Feedback Feedback
|
Table Of Contents
Router IP Traffic Export Packet Capture Enhancements
Restrictions for IP Traffic Export
Information About IP Traffic Export
IP Traffic Export Profiles Overview
Configuring IP Traffic Capture
Configuring IP Traffic Capture
Displaying IP Traffic Export Configuration Data
Configuration Examples for IP Traffic Export
Exporting IP Traffic Configuration: Example
Capturing IP Traffic Configuration: Example
Feature Information for IP Traffic Export
Router IP Traffic Export Packet Capture Enhancements
First Published: November 17, 2006Last Updated: November 17, 2006IP Traffic Export allows you to configure your router to export IP packets received on multiple, simultaneous WAN or LAN interfaces. The unaltered IP packets are exported on a single LAN or VLAN interface, thereby, easing deployment of protocol analyzers and monitoring devices.
The Router IP Traffic Export Packet Capture Enhancements feature allows you to configure your router to capture IP packets in a buffer within the router, and then to dump these packets into a specified memory device.
Finding Feature Information in This Module
Your Cisco IOS software release may not support all of the features documented in this module. To reach links to specific feature documentation in this module and to see a list of the releases in which each feature is supported, use the "Feature Information for IP Traffic Export" section.
Finding Support Information for Platforms and Cisco IOS and Catalyst OS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS and Catalyst OS software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Contents
•
Restrictions for IP Traffic Export
•
Information About IP Traffic Export
•
Configuration Examples for IP Traffic Export
•
Feature Information for IP Traffic Export
Restrictions for IP Traffic Export
Platform Restrictions
IP traffic export is intended only for software switching platforms; distributed architectures are not supported.
IP traffic capture is supported only on the Cisco 1841, Cisco 2800 series, and Cisco 3800 series integrated services routers.
IP Packet Forwarding Performance Impact
When IP traffic export is enabled, a delay is incurred on the outbound interface when packets are captured and transmitted across the interface. Performance delays increase with the increased number of interfaces that are monitored and the increased number of destination hosts.
Exported Traffic Limitation
•
The MAC address of the device that is receiving the exported traffic must be on the same VLAN or directly connected to one of the router interfaces. (Use the show arp command to determine the MAC address of device that is directly connected to an interface.)
•
The outgoing interface for exported traffic must be Ethernet (10/100/1000). (Incoming (monitored) traffic can traverse any interface.)
Information About IP Traffic Export
To use the IP traffic export, you should understand the following concept:
•
Benefits of IP Traffic Export
Benefits of IP Traffic Export
Simplified Cisco IDS Deployment
Without the ability to export IP traffic, the Cisco Intrusion Detection System (Cisco IDS) probe must be inline with the network device to monitor traffic flow. IP traffic export eliminates the probe placement limitation, allowing users to place a Cisco IDS probe in any location within their network or direct all exported traffic to a VLAN that is dedicated for network monitoring. Allowing users to choose the optimal location of their Cisco IDS probe reduces processing burdens.
Also, because packet processing that was performed on the network device can now be performed away from the network device, the need to enable Cisco IDS with the Cisco IOS software is eliminated.
IP Traffic Export Functionality Benefits
Users can configure their router to perform the following tasks:
•
Filter copied packets using an access control list (ACL)
•
Filter copied packets via sampling, which allows you to export one in every few packets in which you are interested. Use this option when you do not need to export all incoming traffic. Also, sampling is useful when a monitored ingress interface can send traffic faster than the egress interface can transmit it.
•
Configure bidirectional traffic on an interface. (By default, only incoming traffic is exported or captured.)
How to Use IP Traffic Export
This section contains the following procedures:
•
Configuring IP Traffic Export (required)
•
Configuring IP Traffic Capture (required)
•
Displaying IP Traffic Export Configuration Data (required)
Configuring IP Traffic Export
Use this task to configure IP traffic export profiles, which enable IP traffic to be exported on an ingress interface and allow you to specify profile attributes, such as the outgoing interface for exporting traffic.
