Feedback Feedback
|
Table Of Contents
Installation and Configuration for Common Criteria EAL2 Evaluated Cisco IOS IPSec
Supported Hardware and Software Versions
Supported Hardware Documentation
Organizational Security Policy
Security Implementation Considerations
Remote Administration and Management
Verification of Image and Hardware IPSec Module
Hardware Versions of Hardware IPSec VPN Modules
MD5 Hash Values for Cisco IOS Software Images
Obtaining Technical Assistance
Contacting TAC by Using the Cisco TAC Website
Installation and Configuration for Common Criteria EAL2 Evaluated Cisco IOS IPSec
January 2007This document describes how to install and configure Cisco IOS routers in accordance with the Common Criteria Evaluation Assurance Level 2 (EAL2) evaluated Cisco IOS IP Security (IPSec).
Note
Any changes to the information provided in this document will result in noncompliance between the Cisco IOS router and the Cisco IOS IPSec evaluation and may make the router insecure.
This document includes the following sections:
•
Supported Hardware and Software Versions
•
Hardware Versions of Hardware IPSec VPN Modules
•
MD5 Hash Values for Cisco IOS Software Images
•
Obtaining Technical Assistance
Introduction
This document is an addendum to the Cisco IOS Release 12.2 and 12.4 documentation sets, which should be read prior to configuring a Cisco IOS router in accordance with the Common Criteria Evaluation Assurance Level 2 (EAL2) evaluated Cisco IOS IPSec.
Cisco product documentation includes
•
Configuration Guides, which provide a descriptive overview of functions, the commands needed to enable them, and the sequence of operations that should be followed to implement them. The configuration guide should be consulted first when enabling features and functions.
•
Command References, which provide a complete and detailed summary of all configuration commands and options, their effects, and examples and guidelines for their use. The command references should be consulted to confirm detailed syntax and functionality options.
•
Error Message summaries, which describe all error messages issued by the product.
When this guide refers to a Cisco document, the title is listed and the filename (as available on www.cisco.com) is provided in brackets. The following Cisco IOS Release 12.2 and 12.4 documentation is referenced by this document:
•
Regulatory Compliance and Safety Information specific to each router platform (Table 2)
•
Hardware Installation Guides for each router platform (Table 4)
•
Cisco IOS Configuration Fundamentals Configuration Guide, Release 12.2 (fcfbook.pdf)
•
Cisco IOS Configuration Fundamentals Configuration Guide, Release 12.4, File Management, Loading and Maintaining System Images (cfh900.pdf)
•
Cisco IOS Security Configuration Guide, Release 12.4, Part 4: Implementing IPSec and IKE, "Configuring Internet Key Exchange for IPSec VPNs" (sec_ike.pdf)
•
Cisco IOS Security Configuration Guide, Release 12.4, Part 4: Implementing IPSec and IKE, "Configuring Security for VPNs with IPSec" (sec_ipse.pdf)
•
Cisco IOS Security Configuration Guide, Release 12.4, Part 3: Traffic Filtering, Firewalls, and Virus Detection, "Access Control Lists: Overview and Guidelines" (schacls.pdf)
•
Cisco IOS IP Application Services Command Reference, Release 12.4 (apl_bokh.pdf)
•
Cisco IOS IP Application Services Command Reference, Release 12.2SR (iap_a1sr.pdf)
•
Cisco IOS Network Management Configuration Guide, Release 12.4, Part 3: System and Network Management, "Troubleshooting and Fault Management" (fcf013.pdf)
•
Cisco IOS Security Configuration Guide, Release 12.4, Part 1: Authentication, Authorization, and Accounting (AAA), "Configuring Authentication, Configuring Authentication" (schathen.pdf)
•
Cisco IOS Network Management Configuration Guide, Release 12.4, Part 3: System and Network Management, "Performing Basic System Management" (fcf012.pdf)
Cisco IOS documentation is available on CD-ROM, in printed-paper form, and online (in both HTML and PDF formats). This document may be used in conjunction with the August 2006 Cisco IOS IPSec Evaluation Documentation DVD-ROM available upon request from Cisco Systems by sending an email to CC-Doc-Request@cisco.com.
