Feedback Feedback
|
Table Of Contents
Cisco Prime Optical 9.3.1 Basic External Authentication
Prime Optical Implementation of RADIUS
Default Prime Optical Policy Server Settings
Understanding the RADIUS Implementation
Installing RADIUS Authentication Tools
Configuring External Authentication Settings
Caveats for Local Authentication When External Authentication Is Enabled
Obtaining Documentation and Submitting a Service Request
Cisco Prime Optical 9.3.1 Basic External Authentication
June 6, 2012
This document describes the basic external authentication functionality in Cisco Prime Optical 9.3.1 running on a Solaris server.
Note
External authentication is not supported in Cisco Prime Optical running on a Linux server.
Contents
This document contains the following topics:
•
Default Prime Optical Policy Server Settings
•
Understanding the RADIUS Implementation
•
Installing RADIUS Authentication Tools
•
Configuring External Authentication Settings
•
Caveats for Local Authentication When External Authentication Is Enabled
•
Obtaining Documentation and Submitting a Service Request
Introduction
Cisco Prime Optical (formerly Cisco Transport Manager) is a carrier-class, multitechnology management system that integrates the end-to-end management of traditional transport networks and new carrier packet transport networks. It can help maintain the integrity of existing services, plus deliver interactive, content-based services and high-bandwidth applications.
Cisco Prime Optical manages the entire Cisco optical portfolio, including:
•
Metro core
•
Metro dense wavelength-division multiplexing (DWDM)
•
Metro edge and access products
•
New Carrier Packet Transport (CPT) System products
Prime Optical also serves as a foundation for integration into a larger overall Operations Support System (OSS) environment by providing northbound gateway interfaces to higher-layer management systems.
Overview
The basic external authentication feature enables Prime Optical to authenticate users who log in through the RADIUS access server.
Basic external authentication involves the following key components:
•
Prime Optical Implementation of RADIUS
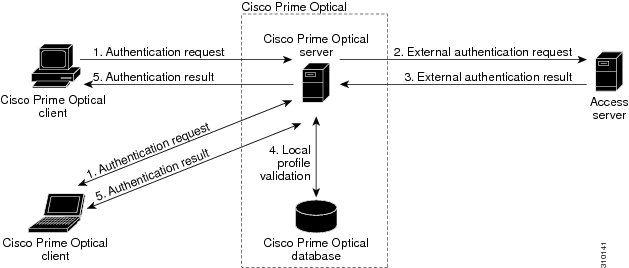
The following figure illustrates the basic external authentication workflow.
Figure 1 Basic External Authentication Workflow
Note
Basic external authentication is not available when Prime Optical is installed as part of Prime Central. For more information about Prime Central, see http://www.cisco.com/en/US/products/ps11754/tsd_products_support_series_home.html.
RADIUS Access Servers
An access server is a centralized network server that stores user and credential information. Network devices such as routers, NEs, and software applications request permission from the access server. If a user wants access to a network device, the network device sends an Access-Request to the access server. The access server replies with one of the following responses:
•
Access-Accept—The user can log into the network device.
•
Access-Reject—User access is denied.
•
Access-Challenge—Additional information is requested from the user.
The RADIUS access server:
•
Verifies user identity.
•
Determines whether the user is allowed to perform a task or access a network device.
•
Applies rules to user accounts.
Prime Optical Implementation of RADIUS
The Prime Optical server acts as a RADIUS client and sends authentication requests to a RADIUS server implementing a single sign-on (SSO) application.
The Prime Optical server uses the Pluggable Authentication Module (PAM) Solaris library for authentication. Specifically, it uses the pam_radius_auth module to authenticate users against the RADIUS access server. The PAM framework consists of the following parts:
•
PAM consumers—Solaris access applications such as login and rlogin, and the Prime Optical server.
•
PAM library.
•
PAM configuration file (pam.conf).
•
PAM service modules—Also referred to as providers.
Default Prime Optical Policy Server Settings
The following table lists the default Prime Optical configuration for the RADIUS access server.
Table 1 Default External Authentication Settings
External authentication
Disabled
Allow local fallback
Enabled
Enable SysAdmin
Enabled
Understanding the RADIUS Implementation
The Prime Optical server operates as a RADIUS client that is responsible for passing user information to designated RADIUS servers, and then acting on the response that is returned.
Prime Optical provides an installation script that installs the following files:
•
Pam_radius_auth.so—A shared library file that is provided by FreeRADIUS. It is a PAM service module that encapsulates all RADIUS client code installed in the usr/lib/security directory. The pam_radius_auth.so file is considered a third-party component.
•
Pam_radius_auth.conf—A configuration file installed in the /opt/ExtAuth/cfg directory. Configuration information includes the IP address of the RADIUS server, the authentication port, the shared secret, the request timeout, and the number of retries.
Note
The shared secret should be a strong password that contains at least 16 characters.
The installation script also changes the /etc/pam.conf file to configure the PAM library to use the pam_radius_auth.so service module for authentication.