Note
Perform packet exporting before packet switching or filtering.
IP Traffic Export Profiles Overview
All packet export configurations are specified using IP traffic export profiles, which consist of IP-traffic-export-related command-line interfaces (CLIs) that control various attributes for both incoming and outgoing exported IP traffic. You can configure a router with multiple IP traffic export profiles. (Each profile must have a different name.) You can apply different profiles on different interfaces.
The two different IP traffic export profiles are as follows:
•
The global configuration profile, which is configured by the ip traffic-export profile command.
•
The IP traffic export submode configuration profile, which is configured by any of the following router IP Traffic Export (RITE) commands—bidirectional, incoming, interface, mac-address, and outgoing.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ip traffic-export profile profile-name
4.
interface interface-name
5.
bidirectional
6.
mac-address H.H.H
7.
incoming {access-list {standard | extended | named} | sample one-in-every packet-number}
8.
outgoing {access-list {standard | extended | named} | sample one-in-every packet-number}
9.
exit
10.
interface type number
11.
ip traffic-export apply profile-name
DETAILED STEPS
Troubleshooting Tips
Creating an IP Traffic Export Profile
The interface and mac-address commands are required to successfully create a profile. If these commands are not entered, you will receive the following profile incomplete message when you enter the show running config command:
ip traffic-export profile newone! No outgoing interface configured! No destination mac-address configuredApplying an IP Traffic Export Profile to an interface
The following system logging messages should appear immediately after you activate and deactivate a profile from an interface (via the ip traffic-export apply profile command):
•
Activated profile:
%RITE-5-ACTIVATE: Activated IP traffic export on interface FastEthernet 0/0.•
Deactivated profile:
%RITE-5-DEACTIVATE: Deactivated IP traffic export on interface FastEthernet 0/0.If you attempt to apply an incomplete profile to an interface, you will receive the following message:
Router(config-if)# ip traffic-export apply newoneRITE: profile newone has missing outgoing interfaceWhat to Do Next
After you configure a profile and enable the profile on an ingress interface, you can monitor IP traffic exporting events and verify your profile configurations. To complete these steps, see the "Displaying IP Traffic Export Configuration Data" section.
Configuring IP Traffic Capture
IP traffic export provides the capability to export IPO traffic over an Ethernet port. IP traffic capture provides the capability to capture IP packets in local router memory, and then dump this data to a file on an external device, such as flash memory.
IP traffic capture is supported on the Cisco 1841, Cisco 2800 series, and Cisco 3800 series integrated services routers.
The following sections describe the configuration and control of IP traffic capture:
•
Configuring IP Traffic Capture (required)
•
Performing IP Traffic Capture (required)
Configuring IP Traffic Capture
Perform the following steps to configure IP traffic capture.
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ip traffic-export profile profile-name mode capture
4.
bidirectional
5.
incoming {access-list {standard | extended | named} | sample one-in-every packet-number}
6.
outgoing {access-list {standard | extended | named} | sample one-in-every packet-number}
7.
length bytes
8.
exit
9.
interface type number
10.
ip traffic-export apply profile-name size size
DETAILED STEPS
Performing IP Traffic Capture
When traffic capture is configured, perform it using with CLI commands. There are commands to clear the capture buffer, to start and stop packet capture, and to copy the capture buffer to an external memory device. These commands are:
•
traffic-export interface type number clear
•
traffic-export interface type number start
•
traffic-export interface type number stop
•
traffic-export interface type number copy
Use these commands in privileged EXEC mode at your discretion to perform the following operations:
•
Clear the IP Traffic Capture Buffer
Clear the IP Traffic Capture Buffer
To clear the packet capture buffer for the designated interface, use the traffic-export interface clear command.
Start IP Traffic Capture
To initiate packet capture, use the traffic-export interface start command. This action will copy those packets designated in the traffic capture configuration into the internal capture buffer for the interface.
Stop IP Traffic Capture
To halt packet capture, use the traffic-export interface stop command.