The Cisco IOS documents listed above can also be found online at: http://www.cisco.com/univercd/cc/td/doc/product/software/ios124/index.htm
http://www.cisco.com/univercd/cc/td/doc/product/software/ios122sr/index.htm
Audience
This document is written for administrators configuring a Cisco IOS router in accordance with the Common Criteria evaluated Cisco IOS IPSec. This document assumes you are familiar with networks and network terminology, that you are a trusted individual, and that you have been trained for use with IPSec technology and its applications; for example, site-to-site Virtual Private Networks (VPNs). There are no components of the Cisco IP System that are accessible to non-administrative users (end-users), and hence there is no user-level documentation.
Supported Hardware and Software Versions
The hardware and software combinations that are complaint with Common Criteria evaluated Cisco IOS IPSec are outlined in Table 1. To display the hardware version of an IPSec/VPN Hardware module, use the show diag command.
Table 1 Supported Hardware and Software for the Common Criteria Evaluated Cisco IOS IPSec
Cisco 800 series
871, 876, 877, 878, 851, 851W, 857, 857W
Built In
Cisco IOS 12.4(6)T3
Cisco 1800 series
1841
optionally with AIM-VPN/BPII-PLUS
Cisco IOS 12.4(7)
1801, 1802, 1803, 1811, 1812
Built In
Cisco IOS 12.4(6)T3
Cisco 2800 series
2801,2811, 2821, 2851
optionally with AIM-VPN/EPII-PLUS
Cisco IOS 12.4(7)
Cisco 3800 series
3825
optionally with AIM-VPN/EPII-PLUS
Cisco IOS 12.4(7)
3845
optionally with AIM-VPN/HPII-PLUS
Cisco IOS 12.4(7)
Cisco 7200 series
7204, 7206
SA-VAM2+
Cisco IOS 12.4(7)
Cisco 7300 series
7301
SA-VAM2+
Cisco IOS 12.4(7)
Cisco 7600
Catalyst 6500
Any 6500 or 7600 with Supervisor Engine 720, 720-3B, or 720-3BXL
SPA-IPSEC-2G
Cisco IOS 12.2(33)SRA
1 Support for RSA public/private key pairs for IKE authentication requires the use of an IPSec hardware acceleration module. Models listed as using "Built In" modules do not support RSA public/private key pairs for IKE authentication.
Security Information
This section contains the following sections:
•
Supported Hardware Documentation
•
Organizational Security Policy
•
Security Implementation Considerations
Supported Hardware Documentation
In addition to the regulatory compliance documentation for each hardware platform listed in Table 2, the sections that follow provide additional security information for use with a Common Criteria evaluation Cisco IOS IPSec router.
Organizational Security Policy
Ensure that your Cisco IOS Router is delivered, installed, managed, and operated in a manner that maintains an organizational security policy for IPSec protected traffic. The organizational security policy must describe
•
Which networks are to be considered trusted and untrusted
•
The traffic flows between trusted networks that must be protected using IPSec to provide confidentiality, authenticity and integrity, in terms of source/destination IP address and/or port number
•
The Cisco IOS routers associated with each trusted network that provide IPSec services to the identified traffic flows
The administrator must identify which interfaces on the Cisco IOS Router are to be considered untrusted and trusted. An untrusted interface is one that is connected to an untrusted network over which the administrator wishes to send and receive trusted traffic protected by IPSec encryption.
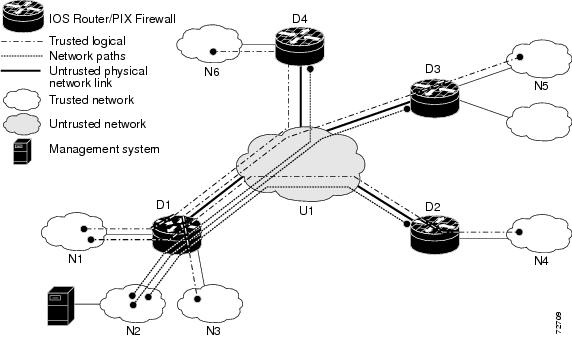
Figure 1 Organizational Security Policy Example
Figure 1 displays an organizational security policy with traffic flows that are identified solely by source and destination IP addresses. All Cisco IOS routers (D1, D2, D3, and D4) must be configured to implement a portion of the organizational security policy. For example, Router D1 has three trusted networks attached to it (N1, N2, and N3); this router implements a policy for the three trusted network-to-network flows and three secure management flows that cross the untrusted network (U1). (The policy that Router D1 implements is outlined in Table 3.)
