IP Video Surveillance Design Guide
Network Diagram and Configuration Files

Table Of Contents
Network Diagram and Configuration Files
Router and Firewall Configurations
Network Diagram and Configuration Files
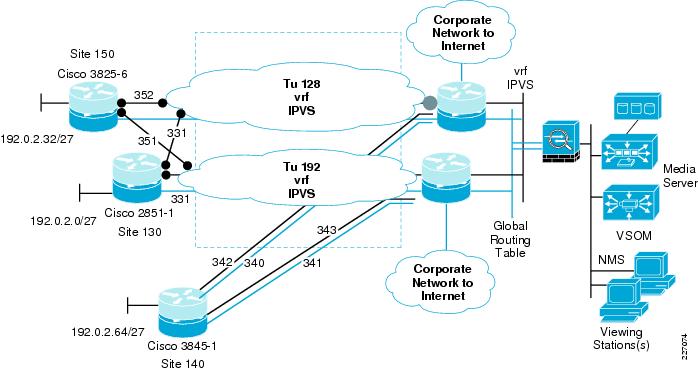
This chapter contains a topology diagram and the associated router, firewall, and switch configuration files for the devices in this sample implementation. See Figure 1.
Figure 1 Network Diagram
Router and Firewall Configurations
In this section the running configuration files from the routers shown in the previous topology diagram are included as reference.
vpn-jk2-7206-1
This configuration is for the upper WAN aggregation router shown in the topology diagram.
!! Last configuration change at 13:06:43 edt Tue Aug 4 2009! NVRAM config last updated at 13:07:50 edt Tue Aug 4 2009!upgrade fpd autoversion 12.4service timestamps debug datetime msec localtime show-timezoneservice timestamps log datetime msec localtime show-timezoneservice password-encryption!hostname vpn-jk2-7206-1!boot-start-markerboot system flash disk0:c7200-adventerprisek9-mz.124-15.T5boot-end-marker!logging buffered 2000000enable secret 5 [removed]!no aaa new-modelclock timezone est -5clock summer-time edt recurringip wccp 61ip wccp 62ip cef!!no ip dhcp use vrf connected!!!ip vrf IPVSrd 100:10route-target export 100:10route-target import 100:10!no ip domain lookupip domain name cisco.comip host rtp5-esevpn-ios-ca 10.81.0.27ip multicast-routingip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3!multilink bundle-name authenticated!!!crypto pki trustpoint rtp5-esevpn-ios-caenrollment url http://rtp5-esevpn-ios-ca:80revocation-check none!!crypto pki certificate chain rtp5-esevpn-ios-cacertificate 0D3082023A 308201A3 A0030201 0202010D 300D0609 2A864886 F70D0101 040500306B310C30 0A060355 04081303 204E4331 11300F06 03550407 13082052 616C6569419A9E33 E84ABC15 FCCFB1CC EBC1AE94 F07752CC 22A803C7 99AE4097 BA2Dquitcertificate ca 01308202AF 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 0405003047DC2CE3 BC3F5F40 32409535 C9E0E6C0 F29D4Equitarchivelog confighidekeys!!crypto isakmp policy 100encr 3desgroup 2crypto isakmp keepalive 10crypto isakmp nat keepalive 10crypto isakmp profile IPVS_Branches_isakmp_profiledescription IPVS_Branches_isakmp_profileself-identity addressca trust-point rtp5-esevpn-ios-camatch identity host domain ese.cisco.comcrypto isakmp profile DMVPN_IKE_PROFILEdescription DMVPN Profileself-identity fqdnca trust-point rtp5-esevpn-ios-camatch identity address 64.102.223.24 255.255.255.255keepalive 10 retry 2!!crypto ipsec transform-set 3DES_SHA_TUNNEL esp-3des esp-sha-hmaccrypto ipsec transform-set 3DES_SHA_TRANSPORT esp-3des esp-sha-hmacmode transport!crypto ipsec profile DMVPN_IPSEC_PROFILEset transform-set 3DES_SHA_TRANSPORTset isakmp-profile DMVPN_IKE_PROFILE!crypto ipsec profile IPVS_Branches_ipsec_profiledescription IPVS_Branches_ipsec_profileset transform-set 3DES_SHA_TRANSPORT 3DES_SHA_TUNNELset isakmp-profile IPVS_Branches_isakmp_profile!!controller ISA 5/1!!class-map match-any LOW-LATENCY-DATAmatch ip dscp af21 af22 af23class-map match-any HIGH-THROUGHPUT-DATAmatch ip dscp af11 af12 af13class-map match-all BROADCAST-VIDEOmatch ip dscp cs5class-map match-all NETWORK-CONTROLmatch ip dscp cs6class-map match-any MULTIMEDIA-CONFERENCINGmatch ip dscp af41 af42 af43class-map match-all OAMmatch ip dscp cs2class-map match-all VOICEmatch ip dscp efclass-map match-all SCAVENGERmatch ip dscp cs1class-map match-any CALL-SIGNALINGmatch ip dscp cs3!!policy-map IPVS_BRANCHclass BROADCAST-VIDEObandwidth percent 40class VOICEpriority percent 10class LOW-LATENCY-DATAbandwidth percent 4class HIGH-THROUGHPUT-DATAbandwidth percent 4class MULTIMEDIA-CONFERENCINGbandwidth percent 4class SCAVENGERbandwidth percent 1class OAMbandwidth percent 1class NETWORK-CONTROLbandwidth percent 1class CALL-SIGNALINGbandwidth percent 1class class-defaultfair-queuepolicy-map 30Mclass class-defaultshape average 30000000service-policy IPVS_BRANCH!!!!!interface Loopback0description Loopback for Global RTip address 192.168.15.40 255.255.255.255!interface Tunnel128description DMVPN tunnel/cloud to Branchesip vrf forwarding IPVSip address 192.168.15.129 255.255.255.192no ip redirectsip mtu 1400ip nhrp authentication FOOip nhrp map multicast dynamicip nhrp map multicast 192.168.15.40ip nhrp network-id 128ip nhrp nhs 192.168.15.129ip nhrp server-onlyip route-cache flowno ip split-horizon eigrp 65ip summary-address eigrp 65 192.0.2.0 255.255.255.0 5tunnel source Loopback0tunnel mode gre multipointtunnel key 128tunnel protection ipsec profile IPVS_Branches_ipsec_profile!interface Tunnel300description DMVPN Tunnel to Enterprise/Internetip address 10.81.7.254 255.255.255.240ip mtu 1400ip pim sparse-modeip nhrp authentication BARip nhrp map multicast dynamicip nhrp map 10.81.7.241 64.102.223.24ip nhrp map multicast 64.102.223.24ip nhrp network-id 22341ip nhrp nhs 10.81.7.241ip route-cache flowload-interval 30tunnel source FastEthernet0/0tunnel destination 64.102.223.24tunnel key 300tunnel protection ipsec profile DMVPN_IPSEC_PROFILE!interface FastEthernet0/0description FLASH156ip address 172.26.157.3 255.255.254.0no ip proxy-arpload-interval 30duplex fullspeed 100!interface FastEthernet0/1no ip addressip flow ingressduplex autospeed auto!interface FastEthernet0/1.90description ASA DMZ Globalencapsulation dot1Q 90ip address 10.81.7.161 255.255.255.248ip flow ingressstandby 0 ip 10.81.7.166standby 0 preempt delay minimum 60!interface FastEthernet0/1.91description ASA DMZ vrf IPVSencapsulation dot1Q 91ip vrf forwarding IPVSip address 192.168.15.97 255.255.255.248ip flow ingressstandby 0 ip 192.168.15.102standby 0 preempt delay!interface FastEthernet0/1.332description MAN/WAN to Site 130 (vpn1-2851-1)encapsulation dot1Q 332ip address 192.168.15.45 255.255.255.252ip flow ingressservice-policy output 30M!interface FastEthernet0/1.340description MAN/WAN to Site 140 (vpn1-3845-1)encapsulation dot1Q 340ip address 192.168.15.13 255.255.255.252ip flow ingressservice-policy output 30M!interface FastEthernet0/1.342description MAN/WAN to Site 140 (vpn1-3845-1)encapsulation dot1Q 342ip vrf forwarding IPVSip address 192.168.15.77 255.255.255.252ip flow ingressip summary-address eigrp 65 192.0.2.0 255.255.255.0 5service-policy output 30M!interface FastEthernet0/1.352description MAN/WAN to Site 150 (vpn4-3800-6)encapsulation dot1Q 352ip address 192.168.15.49 255.255.255.252ip flow ingress!router eigrp 64redistribute static metric 1000 100 255 1 1500 route-map ASA5510_VPN3080redistribute eigrp 65 metric 1000 100 255 1 1500 route-map Branch_Networkspassive-interface FastEthernet0/1.90network 10.0.0.0no auto-summaryeigrp stub connected redistributed!router eigrp 65redistribute eigrp 64 metric 1000 100 255 1 1500 route-map DEFAULTnetwork 192.168.15.0 0.0.0.63no auto-summary!address-family ipv4 vrf IPVSredistribute static metric 1000 10 255 1 1500 route-map COMMAND_CENTERnetwork 192.168.15.64 0.0.0.63network 192.168.15.128 0.0.0.63distribute-list route-map Branch_Net_vrf_IPVS_RT inno auto-summaryautonomous-system 65exit-address-family!ip forward-protocol ndip route 