Feedback Feedback
|
Table Of Contents
Information About MPLS LDP Session Protection
How to Configure MPLS LDP Session Protection
Enabling MPLS LDP Session Protection
Customizing MPLS LDP Session Protection
Specifying How Long an LDP Targeted Hello Adjacency Should Be Retained
Specifying Which Routers Should Have MPLS LDP Session Protection
Verifying MPLS LDP Session Protection
Configuration Examples for MPLS LDP Session Protection
debug mpls ldp session protection
Feature Information for MPLS LDP Session Protection
MPLS LDP Session Protection
First Published: November 8, 2004Last Updated: May 31, 2007The MPLS LDP Session Protection feature provides faster label distribution protocol convergence when a link recovers following an outage. MPLS LDP Session Protection protects a label distribution protocol (LDP) session between directly connected neighbors or an LDP session established for a traffic engineering (TE) tunnel.
Finding Feature Information in This Module
Your Cisco IOS software release may not support all of the features documented in this module. To reach links to specific feature documentation in this module and to see a list of the releases in which each feature is supported, use the "Feature Information for MPLS LDP Session Protection" section.
Finding Support Information for Platforms and Cisco IOS and Catalyst OS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS and Catalyst OS software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Contents
•
Information About MPLS LDP Session Protection
•
How to Configure MPLS LDP Session Protection
•
Configuration Examples for MPLS LDP Session Protection
•
Feature Information for MPLS LDP Session Protection
Information About MPLS LDP Session Protection
MPLS LDP Session Protection maintains LDP bindings when a link fails. MPLS LDP sessions are protected through the use of LDP Hello messages. When you enable MPLS LDP, the label switched routers (LSRs) send messages to find other LSRs with which they can create LDP sessions.
•
If the LSR is one hop from its neighbor, it is directly connected to its neighbor. The LSR sends out LDP Hello messages as User Datagram Protocol (UDP) packets to all the routers on the subnet. The hello message is called an LDP Link Hello. A neighboring LSR responds to the hello message and the two routers begin to establish an LDP session.
•
If the LSR is more than one hop from its neighbor, it is not directly connected to its neighbor. The LSR sends out a directed hello message as a UDP packet, but as a unicast message specifically addressed to that LSR. The hello message is called an LDP Targeted Hello. The nondirectly connected LSR responds to the Hello message and the two routers establish an LDP session. (If the path between two LSRs has been traffic engineered and has LDP enabled, the LDP session between them is called a targeted session.)
MPLS LDP Session Protection uses LDP Targeted Hellos to protect LDP sessions. Take, for example, two directly connected routers that have LDP enabled and can reach each other through alternate IP routes in the network. An LDP session that exists between two routers is called an LDP Link Hello Adjacency. When MPLS LDP Session Protection is enabled, an LDP Targeted Hello Adjacency is also established for the LDP session. If the link between the two routers fails, the LDP Link Adjacency also fails. However, if the LDP peer is still reachable through IP, the LDP session stays up, because the LDP Targeted Hello Adjacency still exists between the routers. When the directly connected link recovers, the session does not need to be reestablished, and LDP bindings for prefixes do not need to be relearned.
How to Configure MPLS LDP Session Protection
This section explains how to configure and verify MPLS LDP Session Protection:
•
Enabling MPLS LDP Session Protection (required)
•
Customizing MPLS LDP Session Protection (optional)
•
Verifying MPLS LDP Session Protection (optional)
Enabling MPLS LDP Session Protection
You use the mpls ldp session protection command to enable MPLS LDP Session Protection. This command enables LDP sessions to be protected during a link failure. By default, the command protects all LDP sessions. The command has several options that enable you to specify which LDP sessions to protect. The vrf keyword lets you protect LDP sessions for a specified VRF. The for keyword lets you specify a standard IP access control list (ACL) of prefixes that should be protected. The duration keyword enables you to specify how long the router should retain the LDP Targeted Hello Adjacency following the loss of the LDP Link Hello Adjacency.
Prerequisites
LSRs must be able to respond to LDP targeted hellos. Otherwise, the LSRs cannot establish a targeted adjacency. All routers that participate in MPLS LDP Session Protection must be enabled to respond to targeted hellos. Both neighbor routers must be configured for session protection or one router must be configured for session protection and the other router must be configured to respond to targeted hellos.
