Feedback Feedback
|
Table Of Contents
Prerequisites for L2VPN Interworking
Restrictions for L2VPN Interworking
Cisco 12000 Series Router Restrictions
Cisco 7600 Series Routers Restrictions
ATM AAL5 Interworking Restrictions
Ethernet/VLAN Interworking Restrictions
Frame Relay Interworking Restrictions
Information About L2VPN Interworking
Overview of L2VPN Interworking
How to Configure L2VPN Interworking
Configuring L2VPN Interworking
Configuring Static IP Addresses for L2VPN Interworking for PPP
Verifying the L2VPN Interworking Configuration
Configuration Examples for L2VPN Interworking
Ethernet to VLAN over L2TPV3 (Bridged): Example
Ethernet to VLAN over AToM (Bridged): Example
Frame Relay to VLAN over L2TPV3 (Routed): Example
Frame Relay to VLAN over AToM (Routed): Example
Frame Relay to ATM AAL5 over AToM (Routed): Example
VLAN to ATM AAL5 over AToM (Bridged): Example
Frame Relay to PPP over L2TPv3 (Routed): Example
Frame Relay to PPP over AToM (Routed): Example
Ethernet/VLAN to PPP over AToM (Routed): Example
Feature Information for L2VPN Interworking
L2VPN Interworking
First Published: August 26, 2003Last Updated: June 29, 2007This feature module explains how to configure the following Layer 2 Virtual Private Network (L2VPN) Interworking features:
•
Ethernet/VLAN to ATM AAL5 Interworking
•
Ethernet/VLAN to Frame Relay Interworking
•
Ethernet/VLAN to PPP Interworking
•
Ethernet to VLAN Interworking
•
Frame Relay to ATM AAL5 Interworking
•
Frame Relay to PPP Interworking
Finding Feature Information in This Module
Your Cisco IOS software release may not support all of the features documented in this module. To reach links to specific feature documentation in this module and to see a list of the releases in which each feature is supported, use the "Feature Information for L2VPN Interworking" section.
Finding Support Information for Platforms and Cisco IOS and Catalyst OS Software Images
Use Cisco Feature Navigator to find information about platform support and Cisco IOS and Catalyst OS software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Contents
•
Prerequisites for L2VPN Interworking
•
Restrictions for L2VPN Interworking
•
Information About L2VPN Interworking
•
How to Configure L2VPN Interworking
•
Configuration Examples for L2VPN Interworking
•
Feature Information for L2VPN Interworking
Prerequisites for L2VPN Interworking
Before you configure L2VPN Interworking on a router:
•
You must enable Cisco Express Forwarding.
•
On the Cisco 12000 series Internet router, before you configure Layer 2 Tunnel Protocol version 3 (L2TPv3) for L2VPN Interworking on an IP Services Engine (ISE/Engine 3) or Engine 5 interface, you must also enable the L2VPN feature bundle on the line card.
To enable the feature bundle, enter the hw-module slot np mode feature command in global configuration mode as follows:
Router# configure terminalRouter(config)# hw-module slot slot-number np mode featureRestrictions for L2VPN Interworking
The following sections list the L2VPN Interworking restrictions:
•
Cisco 12000 Series Router Restrictions
•
Cisco 7600 Series Routers Restrictions
•
ATM AAL5 Interworking Restrictions
•
Ethernet/VLAN Interworking Restrictions
•
Frame Relay Interworking Restrictions
•
PPP Interworking Restrictions
General Restrictions
This section lists general restrictions that apply to L2VPN Interworking. Other restrictions that are platform-specific or device-specific are listed in the following sections.
•
The interworking type on one provider edge (PE) router must match the interworking type on the peer PE router.
•
Distributed Cisco Express Forwarding switching is supported on the Cisco 7500.
•
Although Layer 2 quality of service (QoS) is supported extensively on Cisco 12000 series routers (details are given in Any Transport over MPLS (AToM): Layer 2 QoS (Quality of Service) for the Cisco 12000 Series Router), on other platforms only the following QoS features are supported with L2VPN Interworking:
–
Static IP type of service (ToS) or Multiprotocol Label Switching (MPLS) experimental bit (EXP) setting in tunnel header
–
IP ToS reflection in tunnel header (Layer 2 Tunnel Protocol Version 3 (L2TPv3) only)
–
Frame Relay policing
–
Frame Relay data-link connection identifier (DLCI)-based congestion management (Cisco 7500/Versatile Interface Processor (VIP))
–
One-to-one mapping of VLAN priority bits to MPLS EXP bits
•
L2VPN Interworking is supported on the Cisco 7200 and 7500 series routers. For details on supported hardware, see the following documents:
–
Cross-Platform Release Notes for Cisco IOS Release 12.0S
–
Cross-Platform Release Notes for Cisco IOS Release 12.4T, Part 2: Platform-Specific Information
•
L2VPN Interworking is supported on the Cisco 7600 routers. For details on supported shared port adapters and line cards, see the following documents:
–
Supported Hardware for Cisco 7600 Series Routers with Release 12.2SR
–
Release Notes for Cisco IOS Release 12.2SR for the Cisco 7600 Series Routers
•
L2VPN Interworking is supported on the Cisco12000 Series Routers. For information about hardware requirements, see the Cross-Platform Release Notes for Cisco IOS Release 12.0S.
Cisco 12000 Series Router Restrictions
Frame Relay to PPP and High-Level Data Link Control (HDLC) Interworking
The Cisco 12000 series Internet router does not support L2VPN Interworking with PPP and HDLC transport types in Cisco IOS releases earlier than Cisco IOS release 12.0(32)S.
In Cisco IOS Release 12.0(32)S and later releases, the Cisco 12000 series Internet router supports L2VPN interworking for Frame Relay over MPLS and PPP and HDLC over MPLS only on the following shared port adapters (SPAs):
•
ISE/Engine 3 SPAs:
–
SPA-2XCT3/DS0 (2-port channelized T3 to DS0)
–
SPA-4XCT3/DS0 (4-port channelized T3 to DS0)
•
Engine 5 SPAs:
–
SPA-1XCHSTM1/OC-3 (1-port channelized STM-1c/OC-3c to DS0)
–
SPA-8XCHT1/E1 (8-port channelized T1/E1)
–
SPA-2XOC-48-POS/RPR (2-port OC-48/STM16 POS/RPR)
–
SPA-OC-192POS-LR (1-port OC-192/STM64 POS/RPR)
–
SPA-OC-192POS-XFP (1-port OC-192/STM64 POS/RPR)
L2VPN Interworking over L2TPv3
On the Cisco 12000 series Internet router, Ethernet (bridged) interworking is not supported for L2TPv3. Only IP (routed) interworking is supported.
IP (routed) interworking is not supported in an L2TPv3 pseudowire that is configured for data sequencing (using the sequencing command).
In Cisco IOS Release 12.0(32)SY and later releases, the Cisco 12000 series Internet router supports L2VPN Interworking over L2TPv3 tunnels in IP mode on ISE and Engine 5 line cards as follows:
•
On an ISE interface configured for L2TPv3 tunneling, the following Layer 2 encapsulations are supported:
–
ATM Adaptation Layer Type-5 (AAL5)
–
Ethernet
–
802.1q (VLAN)
–
Frame Relay DLCI
•
On an Engine 5 interface configured for L2TPv3 tunneling, the following Layer 2 encapsulations are supported:
–
Ethernet
–
802.1q (VLAN)
–
Frame Relay DLCI
For more information, refer to Layer 2 Tunnel Protocol Version 3.
The only frame format supported for L2TPv3 interworking on Engine 5 Ethernet SPAs is Ethernet Version 2 (also known as Ethernet II) with the Ether type 0x0800 value set as Internet Protocol Payload and (optionally) 802.1q VLAN. Ethernet packets with other Ethernet frame formats are dropped.