10.81.0.27 255.255.255.255 172.26.156.1 name rtp5-esevpn-ios-caip route 10.81.7.56 255.255.255.252 10.81.7.163 name ASA5510ip route 10.81.254.0 255.255.255.0 172.26.156.1 name NTP_Serversip route 64.102.223.16 255.255.255.240 172.26.156.1 name cryptHEip route 172.26.0.0 255.255.0.0 172.26.156.1ip route vrf IPVS 10.81.7.0 255.255.255.0 192.168.15.99 name ASA5510_PATip route vrf IPVS 192.0.2.128 255.255.255.224 192.168.15.99 name ASA5510ip route vrf IPVS 192.168.15.64 255.255.255.248 192.168.15.99 name VPN3080_poolno ip http serverno ip http secure-server!ip flow-cache timeout inactive 30ip flow-cache timeout active 1ip flow-export version 5!!ip access-list standard Branch_Net_vrf_IPVS_RTpermit 192.0.2.0 0.0.0.255ip access-list standard DEFAULTpermit 0.0.0.0!ip prefix-list ALL_VMSS seq 5 permit 192.0.2.0/24!ip prefix-list ASA5510_VPN3080 seq 5 permit 10.81.7.56/30!ip prefix-list Branch_Net_vrf_IPVS_RT seq 132 permit 192.168.111.0/24ip prefix-list Branch_Net_vrf_IPVS_RT seq 142 permit 192.168.11.0/24ip prefix-list Branch_Net_vrf_IPVS_RT seq 152 permit 192.168.211.0/24!ip prefix-list Branch_Networks seq 130 permit 10.81.7.152/29ip prefix-list Branch_Networks seq 131 permit 192.0.2.0/27ip prefix-list Branch_Networks seq 132 permit 192.168.111.0/24ip prefix-list Branch_Networks seq 140 permit 10.81.7.0/29ip prefix-list Branch_Networks seq 141 permit 192.0.2.64/26ip prefix-list Branch_Networks seq 142 permit 192.168.11.0/24ip prefix-list Branch_Networks seq 150 permit 10.81.7.88/29ip prefix-list Branch_Networks seq 151 permit 192.0.2.32/27ip prefix-list Branch_Networks seq 152 permit 192.168.211.0/24!ip prefix-list COMMAND_CENTER seq 100 permit 192.0.2.128/25ip prefix-list COMMAND_CENTER seq 101 permit 10.81.7.0/24ip prefix-list COMMAND_CENTER seq 102 permit 192.168.15.64/29!ip prefix-list SITE_130 seq 5 permit 192.0.2.0/27!ip prefix-list SITE_140 seq 5 permit 192.0.2.64/26ip sla responderlogging alarm informationalsnmp-server enable traps tty!!!route-map Branch_Net_vrf_IPVS_RT permit 10match ip address prefix-list Branch_Net_vrf_IPVS_RTset tag 5011!route-map Branch_Net_vrf_IPVS_RT permit 20match ip address Branch_Net_vrf_IPVS_RTset tag 5011!route-map COMMAND_CENTER permit 10match ip address prefix-list COMMAND_CENTERset tag 2128!route-map Branch_Networks permit 10match ip address prefix-list Branch_Networksset tag 5010!route-map DEFAULT permit 10match ip address DEFAULT!route-map ASA5510_VPN3080 permit 10match ip address prefix-list ASA5510_VPN3080!!!!control-plane!!!gatekeepershutdown!banner exec========== This is the WAN/MAN router for IPVS branches======!line con 0exec-timeout 0 0stopbits 1line aux 0stopbits 1line vty 0 4exec-timeout 0 0password 7 [removed]login!ntp master 12ntp update-calendarntp server 10.81.254.202ntp server 10.81.254.131!endvpn-jk2-7206-2
This configuration is for the bottomWAN aggregation router shown in the topology diagram.
!! Last configuration change at 13:10:14 edt Tue Aug 4 2009! NVRAM config last updated at 13:11:17 edt Tue Aug 4 2009!upgrade fpd autoversion 12.4no service padservice timestamps debug datetime msec localtime show-timezoneservice timestamps log datetime msec localtime show-timezoneservice password-encryption!hostname vpn-jk2-7206-2!boot-start-markerboot system disk0:c7200-adventerprisek9-mz.124-15.T5boot-end-marker!enable secret 5 [removed]!no aaa new-modelclock timezone est -5clock summer-time edt recurringip cef!!!!ip vrf IPVSrd 100:10route-target export 100:10route-target import 100:10!no ip domain lookupip domain name cisco.comip host rtp5-esevpn-ios-ca 10.81.0.27ip multicast-routingip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3!multilink bundle-name authenticated!!crypto pki trustpoint rtp5-esevpn-ios-caenrollment url http://rtp5-esevpn-ios-ca:80revocation-check none!!crypto pki certificate chain rtp5-esevpn-ios-cacertificate 123082023A 308201A3 A0030201 02020112 300D0609 2A864886 F70D0101 04050030D2993DBF 32824A8C 420DC983 C5BF7E17 28D1406E 0D937B7D 152C6FB3 D581quitcertificate ca 01308202AF 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 0405003047DC2CE3 BC3F5F40 32409535 C9E0E6C0 F29D4Equitarchivelog confighidekeys!!crypto isakmp policy 100encr 3desgroup 2crypto isakmp keepalive 10crypto isakmp nat keepalive 10crypto isakmp profile IPVS_Branches_isakmp_profiledescription IPVS_Branches_isakmp_profileself-identity addressca trust-point rtp5-esevpn-ios-camatch identity host domain ese.cisco.com!!crypto ipsec transform-set 3DES_SHA_TUNNEL esp-3des esp-sha-hmaccrypto ipsec transform-set 3DES_SHA_TRANSPORT esp-3des esp-sha-hmacmode transportcrypto ipsec transform-set AES_SHA_TUNNEL esp-aes esp-sha-hmaccrypto ipsec transform-set AES_SHA_TRANSPORT esp-aes esp-sha-hmacmode transport!crypto ipsec profile IPVS_Branches_ipsec_profiledescription IPVS_Branches_ipsec_profileset transform-set 3DES_SHA_TRANSPORT 3DES_SHA_TUNNELset isakmp-profile IPVS_Branches_isakmp_profile!!controller ISA 5/1!!class-map match-any LOW-LATENCY-DATAmatch ip dscp af21 af22 af23class-map match-any HIGH-THROUGHPUT-DATAmatch ip dscp af11 af12 af13class-map match-all BROADCAST-VIDEOmatch ip dscp cs5class-map match-all NETWORK-CONTROLmatch ip dscp cs6class-map match-any MULTIMEDIA-CONFERENCINGmatch ip dscp af41 af42 af43class-map match-all OAMmatch ip dscp cs2class-map match-all VOICEmatch ip dscp efclass-map match-all SCAVENGERmatch ip dscp cs1class-map match-any CALL-SIGNALINGmatch ip dscp cs3!!policy-map IPVS_BRANCHclass BROADCAST-VIDEObandwidth percent 40class VOICEpriority percent 10class LOW-LATENCY-DATAbandwidth percent 4class HIGH-THROUGHPUT-DATAbandwidth percent 4class MULTIMEDIA-CONFERENCINGbandwidth percent 4class SCAVENGERbandwidth percent 1class OAMbandwidth percent 1class NETWORK-CONTROLbandwidth percent 1class CALL-SIGNALINGbandwidth percent 1class class-defaultfair-queuepolicy-map 30Mclass class-defaultshape average 30000000service-policy IPVS_BRANCH!!interface Loopback0description Loopback for Global RTip address 192.168.15.41 255.255.255.255!interface Tunnel192ip vrf forwarding IPVSip address 192.168.15.193 255.255.255.192no ip redirectsip mtu 1400ip nhrp authentication FOOip nhrp map multicast dynamicip nhrp map multicast 192.168.15.41ip nhrp network-id 192ip nhrp nhs 192.168.15.193ip nhrp server-onlyip route-cache flowno ip split-horizon eigrp 65ip summary-address eigrp 65 192.0.2.0 255.255.255.0 5tunnel source Loopback0tunnel mode gre multipointtunnel key 192tunnel protection ipsec profile IPVS_Branches_ipsec_profile!interface FastEthernet0/0ip address 172.26.157.4 255.255.254.0no ip proxy-arpip route-cache flowduplex fullspeed 100!interface FastEthernet0/1description MAN/WAN to Branchesno ip addressip route-cache flowduplex fullspeed 100!interface FastEthernet0/1.90description ASA DMZ Globalencapsulation dot1Q 90ip address 10.81.7.162 255.255.255.248ip flow ingressstandby 0 ip 10.81.7.166standby 0 priority 90standby 0 preempt delay minimum 60!interface FastEthernet0/1.91description ASA DMZ vrf IPVSencapsulation dot1Q 91ip vrf forwarding IPVSip address 192.168.15.98 255.255.255.248ip flow ingressstandby 0 ip 192.168.15.102standby 0 priority 90standby 0 preempt delay minimum 