Restrictions
This feature is not supported under the following circumstances:
•
With TDP sessions
•
With extended access lists
•
With LC-ATM routers
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
ip cef [distributed]
4.
interface loopbacknumber
5.
ip address {prefix mask}
6.
interface interface
7.
mpls ip
8.
mpls label protocol {ldp | tdp | both}
9.
exit
10.
mpls ldp session protection [vrf vpn-name] [for acl] [duration seconds]
DETAILED STEPS
Customizing MPLS LDP Session Protection
You can modify MPLS LDP Session Protection by using the keywords in the mpls ldp session protection command. The following sections explain how to customize the feature.
Specifying How Long an LDP Targeted Hello Adjacency Should Be Retained
The default behavior of the mpls ldp session protection command allows an LDP Targeted Hello Adjacency to exist indefinitely following the loss of an LDP Link Hello Adjacency. You can issue the duration keyword to specify the number of seconds (from 30 to 2,147,483) that the LDP Targeted Hello Adjacency is retained after the loss of the LDP Link Hello Adjacency. When the link is lost, a timer starts. If the timer expires, the LDP Targeted Hello Adjacency is removed.
Specifying Which Routers Should Have MPLS LDP Session Protection
The default behavior of the mpls ldp session protection command allows MPLS LDP Session Protection for all neighbor sessions. You can issue either the vrf or for keyword to limit the number of neighbor sessions that are protected.
Enabling MPLS LDP Session Protection on Specified VPN Routing and Forwarding Instances
If the router is configured with at least one VPN routing and forwarding (VRF) instance, you can use the vrf keyword to select which VRF is to be protected. You cannot specify more than one VRF with the mpls ldp session protection command. To specify multiple VRFs, issue the command multiple times.
Enabling MPLS LDP Session Protection on Specified Peer Routers
You can create an access list that includes several peer routers. You can specify that access list with the for keyword to enable LDP Session Protection for the peer routers in the access control list.
Verifying MPLS LDP Session Protection
To verify that LDP Session Protection has been correctly configured, perform the following steps.
SUMMARY STEPS
1.
show mpls ldp discovery
2.
show mpls ldp neighbor
3.
show mpls ldp neighbor detail
DETAILED STEPS
Step 1
show mpls ldp discovery
Issue this command and check that the output contains xmit/recv to the peer router.
Router# show mpls ldp discoveryLocal LDP Identifier:10.0.0.5:0Discovery Sources:Interfaces:ATM5/1/0.5 (ldp): xmit/recvLDP Id: 10.0.0.1:0Targeted Hellos:10.0.0.5 -> 10.0.0.3 (ldp): active, xmit/recvLDP Id: 10.0.0.3:0Step 2
show mpls ldp neighbor
Issue this command to check that the targeted hellos are active.
Router# show mpls ldp neighborPeer LDP Ident: 10.0.0.3:0; Local LDP Ident 10.0.0.5:0TCP connection: 10.0.0.3.646 - 10.0.0.5.11005State: Oper; Msgs sent/rcvd: 1453/1464; DownstreamUp time: 21:09:56LDP discovery sources:Targeted Hello 10.0.0.5 -> 10.0.0.3, activeAddresses bound to peer LDP Ident:10.3.104.3 10.0.0.2 10.0.0.3Step 3
show mpls ldp neighbor detail
Issue this command to check that the MPLS LDP Session Protection state is Ready or Protecting. If the second last line of the output shows Incomplete, the Targeted Hello Adjacency is not up yet.
Router# show mpls ldp neighbor detailPeer LDP Ident: 10.16.16.16:0; Local LDP Ident 10.15.15.15:0TCP connection: 10.16.16.16.11013 - 10.15.15.15.646State: Oper; Msgs sent/rcvd: 53/51; Downstream; Last TIB rev sent 74Up time: 00:11:32; UID: 1; Peer Id 0;LDP discovery sources:Targeted Hello 10.15.15.15 -> 10.16.16.16, active, passive;holdtime: infinite, hello interval: 10000 msAddresses bound to peer LDP Ident:10.0.0.2 10.16.16.16 10.101.101.101 11.0.0.1Peer holdtime: 180000 ms; KA interval: 60000 ms; Peer state: estabClients: Dir Adj ClientLDP Session Protection enabled, state: Protectingduration: infinite
Troubleshooting Tips
Use the clear mpls ldp neighbor command if you need to terminate an LDP session after a link goes down. This is useful for situations where the link needs to be taken out of service or needs to be connected to a different neighbor.