Table 3 Policy for Cisco IPSec System Example
N1
N6
D4
N1
N5
D3
N3
N4
D2
N2
D2
D2
N2
D3
D3
N2
D4
D4
All other routers (D2, D3, D4) must have a matching configuration to implement the organizational security policy. Each of the rows in Table 3 is configured on the Cisco IOS router as an IPSec tunnel.
An organizational security policy may implement a site-to-site VPN between multiple locations (trusted networks) over the Internet (an untrusted network), or it may specify that all LAN traffic (trusted networks) be encrypted when transmitted over any WAN link (untrusted network).
Security Implementation Considerations
The following sections provide implementation considerations that need to be addressed to administer Cisco IOS routers in a secure manner that is consistent with Common Criteria evaluated Cisco IOS IPSec:
•
Remote Administration and Management
•
SNMP
Evaluated Configuration
Only the hardware and software version combinations that are described in Table 1 can be used to implement an evaluated configuration. You will invalidate the evaluated status of a particular hardware platform if you change the software to a different version.
The Common Criteria Target of Evaluation (TOE) for Cisco IOS IPSec defines only the following features:
•
IPSec IKE using preshared keys, RSA keys1 , or digital certificates
Note
The AIM-VPN/BPII, AIM-VPN/EPII, AIM-VPN/HPII, and VAM2 do not support IKE with RSA keys for IKE authentication.
•
IPSec encapsulating security payload (ESP) using tunnel or transport mode with Data Encryption Standard (DES) or 3DES
•
Hardware acceleration of IPSec (as specified in Table 1)
•
Cryptographic key generation and management
•
Inbound access lists
•
Message logging
•
User authentication for access to the command-line interface (CLI) using locally configured accounts
•
Time management
All other hardware and software features and functions of a Cisco IOS router are outside the scope of this evaluated product configuration, and therefore can be used in conjunction with the TOE functions only if the TOE functions are configured, operated, and managed in accordance with this document.
To ensure that the Cisco IOS router configuration continues to meet the organizational security policy, you should review your router configurations for the following possible changes:
•
Changes in the Cisco IOS router configuration
•
Changes in the organizational security policy
•
Changes in the threats presented from untrusted networks
•
Changes in the administration and operation staff or of the physical environment of the Cisco IOS router
Physical Security
The Cisco IOS router must be located in a physically secure environment in which only a trusted administrator has access. The secure configuration of a Cisco IOS router can be compromised if an intruder gains physical access to the router.
Certificate Authority
If digital certificates are used to provide authentication between evaluated Cisco IOS IPSec routers, the certificate authority that issues the certificates must be trusted or evaluated to the same level as Cisco IOS IPSec (Common Criteria EAL2).
Time Sources
Routers configured in accordance with the Cisco IOS IPSec evaluation must timestamp system log messages. For Cisco routers without internal real time hardware clocks (800 series) their software clock must be set from an external time source via the Network Time Protocol (NTP). NTP servers must be connected to a trusted network in a secure location to be able to provide a trusted time source for the TOE.
Access Control
The Cisco IOS Router must be configured to authenticate both unprivileged and privileged (enable mode) access to the CLI using a username and password. A good password has a combination of alphabetic and numeric characters as well as punctuation characters. This password must be at least eight characters long. We recommend that you tell the password to someone who is in a position of trust.
Remote Administration and Management
If you administer and manage the Cisco IOS router from a remote management system across an untrusted network, the following requirements apply:
•
The management station must be connected to a trusted network.
•
There must be another Cisco IOS router connected to the trusted and untrusted network.
•
There must be an IPSec tunnel between the trusted network and the Cisco IOS router that is managed.
A topology, such as Figure 1, that displays these requirements, applies to any in-band administrative protocol including Telnet, Simple Network Management Protocol (SNMP), and syslog.