Copy IP Traffic Capture
To copy the packet capture buffer to an external memory device, use the traffic-export interface copy command.
After you enter this command, an interactive dialog occurs.
Enter the name or address of the remote host containing the external memory device.
Address or name of remote host []? [name | address]Enter the name of the capture buffer file in the remote host.
Capture buffer filename []? filenameAn example of this dialog is:
Router# traffic-export interface fastethernet0/0 copy tftp:Address or name of remote host []? 172.18.207.15Capture buffer filename []? atmcaptureCopying capture buffer to tftp://172.18.207.15/atmcapture !!Displaying IP Traffic Export Configuration Data
This task allows you to verify IP traffic export parameters such as the monitored ingress interface, which is where the IP traffic is exported, and outgoing and incoming IP packet information, such as configured ACLs. You can also use this task to monitor packets that are captured and then transmitted across an interface to a destination host. Use this optional task to help you troubleshoot any problems with your exported IP traffic configurations.
SUMMARY STEPS
1.
enable
2.
debug ip traffic-export events
3.
show ip traffic-export [interface interface-name | profile profile-name]
DETAILED STEPS
Examples
The following sample output from the show ip traffic-export command is for the profile "one." This example is for a single, configured interface. If multiple interfaces are configured, the information below is displayed for each interface.
Router# show ip traffic-exportRouter IP Traffic Export Parameters
Monitored Interface FastEthernet0/0
Export Interface FastEthernet0/1
Destination MAC address 0030.7131.abfc
bi-directional traffic export is off
Input IP Traffic Export Information Packets/Bytes Exported 0/0
Packets Dropped 0
Sampling Rate one-in-every 1 packets
No Access List configuredProfile one is ActiveConfiguration Examples for IP Traffic Export
This section includes the following configuration examples:
•
Exporting IP Traffic Configuration: Example
•
Capturing IP Traffic Configuration: Example
Exporting IP Traffic Configuration: Example
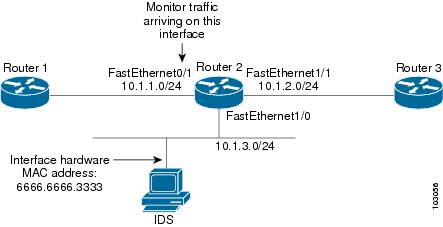
Figure 1 and the following sample output from the show running-config command illustrate how to configure Router 2 to export the incoming traffic from Router 1 to Cisco IDS:
Figure 1 Traffic Export Example
Router2# show running-configBuilding configuration...Current configuration :2349 bytes! Last configuration change at 20:35:39 UTC Wed Oct 8 2003! NVRAM config last updated at 20:35:39 UTC Wed Oct 8 2003!version 12.3service timestamps debug uptimeservice timestamps log uptimeno service password-encryptionservice internalservice udp-small-servers!hostname rite-3745!boot system flash:c3745-js-mz.123-1.8.PI2dno logging consoleenable password lab!no aaa new-modelip subnet-zero!no ip domain lookup!ip cef!ip traffic-export profile my_riteinterface FastEthernet1/0mac-address 6666.6666.3333!interface FastEthernet0/0ip address 10.0.0.94 255.255.255.0duplex autospeed auto!interface FastEthernet0/1ip address 10.1.1.2 255.255.255.0duplex autospeed autoip traffic-export apply my_rite!interface FastEthernet1/0ip address 10.1.3.2 255.255.255.0no ip redirectsno cdp enable!interface FastEthernet1/1ip address 10.1.2.2 255.255.255.0duplex autospeed auto!router ospf 100log-adjacency-changesnetwork 10.1.0.0 0.0.255.255 area 0!ip http serverip classless!snmp-server engineID local 0000000902000004C1C59140snmp-server community public ROsnmp-server enable traps tty!control-plane!dial-peer cor custom!gateway!line con 0exec-timeout 0 0stopbits 1line aux 0line vty 0 4password lablogin!ntp clock-period 17175608ntp server 10.0.0.2!endCapturing IP Traffic Configuration: Example
The following sample output from the show running-config command also refers to Figure 1. It illustrates how to configure Router 2 to locally capture the incoming traffic from Router 1, rather than export it.