To enable the display of events related to MPLS LDP Session Protection, use the debug mpls ldp session protection command.
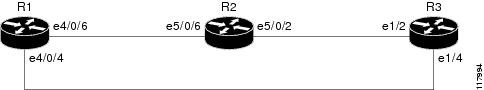
Configuration Examples for MPLS LDP Session Protection
Figure 1 shows a sample configuration for MPLS LDP Session Protection.
Figure 1 MPLS LDP Session Protection Example
R1
redundancyno keepalive-enablemode hsa!ip cef distributedno ip domain-lookupmultilink bundle-name bothmpls label protocol ldpmpls ldp session protectionno mpls traffic-eng auto-bw timers frequency 0tag-switching tdp router-id Loopback0 force!interface Loopback0ip address 10.0.0.1 255.255.255.255no ip directed-broadcastno ip mroute-cache!interface Multilink4no ip addressno ip directed-broadcastno ip mroute-cacheload-interval 30ppp multilinkmultilink-group 4!interface Ethernet1/0/0ip address 10.3.123.1 255.255.0.0no ip directed-broadcast!interface Ethernet4/0/0no ip addressno ip directed-broadcastshutdown!interface Ethernet4/0/1description -- ip address 10.0.0.2 255.255.255.0no ip addressno ip directed-broadcastshutdown!interface Ethernet4/0/4ip address 10.0.0.1 255.0.0.0no ip directed-broadcastmpls label protocol ldptag-switching ip!interface Ethernet4/0/6ip address 10.0.0.1 255.0.0.0no ip directed-broadcastmpls label protocol ldptag-switching ip!interface Ethernet4/0/7ip address 10.0.0.1 255.0.0.0no ip directed-broadcastmpls label protocol ldptag-switching ip!router ospf 100log-adjacency-changesredistribute connectednetwork 10.0.0.1 0.0.0.0 area 100network 10.0.0.0 0.255.255.255 area 100network 10.0.0.0 0.255.255.255 area 100network 10.0.0.0 0.255.255.255 area 100network 10.0.0.0 0.255.255.255 area 100!ip classlessR2
redundancyno keepalive-enablemode hsa!ip subnet-zeroip cef distributedmpls label protocol ldpmpls ldp session protectionno mpls traffic-eng auto-bw timers frequency 0tag-switching tdp router-id Loopback0 force!interface Loopback0ip address 10.0.0.3 255.255.255.255no ip directed-broadcast!interface Ethernet5/0/0no ip addressno ip directed-broadcastshutdownfull-duplex!interface Ethernet5/0/2ip address 10.0.0.1 255.0.0.0no ip directed-broadcastfull-duplexmpls label protocol ldptag-switching ip!interface Ethernet5/0/6ip address 10.0.0.2 255.0.0.0no ip directed-broadcastip load-sharing per-packetfull-duplexmpls label protocol ldptag-switching ip!interface FastEthernet5/1/0ip address 10.3.123.112 255.255.0.0no ip directed-broadcast!router ospf 100log-adjacency-changesredistribute connectednetwork 10.0.0.3 0.0.0.0 area 100network 10.0.0.0 0.255.255.255 area 100network 10.0.0.0 0.255.255.255 area 100!ip classlessR3
ip cefno ip domain-lookupmpls label range 200 100000 static 16 199mpls label protocol ldpno mpls traffic-eng auto-bw timers frequency 0tag-switching tdp router-id Loopback0 force!interface Loopback0ip address 10.0.0.5 255.255.255.255no ip directed-broadcast!interface Ethernet1/0no ip addressno ip directed-broadcastshutdownhalf-duplex!interface Ethernet1/2ip address 10.0.0.2 255.0.0.0no ip directed-broadcastfull-duplexmpls label protocol ldptag-switching ip!interface Ethernet1/4ip address 10.0.0.2 255.0.0.0no ip directed-broadcastfull-duplexmpls label protocol ldptag-switching ip!router ospf 100log-adjacency-changesredistribute connectednetwork 10.0.0.5 0.0.0.0 area 100network 10.0.0.0 0.255.255.255 area 100network 10.0.0.0 0.255.255.255 area 100!ip classlessAdditional References
The following sections provide references related to the MPLS LDP Session Protection feature.
Related Documents
Standards
MIBs
MPLS LDP MIB
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL:
RFCs
Technical Assistance
Command Reference
This section documents only commands that are new or modified.