60!!interface FastEthernet0/1.331encapsulation dot1Q 331ip address 192.168.15.21 255.255.255.252service-policy output 30M!interface FastEthernet0/1.341encapsulation dot1Q 341ip address 192.168.15.25 255.255.255.252service-policy output 30M!interface FastEthernet0/1.343encapsulation dot1Q 343ip vrf forwarding IPVSip address 192.168.15.89 255.255.255.252ip summary-address eigrp 65 192.0.2.0 255.255.255.0 5service-policy output 30M!interface FastEthernet0/1.351encapsulation dot1Q 351ip address 192.168.15.29 255.255.255.252!router eigrp 64redistribute eigrp 65 metric 1000 100 255 1 1500 route-map Branch_Networkspassive-interface FastEthernet0/1.90network 10.0.0.0no auto-summaryeigrp stub connected redistributed!router eigrp 65redistribute eigrp 64 metric 1000 100 255 1 1500 route-map DEFAULTnetwork 192.168.15.0 0.0.0.63no auto-summary!address-family ipv4 vrf IPVSredistribute static metric 1000 10 255 1 1500 route-map COMMAND_CENTERoffset-list 0 out 1000network 192.168.15.64 0.0.0.63network 192.168.15.192 0.0.0.63distribute-list route-map Branch_Net_vrf_IPVS_RT inno auto-summaryautonomous-system 65exit-address-family!ip forward-protocol ndip route 10.81.0.27 255.255.255.255 172.26.156.1 name rtp5-esevpn-ios-caip route 10.81.7.56 255.255.255.252 10.81.7.163 name ASA5510ip route 10.81.254.0 255.255.255.0 172.26.156.1 name NTP_Serversip route 64.102.223.16 255.255.255.240 172.26.156.1 name cryptHEip route vrf IPVS 10.81.7.0 255.255.255.0 192.168.15.99 name ASA5510_PATip route vrf IPVS 192.0.2.128 255.255.255.224 192.168.15.99 name ASA5510ip route vrf IPVS 192.168.15.64 255.255.255.248 192.168.15.99 name VPN3080_poolno ip http serverno ip http secure-server!!!ip access-list standard Branch_Net_vrf_IPVS_RTpermit 192.0.2.0 0.0.0.255ip access-list standard DEFAULTpermit 0.0.0.0!!!ip prefix-list Branch_Net_vrf_IPVS_RT seq 132 permit 192.168.111.0/24ip prefix-list Branch_Net_vrf_IPVS_RT seq 142 permit 192.168.11.0/24ip prefix-list Branch_Net_vrf_IPVS_RT seq 152 permit 192.168.211.0/24!ip prefix-list Branch_Networks seq 130 permit 10.81.7.152/29ip prefix-list Branch_Networks seq 131 permit 192.0.2.0/27ip prefix-list Branch_Networks seq 132 permit 192.168.111.0/24ip prefix-list Branch_Networks seq 140 permit 10.81.7.0/29ip prefix-list Branch_Networks seq 141 permit 192.0.2.64/26ip prefix-list Branch_Networks seq 142 permit 192.168.11.0/24ip prefix-list Branch_Networks seq 150 permit 10.81.7.88/29ip prefix-list Branch_Networks seq 151 permit 192.0.2.32/27ip prefix-list Branch_Networks seq 152 permit 192.168.211.0/24!ip prefix-list COMMAND_CENTER seq 100 permit 192.0.2.128/25ip prefix-list COMMAND_CENTER seq 101 permit 10.81.7.0/24ip prefix-list COMMAND_CENTER seq 102 permit 192.168.15.64/29logging alarm informational!!!route-map Branch_Net_vrf_IPVS_RT permit 10match ip address prefix-list Branch_Net_vrf_IPVS_RTset tag 5011!route-map Branch_Net_vrf_IPVS_RT permit 20match ip address Branch_Net_vrf_IPVS_RTset tag 5011!route-map COMMAND_CENTER permit 10match ip address prefix-list COMMAND_CENTERset tag 2128!route-map Branch_Networks permit 10match ip address prefix-list Branch_Networksset tag 5010!route-map DEFAULT permit 10match ip address DEFAULT!control-plane!!!gatekeepershutdown!!line con 0transport output allstopbits 1line aux 0transport output allstopbits 1line vty 0 4password 7 [removed]logintransport input alltransport output all!ntp clock-period 17179966ntp master 12ntp update-calendarntp server 10.81.254.202ntp server 10.81.254.131!endvpn-jk2-asa5510-1
This configuration is for the firewall shown in the topology diagram: Saved: Written by enable_15 at 13:55:41.021 edt Tue Aug 4 2009!ASA Version 8.0(4)!hostname vpn-jk2-asa5510-1domain-name ese.cisco.comenable password 2KFQnbNIdI.2KYOU encryptedpasswd [removed] encryptednamesdns-guard!interface Ethernet0/0description Campus_IPVS VLAN 220speed 100duplex fullnameif Campus_IPVSsecurity-level 70ip address 192.0.2.129 255.255.255.224!interface Ethernet0/1description DMZ_IPVS VLAN 91speed 100duplex fullnameif DMZ_IPVSsecurity-level 50ip address 192.168.15.99 255.255.255.248!interface Ethernet0/2description DMZ_Global VLAN 90speed 100duplex fullnameif DMZ_Globalsecurity-level 10ip address 10.81.7.163 255.255.255.248!interface Ethernet0/3description DMZ for VPN3080speed 100duplex fullnameif DMZ_VPN3080security-level 20ip address 10.81.7.58 255.255.255.252!interface Management0/0description FlashNETspeed 100duplex fullnameif FlashNETsecurity-level 0ip address 172.26.156.3 255.255.254.0!boot system disk0:/asa804-k8.binftp mode passiveclock timezone est -5clock summer-time edt recurringdns server-group DefaultDNSdomain-name ese.cisco.comaccess-list MANAGEMENT extended permit tcp 10.81.7.0 255.255.255.0 interface FlashNETaccess-list IPVS-CC extended permit udp any 192.0.2.128 255.255.255.224 eq syslogaccess-list IPVS-CC extended permit udp any host 192.0.2.139 eq snmptrapaccess-list IPVS-CC extended permit udp any host 192.0.2.139 eq 7777access-list IPVS-CC extended permit tcp 192.0.2.0 255.255.255.0 any eq wwwaccess-list INBOUND extended permit esp any host 10.81.7.57access-list INBOUND extended permit udp any host 10.81.7.57 eq isakmpaccess-list INBOUND extended permit udp any host 10.81.7.57 eq 4500access-list INBOUND extended permit icmp any host 10.81.7.57pager lines 24logging enablelogging buffered debugginglogging asdm debuggingmtu Campus_IPVS 1500mtu DMZ_IPVS 1500mtu DMZ_Global 1500mtu DMZ_VPN3080 1500mtu FlashNET 1500no failovericmp unreachable rate-limit 1 burst-size 1icmp permit any Campus_IPVSicmp permit any DMZ_IPVSicmp permit any DMZ_Globalicmp permit any DMZ_VPN3080asdm image disk0:/asdm-61551.binno asdm history enablearp timeout 14400global (DMZ_Global) 1 interfacenat (Campus_IPVS) 1 192.0.2.128 255.255.255.224static (DMZ_VPN3080,DMZ_Global) 192.168.15.56 192.168.15.56 netmask 255.255.255.252static (Campus_IPVS,DMZ_IPVS) 192.0.2.128 192.0.2.128 netmask 255.255.255.224static (Campus_IPVS,DMZ_IPVS) 192.168.15.64 192.168.15.64 netmask 255.255.255.248access-group IPVS-CC in interface DMZ_IPVSaccess-group INBOUND in interface DMZ_Globalaccess-group MANAGEMENT in interface FlashNET control-planeroute DMZ_Global 0.0.0.0 0.0.0.0 10.81.7.166 1route FlashNET 172.16.0.0 255.240.0.0 172.26.156.1 1route DMZ_IPVS 192.0.2.0 255.255.255.0 192.168.15.102 1route DMZ_IPVS 192.168.11.0 255.255.255.0 192.168.15.102 1route Campus_IPVS 192.168.15.64 255.255.255.248 192.0.2.136 1route DMZ_IPVS 192.168.111.0 255.255.255.0 192.168.15.102 1route DMZ_IPVS 192.168.211.0 255.255.255.0 192.168.15.102 1timeout xlate 3:00:00timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolutedynamic-access-policy-record DfltAccessPolicyhttp server enablehttp 172.26.156.0 255.255.254.0 FlashNEThttp 10.81.7.0 255.255.255.0 FlashNETsnmp-server location ESE Labsnmp-server contact joel.king@cisco.comsnmp-server enable traps snmp authentication linkup linkdown coldstartcrypto ipsec security-association lifetime seconds 28800crypto ipsec security-association lifetime kilobytes 4608000telnet 10.81.7.176 255.255.255.248 FlashNETtelnet 172.26.156.0 255.255.254.0 FlashNETtelnet timeout 60ssh 10.81.7.0 255.255.255.0 FlashNETssh 172.26.156.0 255.255.254.0 FlashNETssh timeout 60console timeout 0dhcpd dns 64.102.6.247dhcpd wins 64.102.6.247dhcpd lease 28880dhcpd domain ese.cisco.comdhcpd option 3 ip 192.0.2.129!dhcpd address 192.0.2.140-192.0.2.150 Campus_IPVSdhcpd enable Campus_IPVS!threat-detection basic-threatthreat-detection statistics access-listno threat-detection statistics tcp-interceptntp server 10.81.7.162ntp server 10.81.7.161ssl encryption rc4-sha1!class-map inspection_defaultmatch default-inspection-traffic!!policy-map type inspect dns migrated_dns_map_1parametersmessage-length maximum 512policy-map global_policyclass inspection_defaultinspect dns migrated_dns_map_1inspect ftpinspect h323 h225inspect h323 rasinspect netbiosinspect rshinspect rtspinspect skinnyinspect esmtpinspect sqlnetinspect sunrpcinspect tftpinspect sipinspect xdmcp!service-policy global_policy globalprompt hostname contextCryptochecksum:3d4d4e2f06d5a11ff2dd5d5643e862f5: endvpn1-2851-1