SNMP
The operation of the TOE can be modified via SNMP, if SNMP read-write access is permitted. Therefore if SNMP is enabled on the TOE, to support monitoring of the Cisco IOS router, it must explicitly be configured in read-only mode.
Logging and Messages
Monitoring activity in the log files is an important aspect of your network security and should be conducted regularly. Monitoring the log files allows you take appropriate and timely action when you detect breaches of security or events that are likely to lead to a potential security breach.
To view log file messages, use the show logging EXEC command. For configuration details, refer to the section "Message Logging" in Table 6.
Access Lists
The access-list command operates on a first match basis. Therefore, the last rule added to the access list is the last rule checked. The administrator should make a note of the last rule during initial configuration because it may impact the remainder of the rule parsing.
To enable logging of access-list matches, the log keyword should be used with access-list definitions.
Monitoring and Maintenance
There are several ways (from logs to messages) in which you can monitor the operation of your Cisco IOS routers. However, ensure you know how you will monitor the router for performance and possible security issues. Also, plan your backups; if there should be hardware or software problems, you may need to restore the router configuration.
Installation Notes
Table 4 lists the documentation that should be used when installing a Cisco IOS IPSec evaluated router.
Verification of Image and Hardware IPSec Module
To verify that the Cisco IOS software and hardware IPSec VPN module (if used) has not been tampered with during delivery, perform the following steps.
Note
If a hardware IPSec VPN module is not being used, only steps 6 and 7 are necessary.
Note
Hardware IPSec VPN modules are delivered either as separate discrete items or preinstalled in a Cisco router platform.
Step 1
Inspect the physical packaging in which the equipment was delivered before unpacking the hardware IPSec VPN module.
•
Verify that the external cardboard packing is printed with the Cisco Systems logo and motifs. If the external packaging is not printed with Cisco branding, contact the equipment supplier (Cisco Systems or an authorized Cisco distributor or partner).
Step 2
Verify that the packaging has not been opened and resealed by examining the tape that seals the package. If the package appears to have been resealed, contact the equipment supplier.
Step 3
Verify that the box has a white tamper-resistant, tamper-evident Cisco Systems bar-coded label that is applied to the external cardboard box. (This label will include the Cisco product number, serial number, and other information regarding the contents of the box.) If this label is missing, contact the equipment supplier.
Step 4
Note the serial number of the hardware IPSec VPN module on the shipping documentation. If the hardware IPSec VPN module has been preinstalled, the white label on the outer box will show the serial number of the router platform inside; thus, the serial number of the hardware IPSec VPN module will appear on the shipping documents also attached to the outer box. Otherwise, if the VPN has not been preinstalled, the serial number of the hardware IPSec VPN module will be displayed on the white label.
Ensure that the serial number on the shipping documentation matches the serial number on the separately mailed invoice for the equipment. If the serial numbers do not match, contact the equipment supplier.Step 5
Verify that the box has indeed been shipped from the expected supplier of the equipment (Cisco Systems or an authorized Cisco distributor/partner) by performing the following tasks:
•
Contact the supplier to verify that the box was shipped with the courier company that delivered the box and that the consignment note number for the shipment matches the number used for the delivery.
•
Verify that the serial numbers of the items shipped match the serial numbers of the items delivered. For equipment shipped directly from Cisco, you can verify the serial numbers online through the Order Status Tool (requires a cisco.com login). The Order Status Tool can be accessed from http://cco.cisco.com/en/US/partner/ordering/index.shtml or directly via http://cco.cisco.com/cgi-bin/status. For other suppliers, verify that the serial numbers match by using a mechanism that was not involved in the actual equipment delivery; for example, use the phone, fax, or another online tracking service.
Step 6
Inspect the module after the hardware IPSec VPN module has been unpacked. Verify that the serial number displayed on the module matches the serial number on the shipping documentation and the invoice. If the serial numbers do not match, contact the equipment supplier.
Step 7
Download a Common Criteria evaluated software image file from cisco.com for your specific hardware platform onto a trusted computer system (as specified in Table 1). For all images, ensure that you have sufficient system and Flash memory to support the image on your router hardware by checking the release notes appropriate for the Cisco IOS release and by selecting the appropriate feature set as listed in Table 10.
