-
Cisco MDS 9000 Family NX-OS System Management Configuration Guide
-
Index
-
New and Changed Information
-
Preface
-
Overview
-
Using the CFS Infrastructure
-
Configuring System Message Logging
-
Configuring Call Home
-
Scheduling Maintenance Jobs
-
Monitoring System Processes and Log
-
Configuring the Embedded Event Manager
-
Configuring SNMP
-
Configuring RMON
-
Configuring Domain Parameters
-
Configuring Fabric Configuration Servers
-
Monitoring Network Traffic Using SPAN
-
Table Of Contents
Assigning SNMP Switch Contact and Location Information
SNMPv3 CLI User Management and AAA Integration
CLI and SNMP User Synchronization
About AES Encryption-Based Privacy
Configuring SNMP Users from the CLI
Enforcing SNMPv3 Message Encryption
Assigning SNMPv3 Users to Multiple Roles
Adding or Deleting Communities
SNMP Trap and Inform Notifications
Configuring SNMPv2c Notifications
Configuring SNMPv3 Notifications
Configuring the Notification Target User
Configuring LinkUp/LinkDown Notifications for Switches
Configuring Up/Down SNMP Link-State Traps for Interfaces
Scope of Link Up/Down Trap Settings
Configuring Entity (FRU) Traps
Displaying SNMP Security Information
Configuring SNMP
The CLI and SNMP use common roles in all switches in the Cisco MDS 9000 Family. You can use SNMP to modify a role that was created using the CLI and vice versa.
Users, passwords, and roles for all CLI and SNMP users are the same. A user configured through the CLI can access the switch using SNMP (for example, the Fabric Manager or the Device Manager) and vice versa.
This chapter includes the following sections:
•
SNMPv3 CLI User Management and AAA Integration
•
SNMP Trap and Inform Notifications
About SNMP Security
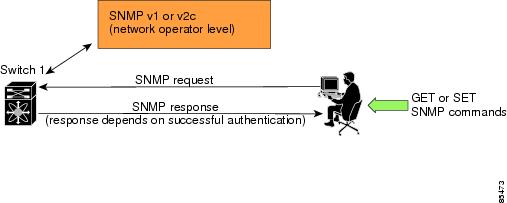
SNMP is an application layer protocol that facilitates the exchange of management information between network devices. In all Cisco MDS 9000 Family switches, three SNMP versions are available: SNMPv1, SNMPv2c, and SNMPv3 (see Figure 7-1).
Figure 7-1 SNMP Security
This section includes the following topics:
•
SNMP Version 1 and Version 2c
•
Assigning SNMP Switch Contact and Location Information
SNMP Version 1 and Version 2c
SNMP Version 1 (SNMPv1) and SNMP Version 2c (SNMPv2c) use a community string match for user authentication. Community strings provided a weak form of access control in earlier versions of SNMP. SNMPv3 provides much improved access control using strong authentication and should be preferred over SNMPv1 and SNMPv2c wherever it is supported.
SNMP Version 3
SNMP Version 3 (SNMPv3) is an interoperable standards-based protocol for network management. SNMPv3 provides secure access to devices by a combination of authenticating and encrypting frames over the network. The security features provided in SNMPv3 are:
•
Message integrity—Ensures that a packet has not been tampered with in-transit.
•
Authentication—Determines the message is from a valid source.
•
Encryption—Scrambles the packet contents to prevent it from being seen by unauthorized sources.
SNMPv3 provides for both security models and security levels. A security model is an authentication strategy that is set up for a user and the role in which the user resides. A security level is the permitted level of security within a security model. A combination of a security model and a security level determines which security mechanism is employed when handling an SNMP packet.
Assigning SNMP Switch Contact and Location Information
You can assign the switch contact information, which is limited to 32 characters (without spaces) and the switch location.