•
debug mpls ldp session protection
debug mpls ldp session protection
To enable the display of events related to MPLS LDP Session Protection, use the debug mpls ldp session protection command in privileged EXEC mode. To disable this feature, use the no form of this command.
debug mpls ldp session protection [peer-acl acl]
no debug mpls ldp session protection [peer-acl acl]
Syntax Description
peer-acl acl
(Optional) Enables the display of events for the peers whose router IDs are listed in the access control list.
Command Modes
Privileged EXEC
Command History
Examples
In the following example, the display of events related to MPLS LDP Session Protection are enabled:
Router# debug mpls ldp session protectionRelated Commands
clear mpls ldp neighbor
Forcibly resets an LDP session.
show mpls ldp neighbor
Displays the contents of the LDP.
mpls ldp session protection
To enable MPLS LDP Session Protection for existing Label Distribution Protocol (LDP) sessions or when new sessions are established, use the mpls ldp session protection command in global configuration mode. To disable this feature, use the no form of this command.
mpls ldp session protection [vrf vpn-name] [for acl] [duration {infinite | seconds}]
no mpls ldp session protection [vrf vpn-name] [for acl] [duration {infinite | seconds}]
Syntax Description
Defaults
LDP sessions are not established.
Command Modes
Global configuration
Command History
Usage Guidelines
This command is not supported under the following circumstances:
•
With TDP sessions
•
With extended access lists
•
With LC-ATM routers
If you issue the mpls ldp session protection command without the duration keyword, then session protection is enabled for 86400 seconds (24 hours) meaning that the LDP Targeted Hello Adjacency is retained for 24 hours after a link is lost. This is the default timeout.
If you issue the mpls ldp session protection duration infinite command, then session protection is enabled forever meaning that the LDP Targeted Hello Adjacency is retained forever after a link is lost.
If you issue the mpls ldp session protection duration seconds command, then session protection is enabled for the number of seconds indicated meaning that the LDP Targeted Hello Adjacency is retained for that amount of time. For example, if you issued mpls ldp session protection duration 100, then the LDP Targeted Hello Adjacency is retained for 100 seconds after a link is lost.
Examples
In the following example, MPLS LDP Session Protection is enabled for LDP sessions for peers whose router IDs are listed in access control list rtr4:
Router(config)# mpls ldp session protection for rtr4Related Commands
clear mpls ldp neighbor
Forcibly resets an LDP session.
show mpls ldp neighbor
Displays the contents of the LDP.
show mpls ldp neighbor
To display the status of Label Distribution Protocol (LDP) sessions, use the show mpls ldp neighbor command in user EXEC or privileged EXEC mode.
show mpls ldp neighbor [vrf vrf-name | all] [address | interface] [detail] [graceful-restart]
Syntax Description
Defaults
This command displays information about LDP neighbors for the default routing domain if you do not specify the optional vrf keyword.
Command Modes
User EXEC
Privileged EXECCommand History
Usage Guidelines
The show mpls ldp neighbor command can provide information about all LDP neighbors, or the information can be limited to the following:
•
Neighbor with specific IP address
•
LDP neighbors known to be accessible over a specific interface
Note
This command displays information about LDP and Tag Distribution Protocol (TDP) neighbor sessions.
Examples
For explanations of the significant fields shown in the displays, see Table 1.
The following is sample output from the show mpls ldp neighbor command:
Router# show mpls ldp neighborPeer LDP Ident: 10.0.7.7:2; Local LDP Ident 10.1.1.1:1TCP connection: 10.0.7.7.11032 - 10.1.1.1.646State: Oper; Msgs sent/rcvd: 5855/6371; Downstream on demandUp time: 13:15:09LDP discovery sources:ATM3/0.1Peer LDP Ident: 10.1.1.1:0; Local LDP Ident 10.1.1.1:0TCP connection: 10.1.1.1.646 - 10.1.1.1.11006State: Oper; Msgs sent/rcvd: 4/411; DownstreamUp time: 00:00:52LDP discovery sources:Ethernet1/0/0Addresses bound to peer LDP Ident:10.0.0.29 10.1.1.1 10.0.0.199 10.10.1.110.205.0.9The following is sample output from the show mpls ldp neighbor command, in which duplicate addresses are detected. They indicate an error because a given address should be bound to only one peer.
