2(50)SY implements the full 802.1X security features set, so users and device can be authenticated in the Cisco TrustSec domain.
• Secure communication with MACSec Encryption: 12.2(50)SY enables MACSec hardware encryption on all the new 69XX line cards as well as on the Supervisor Engine 2T. Communication on each link between devices in the domain can be secured with a combination of encryption, message integrity checks, and data-path replay protection mechanisms.
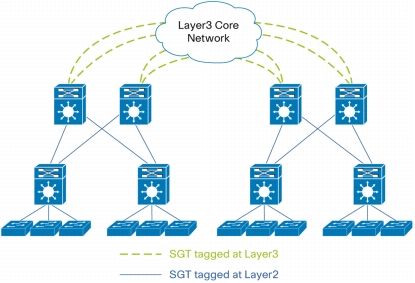
• Ingress Security Group Tagging: Access policies within the Cisco TrustSec domain are topology-independent, based on the roles (as indicated by security group number) of source and destination devices rather than on network addresses. Supervisor Engine 2T introduces hardware-based SGT imposition so individual packets are tagged in hardware with the security group number of the source. 12.2(50)SY and Supervisor Engine 2T not only tag the packets at Layer 2 but can also do it at Layer 3. This functionality allows to easy propagation of SGT tagged traffic on top of an existing Layer 3 infrastructure. The migration to Cisco TrustSec gets simplified.
• Egress Security Group Enforcement: At the egress point of the Cisco TrustSec domain, an egress Supervisor Engine 2T uses the source SGT and the security group number of the destination entity (the destination SG, or DGT) to determine which access policy to apply from the SGACL policy matrix.
Figure 5. Layer 3 SGT tagging and forwarding to pass SGT over a heterogeneous Layer 3 network.
• Cisco TrustSec Reflector: This feature allows the user to plug non Cisco TrustSec capable line cards in a 6500 chassis with Supervisor Engine 2T. The traffic ingressing and egressing from those line cards will be reflected to the supervisor so it can add or remove the SGT tag to ingressing and egressing traffic.
• SXP Support: Network devices not supporting SGT imposition in hardware use SXP to exchange the SGT/IP binding. 12.2(50)SY provides SXP support to Supervisor Engine 2T, allowing the user to interconnect with such devices.
• Layer 3 ACL Dry Run: Configuring large ACLs can be quite a tedious task. ACLs that do not fit in the hardware resources could cause software forwarding and possible high CPU utilization. This new feature allows the user to verify if the ACL changes will fit within the hardware resources before applying it. By doing so, the user can change its ACLs configuration without risking side effects on the control plane of its device.
• ACL Hitless Atomic Update: This new feature makes sure that the production traffic is not affected by ACL modification. The traffic will use the new ACL only when this one is fully programmed in hardware. It also avoids unanticipated network disruption by allowing the update of multiple features at once (IPv4, IPv6, RACL, VACL, and so on).
• New ACL Classification Options: 12.2(50)SY adds more granularity to ACL definitions by offering to classify the traffic based on new options such as dscp, fragments, IP options, time-range, ttl, and so on.
Embedded Management
• Connectivity Management Processor (CMP)
1. Users can access the console remotely (SSH/telnet) without a terminal server for troubleshooting and recovery (even when the route processor is not responsive).
2. Users are able to quickly recover image via TFTP/USB remotely without terminal server or on-site personnel requirements.
3. Users are able to reset the Supervisor Engine 2T remotely without any external power management devices.
4. In a situation where the primary console is unresponsive or the Cisco IOS Software image is unresponsive and the Cisco IOS Software image on compact flash is corrupted, the CMP provides the ability to access the switch logs, in order to determine the possible causes.
• Embedded Event Manager (EEM) 3.0
• Control Plane Policing (CoPP)
IP Services
• IP NAT - Static Mapping of a Port Range: The Cisco Catalyst 6500 performs NAT in hardware with high throughput. In this software release, one IP NAT improvement is the ability to configure a static ip NAT mapping and indicate a range of contiguous ports. Previously only one specific port was permitted in a static NAT.
• WCCP improvements: Supervisor Engine 2T has new hardware and software capabilities that improve WCCP operations. These improvements include Egress Netflow Support, Egress ACL rewrite, and WCCP GRE Decapsulation hardware support. Egress NetFlow can be used for egress WCCP features when NetFlow is needed. Ingress WCCP uses Ingress NetFlow entry and the Egress WCCP feature uses Egress NetFlow entry whenever a NetFlow entry is required for hardware packet redirection. WCCP GRE return packet processing is also implemented in hardware.
