Feedback Feedback
|
Table Of Contents
Release Notes for Cisco Aironet Access Points for Cisco IOS Release 12.3(11)JA4
Finding the IOS Software Version
Upgrading to a New Software Release
Disable Radios to Prevent Unexpected Reboot When Upgrading System Software
CCKM and Fast Roaming on Cisco 7921/7925 IP Phones
Obtaining Documentation and Submitting a Service Request
Release Notes for Cisco Aironet Access Points for Cisco IOS Release 12.3(11)JA4
July 27, 2007
This release is a maintenance release and contains no new features. These release notes list open and resolved caveats for Cisco IOS Release 12.3(11)JA4.
Cisco IOS Release 12.3(11)JA4 supports autonomous 32 Mb platforms. 16 Mb platforms and platforms supported by Cisco IOS Release 12.3(8)JA and earlier (350, 1100, 1130, 1200, and 1230 series access points and 1300 series access point/bridge) are supported by Cisco IOS Release 12.3(8)JEA1.
Contents
These release notes contain the following sections:
•
Obtaining Documentation and Submitting a Service Request
Introduction
The Cisco Aironet Access Point is a wireless LAN transceiver that acts as the connection point between wireless and wired networks or as the center point of a standalone wireless network. In large installations, the roaming functionality provided by multiple access points enables wireless users to move freely throughout the facility while maintaining uninterrupted access to the network.
You can configure and monitor 1130, 1240, and the 1300 series outdoor access point/bridge using the command-line interface (CLI), the web-browser interface, or Simple Network Management Protocol (SNMP).
System Requirements
You can install Cisco IOS Release 12.3(11)JA4 on all 1130, 1240 series access points, and 1300 series outdoor access point/bridges.
Finding the IOS Software Version
To find the version of IOS software running on your access point, use a Telnet session to log into the access point and enter the show version EXEC command. This example shows command output from an access point running Cisco IOS Release 12.3(11)JA4:
ap1240AG>show versionCisco Internetwork Operating System SoftwareIOS (tm) C1240 Software (C1240-K9W7-M), Version 12.3(11)JA4Copyright (c) 1986-2006 by Cisco Systems, Inc.On access points running IOS software, you can also find the software version on the System Software Version page in the access point's web-browser interface. If your access point does not run IOS software, the software version appears at the top left of most pages in the web-browser interface.
Obtaining the Software Image
To obtain the Cisco IOS software for your access point, follow these instructions to reach the Cisco IOS Software Center on Cisco.com:
Step 1
Follow this link to the Cisco Software Center page:
http://www.cisco.com/cisco/software/navigator.html
Step 2
Scroll down to the Access Point section.
Step 3
Choose your access point from the displayed list. The access point introduction page appears.
Step 4
Click Download Software. The Software Download page appears.
Step 5
Click your highlighted access point and the software type page appears.
Note
You must register or be a registered user to obtain the software image. Follow the registration instructions.
Step 6
Click IOS Software and the software release page appears.
Step 7
Click 12.3(11)JA4 > Wireless LAN > Download and the Software License Agreement page appears.
Step 8
Read the agreement, click Agree, and enter your username and password on the Log In screen.
Step 9
Follow the prompts to save the software on your PC.
Upgrading to a New Software Release
For instructions on installing new software for your bridge:
Step 1
Follow this link to the Cisco Software Center page:
http://www.cisco.com/cisco/software/navigator.html
Step 2
Scroll down to the Access point section.
Step 3
Choose your access point from the displayed list. The Cisco Aironet 1400 Series Introduction page appears.
Step 4
Under the Configure section, click Configuration Guides. A list of configuration documents appears.
Step 5
Click Cisco IOS Software Configuration Guide for Cisco Aironet Access Points.
Step 6
Navigate to the Managing Firmware and Configurations chapter.
Disable Radios to Prevent Unexpected Reboot When Upgrading System Software
If your access point runs Cisco IOS Release 12.2(11)JA, 12.2(11)JA1, or 12.2(11)JA2, your access point might unexpectedly reboot after you upgrade to a later Cisco IOS Release. Because of a rare timing condition that affects the radios, the access point sometimes reboots immediately after the upgrade when the radios are enabled. However, after the access point reboots the upgrade is complete and the access point operates normally. To prevent the access point from rebooting unexpectedly, disable the radio interfaces before upgrading software.