To configure contact and location information, follow these steps:
SNMPv3 CLI User Management and AAA Integration
The Cisco NX-OS software implements RFC 3414 and RFC 3415, including user-based security model (USM) and role-based access control. While SNMP and the CLI have common role management and share the same credentials and access privileges, the local user database was not synchronized in earlier releases.
SNMPv3 user management can be centralized at the AAA server level. This centralized user management allows the SNMP agent running on the Cisco MDS switch to leverage the user authentication service of the AAA server. Once user authentication is verified, the SNMP PDUs are processed further. The AAA server also is used to store user group names. SNMP uses the group names to apply the access/role policy that is locally available in the switch.
This section includes the following topics:
•
CLI and SNMP User Synchronization
CLI and SNMP User Synchronization
Any configuration changes made to the user group, role, or password results in database synchronization for both SNMP and AAA.
To create an SNMP or CLI user, use either the username or snmp-server user commands.
•
The auth passphrase specified in the snmp-server user command is synchronized as the password for the CLI user.
•
The password specified in the username command is synchronized as the auth and priv passphrases for the SNMP user.
Users are synchronized as follows:
•
Deleting a user using either command results in the user being deleted for both SNMP and the CLI.
•
User-role mapping changes are synchronized in SNMP and the CLI.
Note
When the passphrase/password is specified in localized key/encrypted format, the password is not synchronized.
•
Existing SNMP users continue to retain the auth and priv passphrases without any changes.
•
If the management station creates an SNMP user in the usmUserTable, the corresponding CLI user is created without any password (login is disabled) and will have the network-operator role.
Restricting Switch Access
You can restrict access to a Cisco MDS 9000 Family switch using IP Access Control Lists (IP-ACLs).
Group-Based SNMP Access
Note
Because group is a standard SNMP term used industry-wide, we refer to role(s) as group(s) in this SNMP section.
SNMP access rights are organized by groups. Each group in SNMP is similar to a role through the CLI. Each group is defined with three accesses: read access, write access, and notification access. Each access can be enabled or disabled within each group.
You can begin communicating with the agent once your user name is created, your roles are set up by your administrator, and you are added to the roles.
Creating and Modifying Users
You can create users or modify existing users using SNMP, Fabric Manager, or the CLI.
•
SNMP—Create a user as a clone of an existing user in the usmUserTable on the switch. Once you have created the user, change the cloned secret key before activating the user. Refer to RFC 2574.
•
Fabric Manager.
•
CLI—Create a user or modify an existing user using the snmp-server user command.
A network-operator and network-admin roles are available in a Cisco MDS 9000 Family switch. There is also a default-role if you want to use the GUI (Fabric Manager and Device Manager). You can also use any role that is configured in the Common Roles database.
Tip
All updates to the CLI security database and the SNMP user database are synchronized. You can use the SNMP password to log into either Fabric Manager or Device Manager. However, after you use the CLI password to log into Fabric Manager or Device Manager, you must use the CLI password for all future logins. If a user exists in both the SNMP database and the CLI database before upgrading to Cisco MDS SAN-OS Release 2.0(1b), then the set of roles assigned to the user becomes the union of both sets of roles after the upgrade.
This section includes the following topics:
•
About AES Encryption-Based Privacy
•
Configuring SNMP Users from the CLI
•
Enforcing SNMPv3 Message Encryption
•
Assigning SNMPv3 Users to Multiple Roles
•
Adding or Deleting Communities
About AES Encryption-Based Privacy
The Advanced Encryption Standard (AES) is the symmetric cipher algorithm. The Cisco NX-OS software uses AES as one of the privacy protocols for SNMP message encryption and conforms with RFC 3826.
The priv option offers a choice of DES or 128-bit AES encryption for SNMP security encryption. The priv option along with the aes-128 token indicates that this privacy password is for generating a 128-bit AES key. The AES priv password can have a minimum of eight characters. If the passphrases are specified in clear text, you can specify a maximum of 64 characters. If you use the localized key, you can specify a maximum of 130 characters.