Software images are available from Cisco.com at the following URL:
http://cco.cisco.com/kobayashi/library/12.4/index.shtml
http://cco.cisco.com/kobayashi/library/12.2/index.shtml
Step 8
After you have downloaded the file, verify that the file has not been tampered with by using a Message Digest 5 (MD5) utility to compute an MD5 hash for the file; compare this MD5 hash with the MD5 hash for the image, which is listed in Table 9. If the MD5 hashes do not match, contact Cisco Technical Support.
Step 9
Install the downloaded and verified software image onto your Cisco IOS router. For information on completing this task, refer to the chapter "Loading and Maintaining System Images" in the part File Management" of the Cisco IOS Configuration Fundamentals and Network Management Configuration Guide.
Step 10
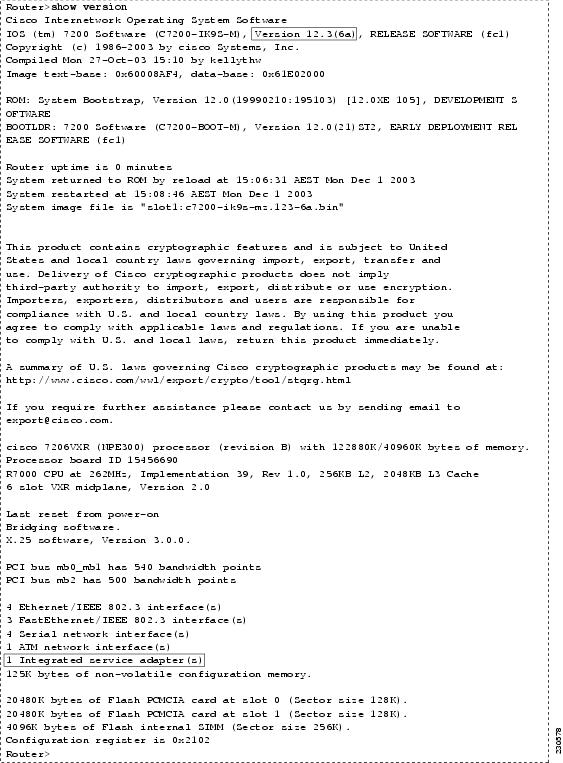
Start your router as described in the appropriate installation documentation that is outlined in Table 4. Confirm that your router loads the image correctly, completes internal self-checks, and displays the cryptographic export warning on the console. At the prompt, type the show version command. (See Figure 2.) Verify that the version matches one of the valid versions listed in Table 1. If the versions do not match or if the image fails to load, contact Cisco Technical Support.
Step 11
If the hardware IPSec VPN module has not been preinstalled, refer to one of the installation guides in Table 4.
Step 12
After the IPSec VPN module is installed, restart the router. At the prompt, enter the show version command. (See Figure 2.) To verify that a VPN module is installed, read the output display. If the output display does not report that the hardware IPSec VPN module is present, contact Cisco Technical Support.
Step 13
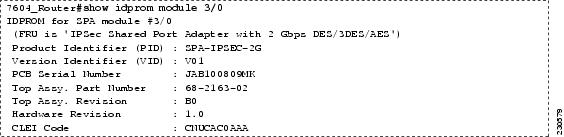
Enter the show diag command for the Cisco 800, 1800, 2800, 3800, 7200 and 7300 series routers; enter the show idprom module module (for example 3/0) (see Figure 3) for the Cisco 6500 and 7500 series routers. Examine the output to verify that the serial number reported by the hardware IPSec VPN module is the same as the serial number on the shipping documentation and invoice (see Step 4), and displayed on the hardware IPSec VPN module itself (see Step 5). At the same time, verify that the hardware version and revision of the module are listed in Table 9.
Figure 2 Sample show version Output That Shows the Cisco IOS Version and Presence of the Hardware IPSec VPN Module
Figure 3 Sample show idprom module 3/0 Output That Shows the IPSec VPN Module Serial Number
Configuration Notes
The Common Criteria TOE for Cisco IOS IPSec defines the following two groups of features:
–
IPSec IKE using pre-shared keys, RSA keys or digital certificates
–
IPSec ESP using tunnel or transport mode with 3DES or AES
–
Hardware acceleration of IPSec (see Table 1)
–
Cryptographic key generation and management
–
Inbound access-lists
–
Message logging
–
User authentication for access to the Command Line Interface using locally configured accounts
–
Time management
Note
Upon delivery, a Cisco IOS router is not configured to support any of these security enforcing or supporting functions. To ensure that your router is operating in accordance with Common Criteria evaluated Cisco IOS IPSec, these functions must be explicitly configured as described in this document and in the appropriate product documentation.