This configuration is for the branch 2851 model router shown in the topology diagram!! Last configuration change at 13:26:29 edt Tue Aug 4 2009! NVRAM config last updated at 13:27:56 edt Tue Aug 4 2009!version 12.4service timestamps debug datetime msec localtime show-timezoneservice timestamps log datetime msec localtime show-timezoneservice password-encryptionservice udp-small-serversservice tcp-small-servers!hostname vpn1-2851-1!boot-start-markerboot-end-marker!logging buffered 8192enable secret 5 [removed]!no aaa new-modelclock timezone est -5clock summer-time edt recurring!crypto pki trustpoint rtp5-esevpn-ios-caenrollment url http://rtp5-esevpn-ios-ca:80revocation-check nonesource interface Vlan1!!crypto pki certificate chain rtp5-esevpn-ios-cacertificate 0F3082023B 308201A4 A0030201 0202010F 300D0609 2A864886 F70D0101 0405003032C8325C 8DF24E4B D16823BA AF45A2F8 A6AA3C9C 8E33E400 CBAE2184 09F267quitcertificate ca 01308202AF 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 0405003047DC2CE3 BC3F5F40 32409535 C9E0E6C0 F29D4Equitdot11 syslog!!ip cefip dhcp use vrf connectedip dhcp excluded-address 192.168.111.1 192.168.111.149ip dhcp excluded-address 192.0.2.17 192.0.2.19!ip dhcp pool CAMERASvrf IPVSnetwork 192.0.2.16 255.255.255.240default-router 192.0.2.17dns-server 64.102.6.247 171.68.226.120domain-name cisco.com!ip dhcp pool iSCSI-tempnetwork 192.168.111.0 255.255.255.0default-router 192.168.111.1domain-name cisco.com!!ip vrf IPVSrd 100:10route-target export 100:10route-target import 100:10!no ip domain lookupip host harry 172.26.129.252ip host rtp5-esevpn-ios-ca 10.81.0.27ip multicast-routingip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3!multilink bundle-name authenticated!!voice-card 0no dspfarm!!username joeking privilege 15 secret 5 [removed]!!crypto isakmp policy 120encr 3desgroup 2crypto isakmp keepalive 10crypto isakmp nat keepalive 10crypto isakmp profile IPVS_Branches_isakmp_profileself-identity fqdnca trust-point rtp5-esevpn-ios-camatch identity address 192.168.15.40 255.255.255.255keepalive 10 retry 2crypto isakmp profile IPVS_Branches_isakmp_profile_2self-identity fqdnca trust-point rtp5-esevpn-ios-camatch identity address 192.168.15.41 255.255.255.255keepalive 10 retry 2!!crypto ipsec transform-set AES_SHA_TUNNEL esp-aes esp-sha-hmaccrypto ipsec transform-set 3DES_SHA_TUNNEL esp-3des esp-sha-hmaccrypto ipsec transform-set 3DES_SHA_TRANSPORT esp-3des esp-sha-hmacmode transportcrypto ipsec transform-set AES_SHA_TRANSPORT esp-aes esp-sha-hmacmode transport!crypto ipsec profile IPVS_Branches_ipsec_profiledescription IPVS_Branches_ipsec_profileset transform-set 3DES_SHA_TRANSPORT 3DES_SHA_TUNNELset isakmp-profile IPVS_Branches_isakmp_profile!crypto ipsec profile IPVS_Branches_ipsec_profile_2set transform-set 3DES_SHA_TRANSPORT 3DES_SHA_TUNNELset isakmp-profile IPVS_Branches_isakmp_profile_2!!archivelog confighidekeys!!ip finger!class-map match-any GOLDmatch ip dscp cs2 cs3 cs6 cs7match ip dscp af41 af42 af43match ip dscp af31 af32 af33class-map match-all TELEPRESENCEmatch ip dscp cs4class-map match-any LOW-LATENCY-DATAmatch ip dscp af21 af22 af23class-map match-any BRONZEmatch ip dscp af11 af12 af13match ip dscp cs1class-map match-any HIGH-THROUGHPUT-DATAmatch ip dscp af11 af12 af13class-map match-any VMSSmatch access-group name HTTPclass-map match-all BROADCAST-VIDEOmatch ip dscp cs5class-map match-all NETWORK-CONTROLmatch ip dscp cs6class-map match-any MULTIMEDIA-CONFERENCINGmatch ip dscp af41 af42 af43class-map match-all OAMmatch ip dscp cs2class-map match-all FOOclass-map match-any REAL_TIMEmatch ip dscp cs5match ip dscp cs4match ip dscp efclass-map match-all VOICEmatch ip dscp efclass-map match-all SCAVENGERmatch ip dscp cs1class-map match-any CALL-SIGNALINGmatch ip dscp cs3class-map match-any MULTIMEDIA-STREAMINGmatch ip dscp af31 af32 af33!!policy-map IPVS_BRANCHclass BROADCAST-VIDEObandwidth percent 40class VOICEpriority percent 10class LOW-LATENCY-DATAbandwidth percent 4class HIGH-THROUGHPUT-DATAbandwidth percent 4class MULTIMEDIA-CONFERENCINGbandwidth percent 4class SCAVENGERbandwidth percent 1class OAMbandwidth percent 1class NETWORK-CONTROLbandwidth percent 1class CALL-SIGNALINGbandwidth percent 1class class-defaultfair-queuepolicy-map UPLINK_50Mclass class-defaultshape average 50000000service-policy IPVS_BRANCHpolicy-map INGRESS_VMSSclass VMSSset ip dscp cs5class class-defaultset ip dscp cs3policy-map PER_CLASS_SHAPINGclass REAL_TIMEset cos 5police 40000000 conform-action transmit exceed-action transmitclass GOLDshape average 2500000set cos 6class BRONZEshape average 2500000set cos 1class class-defaultset cos 0shape average 5000000policy-map 30Mclass class-defaultshape average 30000000service-policy IPVS_BRANCH!!interface Tunnel128ip vrf forwarding IPVSip address 192.168.15.130 255.255.255.192ip mtu 1400ip nhrp authentication FOOip nhrp map 192.168.15.129 192.168.15.40ip nhrp map multicast 192.168.15.40ip nhrp network-id 128ip nhrp nhs 192.168.15.129ip summary-address eigrp 65 192.0.2.0 255.255.255.224 5tunnel source GigabitEthernet0/1.332tunnel destination 192.168.15.40tunnel key 128tunnel protection ipsec profile IPVS_Branches_ipsec_profile!interface Tunnel192ip vrf forwarding IPVSip address 192.168.15.194 255.255.255.192ip mtu 1400ip nhrp authentication FOOip nhrp map multicast 192.168.15.41ip nhrp map 192.168.15.193 192.168.15.41ip nhrp network-id 192ip nhrp nhs 192.168.15.193ip summary-address eigrp 65 192.0.2.0 255.255.255.224 5tunnel source GigabitEthernet0/1.331tunnel destination 192.168.15.41tunnel key 192tunnel protection ipsec profile IPVS_Branches_ipsec_profile_2!interface GigabitEthernet0/0description Insideno ip addressip flow ingressload-interval 30duplex autospeed auto!interface GigabitEthernet0/0.204description Insideencapsulation dot1Q 204ip address 10.81.7.153 255.255.255.248ip flow ingress!interface GigabitEthernet0/0.206description VLAN 206 for IP Camerasencapsulation dot1Q 206ip vrf forwarding IPVSip address 192.0.2.17 255.255.255.240ip flow ingress!interface GigabitEthernet0/1description Outsideno ip addressload-interval 30duplex autospeed auto!interface GigabitEthernet0/1.130description To vpn-jk3-2651xm-4 Primary WANbandwidth 