• VRF aware WCCP: The WCCP VRF Support feature enhances the existing WCCPv2 protocol by implementing support for Virtual Routing and Forwarding (VRF). The WCCP VRF Support feature allows service groups to be configured on a per VRF basis in addition to those defined globally.
IP Multicast
Table 3. Multicast Enhancements for Supervisor Engine 2T in 12.2(50)SY
IPv6
• http://www.cisco.com/en/US/partner/solutions/ns340/ns414/ns742/ns815/landing_cIPv6.html
Figure 6. Network Placement Where New IPv6 Features for First Hop Security and IPv6 uRPF Apply
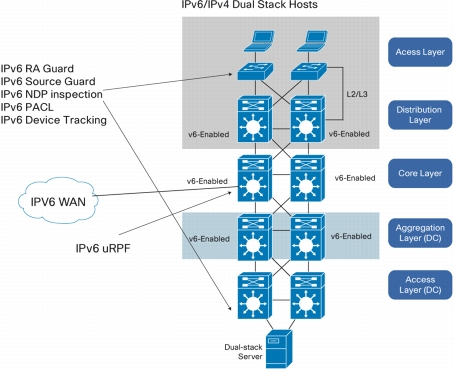
• IPv6 Unicast Reverse-Path Forwarding (uRPF): IPv6 uRPF is a security feature that checks to see if traffic is spoofed. The IPv6 uRPF feature checks to see if any packet received at a router interface arrives on one of the best return paths to the source of the packet. If URPF does not find a reverse path for the packet, uRPF can drop or forward the packet, depending on whether an access control list (ACL) is specified in the ipv6 verify unicast source reachable-via command. In this software release, uRPF increases from 6 to 16 paths for both IPv4 and IPv6.
For more information on uRPF, read:
– http://www.cisco.com/web/about/security/intelligence/unicast-rpf.html
• IPv6 Neighbor Discovery Protocol Inspection (NDP Inspection): IPv6 Neighbor Discovery Protocol Inspection (NDP Inspection) prevents spoofing attacks due to NDP vulnerabilities. IPv6 NDP Inspection learns and secures bindings for stateless auto configuration addresses in the Layer 2 Neighbor Cache.
NDP inspection can verify the signature of ND message containing CGA (Cryptographically Generated Address) IPv6 address. If the verification fails, then it drops the NDP messages.
• IPv6 Device Tracking: The tracking command in NDP inspection policy configuration mode overrides the default tracking policy set by the ipv6 neighbor tracking command on the port on which this policy applies. This function is useful on trusted ports where, for example, one may not want to track entries but wants an entry to stay in the binding table to prevent it from being stolen. The switch probes secure nodes at regular intervals by sending unicast Neighbor Solicitation messages with source ip address as unspecified address. The Active Node responds with a neighbor advertisement.
A Failure to receive response results in removing node's entry from neighbor cache and its access privileges are revoked by the guard features.
For more information on Neighbor Discovery, read:
– http://www.cisco.com/en/US/prod/collateral/iosswrel/ps6537/ps6553/white_paper_c11-563156.html
– http://www.cisco.com/en/US/docs/ios/ipv6/configuration/guide/ip6-addrg_bsc_con.html#wp1282543
For more information on IPv6 First Hop Security, read:
– http://www.cisco.com/en/US/prod/collateral/iosswrel/ps6537/ps6553/whitepaper_c11-602135.html
• IPv6 RA-Guard Host Mode: IPv6 RA-Guard protects from Rogue RA generated maliciously or unintentionally. The content of the RA message is inspected and the decision of dropping it can be based on almost all RA fields including prefixes. This sometimes happens due to unauthorized or improperly configured IPv6 hosts when operating IPv6 in a shared Layer 2 network environment.
For more information visit:
– http://www.cisco.com/en/US/partner/docs/solutions/Enterprise/Campus/CampIPv6.html
– http://www.cisco.com/en/US/docs/ios/ipv6/configuration/guide/ip6-first_hop_security.html
• IPv6 Port-Based Access Control List (IPv6 PACL) Support: Port-based access control list (PACL) provides a mechanism to filter incoming packets based on Layer 2 through 4 parameters at Layer 2 port level for IPv6 traffic. This feature increases the level of security available to the Cisco Catalyst 6500 when IPv6 is configured.