Installing RADIUS Authentication Tools
Note
External authentication is not supported in Cisco Prime Optical running on a Linux server.
Step 1
Mount the Prime Optical Server Disk 1 installation DVD.
Step 2
Enter the following command:
cd /cdrom/ExtAuth/binStep 3
Launch the ./pam_radius_auth_install interactive script to install and configure the RADIUS client for Prime Optical.
Note
This step also copies the RADIUS files locally to /opt/ExtAuth, so that you can proceed without using a DVD.
Step 4
Follow the interactive script to install and add the RADIUS server configuration. The interactive script allows you to:
•
Install the PAM service module and RADIUS configurations.
•
Add configuration information for other RADIUS servers at any time.
•
Delete or modify configuration information.
•
Change the order of the RADIUS servers, because the position of a RADIUS server determines the order that Prime Optical's RADIUS client follows when requesting authentication when more than one RADIUS server is present.
•
Uninstall the PAM service module and RADIUS configurations.
RADIUS System Flow
Users must be configured on both the Prime Optical local authentication database and the remote access server. Usernames must be the same, but passwords can differ.
The following describes the system flow:
1.
The Prime Optical installation installs one user, the SysAdmin. As a SysAdmin user, you configure external authentication settings in the Prime Optical client Control Panel.
2.
The Prime Optical client forwards the authentication request to the Prime Optical server.
3.
The Prime Optical server's RADIUS client sends an Access-Request message to the RADIUS access server. The access server replies with an Access-Accept RADIUS message if the user credentials are accepted, with an Access-Reject if the user credentials are rejected, or with an Access-Challenge. For an Access-Challenge, the access server sends a human-readable request to the user; the Prime Optical client prompts the user with the request, collects the user response, and sends the response back to the Prime Optical server. The Prime Optical server sends a new Access-Request with the user's response to the access server. This process continues cyclically until the access server sends an Access-Accept or Access-Reject RADIUS message. For details, see http://www.ietf.org/rfc/rfc2865.txt.
The following table describes the RADIUS attributes that Prime Optical server's RADIUS client sends in Access-Request messages.
Configuring External Authentication Settings
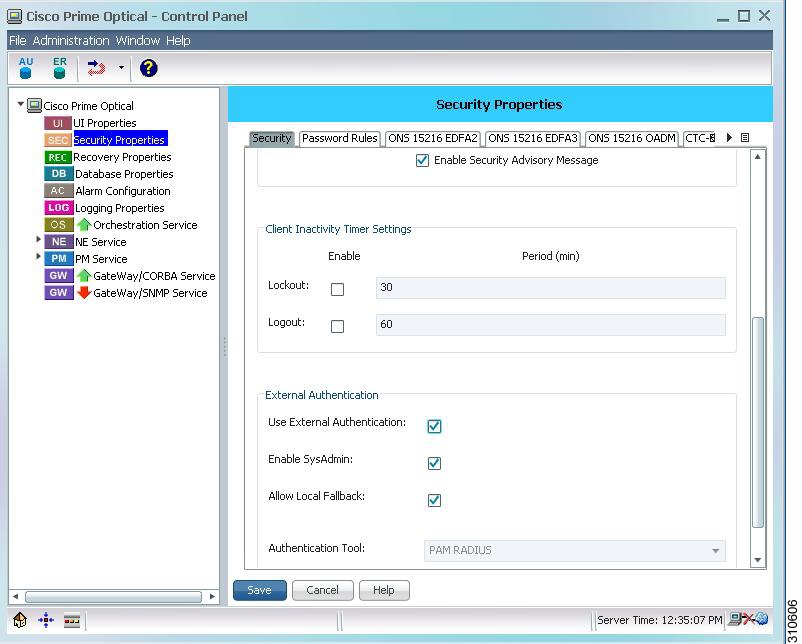
The following figure shows the External Authentication fields in the Control Panel. Complete the following steps to configure external authentication settings, which are stored in the Prime Optical database.
Figure 2 External Authentication Fields
Step 1
In the Domain Explorer window, choose Administration > Control Panel.
Step 2
Click Security Properties.
Step 3
In the External Authentication area, configure the following settings:
•
Use External Authentication—If checked, all authentication options are enabled, and the external authentication feature is active.
•
Enable SysAdmin—If checked, the SysAdmin user can always log into Prime Optical, even if the Allow Local Fallback check box is unchecked and the policy server is down.
•
Allow Local Fallback—If checked, the Prime Optical client users can still log into the Prime Optical server even if the policy server is unreachable. The SysAdmin user should enable the Allow Local Fallback setting in case the policy server is unavailable.
•
Authentication Tool—Display only. Indicates that PAM RADIUS is the third-party tool used for authentication.
Step 4
Click Save.