Remote Ethernet Port Shutdown Support
The Cisco Remote Ethernet Port Shutdown feature (which minimizes potential data loss after a remote link failure) is supported only on the following Engine 5 Ethernet SPAs:
•
SPA-8XFE (8-port Fast Ethernet)
•
SPA-2X1GE (2-port Gigabit Ethernet)
•
SPA-5X1GE (5-port Gigabit Ethernet)
•
SPA-10X1GE (10-port Gigabit Ethernet)
•
SPA-1X10GE (1-port 10-Gigabit Ethernet)
For more information about this feature, refer to Any Transport over MPLS (AToM): Remote Ethernet Port Shutdown.
L2VPN Any-to-Any Interworking on Engine 5 Line Cards
Table 1 shows the different combinations of transport types supported for L2VPN interworking on Engine 3 and Engine 5 SPA interfaces connected through an attachment circuit over MPLS or L2TPv3.
Cisco 7600 Series Routers Restrictions
The following line cards are supported on the Cisco 7600 series router. Table 2 shows the line cards that are supported on the WAN (ATM, Frame Relay, or PPP) side of the interworking link. Table 3 shows the line cards that are supported on the Ethernet side of the interworking link.
•
The Cisco 7600 series routers do not support L2VPN Interworking over L2TPv3.
•
Cisco 7600 series routers support only the following interworking types:
–
Ethernet/VLAN to Frame Relay (IP and Ethernet modes)
–
Ethernet/VLAN to ATM AAL5SNAP (IP and Ethernet modes)
–
Ethernet/VLAN to PPP (IP only)
–
Ethernet to VLAN Interworking
•
Cisco 7600 series routers do not support the following interworking types:
–
Ethernet/VLAN to ATM AAL5MUX
–
Frame Relay to PPP Interworking
–
Frame Relay to ATM AAL5 Interworking
•
Both ends of the interworking link must be configured with the same encapsulation and interworking type:
–
If you use Ethernet encapsulation, you must use the Ethernet (bridged) interworking type. If you are not using Ethernet encapsulation, you can use a bridging mechanism, such as routed bridge encapsulation (RBE).
–
If you use an IP encapsulation (such as ATM or Frame Relay), you must use the IP (routed) interworking type. The PE routers negotiate the process for learning and resolving addresses.
ATM AAL5 Interworking Restrictions
The following restrictions apply to ATM AAL5 Interworking:
•
Cisco 12000 series Engine 5 line cards do not support L2VPN interworking on ATM. On other line cards and platforms, only ATM AAL5 VC mode is supported; ATM VP and port mode are not supported.
•
Switched virtual circuits (SVCs) are not supported.
•
Inverse ARP is not supported with IP interworking.
•
Customer edge (CE) routers must use point-to-point subinterfaces or static maps.
•
Both AAL5MUX and AAL5SNAP encapsulation are supported. In the case of AAL5MUX, no translation is needed.
•
On the Cisco 12000 series Engine 3 line card, Network Layer Protocol ID (NLPID) encapsulation is not supported in routed mode; and neither NLPID nor AAL5MUX is supported in bridged mode.
•
In the Ethernet end-to-end over ATM scenario, the following translations are supported:
–
Ethernet without LAN frame check sequence (FCS) (AAAA030080C200070000)
–
Spanning tree (AAAA030080c2000E)
Everything else is dropped.
•
In the IP over ATM scenario, the IPv4 (AAAA030000000800) translation is supported. Everything else is dropped.
•
Operation, Administration, and Management (OAM) emulation for L2VPN Interworking is the same as like-to-like. The end-to-end F5 loopback cells are looped back on the PE router. When the pseudowire is down, an F5 end-to-end segment Alarm Indication Signal (AIS)/Remote Defect Identification (RDI) is sent from the PE router to the CE router.
•
Interim Local Management Interface (ILMI) can manage virtual circuits (VCs) and permanent virtual circuits (PVCs).
•
To enable ILMI management, configure ILMI PVC 0/16 on the PE router's ATM interface. If a PVC is provisioned or deleted, an ilmiVCCChange trap is sent to the CE router.
•
Only the user side of the User-Network Interface (UNI) is supported; the network side of the UNI is not supported.
Ethernet/VLAN Interworking Restrictions
The following restrictions apply to Ethernet/VLAN interworking:
•
On the Cisco 12000 series Internet router, Ethernet (bridged) interworking is not supported for L2TPv3.
In an L2VPN Interworking configuration, after you configure L2TPv3 tunnel encapsulation for a pseudowire using the encapsulation l2tpv3 command, you cannot enter the interworking ethernet command.
•
On Ethernet SPAs on the Cisco 12000 series Internet router, the only frame format supported for L2TPv3 interworking is Ethernet Version 2 (also known as Ethernet II) with the Ether type 0x0800 value set as Internet Protocol Payload and [optionally] 802.1q VLAN.
Ethernet packets with other Ethernet frame formats are dropped.
•
The Cisco 10720 Internet router supports Ethernet to VLAN Interworking Ethernet only over L2TPv3.
•
Ethernet interworking for a raw Ethernet port or a VLAN trunk is not supported. Traffic streams are not kept separate when traffic is sent between transport types.
•
In routed mode, only one CE router can be attached to an Ethernet PE router.
•
There must be a one-to-one relationship between an attachment circuit and the pseudowire. Point-to-multipoint or multipoint-to-point configurations are not supported.
•
Configure routing protocols for point-to-point operation on the CE routers when configuring an Ethernet to non-Ethernet setup.
•
In the IP interworking mode, the IPv4 (0800) translation is supported. The PE router captures ARP (0806) packets and responds with its own MAC address (proxy ARP). Everything else is dropped.
•
The Ethernet or VLAN must contain only two IP devices: PE router and CE router. The PE router performs proxy ARP and responds to all ARP requests it receives. Therefore, only one CE and one PE router should be on the Ethernet or VLAN segment.
•
If the CE routers are doing static routing, you can perform the following tasks:
–
The PE router needs to learn the MAC address of the CE router to correctly forward traffic to it. The Ethernet PE router sends an Internet Control Message Protocol (ICMP) Router discovery protocol (RDP) solicitation message with the source IP address as zero. The Ethernet CE router responds to this solicitation message. To configure the Cisco CE router's Ethernet or VLAN interface to respond to the ICMP RDP solicitation message, issue the ip irdp command in interface configuration mode. If you do not configure the CE router, traffic is dropped until the CE router sends traffic toward the PE router.
–
To disable the CE routers from running the router discovery protocol, issue the ip irdp maxadvertinterval 0 command in interface mode.
•
When the PE router on the Ethernet side receives a VLAN tagged packet from the CE router, the PE router removes the VLAN tag from the Ethernet frame from the CE router. In the reverse direction, the PE router adds the VLAN tag to the frames before sending the frame to the CE router. The VLAN tag needs to be inserted or removed in this way when you configure VLAN to Ethernet interworking, VLAN to Frame Relay, or ATM using Ethernet (bridged) interworking.
This restriction applies if you configure interworking between Ethernet and VLAN with Catalyst switches as the CE routers. The spanning tree protocol is supported for Ethernet interworking. Ethernet interworking between an Ethernet port and a VLAN supports spanning tree protocol only on VLAN 1. Configure VLAN 1 as a nonnative VLAN.
•
In bridged interworking from VLAN to Frame Relay, the Frame Relay PE router does not strip off VLAN tags from the Ethernet traffic it receives.
•
When you change the interworking configuration on an Ethernet PE router, clear the ARP entry on the adjacent CE router so that it can learn the new MAC address. Otherwise, you might experience traffic drops.