Security Enforcing
Security enforcing features should be configured as described in the following sections of the Cisco IOS Security Configuration Guide
–
Configuring Internet Key Exchange for IPSec VPNs (sec_ike.pdf)
–
Configuring Security for VPNs with IPSec (sec_ipse.pdf)
To ensure that your Cisco IOS router configuration is consistent with Common Criteria evaluated Cisco IOS IPSec, you must consider the IPSec options listed in Table 5.
Security Supporting
Table 6 lists the documents that you should use to configure security supporting functions.
Table 6 Documentation for Evaluated Security Supporting Functions
Inbound access lists
The chapter "Access Control Lists: Overview and Guidelines" (schacls.pdf) in the part "Traffic Filtering and Firewalls" of the Cisco IOS Security Configuration Guide
Specific commands available as follows:
Cisco IOS IP Application Services Command Reference, Release 12.4 (apl_bokh.pdf)
Cisco IOS IP Application Services Command Reference, Release 12.2SR (iap_a1sr.pdf)
Message logging
The chapter "Troubleshooting and Fault Management" (fcf013.pdf) in the section "System and Network Management" of the Cisco IOS Network Management Configuration Guide
User authentication
The chapter "Configuring Authentication" (schathen.pdf) in the part "Configuring Authentication, Authorization, and Accounting (AAA)" of the Cisco IOS Security Configuration Guide
Time management
The chapter "Performing Basic System Management" (fcf012.pdf) in the part "System and Network Management" of the Cisco IOS Network Management Configuration Guide
Saving Configurations
When making changes to the configuration of the router, use the write memory command frequently. If the router reboots and resumes operation when uncommitted changes have been made, these changes will be lost and the router will revert to the last configuration saved.
Enabling Time Stamps
By default, all audit records are not stamped with the time and date, which are generated from the system clock when an event occurs.
The Common Criteria evaluated Cisco IOS IPSec requires that the time-stamp feature be enabled on your Cisco IOS router. To enable the time stamp of audit events, use the service timestamps log datetime command.
To ensure that the timestamps option is meaningful, the system clock in your router must be set correctly. (See the following section, "Setting the System Clock," for more information.)
Setting the System Clock
To provide accurate time stamps for logging and to ensure that your router can process validity dates for digital certificates, the system clock must be set. Some models of Cisco IOS routers have real-time clocks that maintain real time when the router is powered down; these real-time clocks are used to initialize the system clock at startup. Other models of Cisco IOS routers do not have a real-time clock and must obtain the correct date and time from a reliable time source using the NTP. One example of a reliable time source is a Cisco IOS router with a real-time clock operating as an NTP Server. Table 7 lists router clock functions for use with Cisco IOS IPSec.
Table 7 Cisco IOS Router Clock Functions
Cisco 800 series
No
NTP client
The chapter "Performing Basic System Management" (fcf012.pdf) in the part "System and Network Management" of the Cisco IOS Network Management Configuration Guide
Cisco 1800 series Cisco 2800series Cisco 3800 series Cisco 7200s eries Cisco 7300 series Cisco 7600 series Cisco 6500 series
Yes
Internal; can be NTP server
Hardware Versions of Hardware IPSec VPN Modules
Table 8 lists the hardware versions of IPSec VPN modules.
MD5 Hash Values for Cisco IOS Software Images
Table 9 lists the MD5 hash values for Cisco IOS software images.
Related Documentation
Use this document in conjunction with the appropriate Cisco IOS software documentation, which can be found at the following location:
Documentation for Cisco IOS Release 12.4:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios124/index.htmDocumentation for Cisco IOS Release 12.2SR:
http://www.cisco.com/univercd/cc/td/doc/product/software/ios122sr/index.htmObtaining Documentation
The following sections provide sources for obtaining documentation from Cisco Systems.