Router2# show running-configBuilding configuration...Current configuration :2349 bytes! Last configuration change at 20:35:39 UTC Wed Oct 8 2003! NVRAM config last updated at 20:35:39 UTC Wed Oct 8 2003!version 12.3service timestamps debug uptimeservice timestamps log uptimeno service password-encryptionservice internalservice udp-small-servers!hostname rite-3745!boot system flash:c3745-js-mz.123-1.8.PI2dno logging consoleenable password lab!no aaa new-modelip subnet-zero!no ip domain lookup!ip cef!ip traffic-export profile my_rite mode capturelength 512!interface FastEthernet0/0ip address 10.0.0.94 255.255.255.0duplex autospeed auto!interface FastEthernet0/1ip address 10.1.1.2 255.255.255.0duplex autospeed autoip traffic-export apply my_rite size 10000000!interface FastEthernet1/0ip address 10.1.3.2 255.255.255.0no ip redirectsno cdp enable!interface FastEthernet1/1ip address 10.1.2.2 255.255.255.0duplex autospeed auto!router ospf 100log-adjacency-changesnetwork 10.1.0.0 0.0.255.255 area 0!ip http serverip classless!snmp-server engineID local 0000000902000004C1C59140snmp-server community public ROsnmp-server enable traps tty!control-plane!dial-peer cor custom!gateway!line con 0exec-timeout 0 0stopbits 1line aux 0line vty 0 4password lablogin!ntp clock-period 17175608ntp server 10.0.0.2!endAdditional References
The following sections provide references related to IP Traffic Export.
Related Documents
Standards
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature.
—
MIBs
RFCs
No new or modified RFCs are supported by this feature, and support for existing RFCs has not been modified by this feature.
—
Technical Assistance
Command Reference
This section documents new and modified commands only.
ip traffic-export apply
To apply an IP traffic export profile or an IP traffic capture profile to a specific interface, use the ip traffic-export apply profile command in interface configuration mode. To remove an IP traffic export profile or an IP traffic capture profile from an interface, use the no form of this command.
ip traffic-export apply profile-name
no ip traffic-export apply profile-name
Cisco 1841, Cisco 2800 Series, and Cisco 3800 Series
ip traffic-export apply profile-name size size
no ip traffic-export apply profile-name
Syntax Description
Defaults
If you do not use this command, a sucessfully configured profile is not active.
Command Modes
Interface configuration
Command History
Usage Guidelines
After you configure at least one export profile, use the ip traffic-export apply profile command to activate IP traffic export on the specified ingress interface.
After you configure a capture profile, use the ip traffic-export apply profile command to activate IP traffic capture on the specified ingress interface, and to specify the size of the local capture buffer.
Examples
The following example shows how to apply the export profile "corp1" to interface Fast Ethernet 0/0.
Router(config)# ip traffic-export profile corp1Router(config-rite)# interface FastEthernet 0/1Router(config-rite)# bidirectionalRouter(config-rite)# mac-address 00a.8aab.90a0Router(config-rite)# outgoing sample one-in-every 50Router(config-rite)# incoming access-list spam_aclRouter(config-rite)# exitRouter(config)# interface FastEthernet 0/0Router(config-if)# ip traffic-export apply corp1The following example shows how to apply the capture profile "corp2" to interface Fast Ethernet 0/0, and specify a capture buffer of 10,000,000 bytes.