Note
For an SNMPv3 operation using the external AAA server, user configurations in the external AAA server require AES to be the privacy protocol to use SNMP PDU encryption.
Configuring SNMP Users from the CLI
The passphrase specified in the snmp-server user command and the username command are synchronized.
To create or modify SNMP users from the CLI, follow these steps:
To create or modify passwords for SNMP users from the CLI, follow these steps:
CautionAvoid using the localizedkey option when configuring an SNMP user from the CLI. The localized keys are not portable across devices as they contain device engine ID information. If a configuration file is copied to the device, the passwords may not be set correctly if the configuration file was generated at a different device. Explicitly configure the desired passwords after copying the configuration into the device. Passwords specified with the localizedkey option are limited to 130 characters.
Note
The snmp-server user command takes the engineID as an additional parameter. The engineID creates the notification target user (see the "Configuring the Notification Target User" section). If the engineID is not specified, the local user is created.
Enforcing SNMPv3 Message Encryption
By default the SNMP agent allows the securityLevel parameters of authNoPriv and authPriv for the SNMPv3 messages that use user-configured SNMPv3 message encryption with auth and priv keys.
To enforce the message encryption for a user, follow these steps:
Alternatively, you can enforce the SNMPv3 message encryption globally on all the users using the following commands:
Assigning SNMPv3 Users to Multiple Roles
The SNMP server user configuration is enhanced to accommodate multiple roles (groups) for SNMPv3 users. After the initial SNMPv3 user creation, you can map additional roles for the user.
Note
Only users belonging to a network-admin role can assign roles to other users.
To configure multiple roles for SNMPv3 users from the CLI, follow these steps:
Adding or Deleting Communities
You can configure read-only or read-write access for SNMPv1 and SNMPv2 users. Refer to RFC 2576.
To create an SNMPv1 or SNMPv2c community, follow these steps:
SNMP Trap and Inform Notifications
You can configure the Cisco MDS switch to send notifications to SNMP managers when particular.
Note
You must enable the RMON traps in the SNMP configuration. For more information refer to Configuring RMON, page 8-2
Use the SNMP-TARGET-MIB to obtain more information on the destinations to which notifications are to be sent either as traps or as informs. Refer to the Cisco MDS 9000 Family MIB Quick Reference.
This section includes the following topics:
•
Configuring SNMPv2c Notifications
•
Configuring SNMPv3 Notifications
•
Configuring the Notification Target User
•
Configuring LinkUp/LinkDown Notifications for Switches
•
Configuring Up/Down SNMP Link-State Traps for Interfaces
•
Displaying SNMP Security Information
Tip
The SNMPv1 option is not available with the snmp-server host ip-address informs command.
Configuring SNMPv2c Notifications
To configure SNMPv2c notifications using IPv4, follow these steps:
To configure SNMPv2c notifications using IPv6, follow these steps:
Note
Switches can forward events (SNMP traps and informs) up to 10 destinations.
Configuring SNMPv3 Notifications
To configure SNMPv3 notifications using IPv4, follow these steps:
To configure SNMPv3 notifications using IPv6, follow these steps:
Enabling SNMP Notifications
Notifications (traps and informs) are system alerts that the switch generates when certain events occur. You can enable or disable notifications. By default, no notification is defined or issued. If a notification name is not specified, all notifications are disabled or enabled.
With the SNMP central infra feature, you can add the traps that need to be enabled or disabled. The MIB CISCO-NOTIFICATION-CONTROL-MIB is supported to enable the use of a MIB browser to control notification generation.
You can enable or disable the supported traps at the following levels:
•
Switch level—You can use snmp-server enable traps command to enable all the traps in the supported MIBs at the switch level.