Router# show mpls ldp neighborPeer LDP Ident: 10.0.7.7:2; Local LDP Ident 10.1.1.1:1TCP connection: 10.0.7.7.11032 - 10.1.1.1.646State: Oper; Msgs sent/rcvd: 5855/6371; Downstream on demandUp time: 13:15:09LDP discovery sources:ATM3/0.1Peer LDP Ident: 10.1.1.1:0; Local LDP Ident 10.1.1.1:0TCP connection: 10.1.1.1.646 - 10.1.1.1.11006State: Oper; Msgs sent/rcvd: 4/411; DownstreamUp time: 00:00:52LDP discovery sources:Ethernet1/0/0Addresses bound to peer LDP Ident:10.0.0.29 10.1.1.1 10.0.0.199 10.10.1.110.205.0.9Duplicate Addresses advertised by peer:10.10.8.111The following is sample output from the show mpls ldp neighbor vrf vpn10 command, which displays the LDP neighbor information for the specified VPN routing and forwarding instance named vpn10:
Router# show mpls ldp neighbor vrf vpn10Peer LDP Ident:10.14.14.14:0; Local LDP Ident 10.29.0.2:0TCP connection:10.14.14.14.646 - 10.29.0.2.11384State:Oper; Msgs sent/rcvd:1423/800; DownstreamUp time:02:38:11LDP discovery sources:ATM3/0/0.10Addresses bound to peer LDP Ident:10.3.36.9 10.7.0.1 10.14.14.14 10.13.0.110.15.0.1 10.17.0.1 10.19.0.1 10.21.0.110.23.0.1 10.25.0.1 10.27.0.1 10.29.0.110.31.0.1 10.33.0.1 10.35.0.1 10.37.0.110.39.0.1 10.41.0.1 10.43.0.1 10.45.0.110.47.0.1 10.49.0.1 10.51.0.1 10.53.0.110.55.0.1 10.57.0.1 10.59.0.1 10.61.0.110.63.0.1 10.65.0.1 10.67.0.1 10.69.0.110.71.0.1 10.73.0.1 10.75.0.1 10.77.0.110.79.0.1 10.81.0.1 10.83.0.1 10.85.0.110.87.0.1 10.89.0.1 10.91.0.1 10.93.0.110.95.0.1 10.97.0.1 10.99.0.1 10.101.0.110.103.0.1 10.105.0.1 10.107.0.1 10.109.0.110.4.0.2 10.3.0.2The following shows sample output from the show mpls ldp neighbor detail command, which displays information about inbound filtering:
Router# show mpls ldp neighbor vrf vpn1 detailPeer LDP Ident: 10.13.13.13:0; Local LDP Ident 10.33.0.2:0TCP connection: 10.13.13.13.646 - 10.33.0.2.31581State: Oper; Msgs sent/rcvd: 11/10; Downstream; Last TIB rev sent 13Up time: 00:02:25; UID: 26; Peer Id 0;LDP discovery sources:Ethernet1/0/2; Src IP addr: 10.33.0.1holdtime: 15000 ms, hello interval: 5000 msAddresses bound to peer LDP Ident:10.3.105.1 10.13.13.13 10.33.0..1Peer holdtime: 180000 ms; KA interval: 60000 ms; Peer state: estabLDP inbound filtering accept acl:1Peer LDP Ident: 10.14.14.14:0; Local LDP Ident 10.33.0.2:0TCP connection: 10.14.14.14.646 - 10.33.0.2.31601State: Oper; Msgs sent/rcvd: 10/9; Downstream; Last TIB rev sent 13Up time: 00:01:17; UID: 29; Peer Id 3;LDP discovery sources:Ethernet1/0/3; Src IP addr: 10.33.0.1holdtime: 15000 ms, hello interval: 5000 msAddresses bound to peer LDP Ident:10.3.104.1 10.14.14.14 10.32.0.1Peer holdtime: 180000 ms; KA interval: 60000 ms; Peer state: estabLDP inbound filtering accept acl:1The following is sample output from the show mpls ldp neighbor all command, which displays the LDP neighbor information for all VPN routing and forwarding instances, including those in the default routing domain. In this example, note that the same neighbor LDP ID (10.14.14.14) appears in all the listed VRF interfaces, highlighting the fact that the same IP address can coexist in different VPN routing and forwarding instances.