World Wide Web
You can access the most current Cisco documentation on the World Wide Web at the following sites:
Documentation CD-ROM
Cisco documentation and additional literature are available in a CD-ROM package, which ships with your product. The Documentation CD-ROM is updated monthly and may be more current than printed documentation. The CD-ROM package is available as a single unit or through an annual subscription.
Ordering Documentation
Cisco documentation can be ordered in the following ways:
•
Registered Cisco Direct Customers can order Cisco product documentation from the Networking Products MarketPlace:
http://www.cisco.com/web/ordering/root/index.html
•
Registered Cisco.com users can order the Documentation CD-ROM through the online Subscription Store:
http://www.cisco.com/go/subscription
•
Nonregistered Cisco.com users can order documentation through a local account representative by calling Cisco corporate headquarters (California, USA) at 408 526-7208 or, in North America, by calling 800 553-NETS(6387).
Documentation Feedback
If you are reading Cisco product documentation on the World Wide Web, you can submit technical comments electronically. Click Feedback in the toolbar and select Documentation. After you complete the form, click Submit to send it to Cisco.
You can e-mail your comments to bug-doc@cisco.com.
To submit your comments by mail, use the response card behind the front cover of your document, or write to the following address:
Cisco Systems, Inc.
Document Resource Connection
170 West Tasman Drive
San Jose, CA 95134-9883We appreciate your comments.
Obtaining Technical Assistance
Cisco provides Cisco.com as a starting point for all technical assistance. Customers and partners can obtain documentation, troubleshooting tips, and sample configurations from online tools. For Cisco.com registered users, additional troubleshooting tools are available from the TAC website.
Cisco.com
Cisco.com is the foundation of a suite of interactive, networked services that provides immediate, open access to Cisco information and resources at anytime, from anywhere in the world. This highly integrated Internet application is a powerful, easy-to-use tool for doing business with Cisco.
Cisco.com provides a broad range of features and services to help customers and partners streamline business processes and improve productivity. Through Cisco.com, you can find information about Cisco and our networking solutions, services, and programs. In addition, you can resolve technical issues with online technical support, download and test software packages, and order Cisco learning materials and merchandise. Valuable online skill assessment, training, and certification programs are also available.
Customers and partners can self-register on Cisco.com to obtain additional personalized information and services. Registered users can order products, check on the status of an order, access technical support, and view benefits specific to their relationships with Cisco.
To access Cisco.com, go to the following website:
Technical Assistance Center
The Cisco TAC website is available to all customers who need technical assistance with a Cisco product or technology that is under warranty or covered by a maintenance contract.
Contacting TAC by Using the Cisco TAC Website
If you have a priority level 3 (P3) or priority level 4 (P4) problem, contact TAC by going to the TAC website:
P3 and P4 level problems are defined as follows:
•
P3—Your network performance is degraded. Network functionality is noticeably impaired, but most business operations continue.
•
P4—You need information or assistance on Cisco product capabilities, product installation, or basic product configuration.
In each of the above cases, use the Cisco TAC website to quickly find answers to your questions.
To register for Cisco.com, go to the following website:
http://www.cisco.com/register/
If you cannot resolve your technical issue by using the TAC online resources, Cisco.com registered users can open a case online by using the TAC Case Open tool at the following website:
http://www.cisco.com/tac/caseopen
Contacting TAC by Telephone
If you have a priority level 1 (P1) or priority level 2 (P2) problem, contact TAC by telephone and immediately open a case. To obtain a directory of toll-free numbers for your country, go to the following website:
http://www.cisco.com/warp/public/687/Directory/DirTAC.shtml
P1 and P2 level problems are defined as follows:
•
P1—Your production network is down, causing a critical impact to business operations if service is not restored quickly. No workaround is available.
•
P2—Your production network is severely degraded, affecting significant aspects of your business operations. No workaround is available.
Note
This document is to be used in conjunction with the documents listed in the section "Related Documentation."
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2007 Cisco Systems, Inc. All rights reserved.1 Support for RSA public/private key pairs for IKE authentication requires the use of an IPSec hardware acceleration module. Models listed as using "Built In" modules do not support RSA public/private key pairs for IKE authentication