Router(config)# ip traffic-export profile corp2 mode_captureRouter(config-rite)# bidirectionalRouter(config-rite)# outgoing sample one-in-every 50Router(config-rite)# incoming access-list ham_aclRouter(config-rite)# length 512Router(config-rite)# exitRouter(config)# interface FastEthernet 0/0Router(config-if)# ip traffic-export apply corp2 size 10000000After a profile is activated on the interface, a logging message such as the following will appear:
%RITE-5-ACTIVATE: Activated IP traffic export on interface FastEthernet 0/0.After a profile is removed from the interface, a logging message such as the following will appear:
%RITE-5-DEACTIVATE: Deactivated IP traffic export on interface FastEthernet 0/0.If you attempt to apply an incomplete profile to an interface, you will receive the following message:
Router(config-if)# ip traffic-export apply newoneRITE: profile newone has missing outgoing interfaceRelated Commands
ip traffic-export profile
To create or edit an IP traffic export profile or an IP traffic capture profile and enable the profile on an ingress interface, use the ip traffic-export profile command in global configuration mode. To remove an IP traffic export profile from your router configuration, use the no form of this command.
ip traffic-export profile profile-name
no ip traffic-export profile profile-name
Cisco 1841, Cisco 2800 Series, and Cisco 3800 Series Routers
ip traffic-export profile profile-name mode_capture
no ip traffic-export profile profile-name
Syntax Description
profile-name
IP traffic export profile name.
mode_capture
Optional. Creates an IP traffic capture profile.
Defaults
A profile does not exist.
Command Modes
Global configuration
Command History
Usage Guidelines
The ip traffic-export profile command allows you to begin a profile that can be configured to capture or export IP packets as they arrive on or leave from a selected router ingress interface.
When exporting IP packets, a designated egress interface exports IP packets out of the router. So, the router can export unaltered IP packets to a directly connected device.
When capturing IP packets, the packets are stored in local router memory. They may then be dumped to an external device.
IP Traffic Export Profiles
All exported IP traffic configurations are specified by profiles, which consist of RITE-related command-line interface (CLI) commands that control various attributes of both incoming and outgoing IP traffic. You can configure a router with multiple profiles. (Each profile must have a different name.) You can apply different profiles on different interfaces.
The two profiles to configure are:
•
Global configuration profile, which you configure using the ip traffic-export profile command.
•
Submode configuration profile, which you configure using any of the following RITE commands—bidirectional, incoming, interface, mac-address, and outgoing.
Use interface and mac-address commands to successfully create a profile. If you do not issue these commands, the user will receive a profile incomplete messages such as the following:
ip traffic-export profile newone! No outgoing interface configured! No destination mac-address configuredAfter you configure your profiles, you can apply the profiles to an interface with the ip traffic-export apply profile command, which will activate it.
IP Traffic Capture Profiles
On the Cisco 1841, Cisco 2800 series, and Cisco 3800 series routers, you can also configure IP traffic capture. A captured IP traffic configuration is specified by a profile, which consists of RITE-related command-line interface (CLI) commands that control various attributes of both incoming and outgoing IP traffic.
The two profiles that you should configure are:
•
Global configuration profile, which you configure using the ip traffic-export profile mode_capture command.
•
Submode configuration profile, which you configure using any of the following RITE commands—bidirectional, incoming, length, and outgoing.
After you configure your profiles, you can apply the profiles to an interface with the ip traffic-export apply profile command, which will activate it.
When the IP traffic capture profile is applied to an interface, use the traffic-export command to control the capture of the traffic.
Examples
The following example shows how to configure the profile "corp1," which sends captured IP traffic to host "00a.8aab.90a0" at the interface "FastEthernet 0/1." This profile is also configured to export 1 in every 50 packets and to allow incoming traffic only from the access control list (ACL) "ham_ACL."
Router(config)# ip traffic-export profile corp1Router(config-rite)# interface FastEthernet 0/1Router(config-rite)# bidirectionalRouter(config-rite)# mac-address 00a.8aab.90a0Router(config-rite)# outgoing sample one-in-every 50Router(config-rite)# incoming access-list ham_aclRouter(config-rite)# exitRouter(config)# interface FastEthernet 0/0Router(config-if)# ip traffic-export apply corp1The following example shows how to configure the profile "corp2," which captures IP traffic and stores it in a local router memory buffer of 10,000,000 bytes. This profile also captures 1 in every 50 packets and allows incoming traffic only from the access control list (ACL) "ham_ACL."