30000encapsulation dot1Q 130ip address dhcp!interface GigabitEthernet0/1.254description iSCSI Management Subnetencapsulation dot1Q 254ip vrf forwarding IPVSip address 192.168.111.1 255.255.255.0!interface GigabitEthernet0/1.331encapsulation dot1Q 331ip address 192.168.15.22 255.255.255.252service-policy output 30M!interface GigabitEthernet0/1.332encapsulation dot1Q 332ip address 192.168.15.46 255.255.255.252service-policy output PER_CLASS_SHAPING!interface FastEthernet0/3/0duplex fullspeed 100!interface FastEthernet0/3/1!interface FastEthernet0/3/2!interface FastEthernet0/3/3!interface Integrated-Service-Engine1/0ip vrf forwarding IPVSip address 192.0.2.1 255.255.255.252ip flow ingressload-interval 30service-module external ip address 192.168.111.2 255.255.255.0service-module ip address 192.0.2.2 255.255.255.252service-module ip default-gateway 192.0.2.1no keepaliveservice-policy input INGRESS_VMSS!interface Video-Service-Engine2/0ip vrf forwarding IPVSip address 192.0.2.5 255.255.255.252ip flow ingressservice-module ip address 192.0.2.6 255.255.255.252service-module ip default-gateway 192.0.2.5no keepalive!interface Vlan1description Flashnetip address 172.26.156.51 255.255.254.0no ip proxy-arp!router eigrp 65network 10.81.7.152 0.0.0.7network 192.168.15.0 0.0.0.63no auto-summary!address-family ipv4 vrf IPVSnetwork 192.0.2.0 0.0.0.31network 192.168.15.128 0.0.0.63network 192.168.15.192 0.0.0.63network 192.168.111.0no auto-summaryautonomous-system 65exit-address-family!ip forward-protocol ndip route 10.81.0.27 255.255.255.255 172.26.156.1 name rtp5-esevpn-ios-caip route 172.26.0.0 255.255.0.0 172.26.156.1 name Milesip route 192.168.15.40 255.255.255.255 192.168.15.45 name vpn-jk2-7206-1_Loopback_0ip route 192.168.15.41 255.255.255.255 192.168.15.21 name vpn-jk2-7206-2_Loopback_0ip route 64.102.223.16 255.255.255.240 dhcpip route 192.5.41.40 255.255.255.254 dhcp!ip flow-cache timeout active 1ip flow-export version 5ip flow-export destination 172.26.157.11 7777!ip http serverip http secure-serverno ip pim dm-fallbackip pim autorp listener!ip access-list extended HTTPpermit tcp host 192.0.2.2 eq www anyip access-list extended VSOMpermit tcp host 192.0.2.2 eq www 192.168.16.0 0.0.15.255permit tcp host 192.0.2.2 eq 443 192.168.16.0 0.0.15.255!!ip prefix-list CAMPUS seq 5 permit 192.168.16.0/20ip sla responderip sla 219icmp-echo 192.0.2.19tos 192threshold 50vrf IPVSowner networkmgrtag ipvs - design guidefrequency 64history lives-kept 1history buckets-kept 60history filter failuresip sla schedule 219 life forever start-time nowlogging 172.26.157.11snmp-server enable traps tty!!control-plane!!banner execC i s c o S y s t e m s|| |||| || Cisco Systems, Inc.|||| |||| IT-Transport.:|||||||:.......:|||||||:..US, Asia & Americas support: + 1 408 526 8888EMEA support: + 31 020 342 3888UNAUTHORIZED ACCESS TO THIS NETWORK DEVICE IS PROHIBITED.You must have explicit permission to access or configure thisdevice. All activities performed on this device are logged andviolations of this policy may result in disciplinary action.Questions regarding this device should be directed toxxxxxxxbanner motd====== Site 130 === vpn1-2851-1===alias exec analog service-module Video-Service-Engine2/0 session!line con 0exec-timeout 0 0line aux 0line 66no activation-characterno exectransport preferred nonetransport input alltransport output lat pad telnet rlogin lapb-ta mop udptn v120 sshline 130no activation-characterno exectransport preferred nonetransport input alltransport output lat pad telnet rlogin lapb-ta mop udptn v120 sshline vty 0 4exec-timeout 0 0password 7 [removed]login local!scheduler allocate 20000 1000ntp clock-period 17180366ntp source GigabitEthernet0/0.206ntp master 12ntp server 192.168.4.1 source GigabitEthernet0/1.130ntp server 10.81.254.202 source GigabitEthernet0/0.204ntp server 10.81.254.131 source GigabitEthernet0/0.204!endvpn1-3845-1
This configuration is for the branch 3845 model router shown in the topology diagram!! Last configuration change at 13:21:52 edt Tue Aug 4 2009! NVRAM config last updated at 13:23:50 edt Tue Aug 4 2009!version 12.4service timestamps debug datetime msec localtime show-timezoneservice timestamps log datetime msec localtime show-timezoneno service password-encryptionservice udp-small-serversservice tcp-small-servers!hostname vpn1-3845-1!boot-start-markerboot system flash flash:c3845-adventerprisek9-mz.124-15.T5boot system flash flash:c3845-adventerprisek9-mz.124-22.Tboot-end-marker!logging buffered 2000000enable secret 5 [removed]!no aaa new-modelclock timezone est -5clock summer-time edt recurringdot11 syslogip wccp 61ip wccp 62ip cef!!ip dhcp use vrf connectedip dhcp excluded-address 192.0.2.97 192.0.2.102!ip dhcp pool ENTERPRISEnetwork 10.81.7.0 255.255.255.248default-router 10.81.7.1dns-server 64.102.6.247 171.68.226.120domain-name ese.cisco.comnetbios-name-server 171.68.235.228 171.68.235.229!ip dhcp pool CAMERASvrf IPVSnetwork 192.0.2.96 255.255.255.224default-router 192.0.2.97dns-server 64.102.6.247 171.68.226.120domain-name ese.cisco.com!!ip vrf IPVSrd 100:10route-target export 100:10route-target import 100:10!no ip domain lookupip domain name ese.cisco.comip host rtp5-esevpn-ios-ca 10.81.0.27ip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3ip dhcp-client default-router distance 239!multilink bundle-name authenticated!voice-card 0no dspfarm!!!key chain PURPLEkey 10key-string 7 00[removed]00!!!oer masterpolicy-rules LOSSshutdownlogging!border 192.168.0.1 key-chain PURPLEinterface GigabitEthernet0/1.250 internalinterface GigabitEthernet0/1.210 internalinterface GigabitEthernet0/1.294 externalinterface GigabitEthernet0/1.293 externalinterface Integrated-Service-Engine3/0 internal!learnthroughputdelayperiodic-interval 0monitor-period 1expire after time 30aggregation-type prefix-length 29no max range receivedelay threshold 80mode route controlmode select-exit best!oer borderlocal Loopback0master 192.168.0.1 key-chain PURPLE!crypto pki trustpoint rtp5-esevpn-ios-caenrollment url http://rtp5-esevpn-ios-ca:80revocation-check nonesource interface Vlan1!!crypto pki certificate chain rtp5-esevpn-ios-cacertificate 0E3082023B 308201A4 A0030201 0202010E 300D0609 2A864886 F70D0101 04050030DE5E201F F1A6CB47 D57C7260 70BE64AD 78656E15 A2EB7E43 9D969FB5 C4233Bquitcertificate ca 01308202AF 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 0405003047DC2CE3 BC3F5F40 32409535 C9E0E6C0 F29D4Equit!!username joeking privilege 15 secret 5 [removed]archivelog confighidekeys!!crypto isakmp policy 100encr 3desgroup 2crypto isakmp keepalive 10crypto isakmp nat keepalive 10crypto isakmp profile DMVPN_IKE_PROFILEdescription DMVPN Profileself-identity fqdnca trust-point rtp5-esevpn-ios-camatch identity address 64.102.223.24 255.255.255.255keepalive 10 retry 2crypto isakmp profile DMVPN_IKE_PROFILE_2description DMVPN Profileself-identity fqdnca trust-point rtp5-esevpn-ios-camatch identity address 64.102.223.25 255.255.255.255keepalive 10 retry 2!!crypto ipsec transform-set 3DES_SHA_TUNNEL esp-3des esp-sha-hmaccrypto ipsec transform-set 3DES_SHA_TRANSPORT esp-3des esp-sha-hmacmode transport!crypto ipsec profile DMVPN_IPSEC_PROFILEset