•
Feature level—You can use snmp-server enable traps command with the feature name to enable traps at the feature level.
switch =>snmp-server enable traps callhome ?event-notify Callhome External Event Notificationsmtp-send-fail SMTP Message Send Fail notification•
Individual traps - You can use snmp-server enable traps command with the feature name to enable traps at the individual level.
switch =>snmp-server enable traps callhome event-notify ?Table 7-1 lists the CLI commands that enable the notifications for Cisco NX-OS MIBs.
Note
The snmp-server enable traps CLI command enables both traps and informs, depending on how you configured SNMP. See the notifications displayed with the snmp-server host CLI command.
The following notifications are enabled by default:
•
entity fru
•
license
•
link ietf-extended
All other notifications are disabled by default.
To enable individual notifications, follow these steps:
You can use the show snmp trap command to display all the notifications and their status.
switch# show snmp trap--------------------------------------------------------------------------------Trap type Enabled--------------------------------------------------------------------------------entity : entity_mib_change Yesentity : entity_module_status_change Yesentity : entity_power_status_change Yesentity : entity_module_inserted Yesentity : entity_module_removed Yesentity : entity_unrecognised_module Yesentity : entity_fan_status_change Yesentity : entity_power_out_change Yeslink : linkDown Yeslink : linkUp Yeslink : extended-linkDown Yeslink : extended-linkUp Yeslink : cieLinkDown Yeslink : cieLinkUp Yeslink : connUnitPortStatusChange Yeslink : fcTrunkIfUpNotify Yeslink : fcTrunkIfDownNotify Yeslink : delayed-link-state-change Yeslink : fcot-inserted Yeslink : fcot-removed Yescallhome : event-notify Nocallhome : smtp-send-fail Nocfs : state-change-notif Nocfs : merge-failure Nofcdomain : dmNewPrincipalSwitchNotify Nofcdomain : dmDomainIdNotAssignedNotify Nofcdomain : dmFabricChangeNotify Norf : redundancy_framework Yesaaa : server-state-change Nolicense : notify-license-expiry Yeslicense : notify-no-license-for-feature Yeslicense : notify-licensefile-missing Yeslicense : notify-license-expiry-warning Yesscsi : scsi-disc-complete Nofcns : reject-reg-req Nofcns : local-entry-change Nofcns : db-full Nofcns : remote-entry-change Norscn : rscnElsRejectReqNotify Norscn : rscnIlsRejectReqNotify Norscn : rscnElsRxRejectReqNotify Norscn : rscnIlsRxRejectReqNotify Nofcs : request-reject Nofcs : discovery-complete Nofctrace : route Nozone : request-reject1 Nozone : merge-success Nozone : merge-failure Nozone : default-zone-behavior-change Nozone : unsupp-mem Noport-security : fport-violation Noport-security : eport-violation Noport-security : fabric-binding-violation Novni : virtual-interface-created Novni : virtual-interface-removed Novsan : vsanStatusChange Novsan : vsanPortMembershipChange Nofspf : fspfNbrStateChangeNotify Noupgrade : UpgradeOpNotifyOnCompletion Noupgrade : UpgradeJobStatusNotify Nofeature-control : FeatureOpStatusChange Novrrp : cVrrpNotificationNewMaster Nofdmi : cfdmiRejectRegNotify Nosnmp : authentication NoConfiguring the Notification Target User
You must configure a notification target user on the switch for sending SNMPv3 inform notifications to the SNMP manager.
To configure the notification target user, use the following command:
The credentials of the notification target user are used for encrypting the SNMPv3 inform notification messages to the configured SNMPmanager (as in the snmp-server host command).
Note
For authenticating and decrypting the received INFORM PDU, the SNMP manager should have the same user credentials in its local configuration data store of users.
Configuring LinkUp/LinkDown Notifications for Switches
You can configure which linkUp/linkDown notifications to enable on switches. You can enable the following types of linkUp/linkDown notifications:
•
Cisco—Only notifications (cieLinkUp, cieLinkDown) defined in CISCO-IF-EXTENSION-MIB.my are sent for an interface, if ifLinkUpDownTrapEnable (defined in IF-MIB) is enabled for that interface.