Frame Relay Interworking Restrictions
The following restrictions apply to Frame Relay interworking:
•
The attachment circuit maximum transmission unit (MTU) sizes must match when you connect them over MPLS. By default, the MTU size associated with a Frame Relay DLCI is the interface MTU. This may cause problems, for example, when connecting some DLCIs on a PoS interface (with a default MTU of 4470 bytes) to Ethernet or VLAN (with a default MTU of 1500 bytes) and other DLCIs on the same PoS interface to ATM (with a default MTU of 4470 bytes). To avoid reducing all the interface MTUs to the lowest common denominator (1500 bytes in this case), you can specify the MTU for individual DLCIs using the mtu command.
•
Only DLCI mode is supported. Port mode is not supported.
•
Configure Frame Relay switching to use DCE or Network-to-Network Interface (NNI). DTE mode does not report status in the Local Management Interface (LMI) process. If a Frame Relay over MPLS circuit goes down and the PE router is in DTE mode, the CE router is never informed of the disabled circuit. You must configure the frame-relay switching command in global configuration mode in order to configure DCE or NNI.
•
Frame Relay policing is non-distributed on the Cisco 7500 series routers. If you enable Frame Relay policing, traffic is sent to the RSP for processing.
•
Inverse ARP is not supported with IP interworking. CE routers must use point-to-point subinterfaces or static maps.
•
The PE router automatically supports translation of both the Cisco encapsulations and the
Internet Engineering Task Force (IETF) encapsulations that come from the CE, but translates only to IETF when sending to the CE router. This is not a problem for the Cisco CE router, because it can handle IETF encapsulation on receipt even if it is configured to send Cisco encapsulation.•
With Ethernet interworking, the following translations are supported:
–
Ethernet without LAN FCS (0300800080C20007 or 6558)
–
Spanning tree (0300800080C2000E or 4242)
All other translations are dropped.
•
With IP interworking, the IPv4 (03CC or 0800) translation is supported. All other translations are dropped.
•
PVC status signaling works the same way as in like-to-like case. The PE router reports the PVC status to the CE router, based on the availability of the pseudowire. PVC status detected by the PE router will also be reflected into the pseudowire. LMI to OAM interworking is supported when you connect Frame Relay to ATM.
PPP Interworking Restrictions
The following restrictions apply to PPP interworking:
•
There must be a one-to-one relationship between a PPP session and the pseudowire. Multiplexing of multiple PPP sessions over the pseudowire is not supported.
•
There must be a one-to-one relationship between a PPP session and a Frame Relay DLCI. Each Frame Relay PVC must have only one PPP session.
•
Only IP (IPv4 (0021) interworking is supported. Link Control Protocol (LCP) packets and Internet Protocol Control Protocol (IPCP) packets are terminated at the PE router. Everything else is dropped.
•
Proxy IPCP is automatically enabled on the PE router when IP interworking is configured on the pseudowire.
•
By default, the PE router assumes that the CE router knows the remote CE router's IP address.
•
Password Authentication Protocol (PAP) and Challenge-Handshake Authentication Protocol (CHAP) authentication are supported.
Information About L2VPN Interworking
The following sections provide an introduction to L2VPN interworking.
•
Overview of L2VPN Interworking
Overview of L2VPN Interworking
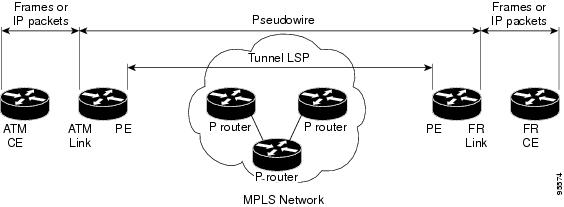
Layer 2 transport over MPLS and IP already exists for like-to-like attachment circuits, such as Ethernet-to-Ethernet or PPP-to-PPP. L2VPN Interworking builds on this functionality by allowing disparate attachment circuits to be connected. An interworking function facilitates the translation between the different Layer 2 encapsulations. Figure 1 is an example of Layer 2 interworking, where ATM and Frame Relay packets travel over the MPLS cloud.
Figure 1 ATM to Frame Relay Interworking Example
The L2VPN Interworking feature supports Ethernet, 802.1Q (VLAN), Frame Relay, ATM AAL5, and PPP attachment circuits over MPLS and L2TPv3. The features and restrictions for like-to-like functionality also apply to L2VPN Interworking.
L2VPN Interworking Modes
L2VPN Interworking works in either Ethernet ("bridged") mode or IP ("routed") mode. You specify the mode by issuing the interworking {ethernet | ip} command in pseudowire-class configuration mode.
The interworking command causes the attachment circuits to be terminated locally. The two keywords perform the following functions:
•
The ethernet keyword causes Ethernet frames to be extracted from the attachment circuit and sent over the pseudowire. Ethernet end-to-end transmission is assumed. Attachment circuit frames that are not Ethernet are dropped. In the case of VLAN, the VLAN tag is removed, leaving an untagged Ethernet frame.
•
The ip keyword causes IP packets to be extracted from the attachment circuit and sent over the pseudowire. Attachment circuit frames that do not contain IPv4 packets are dropped.
The supported L2VPN Interworking features are listed in Table 4.
Note
The Cisco 7600 series routers do not support L2VPN Interworking over L2TPv3.
The following sections explain more about Ethernet and IP interworking modes.
Ethernet Interworking
Ethernet Interworking is also called bridged interworking. Ethernet frames are bridged across the pseudowire. The CE routers could be natively bridging Ethernet or could be routing using a bridged encapsulation model, such as Bridge Virtual Interface (BVI) or RBE. The PE routers operate in Ethernet like-to-like mode.
This mode is used to offer the following services:
•
LAN services—An example is an enterprise that has several sites, where some sites have Ethernet connectivity to the service provider (SP) network and others have ATM connectivity. The enterprise wants LAN connectivity to all its sites. In this case, traffic from the Ethernet or VLAN of one site can be sent through the IP/MPLS network and encapsulated as bridged traffic over an ATM VCof another site.
•
Connectivity services—An example is an enterprise that has different sites that are running an Internal Gateway Protocol (IGP) routing protocol, which has incompatible procedures on broadcast and nonbroadcast links. The enterprise has several sites that are running an IGP, such as Open Shortest Path First (OSPF) or Intermediate System to Intermediate System (IS-IS), between the sites. In this scenario, some of the procedures (such as route advertisement or designated router) depend on the underlying Layer 2 protocol and are different for a point-to-point ATM connection versus a broadcast Ethernet connection. Therefore, the bridged encapsulation over ATM can be used to achieve homogenous Ethernet connectivity between the CE routers running the IGP.
IP Interworking
IP Interworking is also called routed interworking. The CE routers encapsulate IP on the link between the CE and PE routers. A new VC type is used to signal the IP pseudowire in MPLS and L2TPv3. Translation between the Layer 2 and IP encapsulations across the pseudowire is required. Special consideration needs to be given to address resolution and routing protocol operation, because these are handled differently on different Layer 2 encapsulations.
This mode is used to provide IP connectivity between sites, regardless of the Layer 2 connectivity to these sites. It is different from a Layer 3 VPN because it is point-to-point in nature and the service provider does not maintain any customer routing information.
Address resolution is encapsulation dependent:
•
Ethernet uses ARP
•
Frame Relay and ATM use Inverse ARP
•
PPP uses IPCP
Therefore, address resolution must be terminated on the PE router. End-to-end address resolution is not supported. Routing protocols operate differently over broadcast and point-to-point media. For Ethernet, the CE routers must either use static routing or configure the routing protocols to treat the Ethernet side as a point-to-point network.