transform-set 3DES_SHA_TRANSPORTset isakmp-profile DMVPN_IKE_PROFILE!crypto ipsec profile DMVPN_IPSEC_PROFILE_2set transform-set 3DES_SHA_TRANSPORTset isakmp-profile DMVPN_IKE_PROFILE_2!ip finger!class-map match-any LOW-LATENCY-DATAmatch ip dscp af21 af22 af23class-map match-any HIGH-THROUGHPUT-DATAmatch ip dscp af11 af12 af13class-map match-all BROADCAST-VIDEOmatch ip dscp cs5class-map match-all NETWORK-CONTROLmatch ip dscp cs6class-map match-any MULTIMEDIA-CONFERENCINGmatch ip dscp af41 af42 af43class-map match-all OAMmatch ip dscp cs2class-map match-all VOICEmatch ip dscp efclass-map match-all SCAVENGERmatch ip dscp cs1class-map match-any CALL-SIGNALINGmatch ip dscp cs3!!policy-map DATAclass class-defaultfair-queuerandom-detectpolicy-map IPVS_BRANCHclass BROADCAST-VIDEObandwidth percent 40class VOICEpriority percent 10class LOW-LATENCY-DATAbandwidth percent 4class HIGH-THROUGHPUT-DATAbandwidth percent 4class MULTIMEDIA-CONFERENCINGbandwidth percent 4class SCAVENGERbandwidth percent 1class OAMbandwidth percent 1class NETWORK-CONTROLbandwidth percent 1class CALL-SIGNALINGbandwidth percent 1class class-defaultfair-queuepolicy-map 30Mclass class-defaultshape average 30000000service-policy IPVS_BRANCH!policy-map 2Mclass class-defaultshape average 2000000service-policy DATA!!interface Loopback0description for OER peeringip address 192.168.0.1 255.255.255.255!interface GigabitEthernet0/0no ip addressshutdownduplex fullspeed 100media-type rj45!interface GigabitEthernet0/1description Trunkno ip addressip route-cache flowload-interval 30duplex autospeed automedia-type rj45!interface GigabitEthernet0/1.140description WANencapsulation dot1Q 140ip address dhcp!interface GigabitEthernet0/1.210description IP Camera VLANencapsulation dot1Q 210ip vrf forwarding IPVSip address 192.0.2.97 255.255.255.224!interface GigabitEthernet0/1.250description INSIDE VLANencapsulation dot1Q 250ip address 10.81.7.1 255.255.255.248!interface GigabitEthernet0/1.256description management interface for iSCSIencapsulation dot1Q 256ip vrf forwarding IPVSip address 192.168.11.1 255.255.255.0!interface GigabitEthernet0/1.293description To vpn-jk2-7206-1 for PfRencapsulation dot1Q 293ip address 192.168.15.6 255.255.255.252shutdown!interface GigabitEthernet0/1.294description To vpn-jk2-7206-1 for PfRencapsulation dot1Q 294ip address 192.168.15.2 255.255.255.252shutdown!interface GigabitEthernet0/1.340encapsulation dot1Q 340ip address 192.168.15.14 255.255.255.252service-policy output 2M!interface GigabitEthernet0/1.341encapsulation dot1Q 341ip address 192.168.15.26 255.255.255.252service-policy output 2M!interface GigabitEthernet0/1.342encapsulation dot1Q 342ip vrf forwarding IPVSip address 192.168.15.78 255.255.255.252ip summary-address eigrp 65 192.0.2.64 255.255.255.192 5service-policy output 30M!interface GigabitEthernet0/1.343encapsulation dot1Q 343ip vrf forwarding IPVSip address 192.168.15.90 255.255.255.252ip summary-address eigrp 65 192.0.2.64 255.255.255.192 5service-policy output 30M!interface FastEthernet1/0description connection to Flashnetduplex fullspeed 100!interface FastEthernet1/1!interface FastEthernet1/2!interface FastEthernet1/3!interface FastEthernet1/4!interface FastEthernet1/5!interface FastEthernet1/6!interface FastEthernet1/7!interface FastEthernet1/8!interface FastEthernet1/9!interface FastEthernet1/10!interface FastEthernet1/11!interface FastEthernet1/12!interface FastEthernet1/13!interface FastEthernet1/14!interface FastEthernet1/15!interface GigabitEthernet1/0shutdown!interface Integrated-Service-Engine2/0description NME-WAE-522-K9ip address 192.0.2.69 255.255.255.252ip wccp redirect exclude inservice-module ip address 192.0.2.70 255.255.255.252service-module ip default-gateway 192.0.2.69no keepalive!interface Integrated-Service-Engine3/0description NME-VMSS-HP32 ip wccp 61 red in 62 red outip vrf forwarding IPVSip address 192.0.2.64 255.255.255.254ip nbar protocol-discoveryip flow ingressip route-cache flowload-interval 30service-module external ip address 192.168.11.2 255.255.255.0service-module ip address 192.0.2.65 255.255.255.254service-module ip default-gateway 192.0.2.64no keepalive!interface Vlan1ip address 172.26.156.53 255.255.254.0no ip proxy-arp!router eigrp 65network 10.81.7.0 0.0.0.7network 192.168.15.0 0.0.0.63no auto-summary!address-family ipv4 vrf IPVSnetwork 192.0.2.64 0.0.0.63network 192.168.11.0network 192.168.15.64 0.0.0.63no auto-summaryautonomous-system 65exit-address-family!ip forward-protocol ndip route 192.168.16.0 255.255.240.0 192.168.15.1 230 name OER_Parentip route 192.168.16.0 255.255.240.0 192.168.15.5 230 name OER_Parentip route 192.168.32.0 255.255.224.0 192.168.15.1 230 name OER_Parentip route 192.168.32.0 255.255.224.0 192.168.15.5 230 name OER_Parentip route 64.102.223.16 255.255.255.240 dhcp!ip flow-cache timeout active 1ip flow-export source Integrated-Service-Engine3/0ip flow-export version 5ip flow-export destination 172.26.157.11 7777!no ip http serverno ip http secure-server!!ip prefix-list CAMPUS seq 5 permit 192.168.16.0/20ip sla responderip sla 293udp-jitter 192.168.15.5 14216 source-ip 192.168.15.6 codec g729a codec-numpackets 50tos 184timeout 500owner joekingtag VERIFICATION for Vlan 293ip sla schedule 293 life forever start-time nowip sla 294udp-jitter 192.168.15.1 14214 source-ip 192.168.15.2 codec g729a codec-numpackets 50tos 184timeout 500owner joekingtag VERIFICATION for Vlan 294ip sla schedule 294 life forever start-time nowsnmp-server enable traps tty!!!oer-map LOSS 10match traffic-class prefix-list CAMPUSset mode select-exit bestset mode route controlset mode monitor fastset resolve loss priority 1 variance 10set resolve delay priority 2 variance 10set loss relative 100set active-probe jitter 192.168.16.1 target-port 32014 codec g729aset probe frequency 10!control-plane!!!line con 0exec-timeout 120 0line aux 0line 130no activation-characterno exectransport preferred nonetransport input alltransport output lat pad telnet rlogin lapb-ta mop udptn v120 sshline 194no activation-characterno exectransport preferred nonetransport input alltransport output lat pad telnet rlogin lapb-ta mop udptn v120 sshline vty 0 4login local!scheduler allocate 20000 1000ntp clock-period 17180273ntp source Integrated-Service-Engine3/0ntp master 12ntp server 10.81.254.202 source Vlan1ntp server 10.81.254.131 source Vlan1!endvpn4-3800-6