Follow these steps to disable the radio interfaces using the web-browser interface:
Step 1
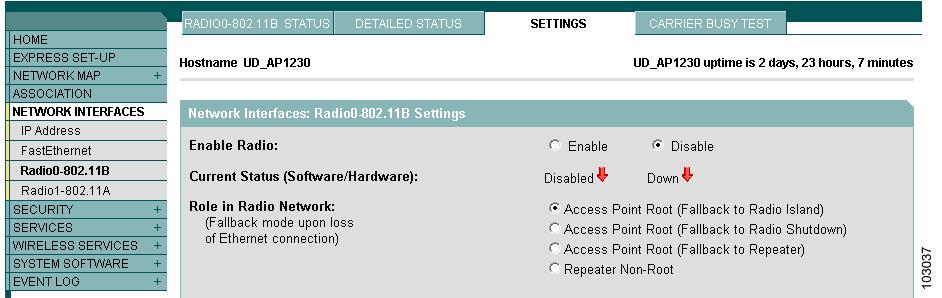
Browse to the Network Interfaces: Radio Settings page. Figure 1 shows the top portion of the Network Interfaces: Radio Settings page.
Figure 1 Network Interfaces: Radio Settings Page
Step 2
Select Disable to disable the radio.
Step 3
Click Apply at the bottom of the page.
Step 4
If your access point has two radios, repeat these steps for the second radio.
Beginning in privileged EXEC mode, follow these steps to disable the access point radios using the CLI:
If your access point has two radios, repeat these steps for the second radio. Use the no form of the shutdown command to enable the radio.
Important Information
CCKM and Fast Roaming on Cisco 7921/7925 IP Phones
When a 7921 or 7925 wireless associates to an access point in a WDS with CCKM, it cannot fast roam because call admission control is not enabled. To work around this issue you must enable admission control by issuing the admit-traffic command in the access point SSID configuration as shown in the following example:
dot11 ssid voice vlan 21 authentication open eap eap_methods authentication network-eap eap_methods authentication key-managemenet wpa cckm admit-trafficNew Features
No new features are introduced in Cisco IOS Release 12.3(11)JA4.
Caveats
This section lists open and resolved caveats for access points.
Open Caveats
These caveats are open in Cisco IOS Release 12.3(11)JA4:
•
CSCsd99125— WDS may report an incorrect new channel to WLSE after a RADAR event
During DFS event testing, it was discovered that if a DFS event was triggered on a non-root device, the WLSE sometimes received an erroneous new channel report.
•
CSCsd90308—Large default beacon size causes blue screen on Conexant Wi-Fi station
The very large default beacon size on the 802.11a band with 12.3(11)JA firmware is causing a Conexant ISL39200C with the Wi-Fi test bed driver to blue screen under Windows XP.
The 802.11a beacon size of with TKIP, AES, and WMM enabled is approximately 285 bytes, depending on the size of the SSID. This is an enormous jump in size since Cisco's last version of firmware due to the Country IE 7 and the Power Constraint IE now being advertised by default.
The Conexant radio seems to blue screen at 235 bytes and larger. Conexant has reproduced the problem.
•
CSCse49342—DHCP_SERVER_FAILURE observed in 1300 series in WGB mode
•
CSCse48137—Nested repeater does not work
A nested 1130 access point configured for open authentication and root mode station role fails to associate with a repeater and displays the following console message:
*Mar 1 00:01:34.822: %DOT11-4-CANT_ASSOC: Interface Dot11Radio1, cannot associate: No Response*Mar 1 00:02:17.603: %DOT11-6-DFS_SCAN_COMPLETE: DFS scan complete on frequency 5560 MHz*Mar 1 00:02:31.821: %DOT11-4-CANT_ASSOC: Interface Dot11Radio1, cannot associate: Rcvd response from 0014.6956.5cda channel 149 801•
CSCse36333—Workgroup bridge client fails to get a DHCP IP address when root link is configured for WPA v2 LEAP authentication
A root access point and workgroup bridge access point configured for WPAv2 LEAP authentication properly associate and authenticate, but the workgroup bridge client does not get an IP address from the DHCP server. The root access point does not show the workgroup bridge client details.
•
CSCse40389—Dot1x(LEAP) reauthentication occurs even though it is not enabled
A 3550 or 2950 switch continuously re-authenticates an access point on a specific interval though re-authentication is disabled on the switch side when the dot1x method is LEAP.
Continuous re-authentication does occur when the dot1x authentication method is FAST.