How to Configure L2VPN Interworking
The following sections explain the tasks you can perform to configure L2VPN Interworking:
•
Configuring L2VPN Interworking (required)
•
Configuring Static IP Addresses for L2VPN Interworking for PPP (optional)
•
Verifying the L2VPN Interworking Configuration (optional)
Configuring L2VPN Interworking
Configuring the L2VPN Interworking feature requires that you add the interworking command to the list of commands that make up the pseudowire. The steps for configuring the pseudowire for L2VPN Interworking are included in this section. You use the interworking command as part of the overall AToM or L2TPv3 configuration. For specific instructions on configuring Any Transport over MPLS (AToM) or L2TPv3, see the following documents:
•
Layer 2 Tunnel Protocol Version 3
SUMMARY STEPS
1.
enable
2.
configure terminal
3.
hw-module slot slot-number np mode feature
4.
pseudowire-class name
5.
encapsulation {mpls | l2tpv3}
6.
interworking {ethernet | ip}
DETAILED STEPS
Configuring Static IP Addresses for L2VPN Interworking for PPP
If the PE router needs to perform address resolution with the local CE router for PPP, you can configure the remote CE router's IP address on the PE router. Issue the ppp ipcp address proxy command with the remote CE router's IP address on the PE router's xconnect PPP interface. The following example shows a sample configuration:
pseudowire-class ip-interworkingencapsulation mplsinterworking ipinterface Serial2/0encapsulation pppxconnect 10.0.0.2 200 pw-class ip-interworkingppp ipcp address proxy 10.65.32.14You can also configure the remote CE router's IP address on the local CE router with the peer default ip address command if the local CE router performs address resolution.
Verifying the L2VPN Interworking Configuration
To verify the L2VPN Interworking configuration, you can use the following commands.
SUMMARY STEPS
1.
show l2tun session all (L2TPv3 only)
2.
show arp
3.
ping
4.
show l2tun session interworking (L2TPv3 only)
5.
show mpls l2transport vc detail (AToM only)
DETAILED STEPS
Step 1
show l2tun session all (L2TPv3 only)
For L2TPv3, you can verify the L2VPN Interworking configuration using the show l2tun session all command on the PE routers.
In the following example, the interworking type is shown in bold.
Step 2
show arp
You can issue show arp command between the CE routers to ensure that data is being sent:
Router# show arpProtocol Address Age (min) Hardware Addr Type InterfaceInternet 10.1.1.5 134 0005.0032.0854 ARPA FastEthernet0/0Internet 10.1.1.7 - 0005.0032.0000 ARPA FastEthernet0/0Step 3
ping
You can issue ping command between the CE routers to ensure that data is being sent:
Router# ping 10.1.1.5Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 10.1.1.5, timeout is 2 seconds:!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 msStep 4
show l2tun session interworking (L2TPv3 only)
To verify that the interworking type is correctly set, use the show l2tun session interworking command. Enter the command on the PE routers that are performing the interworking translation.
•
In Example 1, the PE router performs the raw Ethernet translation. The command output displays the interworking type with a dash (-).
•
In Example 2, the PE router performs the Ethernet VLAN translation. The command output displays the interworking type as ETH.
Example 1 Command Output for Raw Ethernet Translation
Router# show l2tun session interworkingSession Information Total tunnels 1 sessions 1LocID TunID Peer-address Type IWrk Username, Intf/Vcid, Circuit15736 35411 10.9.9.9 ETH - 123, Fa1/1/0Example 2 Command Output for Ethernet VLAN Translation
Router# show l2tun session interworkingSession Information Total tunnels 1 sessions 1LocID TunID Peer-address Type IWrk Username, Intf/Vcid, Circuit26570 46882 10.8.8.8 VLAN ETH 123, Fa2/0.1:10Step 5
show mpls l2transport vc detail (AToM only)
You can verify the AToM configuration by using the show mpls l2transport vc detail command. In the following example, the interworking type is shown in bold.
Configuration Examples for L2VPN Interworking
The following sections show examples of L2VPN Interworking:
•
Ethernet to VLAN over L2TPV3 (Bridged): Example
•
Ethernet to VLAN over AToM (Bridged): Example
•
Frame Relay to VLAN over L2TPV3 (Routed): Example
•
Frame Relay to VLAN over AToM (Routed): Example
•
Frame Relay to ATM AAL5 over AToM (Routed): Example
•
VLAN to ATM AAL5 over AToM (Bridged): Example
•
Frame Relay to PPP over L2TPv3 (Routed): Example
•
Frame Relay to PPP over AToM (Routed): Example
•
Ethernet/VLAN to PPP over AToM (Routed): Example
Ethernet to VLAN over L2TPV3 (Bridged): Example
The following example shows the configuration of Ethernet to VLAN over L2TPv3:
Ethernet to VLAN over AToM (Bridged): Example
The following example shows the configuration of Ethernet to VLAN over AToM:
Frame Relay to VLAN over L2TPV3 (Routed): Example
The following example shows the configuration of Frame Relay to VLAN over L2TPv3:
Frame Relay to VLAN over AToM (Routed): Example
The following example shows the configuration of Frame Relay to VLAN over AToM:
Frame Relay to ATM AAL5 over AToM (Routed): Example
Note
Frame Relay to ATM AAL5 is available only with AToM in IP mode.
The following example shows the configuration of Frame Relay to ATM AAL5 over AToM:
VLAN to ATM AAL5 over AToM (Bridged): Example
The following example shows the configuration of VLAN to ATM AAL5 over AToM:
Frame Relay to PPP over L2TPv3 (Routed): Example
The following example shows the configuration of Frame Relay to PPP over L2TPv3:
Frame Relay to PPP over AToM (Routed): Example
The following example shows the configuration of Frame Relay to PPP over AToM:
Ethernet/VLAN to PPP over AToM (Routed): Example
The following example shows the configuration of Ethernet VLAN to PPP over AToM:
Additional References
The following sections provide references related to the L2VPN Interworking feature.
Related Documents
Layer 2 Tunnel Protocol Version 3
Any Transport over MPLS
Cisco 12000 series router shared port adaptors
Cisco 12000 Series Router SIP and SPA Software Configuration Guide
Standards
MIBs
RFCs
No new or modified RFCs are supported by this feature, and support for existing RFCs has not been modified by this feature.
—
Technical Assistance
Command Reference
This section documents only commands that are new or modified.
•
mtu
debug frame-relay pseudowire
To display events and error conditions that occur when binding a Frame Relay data-link connection identifier (DLCI) to a pseudowire, use the debug frame-relay pseudowire command in privileged EXEC mode. To disable the display of these events and error conditions, use the no form of this command.
debug frame-relay pseudowire
no debug frame-relay pseudowire
Syntax Description
This command contains no arguments or keywords.
Command Default
DLCI events and errors are not displayed.
Command Modes
Privileged EXEC (#)
Command History
Usage Guidelines
The following are examples of Frame Relay pseudowire events:
•
Command-line interface (CLI) provisioning events
•
Pseudowire circuit status updates
•
Failures occurring during the management of these events
Examples
The following example enables the display of Frame Relay pseudowire events. In this example, the interface has been shut down and then enabled.