This configuration is for the branch 3825 model router shown in the topology diagram! ================= vpn4-3800-6 ==================================!! Last configuration change at 13:33:32 edt Tue Aug 4 2009! NVRAM config last updated at 13:35:16 edt Tue Aug 4 2009!version 12.4service timestamps debug datetime msec localtime show-timezoneservice timestamps log datetime msec localtime show-timezoneservice password-encryptionservice udp-small-serversservice tcp-small-servers!hostname vpn4-3800-6!boot-start-markerboot-end-marker!enable secret 5 [removed]!no aaa new-modelclock timezone est -5clock summer-time edt recurringdot11 syslogip cef!!ip dhcp use vrf connectedip dhcp excluded-address 192.168.211.1 192.168.211.149ip dhcp excluded-address 192.0.2.52!ip dhcp pool camerasvrf IPVSnetwork 192.0.2.48 255.255.255.240default-router 192.0.2.49domain-name ese.cisco.comdns-server 64.102.6.247 171.68.226.120!ip dhcp pool iSCSI-tempnetwork 192.168.211.0 255.255.255.0default-router 192.168.211.1domain-name cisco.com!!ip vrf IPVSrd 100:10route-target export 100:10route-target import 100:10!ip host rtp5-esevpn-ios-ca 10.81.0.27ip host harry 172.26.129.252ip multicast-routingip auth-proxy max-nodata-conns 3ip admission max-nodata-conns 3!multilink bundle-name authenticated!voice-card 0no dspfarm!!!crypto pki trustpoint rtp5-esevpn-ios-caenrollment url http://rtp5-esevpn-ios-ca:80revocation-check none!!crypto pki certificate chain rtp5-esevpn-ios-cacertificate 133082023B 308201A4 A0030201 02020113 300D0609 2A864886 F70D0101 040500306C240A83 ADF2674E D83B7BEF 59A04BC8 A0474C0C 492CAD79 2713CCFA 1783F4quitcertificate ca 01308202AF 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 04050030A9C7FB7B F68000AE 7C8FABF5 24279B82 8A394A91 4DF83555 D2C9D52E 84779C3747DC2CE3 BC3F5F40 32409535 C9E0E6C0 F29D4Equit!!username joeking privilege 15 secret 5 vpn4-3800-6username test password 7 vpn4-3800-6archivelog confighidekeys!!crypto isakmp policy 100encr 3desgroup 2crypto isakmp keepalive 10crypto isakmp nat keepalive 10crypto isakmp profile IPVS_Branches_isakmp_profileself-identity fqdnca trust-point rtp5-esevpn-ios-camatch identity address 192.168.15.40 255.255.255.255keepalive 10 retry 2crypto isakmp profile IPVS_Branches_isakmp_profile_2self-identity fqdnca trust-point rtp5-esevpn-ios-camatch identity address 192.168.15.41 255.255.255.255keepalive 10 retry 2!!crypto ipsec transform-set 3DES_SHA_TUNNEL esp-3des esp-sha-hmaccrypto ipsec transform-set 3DES_SHA_TRANSPORT esp-3des esp-sha-hmacmode transportcrypto ipsec transform-set AES_SHA_TUNNEL esp-aes esp-sha-hmaccrypto ipsec transform-set AES_SHA_TRANSPORT esp-aes esp-sha-hmacmode transport!crypto ipsec profile IPVS_Branches_ipsec_profiledescription IPVS_Branches_ipsec_profileset transform-set 3DES_SHA_TRANSPORT 3DES_SHA_TUNNELset isakmp-profile IPVS_Branches_isakmp_profile!crypto ipsec profile IPVS_Branches_ipsec_profile_2set transform-set 3DES_SHA_TRANSPORT 3DES_SHA_TUNNELset isakmp-profile IPVS_Branches_isakmp_profile_2!!!!ip finger!class-map match-any LOW-LATENCY-DATAmatch ip dscp af21 af22 af23class-map match-any HIGH-THROUGHPUT-DATAmatch ip dscp af11 af12 af13class-map match-all BROADCAST-VIDEOmatch ip dscp cs5class-map match-all NETWORK-CONTROLmatch ip dscp cs6class-map match-any MULTIMEDIA-CONFERENCINGmatch ip dscp af41 af42 af43class-map match-all OAMmatch ip dscp cs2class-map match-all VOICEmatch ip dscp efclass-map match-all SCAVENGERmatch ip dscp cs1class-map match-any CALL-SIGNALINGmatch ip dscp cs3!!policy-map IPVS_BRANCHclass BROADCAST-VIDEObandwidth percent 40class VOICEpriority percent 10class LOW-LATENCY-DATAbandwidth percent 4class HIGH-THROUGHPUT-DATAbandwidth percent 4class MULTIMEDIA-CONFERENCINGbandwidth percent 4class SCAVENGERbandwidth percent 1class OAMbandwidth percent 1class NETWORK-CONTROLbandwidth percent 1class CALL-SIGNALINGbandwidth percent 1class class-defaultfair-queuepolicy-map 30Mclass class-defaultshape average 30000000service-policy IPVS_BRANCH!!interface Tunnel128ip vrf forwarding IPVSip address 192.168.15.131 255.255.255.192ip mtu 1400ip nhrp authentication FOOip nhrp map 192.168.15.129 192.168.15.40ip nhrp map multicast 192.168.15.40ip nhrp network-id 128ip nhrp nhs 192.168.15.129ip summary-address eigrp 65 192.0.2.32 255.255.255.224 5tunnel source GigabitEthernet0/0.352tunnel destination 192.168.15.40tunnel key 128tunnel protection ipsec profile IPVS_Branches_ipsec_profile!interface Tunnel192ip vrf forwarding IPVSip address 192.168.15.195 255.255.255.192ip mtu 1400ip nhrp authentication FOOip nhrp map 192.168.15.193 192.168.15.41ip nhrp map multicast 192.168.15.41ip nhrp network-id 192ip nhrp nhs 192.168.15.193ip summary-address eigrp 65 192.0.2.32 255.255.255.224 5tunnel source GigabitEthernet0/0.351tunnel destination 192.168.15.41tunnel key 192tunnel protection ipsec profile IPVS_Branches_ipsec_profile_2!interface GigabitEthernet0/0description TRUNKno ip addressip route-cache flowload-interval 30duplex fullspeed 100media-type rj45!interface GigabitEthernet0/0.150description Outside WANencapsulation dot1Q 150ip address dhcp!interface GigabitEthernet0/0.203description Inside global routing for corporate end-usersencapsulation dot1Q 203ip address 10.81.7.89 255.255.255.248!interface GigabitEthernet0/0.208description Inside interface for IP Camerasencapsulation dot1Q 208ip vrf forwarding IPVSip address 192.0.2.49 255.255.255.240ip pim sparse-mode!interface GigabitEthernet0/0.258description iSCSI Management Subnetencapsulation dot1Q 258ip vrf forwarding IPVSip address 192.168.211.1 255.255.255.0!interface GigabitEthernet0/0.351description vpn-jk2-7206-2 [Second Head-end]encapsulation dot1Q 351ip address 192.168.15.30 255.255.255.252service-policy output 30M!interface GigabitEthernet0/0.352description vpn-jk2-7206-1 [Primary Head-end]encapsulation dot1Q 352ip address 192.168.15.50 255.255.255.252service-policy output 30M!interface GigabitEthernet0/1no ip addressduplex autospeed automedia-type rj45!interface FastEthernet0/2/0description Flashnetduplex fullspeed 100!interface FastEthernet0/2/1!interface FastEthernet0/2/2!interface FastEthernet0/2/3!interface Video-Service-Engine1/0ip vrf forwarding IPVSip address 192.0.2.37 255.255.255.252ip route-cache flowservice-module ip address 192.0.2.38 255.255.255.252service-module ip default-gateway 192.0.2.37no keepalive!interface Integrated-Service-Engine2/0ip vrf forwarding IPVSip address 192.0.2.33 255.255.255.252ip route-cache flowservice-module external ip address 192.168.211.2 255.255.255.0service-module ip address 192.0.2.34 255.255.255.252service-module ip default-gateway 192.0.2.33no keepalive!interface Vlan1description FlashNetip address 172.26.156.105 255.255.254.0no ip proxy-arp!router eigrp 65network 10.81.7.88 0.0.0.7network 192.168.15.0 0.0.0.63no auto-summary!address-family ipv4 vrf IPVSnetwork 192.0.2.32 0.0.0.31network 192.168.15.128 0.0.0.127network 192.168.211.0no auto-summaryautonomous-system 65exit-address-family!ip forward-protocol ndip route 10.81.0.27 255.255.255.255 172.26.156.1 name IOS-CAip route 192.168.15.40 255.255.255.255 192.168.15.49 name vpn-jk2-7206-1_Loopback_0ip route 192.168.15.41 255.255.255.255 192.168.15.29 name vpn-jk2-7206-2_Loopback_0ip route 64.102.223.16 255.255.255.240 dhcpip route 192.5.41.40 255.255.255.254 dhcp!ip flow-cache timeout active 1ip flow-export version 5ip flow-export destination 172.26.157.11 7777!ip http serverno ip http secure-server!ip access-list extended LOCAL_LOGINpermit tcp host 192.0.2.33 any eq 2130deny ip any any log!snmp-server enable traps tty!!control-plane!!banner exec3825192.0.2.32 /30 ISR NM NME-VMSS-HP16192.0.2.36 /30 EVM-IPVS-16A192.0.2.40 reserved .40 to .47192.0.2.48 /28 Reserved for IP Cameras (0.0.0.15)banner motdC i s c o S y s t e m s|| |||| || Cisco Systems, Inc.|||| |||| IT-Transport.:|||||||:.......:|||||||:..US, Asia & Americas support: + 1 408 526 8888EMEA support: + 31 020 342 3888UNAUTHORIZED ACCESS TO THIS NETWORK DEVICE IS PROHIBITED.You must have explicit permission to access or configure thisdevice. All activities performed on this device are logged andviolations of this policy may result in disciplinary action.!line con 0exec-timeout 0 0line aux 0line 66no activation-characterno exectransport preferred nonetransport input alltransport output lat pad telnet rlogin lapb-ta mop udptn v120 sshline 130access-class LOCAL_LOGIN in vrf-alsologin localno activation-characterno exectransport preferred nonetransport input telnettransport output noneline vty 0 4exec-timeout 0 0login local!scheduler allocate 20000 1000ntp clock-period 17178750ntp source Integrated-Service-Engine2/0ntp master 12ntp server 192.168.6.1 source GigabitEthernet0/0.150ntp server 10.81.254.202 source Vlan1ntp server 10.81.254.131 source Vlan1!end3750-access