Router(config)# ip traffic-export profile corp2 mode_captureRouter(config-rite)# bidirectionalRouter(config-rite)# outgoing sample one-in-every 50Router(config-rite)# incoming access-list ham_aclRouter(config-rite)# length 512Router(config-rite)# exitRouter(config)# interface FastEthernet 0/0Router(config-if)# ip traffic-export apply corp2 size 10000000Related Commands
length (RITE)
To specify the length the captured portion of the packets being captured in IP traffic export capture mode, use the length command in RITE configuration mode. To return to the default condition of capturing entire packets, use the no form of this command.
length bytes
no length
Syntax Description
bytes
The length in bytes of the packet captured in IP traffic export capture mode. Acceptable values are 128, 256, and 512.
Command Default
When you do not use this command, the entire packet is captured.
Command Modes
RITE configuration
Command History
Usage Guidelines
Use this command to limit the length of the portion of the packets being captured in IP traffic export capture mode. The captured portion of the packets are limited to 128, 256, or 512 bytes. If you do not use the length command, entire packets are captured.
Examples
The following example shows the use of the length command in the configuration of IP traffic export capture mode profile "corp2":
Router(config)# ip traffic-export profile corp2 mode_captureRouter(config-rite)# bidirectionalRouter(config-rite)# outgoing sample one-in-every 50Router(config-rite)# incoming access-list ham_aclRouter(config-rite)# length 512Router(config-rite)# exitRouter(config)# interface FastEthernet 0/0Router(config-if)# ip traffic-export apply corp2 size 10000000Related Commands
traffic-export
To control the operation of IP traffic capture mode in IP traffic export, use the traffic-export command in privileged EXEC mode.
traffic-export interface type number { start | stop | clear | copy memory-device }
Syntax Description
Command Default
This command has no defaults.
Command Modes
Privileged EXEC.
Command History
Usage Guidelines
Use the traffic-export command to control the operation of IP traffic capture mode in IP traffic export. The operator uses CLI commands to start or stop capture of packets flowing across a monitored interface, to copy the captured packets to an external memory device, or to clear the internal buffer which holds the captured packets.
Examples
The following example illustrates the use of the traffic-export command to initiate the capture of packets on interface FastEthernet 0/0.
Router# traffic-export interface fastethernet 0/0 start%RITE-5-CAPTURE_START: Started IP traffic capture for interface FastEthernet0/0router#The following example illustrates the use of the traffic-export command to halt the packet capture sequence on interface FastEthernet 0/0.
Router# traffic-export interface fastethernet 0/0 stop%RITE-5-CAPTURE_STOP: Stopped IP traffic capture for interface FastEthernet0/0router#The following example illustrates the use of the traffic-export command to copy the contents of the packet capture buffer to an external memory device. The example of the interactive dialog identifies the external memory device and the remote host in which it resides.
Router# traffic-export interface fastethernet0/0 copy tftp:Address or name of remote host []? 172.18.207.15Capture buffer filename []? atmcaptureCopying capture buffer to tftp://172.18.207.15/atmcapture !!router#The following example illustrates the use of the traffic-export command to clear the packet capture buffer that is in local memory.
Router# traffic-export interface fastethernet 0/0 clear%RITE-5-CAPTURE_CLEAR: Cleared IP traffic capture buffer for interface FastEthernet0/0router#Related Commands
Feature Information for IP Traffic Export
Table 1 lists the release history for this feature.
Not all commands may be available in your Cisco IOS software release. For release information about a specific command, see the command reference documentation.
Use Cisco Feature Navigator to find information about platform support and software image support. Cisco Feature Navigator enables you to determine which Cisco IOS and Catalyst OS software images support a specific software release, feature set, or platform. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Note
Table 1 lists only the Cisco IOS software release that introduced support for a given feature in a given Cisco IOS software release train. Unless noted otherwise, subsequent releases of that Cisco IOS software release train also support that feature.
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2006 Cisco Systems, Inc. All rights reserved.