Router# debug frame-relay pseudowireRouter(config)# interface hssi1/0/0Router(config-if)# shutdown09:18:33.303: FRoPW [10.15.15.15, 100]: acmgr_circuit_down09:18:33.303: FRoPW [10.15.15.15, 100]: SW AC update circuit state to down09:18:33.303: FRoPW [10.15.15.15, 100]: Setting connection DOWN09:18:35.299: %LINK-5-CHANGED: Interface Hssi1/0/0, changed state to administratively down09:18:36.299: %LINEPROTO-5-UPDOWN: Line protocol on Interface Hssi1/0/0, changed state to downRouter(config-if)# no shutdown09:18:41.919: %LINK-3-UPDOWN: Interface Hssi1/0/0, changed state to up09:18:41.919: FRoPW [10.15.15.15, 100]: Local up, sending acmgr_circuit_up09:18:41.919: FRoPW [10.15.15.15, 100]: Setting pw segment UP09:18:41.919: FRoPW [10.15.15.15, 100]: PW nni_pvc_status set ACTIVE09:18:41.919: label_oce_get_label_bundle: flags 14 label 2809:18:42.919: %LINEPROTO-5-UPDOWN: Line protocol on Interface Hssi1/0/0, changed state to upTable 5 describes the significant fields shown in the display.
debug ssm
To display diagnostic information about the Segment Switching Manager (SSM) for switched Layer 2 segments, use the debug ssm command in privileged EXEC mode. To disable debugging, use the no form of this command.
debug ssm {cm errors | cm events | fhm errors | fhm events | sm errors | sm events | sm counters | xdr}
no debug ssm {cm errors | cm events | fhm errors | fhm events | sm errors | sm events | sm counters | xdr}
Syntax Description
Command Modes
Privileged EXEC (#)
Command History
Usage Guidelines
The SSM manages the data-plane component of the Layer 2 Virtual Private Network (L2VPN) configuration. The CM tracks the connection-level errors and events that occur on an xconnect.
The SM tracks the per-segment events and errors on the xconnect. Use the debug ssm command to troubleshoot problems in bringing up the data plane.
This command is generally used only by Cisco engineers for internal debugging of SSM processes.
Examples
The following example shows sample output for the debug ssm xdr command:
Router# debug ssm xdrSSM xdr debugging is on2w5d: SSM XDR: [4096] deallocate segment, len 162w5d: SSM XDR: [8193] deallocate segment, len 162w5d: %LINK-3-UPDOWN: Interface FastEthernet2/1, changed state to down2w5d: %LINK-3-UPDOWN: Interface FastEthernet2/1, changed state to up2w5d: SSM XDR: [4102] provision segment, switch 4101, len 1062w5d: SSM XDR: [4102] update segment status, len 172w5d: SSM XDR: [8199] provision segment, switch 4101, len 2062w5d: SSM XDR: [4102] update segment status, len 172w5d: %SYS-5-CONFIG_I: Configured from console by console2w5d: %LINK-3-UPDOWN: Interface FastEthernet2/1, changed state to down2w5d: SSM XDR: [4102] update segment status, len 172w5d: %LINK-3-UPDOWN: Interface FastEthernet2/1, changed state to up2w5d: SSM XDR: [4102] deallocate segment, len 162w5d: SSM XDR: [8199] deallocate segment, len 162w5d: SSM XDR: [4104] provision segment, switch 4102, len 1062w5d: SSM XDR: [4104] update segment status, len 172w5d: SSM XDR: [8201] provision segment, switch 4102, len 2062w5d: SSM XDR: [4104] update segment status, len 172w5d: SSM XDR: [4104] update segment status, len 172w5d: %SYS-5-CONFIG_I: Configured from console by consoleThe following example shows the events that occur on the segment manager when an Any Transport over MPLS (AToM) virtual circuit (VC) configured for Ethernet over MPLS is shut down and then enabled:
Router# debug ssm sm eventsSSM Connection Manager events debugging is onRouter(config)# interface fastethernet 0/1/0.1Router(config-subif)# shutdown09:13:38.159: SSM SM: [SSS:AToM:36928] event Unprovison segment09:13:38.159: SSM SM: [SSS:Ethernet Vlan:4146] event Unbind segment09:13:38.159: SSM SM: [SSS:AToM:36928] free segment class09:13:38.159: SSM SM: [SSS:AToM:36928] free segment09:13:38.159: SSM SM: [SSS:AToM:36928] event Free segment09:13:38.159: SSM SM: last segment class freed09:13:38.159: SSM SM: [SSS:Ethernet Vlan:4146] segment ready09:13:38.159: SSM SM: [SSS:Ethernet Vlan:4146] event Found segment dataRouter(config-subif)# no shutdown09:13:45.815: SSM SM: [SSS:AToM:36929] event Provison segment09:13:45.815: label_oce_get_label_bundle: flags 14 label 1609:13:45.815: SSM SM: [SSS:AToM:36929] segment ready09:13:45.815: SSM SM: [SSS:AToM:36929] event Found segment data09:13:45.815: SSM SM: [SSS:AToM:36929] event Bind segment09:13:45.815: SSM SM: [SSS:Ethernet Vlan:4146] event Bind segmentThe following example shows the events that occur on the CM when an AToM VC configured for Ethernet over MPLS is shut down and then enabled:
Router(config)# interface fastethernet 0/1/0.1Router(config-subif)# shutdown09:17:20.179: SSM CM: [AToM] unprovision segment, id 3692909:17:20.179: SSM CM: CM FSM: state Open - event Free segment09:17:20.179: SSM CM: [SSS:AToM:36929] unprovision segment 109:17:20.179: SSM CM: [SSS:AToM] shQ request send unprovision complete event09:17:20.179: SSM CM: [SSS:Ethernet Vlan:4146] unbind segment 209:17:20.179: SSM CM: [SSS:Ethernet Vlan] shQ request send ready event09:17:20.179: SSM CM: SM msg event send unprovision complete event09:17:20.179: SSM CM: SM msg event send ready eventRouter(config-subif)# no shutdown09:17:35.879: SSM CM: Query AToM to Ethernet Vlan switching, enabled09:17:35.879: SSM CM: [AToM] provision second segment, id 3693009:17:35.879: SSM CM: CM FSM: state Down - event Provision segment09:17:35.879: SSM CM: [SSS:AToM:36930] provision segment 209:17:35.879: SSM CM: [AToM] send client event 6, id 3693009:17:35.879: SSM CM: [SSS:AToM] shQ request send ready event09:17:35.883: SSM CM: SM msg event send ready event09:17:35.883: SSM CM: [AToM] send client event 3, id 36930The following example shows the events that occur on the CM and SM when an AToM VC is provisioned and then unprovisioned:
Router# debug ssm cm eventsSSM Connection Manager events debugging is onRouter# debug ssm sm eventsSSM Segment Manager events debugging is onRouter# configure terminalRouter(config)# interface ethernet1/0Router(config-if)# xconnect 10.55.55.2 101 pw-class mpls16:57:34: SSM CM: provision switch event, switch id 8604016:57:34: SSM CM: [Ethernet] provision first segment, id 1231316:57:34: SSM CM: CM FSM: state Idle - event Provision segment16:57:34: SSM CM: [SSS:Ethernet:12313] provision segment 116:57:34: SSM SM: [SSS:Ethernet:12313] event Provison segment16:57:34: SSM CM: [SSS:Ethernet] shQ request send ready event16:57:34: SSM CM: SM msg event send ready event16:57:34: SSM SM: [SSS:Ethernet:12313] segment ready16:57:34: SSM SM: [SSS:Ethernet:12313] event Found segment data16:57:34: SSM CM: Query AToM to Ethernet switching, enabled16:57:34: SSM CM: [AToM] provision second segment, id 1641016:57:34: SSM CM: CM FSM: state Down - event Provision segment16:57:34: SSM CM: [SSS:AToM:16410] provision segment 216:57:34: SSM SM: [SSS:AToM:16410] event Provison segment16:57:34: SSM CM: [AToM] send client event 6, id 1641016:57:34: label_oce_get_label_bundle: flags 14 label 1916:57:34: SSM CM: [SSS:AToM] shQ request send ready event16:57:34: SSM CM: SM msg event send ready event16:57:34: SSM SM: [SSS:AToM:16410] segment ready16:57:34: SSM SM: [SSS:AToM:16410] event Found segment data16:57:34: SSM SM: [SSS:AToM:16410] event Bind segment16:57:34: SSM SM: [SSS:Ethernet:12313] event Bind segment16:57:34: SSM CM: [AToM] send client event 3, id 16410Router# configure terminalRouter(config)# interface e1/0Router(config-if)# no xconnect16:57:26: SSM CM: [Ethernet] unprovision segment, id 1638716:57:26: SSM CM: CM FSM: state Open - event Free segment16:57:26: SSM CM: [SSS:Ethernet:16387] unprovision segment 116:57:26: SSM SM: [SSS:Ethernet:16387] event Unprovison segment16:57:26: SSM CM: [SSS:Ethernet] shQ request send unprovision complete event16:57:26: SSM CM: [SSS:AToM:86036] unbind segment 216:57:26: SSM SM: [SSS:AToM:86036] event Unbind segment16:57:26: SSM CM: SM msg event send unprovision complete event16:57:26: SSM SM: [SSS:Ethernet:16387] free segment class16:57:26: SSM SM: [SSS:Ethernet:16387] free segment16:57:26: SSM SM: [SSS:Ethernet:16387] event Free segment16:57:26: SSM SM: last segment class freed16:57:26: SSM CM: unprovision switch event, switch id 1229016:57:26: SSM CM: [SSS:AToM] shQ request send unready event16:57:26: SSM CM: SM msg event send unready event16:57:26: SSM SM: [SSS:AToM:86036] event Unbind segment16:57:26: SSM CM: [AToM] unprovision segment, id 8603616:57:26: SSM CM: CM FSM: state Down - event Free segment16:57:26: SSM CM: [SSS:AToM:86036] unprovision segment 216:57:26: SSM SM: [SSS:AToM:86036] event Unprovison segment16:57:26: SSM CM: [SSS:AToM] shQ request send unprovision complete event16:57:26: SSM CM: SM msg event send unprovision complete event16:57:26: SSM SM: [SSS:AToM:86036] free segment class16:57:26: SSM SM: [SSS:AToM:86036] free segment16:57:26: SSM SM: [SSS:AToM:86036] event Free segment16:57:26: SSM SM: last segment class freedRelated Commands