IPv6 PACLs function the same way as IPv4 PACLs except that they apply to IPv6 traffic.
EtherChannels also behave the same way as with IPv4 PACLs.
• IPv4 and IPv6 support for RFC 4292 (IP Forwarding Table MIB) and RFC 4293 (MIB for the Internet Protocol)
• IPv6 statistics and counters: Supervisor Engine 2T has new hardware functionality to support separate ingress and egress statistics for IPv6 traffic. Supervisor Engine 2T allows for the accounting of traffic for IPv4, IPv6, and MPLS traffic separately which gives more visibility to the network management. Supervisor Engine 720 only supported egress statistics for IPv6 traffic. With this new Supervisor Engine 2T functionality, RFC 4292 and RFC 4293 can be supported with both ingress and egress statistics.
• IPv6 Cisco Networking Services (CNS) Agents: IPv6 addressing is supported with Cisco Networking Services (CNS). CNS is a foundation technology for linking users to networking services and provides the infrastructure for the automated configuration of large numbers of network devices. When standard configurations do not exist or have been modified, the time involved in initial installation and subsequent upgrading is considerable.
• IPv6 Config Logger: IPv6 Configuration Logger is used to monitor who is making changes to the network. IPv6 support for Config Logger is now available. Configuration logger tracks and reports configuration changes. Config logger supports two content types:
– Plain text - With plain-text format, the config logger reports configuration changes only.
– XML - The config logger uses Extensible Markup Language (XML) to report the configuration change details (for example, what changed, who changed it, when changes were made, parser return code (PRC) values, and incremental NVGEN results).
• HTTP(S) IPv6 Support: This feature enhances the HTTP(S) client and server to support IPv6 addresses. The HTTP server in Cisco IOS Software can service requests from both IPv6 and IPv4 HTTP clients. The HTTP client in Cisco IOS Software supports sending requests to both IPv4 and IPv6 HTTP servers.
• IP SLAs for IPv6: Cisco IOS Software IP Service Level Agreements (SLAs) are a portfolio of technology embedded in Cisco IOS Software that allows Cisco customers to analyze IPv6 service levels for IPv6 applications and services, to increase productivity, to lower operational costs, and to reduce the frequency of network outages. IP SLAs uses active traffic monitoring - the generation of traffic in a continuous, reliable, and predictable manner - for measuring network performance. IP SLAs can be used to proactively monitor VoIP quality levels in your network, allowing you to guarantee VoIP quality levels to your users in IPv4 or IPv6 networks.
• IPv6 NETCONF: The Network Configuration Protocol (NETCONF) defines a mechanism through which a network device can be managed, configuration data information can be retrieved, and new configuration data can be uploaded and manipulated. NETCONF uses XML-based data encoding for the configuration data and protocol messages.
For more information about NETCONF, see "Network Configuration Protocol" in the Cisco IOS Software Network Management Configuration Guide:
– http://www.cisco.com/en/US/docs/ios/netmgmt/configuration/guide/nm_cns_netconf.html
• IPv6 SOAP Message Format: IPv6 Service-Oriented Access Protocol (SOAP) protocol provides a way to format the layout of Cisco Networking Services (CNS) messages in a consistent manner. SOAP uses XML technologies to define an extensible messaging framework that provides a message format that can be exchanged over a variety of underlying protocols.
For more information about Cisco Networking Services see the Cisco IOS Software Network Management Configuration Guide:
– http://www.cisco.com/en/US/docs/ios/netmgmt/configuration/guide/nm_cns_services.html
• IPv6 TCL: Tool command language (TCL) is used in Cisco IOS Software IPv6 to support features such as embedded event manager (EEM).
Network Virtualization
• MPLS Throughput: One of the improvements is increased MPLS packet throughput because the software support packets with up to 5 MPLS labels before recirculation is required. This functionality doubles the MPLS throughput with this software release.
• MPLS Management: Management of MPLS is easier with this software release because MPLS per interface, per protocol, and aggregate label statistics are also supported now.
VPLS support on the Cisco Catalyst 6500 with Supervisor Engine 2T is now native. Previously, VPLS support was only through SPA Interface Processor (SIP) WAN line card. With this software release, VPLS is supported on LAN line cards.