Router# show mpls ldp neighbor allPeer TDP Ident:10.11.11.11:0; Local TDP Ident 10.12.12.12:0TCP connection:10.11.11.11.711 - 10.12.12.12.11003State:Oper; PIEs sent/rcvd:185/187; DownstreamUp time:02:40:02TDP discovery sources:ATM1/1/0.1Addresses bound to peer TDP Ident:10.3.38.3 10.1.0.2 10.11.11.11VRF vpn1:Peer LDP Ident:10.14.14.14:0; Local LDP Ident 10.7.0.2:0TCP connection:10.14.14.14.646 - 10.7.0.2.11359State:Oper; Msgs sent/rcvd:952/801; DownstreamUp time:02:38:49LDP discovery sources:ATM3/0/0.1Addresses bound to peer LDP Ident:10.3.36.9 10.7.0.1 10.14.14.14 10.13.0.110.15.0.1 10.17.0.1 10.19.0.1 10.21.0.110.23.0.1 10.25.0.1 10.27.0.1 10.29.0.110.31.0.1 10.33.0.1 10.35.0.1 10.37.0.110.39.0.1 10.41.0.1 10.43.0.1 10.45.0.110.47.0.1 10.49.0.1 10.51.0.1 10.53.0.110.55.0.1 10.57.0.1 10.59.0.1 10.61.0.110.63.0.1 10.65.0.1 10.67.0.1 10.69.0.110.71.0.1 10.73.0.1 10.75.0.1 10.77.0.110.79.0.1 10.81.0.1 10.83.0.1 10.85.0.110.87.0.1 10.89.0.1 10.91.0.1 10.93.0.110.95.0.1 10.97.0.1 10.99.0.1 10.101.0.110.103.0.1 10.105.0.1 10.107.0.1 10.109.0.110.4.0.2 10.3.0.2VRF vpn2:Peer LDP Ident:10.14.14.14:0; Local LDP Ident 10.13.0.2:0TCP connection:10.14.14.14.646 - 10.13.0.2.11361State:Oper; Msgs sent/rcvd:964/803; DownstreamUp time:02:38:50LDP discovery sources:ATM3/0/0.2Addresses bound to peer LDP Ident:10.3.36.9 10.7.0.1 10.14.14.14 10.13.0.110.15.0.1 10.17.0.1 10.19.0.1 10.21.0.110.23.0.1 10.25.0.1 10.27.0.1 10.29.0.110.31.0.1 10.33.0.1 10.35.0.1 10.37.0.110.39.0.1 10.41.0.1 10.43.0.1 10.45.0.110.47.0.1 10.49.0.1 10.51.0.1 10.53.0.110.55.0.1 10.57.0.1 10.59.0.1 10.61.0.110.63.0.1 10.65.0.1 10.67.0.1 10.69.0.110.71.0.1 10.73.0.1 10.75.0.1 10.77.0.110.79.0.1 10.81.0.1 10.83.0.1 10.85.0.110.87.0.1 10.89.0.1 10.91.0.1 10.93.0.110.95.0.1 10.97.0.1 10.99.0.1 10.101.0.110.103.0.1 10.105.0.1 10.107.0.1 10.109.0.110.4.0.2 10.3.0.2VRF vpn3:Peer LDP Ident:10.14.14.14:0; Local LDP Ident 10.15.0.2:0TCP connection:10.14.14.14.646 - 10.15.0.2.11364State:Oper; Msgs sent/rcvd:1069/800; DownstreamUp time:02:38:52LDP discovery sources:ATM3/0/0.3Addresses bound to peer LDP Ident:10.3.36.9 10.17.0.1 10.14.14.14 10.13.0.110.15.0.1 10.17.0.1 10.19.0.1 10.21.0.110.23.0.1 10.25.0.1 10.27.0.1 10.29.0.110.31.0.1 10.33.0.1 10.35.0.1 10.37.0.110.39.0.1 10.41.0.1 10.43.0.1 10.45.0.110.47.0.1 10.49.0.1 10.51.0.1 10.53.0.110.55.0.1 10.57.0.1 10.59.0.1 10.61.0.110.63.0.1 10.65.0.1 10.67.0.1 10.69.0.110.71.0.1 10.73.0.1 10.75.0.1 10.77.0.110.79.0.1 10.81.0.1 10.83.0.1 10.85.0.110.87.0.1 10.89.0.1 10.91.0.1 10.93.0.110.95.0.1 10.97.0.1 10.99.0.1 10.101.0.110.103.0.1 10.105.0.1 10.107.0.1 10.109.0.110.4.0.2 10.3.0.2VRF vpn4:Peer LDP Ident:10.14.14.14:0; Local LDP Ident 10.17.0.2:0TCP connection:10.14.14.14.646 - 10.17.0.2.11366State:Oper; Msgs sent/rcvd:1199/802; DownstreamThe following example shows the Graceful Restart status of the LDP neighbors:
Router# show mpls ldp neighbor graceful-restartPeer LDP Ident: 10.20.20.20:0; Local LDP Ident 10.17.17.17:0TCP connection: 10.20.20.20.16510 - 10.17.17.17.646State: Oper; Msgs sent/rcvd: 8/18; DownstreamUp time: 00:04:39Graceful Restart enabled; Peer reconnect time (msecs): 120000Peer LDP Ident: 10.19.19.19:0; Local LDP Ident 10.17.17.17:0TCP connection: 10.19.19.19.11007 - 10.17.17.17.646State: Oper; Msgs sent/rcvd: 8/38; DownstreamUp time: 00:04:30Graceful Restart enabled; Peer reconnect time (msecs): 120000The following sample output from the show mpls ldp neighbor detail command displays information about the MD5 password configuration:
Router# show mpls ldp neighbor detailPeer LDP Ident: 10.3.3:0; Local LDP Ident 10.1.1.1:0TCP connection: 10.3.3.3.11018 - 10.1.1.1.646Password: required, neighbor, in useState: Oper; Msgs sent/rcvd: 167/167; Downstream; Last TIB rev sent 9Up time: 02:24:02; UID: 5; Peer Id 3;LDP discovery sources:Targeted Hello 10.1.1.1 -> 10.3.3.3, passive;holdtime: 90000 ms, hello interval: 10000 msAddresses bound to peer LDP Ident:10.3.3.3 10.0.30.3Peer holdtime: 180000 ms; KA interval: 60000 ms; Peer state: estabPeer LDP Ident: 10.4.4.4:0; Local LDP Ident 10.1.1.1:0TCP connection: 10.4.4.4.11017 - 10.1.1.1.646Password: not required, none, staleState: Oper; Msgs sent/rcvd: 9/9; Downstream; Last TIB rev sent 9Up time: 00:05:35; UID: 6; Peer Id 1;LDP discovery sources:Ethernet1/0; Src IP addr: 10.0.20.4holdtime: 15000 ms, hello interval: 5000 msAddresses bound to peer LDP Ident:10.0.40.4 10.4.4.4 10.0.20.4Peer holdtime: 180000 ms; KA interval: 60000 ms; Peer state: estabTable 1 describes the significant fields shown in the displays.
Related Commands
Feature Information for MPLS LDP Session Protection
Table 2 lists the release history for this feature.
Not all commands may be available in your Cisco IOS software release. For release information about a specific command, see the command reference documentation.
Cisco IOS software images are specific to a Cisco IOS software release, a feature set, and a platform. Use Cisco Feature Navigator to find information about platform support and Cisco IOS software image support. Access Cisco Feature Navigator at http://www.cisco.com/go/fn. You must have an account on Cisco.com. If you do not have an account or have forgotten your username or password, click Cancel at the login dialog box and follow the instructions that appear.
Note
Table 2 lists only the Cisco IOS software release that introduced support for a given feature in a given Cisco IOS software release train. Unless noted otherwise, subsequent releases of that Cisco IOS software release train also support that feature.
Table 2 Feature Information for MPLS LDP Session Protection
MPLS LDP Session Protection
12.0(30)S
12.3(14)T
12.2(28)SB
12.2(33)SRA
12.2(33)SXHThis feature provides faster label distribution protocol convergence when a link recovers following an outage.
The following sections provide information about this feature:
•
Information About MPLS LDP Session Protection
CCVP, the Cisco logo, and the Cisco Square Bridge logo are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn is a service mark of Cisco Systems, Inc.; and Access Registrar, Aironet, BPX, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, Follow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, iQuick Study, LightStream, Linksys, MeetingPlace, MGX, Networking Academy, Network Registrar, Packet, PIX, ProConnect, ScriptShare, SMARTnet, StackWise, The Fastest Way to Increase Your Internet Quotient, and TransPath are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (0705R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2004-2007 Cisco Systems, Inc. All rights reserved.