interworking
To enable the L2VPN Interworking feature, use the interworking command in pseudowire class configuration mode. To disable the L2VPN Interworking feature, use the no form of this command.
interworking {ethernet | ip}
no interworking {ethernet | ip}
Syntax Description
Command Default
L2VPN Interworking is not enabled.
Command Modes
Pseudowire class configuration (config-pw)
Command History
Usage Guidelines
Table 6 shows which L2VPN Interworking features support Ethernet, IP, or both types of interworking.
Examples
The following example shows a pseudowire class configuration that enables the L2VPN Interworking feature:
Router(config)# pseudowire-class ip-interworkingRouter(config-pw)# encapsulation mplsRouter(config-pw)# interworking ipRelated Commands
mtu
To adjust the maximum packet size or maximum transmission unit (MTU) size, use the mtu command in interface configuration mode or connect submode. To restore the MTU value to its original default value, use the no form of this command.
mtu bytes
no mtu
Syntax Description
Command Default
Table 7 lists default MTU values according to media type.
Table 7 Default Media MTU Values
Ethernet
1500
Serial
1500
Token Ring
4464
ATM
4470
FDDI
4470
HSSI (HSA)
4470
Command Modes
Interface configuration (config-if)
Connect submode (for Frame Relay Layer 2 Interworking)Command History
Usage Guidelines
Each interface has a default maximum packet size or MTU size. This number generally defaults to the largest size possible for that interface type. On serial interfaces, the MTU size varies, but cannot be set to a value less than 64 bytes.
Note
Changing the MTU size is not supported on a loopback interface.
Note
Changing an MTU size on a Cisco 7500 series router results in the recarving of buffers and resetting of all interfaces. The following message is displayed:
%RSP-3-Restart:cbus complex.
Note
You can configure native Gigabit Ethernet ports on the Cisco 7200 series router to a maximum MTU size of 9216 bytes. The MTU values range from 1500 to 9216 bytes.
Protocol-Specific Versions of the mtu Command
Changing the MTU value with the mtu interface configuration command can affect values for the protocol-specific versions of the command (the ip mtu command, for example). If the value specified with the ip mtu interface configuration command is the same as the value specified with the mtu interface configuration command, and you change the value for the mtu interface configuration command, the ip mtu value automatically matches the new mtu interface configuration command value. However, changing the values for the ip mtu configuration commands has no effect on the value for the mtu interface configuration command.
ATM and LANE Interfaces
ATM interfaces are not bound by what is configured on the major interface. By default, MTU on a subinterface is equal to the default MTU (4490); if a client is configured the default is 1500. MTU can be changed on subinterfaces, but it may result in recarving of buffers to accommodate the new maximum MTU on the interface.
Examples
The following example specifies an MTU of 1000 bytes:
Router(config)# interface serial 1Router(config-if)# mtu 1000Related Commands
encapsulation smds
Enables SMDS service on the desired interface.
ip mtu
Sets the MTU size of IP packets sent on an interface.
show l2tun session
To display the current state of Layer 2 sessions and protocol information about Layer 2 Tunnel Protocol (L2TP) control channels, use the show l2tun session command in privileged EXEC mode.
show l2tun session [all [filter] | brief [filter] [hostname] | circuit [filter] [hostname] | interworking [filter] [hostname] | packets [filter] | sequence [filter] | state [filter]]
Syntax Description
all
(Optional) Displays information about all current L2TP sessions on the router.
filter
(Optional) One of the filter parameters defined in Table 8.
brief
(Optional) Displays information about all current L2TP sessions, including peer ID address and circuit status of the L2TP sessions.
hostname
(Optional) Specifies that the peer hostname will be displayed in the output.
circuit
(Optional) Displays information about all current L2TP sessions, including circuit status (up or down).
interworking
(Optional) Displays information about Layer 2 Virtual Private Network (L2VPN) interworking.
packets
(Optional) Displays information about the packet counters (in and out) associated with current L2TP sessions.
sequence
(Optional) Displays sequencing information about each L2TP session, including number of out-of-order and returned packets.
state
(Optional) Displays information about all current L2TP sessions and their protocol state, including remote Virtual Connection Identifier (VCIDs).
Command Modes
Privileged EXEC (#)
Command History
Usage Guidelines
Use the show l2tun session command to display information about current L2TP sessions on the router.
Table 8 defines the filter parameters available to refine the output of the show l2tun session command.
Examples
The following example shows how to display detailed information about all current L2TP sessions:
Router# show l2tun session allSession Information Total tunnels 0 sessions 1Session id 42438 is down, tunnel id 45795Remote session id is 0, remote tunnel id 43092Session Layer 2 circuit, type is Ethernet, name is FastEthernet4/1/1Session vcid is 123456789Circuit state is DOWNLocal circuit state is DOWNRemote circuit state is DOWNCall serial number is 1463700128Remote tunnel name is PE1Internet address is 10.1.1.1Local tunnel name is PE1Internet address is 10.1.1.2IP protocol 115Session is L2TP signalledSession state is idle, time since change 00:00:260 Packets sent, 0 received0 Bytes sent, 0 receivedLast clearing of "show vpdn" counters neverReceive packets dropped:out-of-order: 0total: 0Send packets dropped:exceeded session MTU: 0total: 0DF bit off, ToS reflect disabled, ToS value 0, TTL value 255No session cookie information availableUDP checksums are disabledL2-L2 switching enabledNo FS cached header information availableSequencing is offUnique ID is 1The following example shows how to display information only about the L2TP session set up on a peer router with an IP address of 172.16.184.142 and a VCID of 300:
Router# show l2tun session all ip-addr 172.16.184.142 vcid 300L2TP SessionSession id 32518 is up, tunnel id 35217Call serial number is 2074900020Remote tunnel name is tun1Internet address is 172.16.184.142Session is L2TP signalledSession state is established, time since change 03:06:399932 Packets sent, 9932 received1171954 Bytes sent, 1171918 receivedSession vcid is 300Session Layer 2 circuit, type is Ethernet Vlan, name is FastEthernet0/1/0.3:3Circuit state is UPRemote session id is 18819, remote tunnel id 37340Set DF bit to 0Session cookie information:local cookie, size 4 bytes, value CF DC 5B F3remote cookie, size 4 bytes, value FE 33 56 C4SSS switching enabledSequencing is onNs 9932, Nr 10001, 0 out of order packets discardedTable 9 describes the significant fields shown in the displays.