• Bridge Domain Logical Interface (BD/LIF): This is an infrastructure improvement which allows multiple functionalities. We can support 4096 VLANS and with the new Bridge Domain concept, we can support 16,384 internal bridge domains. There are several features that can use this improvements including VLAN reuse. Where VLANs were a shared resource before between VRFs, with Supervisor Engine 2T, we can scale VRFs and VLANS to 16,000 total. For example, we can have 4 VRFs with 4,000 VLANS each. Or have 8 VRFs with 2,000 VLANS each. With previous deployments prior to Supervisor Engine 2T, the limitation was 4,000 VLANs shared among all VRFs total. Other features, not just MPLS benefit from BD/LIF. Others technologies such as multicast for egress mVPN are enabled by BD/LIF and the new mFIB uses BD/LIF.
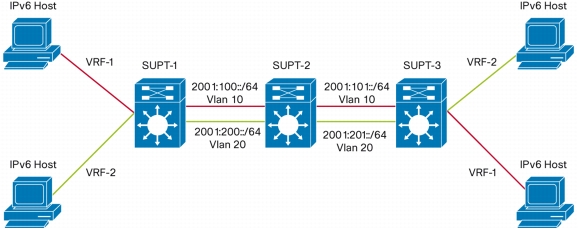
• VLAN Re-use: VRF-Lite deployments are now easier due to VLAN Re-use capabilities. This is where the same VLAN number can be used on subinterfaces under the same primary interface. Before this functionality, VRF-Lite scalability was limited due to the need for different VLAN between sub-interface which complicated deployment. (See Figure 8.)
Figure 7. VLAN Reuse Example Where Same VLAN Number Can Be Used on Different Interfaces from Same Switch Using VRF-Lite; IPv4 and IPv6 Supported
• MPLS Pseudowire Status Signaling: The MPLS Pseudowire Status Signaling feature enables you to configure the router so it can send pseudowire status to a peer router, even when the attachment circuit is down. This feature can be used to prevent blackholing of traffic because of a circuit down at the remote end.
For more information, see:
– http://www.cisco.com/en/US/docs/ios/mpls/configuration/guide/mp_pw_status.html
• MPLS Traffic Engineering (TE) - Path Protection: The MPLS Traffic Engineering (TE): Path Protection feature provides an end-to-end failure recovery mechanism (that is, full path protection) for Multiprotocol Label Switching (MPLS) traffic engineering (TE) tunnels.
For more information on MPLS Traffic Engineering (TE) - Path Protection, see:
– http://www.cisco.com/en/US/docs/ios/mpls/configuration/guide/mp_te_path_prot.html
• Layer 2 over GRE (L2oGRE): Layer 2 over GRE is a new feature which allows Layer 2 and Layer 3 packets to be bridged over a GRE tunnel. This behavior is similar to Layer 2 Tunneling Protocol (L2TP) which is not currently supported natively in hardware on the Cisco Catalyst 6500.
• NSF/SSO - Any Transport over MPLS (AToM): The NSF/SSO - Any Transport over MPLS and AToM Graceful Restart feature allows Any Transport over MPLS (AToM) to use Cisco nonstop forwarding (NSF), stateful switchover (SSO), and Graceful Restart (GR) to allow a Route Processor (RP) to recover from a disruption in control plane service without losing its Multiprotocol Label Switching (MPLS) forwarding state.
NSF with SSO is effective at increasing availability of network services. Cisco NSF with SSO provides continuous packet forwarding, even during a network processor hardware or software failure. In a redundant system, the secondary processor recovers control plane service during a critical failure in the primary processor. SSO synchronizes the network state information between the primary and the secondary processor.
For more information, see:
– http://www.cisco.com/en/US/docs/ios/ios_xe/mpls/configuration/guide/mp_trnsprt_mlps_atom_xe.html
• VRF aware NTP: To configure the software clock to synchronize a peer or to be synchronized by a peer in a virtual private network (VPN) routing forwarding instance (VRF) for routing to the destination instead of to the global routing table.
• VRF support for TFTP server, TFTP Client, and FTP client: TFTP and FTP are now VRF aware in this software release. To use this feature, the source interface is specified and if the interface is in a VRF then the source of the TFTP or FTP will be from that VRF.