This configuration is for an access-layer switch not explicitly shown in the topology diagram. It is a cisco WS-C3750G-24PS model.! System image file is "flash:c3750-advipservicesk9-mz.122-44.SE1.bin"!3750-access#sh run bBuilding configuration...Current configuration : 6533 bytes!version 12.2no service padservice timestamps debug datetime msecservice timestamps log datetime msecno service password-encryption!hostname 3750-access!boot-start-markerboot-end-marker!!no aaa new-modelswitch 1 provision ws-c3750g-24pssystem mtu routing 1500vtp mode transparentip subnet-zerono ip domain-lookup!ip multicast-routing distributed!mls qos!crypto pki trustpoint TP-self-signed-798490880enrollment selfsignedsubject-name cn=IOS-Self-Signed-Certificate-798490880revocation-check nonersakeypair TP-self-signed-798490880!!crypto pki certificate chain TP-self-signed-798490880certificate self-signed 01!!!!macro name cisco-camera-2500#Assign Port Descriptiondescription Connected to IPVS Camera#Assign Cisco IPVS Camera in unique Layer 2 VLANswitchport access vlan $VLAN#Statically configure Cisco Camera port in access-modeswitchport mode access#Enable Layer 2 Port-Securityswitchport port-security#Dynamically register secured IPVS MAC address.switchport port-security mac-address sticky#Set maximum allowed secured MAC entry to 1. Default value, but with macro it will override manual setting.switchport port-security maximum 1#Set port security violation action to shutdown physical port. Default setting,but will macro it will override manual setting.switchport port-security violation shutdown#Enable QoS on Cisco Camera port and trust incoming DSCP value.mls qos trust dscp#Expedite port bring up process by enabling portfast configuration.spanning-tree portfast#Disable transmitting and receiving STP BPDU frame on Cisco Camera portspanning-tree bpdufilter enable@macro name CIVS-IPC-2500description Cisco Video Surveillance 2500 Series IP Cameraswitchport mode accessswitchport access vlan $VLANswitchport port-securityswitchport port-security mac-address stickyswitchport port-security maximum 1switchport port-security violation shutdownmls qos trust dscpspanning-tree portfastspanning-tree bpdufilter enableload-interval 60no shutdown@!spanning-tree mode pvstspanning-tree extend system-id!vlan internal allocation policy ascending!vlan 10,208,220-221!!class-map match-all HTTPmatch protocol httpclass-map match-all HTTP_aclmatch access-group name HTTPclass-map match-all HTTP_acl_clientmatch access-group name HTTP_client!!policy-map VSMSclass HTTP_aclset dscp cs5class class-defaultset dscp cs3policy-map Viewing_Stationclass HTTP_acl_clientset dscp cs5class class-defaultset dscp cs3!!!!interface GigabitEthernet1/0/1description trunk to vpn1-2851-1 [vpn-jk2-2948-1]switchport trunk encapsulation dot1qswitchport mode trunkload-interval 60priority-queue outmls qos trust dscp!interface GigabitEthernet1/0/2description Cisco Video Surveillance 2500 Series IP Cameraswitchport access vlan 208switchport mode accessswitchport port-securityswitchport port-security mac-address stickyswitchport port-security mac-address sticky 001d.e5ea.79d3load-interval 60mls qos trust dscpmacro description CIVS-IPC-2500spanning-tree portfastspanning-tree bpdufilter enable!interface GigabitEthernet1/0/3description 4300 IP camera 0021.1bfd.df85switchport access vlan 220switchport mode accessswitchport port-securityswitchport port-security mac-address stickyswitchport port-security mac-address sticky 0021.1bfd.df85load-interval 60mls qos trust dscpspanning-tree portfastspanning-tree bpdufilter enable!interface GigabitEthernet1/0/4description 4300 IP camera 0021.1bfd.df62switchport access vlan 220switchport mode accessswitchport port-securityswitchport port-security mac-address stickyswitchport port-security mac-address sticky 0021.1bfd.df62load-interval 60mls qos trust dscpspanning-tree portfastspanning-tree bpdufilter enable!interface GigabitEthernet1/0/5description Viewing Stationswitchport access vlan 208switchport mode accesspriority-queue outspanning-tree portfastspanning-tree bpdufilter enableservice-policy input Viewing_Station!interface GigabitEthernet1/0/6!interface GigabitEthernet1/0/7!interface GigabitEthernet1/0/8!interface GigabitEthernet1/0/9!interface GigabitEthernet1/0/10!interface GigabitEthernet1/0/11description CIVS-IPC-4500-1switchport access vlan 220switchport mode accessswitchport port-securityswitchport port-security mac-address stickyswitchport port-security mac-address sticky 001e.bdfc.19d6load-interval 60mls qos trust dscpspanning-tree portfastspanning-tree bpdufilter enable!interface GigabitEthernet1/0/12description CIVS-IPC-4500-2switchport access vlan 220switchport mode accessswitchport port-securityswitchport port-security mac-address stickyswitchport port-security mac-address sticky 0021.1bfd.dfc1load-interval 60mls qos trust dscpspanning-tree portfastspanning-tree bpdufilter enable!interface GigabitEthernet1/0/13description CIVS-IPC-4500-3switchport access vlan 220switchport mode accessswitchport port-securityswitchport port-security mac-address stickyswitchport port-security mac-address sticky 001b.53ff.6cb9load-interval 60mls qos trust dscpspanning-tree portfastspanning-tree bpdufilter enable!interface GigabitEthernet1/0/14description CIVS-IPC-4500-4switchport access vlan 220switchport mode accessswitchport port-securityswitchport port-security mac-address stickyswitchport port-security mac-address sticky 001e.bdfc.19c9load-interval 60mls qos trust dscpspanning-tree portfastspanning-tree bpdufilter enable!interface GigabitEthernet1/0/15!interface GigabitEthernet1/0/16!interface GigabitEthernet1/0/17!interface GigabitEthernet1/0/18!interface GigabitEthernet1/0/19!interface GigabitEthernet1/0/20!interface GigabitEthernet1/0/21!interface GigabitEthernet1/0/22!interface GigabitEthernet1/0/23!interface GigabitEthernet1/0/24!interface GigabitEthernet1/0/25!interface GigabitEthernet1/0/26!interface GigabitEthernet1/0/27!interface GigabitEthernet1/0/28!interface Vlan1no ip addressshutdown!ip classlessip http serverip http secure-server!!ip access-list extended HTTPpermit tcp any eq www anyip access-list extended HTTP_clientpermit tcp any any eq www!!control-plane!!line con 0exec-timeout 0 0line vty 0 4loginline vty 5 15login!!end