The following example shows how to display information about the circuit status of L2TP sessions on a router:
Router# show l2tun session circuitSession Information Total tunnels 3 sessions 3LocID TunID Peer-address Type Stat Username, Intf/Vcid, Circuit32517 26515 172.16.184.142 VLAN UP 100, Fa0/1/0.1:132519 30866 172.16.184.142 VLAN UP 200, Fa0/1/0.2:232518 35217 172.16.184.142 VLAN UP 300, Fa0/1/0.3:3The following example shows how to display information about the circuit status of L2TP sessions and the hostnames of remote peers:
Router# show l2tun session circuit hostnameSession Information Total tunnels 3 sessions 3LocID TunID Peer-hostname Type Stat Username, Intf/Vcid, Circuit32517 26515 <unknown> VLAN UP 100, Fa0/1/0.1:132519 30866 router32 VLAN UP 200, Fa0/1/0.2:232518 35217 access3 VLAN UP 300, Fa0/1/0.3:3Table 10 describes the significant fields shown in the displays.
Related Commands
show l2tun tunnel
To display the current state of Layer 2 Tunneling Protocol (L2TP) tunnels and information about configured tunnels, including local and remote hostnames, aggregate packet counts, and control channel information, use the show l2tun tunnel command in privileged EXEC mode.
Cisco IOS Release 12.0(30)S and Earlier Releases, Cisco IOS Release 12.3(2)T and Later Releases
show l2tun tunnel [all [filter] | packets [filter] | state [filter] | summary [filter] | transport [filter]]
Cisco IOS Release 12.0(31)S and Later Releases
show l2tun tunnel [all [filter] | packets [filter] | state [filter] | summary [filter] | transport [filter] | authentication]
Syntax Description
all
(Optional) Displays information about all current L2TP sessions configured on the router.
filter
(Optional) One of the filter parameters defined in Table 11.
packets
(Optional) Displays aggregate packet counts for all negotiated L2TP sessions.
state
(Optional) Displays information about the current state of L2TP sessions, including the local and remote hostnames for each control channel.
summary
(Optional) Displays a summary of L2TP sessions on the router and their current state, including the number of virtual private dialup network (VPDN) sessions associated with each control channel.
transport
(Optional) Displays information about the L2TP control channels used in each session and the local and remote IP addresses at each end of the control channel.
authentication
(Optional) Displays global information about L2TP control channel authentication attribute-value pairs (AV pairs).
Command Modes
Privileged EXEC (#)
Command History
Usage Guidelines
Use the show l2tun tunnel command to display information about configured L2TP sessions on the router.
Table 11 defines the filter parameters available to refine the output of the show l2tun tunnel command.
Examples
The following example shows how to display detailed information about all L2TP tunnels:
Router# show l2tun tunnel allTunnel Information Total tunnels 1 sessions 1Tunnel id 26515 is up, remote id is 41814, 1 active sessionsTunnel state is established, time since change 03:11:50Tunnel transport is IP (115)Remote tunnel name is tun1Internet Address 172.16.184.142, port 0Local tunnel name is RouterInternet Address 172.16.184.116, port 0Tunnel domain isVPDN group for tunnel isL2TP class for tunnel is0 packets sent, 0 received0 bytes sent, 0 receivedControl Ns 11507, Nr 11506Local RWS 2048 (default), Remote RWS 800Tunnel PMTU checking disabledRetransmission time 1, max 1 secondsUnsent queuesize 0, max 0Resend queuesize 1, max 1Total resends 0, ZLB ACKs sent 11505Total peer authentication failures 8Current nosession queue check 0 of 5Retransmit time distribution: 0 0 0 0 0 0 0 0 0Sessions disconnected due to lack of resources 0The following example shows the display of pseudowire control channel password information:
Router# show l2tun tunnel all!Control message authentication is on, 2 secrets configuredLast message authenticated with first digest secret!Table 12 describes the significant fields shown in the displays.
The following example shows how to filter information to display L2TP control channel details only for the sessions configured with the local name Router and the remote name tun1:
Router# show l2tun tunnel transport local-name Router tun1Tunnel Information Total tunnels 3 sessions 3LocID Type Prot Local Address Port Remote Address Port26515 IP 115 172.16.184.116 0 172.16.184.142 030866 IP 115 172.16.184.116 0 172.16.184.142 035217 IP 115 172.16.184.116 0 172.16.184.142 0Table 13 describes the significant fields shown in the display.
The following example shows how to display information about the current state of L2TP sessions with the local and remote hostnames of each session:
Router# show l2tun tunnel stateLocID RemID Local Name Remote Name State Last-Chg26515 41814 Router tun1 est 03:13:1530866 6809 Router tun1 est 03:13:1535217 37340 Router tun1 est 03:13:15Table 14 describes the significant fields shown in the display.
The following example shows the display of all possible L2TP control channel authentication AV pair statistics. AV pair statistic fields are displayed only if they are nonzero. For the purposes of this example, all possible output fields are displayed in the sample output.
This example is valid for Cisco IOS Release 12.0(31)S and later releases or Cisco IOS Release 12.2(27)SBC. To display authentication statistics in Cisco IOS Release 12.2(28)SB or a later release, use the monitor l2tun counters tunnel l2tp and show l2tun counters tunnel l2tp commands instead.
Router# show l2tun tunnel authenticationL2TPv3 Tunnel Authentication Statistics:Nonce AVP Statistics:Ignored 0Missing 0All Digests Statistics:Unexpected 0Unexpected ZLB 0Primary Digest AVP Statistics:Validate fail 0Hash invalid 0Length invalid 0Missing 0Ignored 0Passed 0Failed 0Secondary Digest AVP Statistics:Validate fail 0Hash invalid 0Length invalid 0Missing 0Ignored 0Passed 0Failed 0Integrity Check Statistics:Validate fail 0Length invalid 0Passed 0Failed 0Local Secret Statistics:Missing 0Challenge AVP Statistics:Generate response fail 0Ignored 0Challenge/Response AVP Statistics:Generate response fail 0Missing 0Ignored 0Passed 0Failed 0Overall Statistics:Passed 0Skipped 0Ignored 0Failed 0Table 15 describes the significant fields shown in the display.
Related Commands
show mpls l2transport vc
To display information about Any Transport over MPLS (AToM) virtual circuits (VCs) and static pseudowires that have been enabled to route Layer 2 packets on a router, use the show mpls l2transport vc command in privileged EXEC mode.
show mpls l2transport vc [vcid vc-id | vcid vc-id-min vc-id-max] [interface name [local-circuit-id]] [destination ip-address | name] [detail]
Syntax Description
Command Modes
Privileged EXEC (#)
Command History
Usage Guidelines
If you do not specify any keywords or arguments, the command displays a summary of all the VCs.