• VPLS: Supervisor Engine 2T supports VPLS natively in 12.2(50) SY release which is highly scalable with sub-second convergence. With a standards based approach, VPLS allows Campus LAN extensions and enables Remote DataCenter connectivity (DCI) using LAN extensions.
VPLS is a class of VPN that supports the connection of multiple sites in a single bridged domain over a managed IP or MPLS network. VPLS presents an Ethernet interface to customers, simplifying the LAN or WAN boundary for enterprise customers and enabling rapid and flexible service provisioning, because the service bandwidth is not tied to the physical interface. All services in a VPLS network appear to be on the same LAN, regardless of location (Figure 7).
VPLS uses edge routers that can learn, bridge, and replicate on a per-VPN basis. These routers are connected by a full mesh of tunnels, enabling any-to-any connectivity. VPLS operation emulates an IEEE Ethernet bridge.
Figure 8. DCI LAN Extension with VPLS
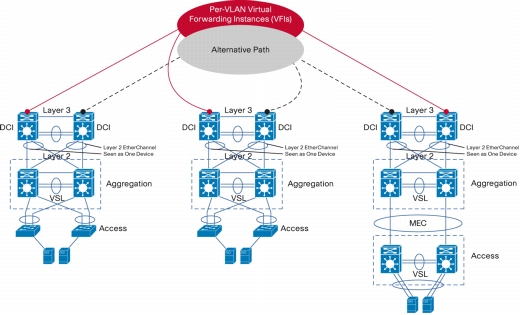
• H-VPLS: Hierarchical VPLS (H-VPLS) mode enables highly scalable bridging domains. Supervisor Engine 2T supports H-VPLS natively from 12.2(50)SY release. It also offers VLAN overlapping at the edge, which is a critical feature in multiple-tenant data centers.
Metro Technologies
• EVC Framework: 12.2(50)SY release significantly enhances the EVC services framework that comply with the MEF, IEEE and IETF standards. Features supported in this release include:
– MST on Bridge Domains
– Advance VLAN Translation and Service Mapping based on IEEE 802.1ah
– IEEE 802.1ad Provider Bridges support with BPDU Handling
– Point-to-point and multipoint EVC
• Ethernet OAM (E-OAM): 12.2(50)SY release supports a rich set of standards based Ethernet OAM (E-OAM) features on Sup2T
E-OAM facilitates deployment of Ethernet services over multiple access technologies and thereby provides service independence from access and transport. The features and standards supported include:
– IEEE 802.3ag: Connectivity Fault Management (CFM) for Untagged and QinQ, CFM with VLAN and CFM on EVC Bridge Domains
– ITU-T Y.1731: E-OAM functions and mechanisms
– IEEE 802.3ah support, AIS Interworking with 802.3ah
– MEF E-LMI: Ethernet Local Management Interface
– Cisco IP SLAs: Performance Management using IP, CFM and Y.1731 Mechanisms
Manageability
– ftp://ftp-sj.cisco.com/pub/mibs/supportlists/wsc6000/wsc6000-supportlist-ios.changes/
Table 4. 12.2(50)SY MIB Enhancements
Additional Information
• http://www.cisco.com/go/trustsec
• http://www.cisco.com/en/US/products/sw/iosswrel/products_ios_cisco_ios_software_category_home.html
• http://www.cisco.com/en/US/products/ps6017/tsd_products_support_series_home.html
• http://www/en/US/products/hw/switches/ps708/prod_bulletin0900aecd804f0694.html
• Download Cisco IOS Software releases and access software upgrade planners: http://www.cisco.com/cisco/software/navigator.html?a=a&i=rpm
• Determine the minimum supported software for platforms: http://tools.cisco.com/Support/Fusion/FusionHome.do
• A Web-based application that allows you to quickly match Cisco IOS Software releases, features, and hardware: http://tools.cisco.com/ITDIT/CFN/jsp/index.jsp
• View all major releases, all platforms, and all software features from a single interface: http://www.cisco.com/pcgi-bin/Software/Iosplanner/Planner-tool/iosplanner.cgi
• View the full Cisco's Catalyst Switching Portfolio in one document: http://www.cisco.com/en/US/prod/collateral/switches/ps5718/ps6406/CatalystPoster_Final.pdf
Product Management Contact
Support
• http://www.cisco.com/en/US/products/products_end-of-life_policy.html
Ordering Information
Table 5. Ordering Information
Cisco Services
For More Information