•
IETF—Only notifications (linkUp, linkDown) defined in IF-MIB are sent for an interface, if ifLinkUpDownTrapEnable (defined in IF-MIB) is enabled for that interface. Only the varbinds defined in the notification definition are sent with the notifications.
•
IEFT extended—Only notifications (linkUp, linkDown) defined in IF-MIB are sent for an interface, if ifLinkUpDownTrapEnable (defined in IF-MIB) is enabled for that interface. In addition to the varbinds defined in the notification definition, varbinds defined in the IF-MIB specific to the Cisco Systems implementation are sent. This is the default setting.
•
IEFT Cisco—Only notifications (linkUp, linkDown) defined in IF-MIB and notifications (cieLinkUp, cieLinkDown) defined in CISCO-IF-EXTENSION-MIB.my are sent for an interface, if ifLinkUpDownTrapEnable (defined in IF-MIB) is enabled for that interface. Only the varbinds defined in the notification definition are sent with the linkUp and linkDown notifications.
•
IEFT extended Cisco—Only notifications (linkUp, linkDown) defined in IF-MIB and notifications (cieLinkUp, cieLinkDown) defined in CISCO-IF-EXTENSION-MIB.my are sent for an interface, if ifLinkUpDownTrapEnable (defined in IF-MIB) is enabled for that interface. In addition to the varbinds defined in linkUp and linkDown notification definition, varbinds defined in the IF-MIB specific to the Cisco Systems implementation are sent with the linkUp and linkDown notifications.
Note
For more information on the varbinds defined in the IF-MIB specific to the Cisco Systems implementation, refer to the Cisco MDS 9000 Family MIB Quick Reference.
To configure the linkUp/linkDown notification for a switch using NX-OS Release 4.1(x) and earlier, follow these steps:
Note
If both IETF and IETF extended are enabled, the show snmp traps command displays both as enabled. However, as a trap, you will receive only one trap with IETF extended payload.
To configure the linkUp/linkDown notification for a switch using NX-OS Release 4.2(1) and later, follow these steps:
Configuring Up/Down SNMP Link-State Traps for Interfaces
By default, SNMP link-state traps are enabled for all interfaces. Whenever a link toggles its state from Up to Down or vice versa, an SNMP trap is generated.
In some instances, you may find that you have numerous switches with hundreds of interfaces, many of which do not require monitoring of the link state. In such cases, you may elect to disable link-state traps.
To disable SNMP link-state traps for specific interfaces, follow these steps:
Whenever you disable an SNMP link-state trap for an interface, the command is also added to the running configuration of the system. To view the running configuration, enter the show running-config command for the interface.
switch# show running-configversion 3.1(2)....interface bay5interface bay6no link-state-trap <-----command is added to the running configuration for the interfaceinterface bay7...To view the SNMP link-state trap configuration for a particular interface, enter the show interface command.
switch# show interface bay 6bay6 is down (Administratively down)Hardware is Fibre ChannelPort WWN is 20:0b:00:05:30:01:70:2cAdmin port mode is auto, trunk mode is onsnmp link-state traps are disabledPort vsan is 1Receive data field Size is 2112Beacon is turned off5 minutes input rate 0 bits/sec, 0 bytes/sec, 0 frames/sec5 minutes output rate 0 bits/sec, 0 bytes/sec, 0 frames/sec0 frames input, 0 bytes0 discards, 0 errors0 CRC, 0 unknown class0 too long, 0 too short0 frames output, 0 bytes0 discards, 0 errors0 input OLS, 0 LRR, 0 NOS, 0 loop inits0 output OLS, 0 LRR, 0 NOS, 0 loop initsScope of Link Up/Down Trap Settings
The link Up/Down trap settings for the interfaces generate traps based on the following scope:
Enabled (defualt)
Enabled (default)
Yes
Enabled
Disabled
No
Disabled
Enabled
No
Disabled
Disabled
No
Configuring Entity (FRU) Traps
To enable individual SNMP trap control, follow these steps:
Note
All these traps have to do with legacy FRU traps.