Examples
The output of the commands varies, depending on the type of Layer 2 packets being transported over the AToM VCs.
The following sample output shows information about the interfaces and VCs that have been configured to transport various Layer 2 packets on the router:
Router# show mpls l2transport vcLocal intf Local circuit Dest address VC ID Status------------- ------------------ --------------- ---------- ----------Se5/0 FR DLCI 55 10.0.0.1 55 UPAT4/0 ATM AAL5 0/100 10.0.0.1 100 UPAT4/0 ATM AAL5 0/200 10.0.0.1 200 UPAT4/0.300 ATM AAL5 0/300 10.0.0.1 300 UPTable 16 describes the fields shown in the display.
The following example shows information about the NSF/SSO and graceful restart capability. The SSO portion indicates when checkpointing data has either been sent (on active) or received (on standby). When SSO data has not been successfully sent or has been released, the SSO information is not shown.
Router# show mpls l2transport vc detailLocal interface: Fa5/1/1.2 down, line protocol down, Eth VLAN 2 upDestination address: 10.55.55.2, VC ID: 1002, VC status: downOutput interface: Se4/0/3, imposed label stack {16}Preferred path: not configuredDefault path: activeTunnel label: imp-null, next hop point2pointCreate time: 02:03:29, last status change time: 02:03:26Signaling protocol: LDP, peer 10.55.55.2:0 downMPLS VC labels: local 16, remote unassignedGroup ID: local 0, remote unknownMTU: local 1500, remote unknownRemote interface description:Sequencing: receive disabled, send disabledSSO Descriptor: 10.55.55.2/1002, local label: 16SSM segment/switch IDs: 12290/8193, PWID: 8193VC statistics:packet totals: receive 0, send 0byte totals: receive 0, send 0packet drops: receive 0, send 0The following example shows information provided when an AToM static pseudowire has been provisioned and the show mpls l2transport vc detail command is used to check the configuration. The Signaling protocol field specifies Manual, because a directed control protocol such as Label Distribution Protocol (LDP) cannot be used to exchange parameters on static pseudowires. The remote interface description field seen for nonstatic pseudowire configurations is not displayed, because remote information is exchanged using signaling between the PEs and this is not done on static pseudowires.
Router# show mpls l2transport vc detailLocal interface: Et1/0 up, line protocol up, Ethernet upDestination address: 10.1.1.2, VC ID: 100, VC status: upOutput interface: Et2/0, imposed label stack {10003 150}Preferred path: not configuredDefault path: activeNext hop: 10.0.0.2Create time: 00:18:57, last status change time: 00:16:10Signaling protocol: ManualMPLS VC labels: local 100, remote 150Group ID: local 0, remote 0MTU: local 1500, remote 1500Remote interface description:Sequencing: receive disabled, send disabledVC statistics:packet totals: receive 219, send 220byte totals: receive 20896, send 26694packet drops: receive 0, send 0Table 17 describes the significant fields shown in the displays.
The following example shows the command output of the show mpls l2transport vc detail command with when VPLS Autodiscovery has configured the VPLS pseudowires. The output that is specific to VPLS Autodiscovery is show in bold.
Router# show mpls l2transport vc detailLocal interface: VFI my_test VFI upMPLS VC type is VFI, interworking type is EthernetDestination address: 10.3.3.1, VC ID: 123456, VC status: upNext hop PE address: 10.55.55.2Output interface: Et3/0, imposed label stack {17 19}Preferred path: not configuredDefault path:Next hop: 10.1.0.2Create time: 2d05h, last status change time: 2d05hSignaling protocol: LDP, peer 10.55.55.2:0 upMPLS VC labels: local 21, remote 19AGI: type 1, len 8, 0000 3333 4F4E 44C4Local AII: type 1, len 4, 0909 0909 (10.9.9.9)Remote AII: type 1, len 4, 0303 0301 (10.3.3.3)Group ID: local 0, remote 0MTU: local 1500, remote 1500Remote interface description:Sequencing: receive disabled, send disabledVC statistics:packet totals: receive 22611, send 22611byte totals: receive 2346570, send 2853581packet drops: receive 0, send 0Table 18 describes the fields shown in the display.
Related Commands
Feature Information for L2VPN Interworking
Table 19 lists the release history for this feature.
Not all commands may be available in your Cisco IOS software release. For release information about a specific command, see the command reference documentation.
Cisco IOS software images are specific to a Cisco IOS software release, a feature set, and a platform. Use Cisco Feature Navigator to find information about platform support and Cisco IOS software image support. Access Cisco Feature Navigator at http://www.cisco.com/go/fn. You must have an account on Cisco.com. If you do not have an account or have forgotten your username or password, click Cancel at the login dialog box and follow the instructions that appear.
Note
Table 19 lists only the Cisco IOS software release that introduced support for a given feature in a given Cisco IOS software release train. Unless noted otherwise, subsequent releases of that Cisco IOS software release train also support that feature.
Table 19 Feature Information for L2VPN Interworking
L2VPN Interworking
12.0(26)S,
12.0(30)S,
12.0(32)S,
12.0(32)SY,
12.2(33)SRA,
12.4(11)T,
12.2(33)SXHThis feature allows disparate attachment circuits to be connected. An interworking function facilitates the translation between the different Layer 2 encapsulations.
This feature was introduced in Cisco IOS Release 12.0(26)S.
In Cisco IOS Release 12.0(30)S, support was added for Cisco 12000 series Internet routers.
In Cisco IOS Release 12.0(32)S, support was added on Engine 5 line cards (SIP-401, SIP-501, SIP-600, and SIP-601) in Cisco 12000 series routers for the following four transport types:
•
Ethernet/VLAN to Frame Relay Interworking
•
Ethernet/VLAN to ATM AAL5 Interworking
•
Ethernet to VLAN Interworking
•
Frame Relay to ATM AAL5 Interworking
On the Cisco 12000 series Internet router, support was added for IP Services Engine (ISE) and Engine 5 line cards that are configured for L2TPv3 tunneling (see Layer 2 Tunnel Protocol Version 3).
In Cisco IOS Release 12.2(33)SRA, support was added for the Cisco 7600 series routers.
In Cisco IOS Release 12.4(11)T, support was added for the following transport types:
•
Ethernet to VLAN Interworking
•
Ethernet/VLAN to Frame Relay Interworking
This feature was integrated into Cisco IOS Release 12.2(33)SXH.
CCVP, the Cisco logo, and the Cisco Square Bridge logo are trademarks of Cisco Systems, Inc.; Changing the Way We Work, Live, Play, and Learn is a service mark of Cisco Systems, Inc.; and Access Registrar, Aironet, BPX, Catalyst, CCDA, CCDP, CCIE, CCIP, CCNA, CCNP, CCSP, Cisco, the Cisco Certified Internetwork Expert logo, Cisco IOS, Cisco Press, Cisco Systems, Cisco Systems Capital, the Cisco Systems logo, Cisco Unity, Enterprise/Solver, EtherChannel, EtherFast, EtherSwitch, Fast Step, Follow Me Browsing, FormShare, GigaDrive, HomeLink, Internet Quotient, IOS, iPhone, IP/TV, iQ Expertise, the iQ logo, iQ Net Readiness Scorecard, iQuick Study, LightStream, Linksys, MeetingPlace, MGX, Networking Academy, Network Registrar, Packet, PIX, ProConnect, ScriptShare, SMARTnet, StackWise, The Fastest Way to Increase Your Internet Quotient, and TransPath are registered trademarks of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
All other trademarks mentioned in this document or Website are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (0705R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
© 2003-2004, 2006-2007 Cisco Systems, Inc. All rights reserved.