Step 5
To enable external authentication, you must restart the Prime Optical server. Enter the following command:
opticalctl stop ; opticalctl start
Note
You can still use the following legacy commands in Prime Optical 9.3.1:
•
ctms-start•
ctms-stop
Caveats for Local Authentication When External Authentication Is Enabled
When external authentication is enabled, the local authentication system is subject to the following caveats:
•
Because user credentials (passwords) are not checked against passwords in the local database, the following Prime Optical authentication features might not work in all cases:
–
User lockout
–
Autologin
The preceding features do not work when a user is logged in and the access server or the access server administrator changes that user's credentials. For example, the RADIUS RSA authentication manager can authenticate users by means of hardware devices (tokens) that generate a pseudorandom number that is used as a password. This number changes every minute, so a locked out user does not know which password was used to log in successfully in the past. To prevent this problem, open the Prime Optical client and in the Domain Explorer, choose Administration > Control Panel > Security Properties and uncheck the Lockout Enable check box.
•
If the Prime Optical client disconnects from the Prime Optical server, the client automatically tries to log in again using the cached username and password, which are no longer valid. The automatic login attempts fail. To resolve this problem, close the automatic login wizard and launch the Prime Optical client again.
•
Password aging rules and login preferences do not work, because they are demanded of the external access server. For this reason, these rules must remain disabled on the Prime Optical client. When external authentication is enabled, the following fields in the Control Panel > Security Properties > Security tab are automatically set to 0 (disabled):
–
Password Aging
–
Password Expiration Early Notification
–
Max Retries
–
Login Disable Period
•
The password change feature changes the local password. For this reason, do not use the password change feature when external authentication is enabled. Furthermore, password changing policies are access server dependent. In the Domain Explorer, choose Administration > Users. In the Cisco Prime Optical Users table, choose Edit > Create. In the Create New User wizard, uncheck the Require Password Change on Next Login check box.
•
Although authentication is external, authorization is local. For example, user privileges are managed locally.
Table of RADIUS Attributes
The following table lists the RADIUS attributes that Prime Optical supports. The table uses the following values:
•
Request/Accept/Reject/Challenge:
–
0—The attribute MUST NOT be present in the packet.
–
0+—Zero or more instances of the attribute MAY be present in the packet.
–
0-1—Zero or one instance of the attribute MAY be present in the packet.
–
1—Exactly one instance of the attribute MUST be present in the packet.
•
No.—Number of the RADIUS attribute as specified in the referenced RFC.
•
Attribute—Name of the RADIUS attribute.
•
Details—Details about the attribute: how it is used, delivered, or interpreted by the RADIUS client on the Prime Optical server.
•
RFC—Number of the referenced RFC.
•
RFC Req. Type—Whether a "requirement statement" is present in the referenced RFC.
–
MUST, MUST NOT, SHOULD, MAY, and so on—Requirement types as specified in RFC 2119. These words indicate that a requirement statement is present in the RFC. Note that the "MAY" requirements are optional requirements.
–
Unspecified—The attribute has no associated requirement statement. The RFC contains only a description of the attribute.
•
Supported—Indicates Prime Optical support for the attribute:
–
Yes—Supported
–
No—Not supported
–
N/A—Not applicable
–
Partial—Partially supported
Related Documentation
Note
You can access the most current Prime Optical documentation online at http://www.cisco.com/en/US/products/ps11670/tsd_products_support_series_home.html.
The Prime Optical documentation set comprises the following guides:
•
Release Notes for Cisco Prime Optical 9.3.1—Describes the caveats for Prime Optical.
•
Cisco Prime Optical 9.3.1 Installation Guide—Explains how to install Prime Optical and how to upgrade from previous releases.
•
Cisco Prime Optical 9.3.1 User Guide—Describes how to use the Prime Optical software, which consists of user applications and tools for network discovery, network configuration, connection management, fault management, system administration, and security management.
•
Cisco Prime Optical 9.3.1 Gateway/CORBA User Guide and Programmer Manual—Describes the GateWay/CORBA northbound interface product that is available for Prime Optical. This document serves as a reference for developers of OSS applications that work with the GateWay/CORBA interface.
•
Cisco Prime Optical 9.3.1 Database Schema—Describes the database schema that Prime Optical uses to store information in a Structured Query Language (SQL) database such as the Oracle database. The document is designed for users who need to create their own reports without using Prime Optical.
•
Cisco Prime Optical 9.3.1 High Availability Installation Guide—Explains how to install Prime Optical in a high availability (HA) environment.
Note
To obtain the Cisco Prime Optical 9.3.1 High Availability Installation Guide, contact your Cisco account representative.
•
Cisco Prime Optical 9.3.1 ML Provisioning Methodology—Describes the methodology that Prime Optical uses to provision ML-series cards.
•
Cisco Prime Optical 9.3.1 Basic External Authentication—This document.
•
Migration Matrix for Service Pack Releases—Describes the migration matrix for service pack releases.
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information, see the monthly What's New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation, at:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What's New in Cisco Product Documentation as a Really Simple Syndication (RSS) feed and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free service and Cisco currently supports RSS version 2.0.
This document is to be used in conjunction with the documents listed in the "Related Documentation" section.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2007-2011 Cisco Systems, Inc. All rights reserved.