Displaying SNMP Security Information
Use the show snmp commands to display configured SNMP information (see Example 7-1 and 7-6).
Example 7-1 Displays SNMP User Details
switch# show snmp user______________________________________________________________SNMP USERS______________________________________________________________User Auth Priv(enforce) Groups____ ____ _____________ ______admin md5 des(no) network-admintestusr md5 aes-128(no) role111role222______________________________________________________________NOTIFICATION TARGET USERS (configured for sending V3 Inform)______________________________________________________________User Auth Priv____ ____ ____testtargetusr md5 des(EngineID 0:0:0:63:0:1:0:0:0:15:10:3)Example 7-2 Displays SNMP Community Information
switch# show snmp communityCommunity Access--------- ------private rwpublic rov93RACqPNH roExample 7-3 Displays SNMP Host Information
switch# show snmp hostHost Port Version Level Type SecName____ ____ _______ ______ ____ ______171.16.126.34 2162 v2c noauth trap public171.16.75.106 2162 v2c noauth trap public...171.31.58.97 2162 v2c auth trap public...The show snmp command displays counter information for SNMP contact, location, and packet settings. This command provides information that is used entirely by the Cisco MDS 9000 Family Fabric Manager (refer to the Cisco Fabric Manager System Management Configuration Guide). See Example 7-4.
Example 7-4 Displays SNMP Information
switch# show snmpsys contact:sys location:1631 SNMP packets input0 Bad SNMP versions0 Unknown community name0 Illegal operation for community name supplied0 Encoding errors64294 Number of requested variables1 Number of altered variables1628 Get-request PDUs0 Get-next PDUs1 Set-request PDUs152725 SNMP packets output0 Too big errors1 No such name errors0 Bad values errors0 General errorsCommunity Group / Access--------- ------public rw______________________________________________________________SNMP USERS______________________________________________________________User Auth Priv(enforce) Groups____ ____ _____________ ______admin md5 des(no) network-admintestusr md5 aes-128(no) role111role222______________________________________________________________NOTIFICATION TARGET USERS (configured for sending V3 Inform)______________________________________________________________User Auth Priv____ ____ ____testtargetusr md5 des(EngineID 0:0:0:63:0:1:0:0:0:15:10:3)Example 7-5 Displays SNMP Engine IDs
switch# show snmp engineIDLocal SNMP engineID: [Hex] 8000000903000DEC2CF180[Dec] 128:000:000:009:003:000:013:236:044:241:128Example 7-6 Displays Information on SNMP Security Groups
switch# show snmp groupgroupname: network-adminsecurity model: anysecurity level: noAuthNoPrivreadview: network-admin-rdwriteview: network-admin-wrnotifyview: network-admin-rdstorage-type: permanentrow status: activegroupname: network-adminsecurity model: anysecurity level: authNoPrivreadview: network-admin-rdwriteview: network-admin-wrnotifyview: network-admin-rdstorage-type: permanentrow status: activegroupname: network-operatorsecurity model: anysecurity level: noAuthNoPrivreadview: network-operator-rdwriteview: network-operator-wrnotifyview: network-operator-rdstorage-type: permanentrow status: activegroupname: network-operatorsecurity model: anysecurity level: authNoPrivreadview: network-operator-rdwriteview: network-operator-wrnotifyview: network-operator-rdstorage-type: permanentrow status: activeDefault Settings
Table 7-2 lists the default settings for all SNMP features in any switch.
Table 7-2 Default SNMP Settings
User account
No expiry (unless configured)
Password
None

 Feedback
Feedback