•
CSCse41589—Workgroup bridge fails to get a DHCP IP address after a successful EAP-FAST authentication to the root access point
The workgroup bridge is able to ping the root access point and wired host if BVI1 is assigned with a static IP address. Occasionally, the workgroup bridge is assigned a DHCP IP address after a long period of time (about 15 to 20 minutes).
The failure to obtain a DHCP IP address is not observed when the the workgroup bridge uses LEAP authentication.
•
CSCse42464—Access point fails to retrieve certificate from certificate authority server using GUI
Certificate is obtained correctly when using the CLI.
•
CSCse48448—Workgroup bridge non-native VLAN configuration blocks switch native VLAN port
The workgroup bridge are associated to the root access point but the switch port (VLAN1) is blocked by spanning-tree with the following error message:
3750Switch#3w2d: %SPANTREE-2-RECV_PVID_ERR: Received BPDU with inconsistent peer vlan id 2 on GigabitEthernet1/0/1 VLAN1.3w2d: %SPANTREE-2-BLOCK_PVID_LOCAL: Blocking GigabitEthernet1/0/1 on VLAN0001. Inconsistent local vlan.3750Switch#•
CSCse09744—SSID config page for NAC for MBSSID on the GUI does not have the ability to tie a VLAN name to the VLAN in the SSID configuration page
On the SSID page, the VLAN fields exists but no fields exist to link the VLAN name. To add a VLAN name associated with the VLAN requires navigating to the Services VLAN page.
Resolved Caveats
These caveats are resolved in Cisco IOS Release 12.3(11)JA4:
•
CSCse56501
A device running Cisco IOS software that has Internet Protocol version 6 (IPv6) enabled may be subject to a denial of service (DoS) attack. For the device to be affected by this vulnerability the device also has to have certain Internet Protocol version 4 (IPv4) User Datagram Protocol (UDP) services enabled. To exploit this vulnerability an offending IPv6 packet must be targeted to the device. Packets that are routed throughout the router can not trigger this vulnerability. Successful exploitation will prevent the interface from receiving any additional traffic. The only exception is Resource Reservation Protocol (RSVP) service, which if exploited, will cause the device to crash. Only the interface on which the vulnerability was exploited will be affected.
Cisco is providing fixed software to address this issue. There are workarounds available to mitigate the effects of the vulnerability.
This advisory is posted at http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20080326-IPv4IPv6.
•
CSCsj44081—Cisco IOS Software has been enhanced with the introduction of additional software checks to signal improper use of data structures. This feature has been introduced in select Cisco IOS Software releases published after April 5, 2007.
Details: The %DATACORRUPTION-1-DATAINCONSISTENCY error message is preceded by a timestamp: May 17 10:01:27.815 UTC: %DATACORRUPTION-1-DATAINCONSISTENCY: copy error. The error message is then followed by a traceback.
If You Need More Information
If you need information about a specific caveat that does not appear in these release notes, you can use the Cisco Bug Toolkit to find select caveats of any severity. Click this URL to browse to the Bug Toolkit:
http://tools.cisco.com/Support/BugToolKit/
(If you request a defect that cannot be displayed, the defect number might not exist, the defect might not yet have a customer-visible description, or the defect might be marked Cisco Confidential.)
Documentation Updates
No documentation updates are introduced in Cisco IOS Release 12.3(11)JA4.
Related Documentation
This section lists documents related to Cisco IOS Release 12.3(11)JA4 and to 1130AG, 1240AG series access points, and 1300 series outdoor access point/bridges.
•
Quick Start Guide: Cisco Aironet 1130AG Series Access Points
•
Quick Start Guide: Cisco Aironet 1240AG Series Access Points
•
Quick Start Guide: Cisco Aironet 1300 Series Outdoor Access Point/Bridge
•
Cisco IOS Software Configuration Guide for Cisco Aironet Access Points
•
Cisco IOS Command Reference for Cisco Aironet Access Points and Bridges
•
Cisco Aironet 1130AG Series Access Point Hardware Installation Guide
•
Cisco Aironet 1240AG Series Access Point Hardware Installation Guide
•
Cisco Aironet 1300 Series Outdoor Access Point/Bridge Hardware Installation Guide
•
Installation Instructions for Cisco Aironet Power Injectors
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information, see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What's New in Cisco Product Documentation as an RSS feed and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free service. Cisco currently supports RSS Version 2.0.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
© 2007 Cisco Systems, Inc. All rights reserved.