|
If you are experiencing a security vulnerability emergency, see the Reporting or Obtaining Support for a Suspected Security Vulnerability section of this document. ContentsCisco Product Security Incident Response
Reporting or Obtaining Support for a Suspected Security Vulnerability General Security-Related Queries Receiving Security Vulnerability Information from Cisco Public Relations or Press Queries Regarding Cisco Security Vulnerability Information Commitment to Product Security and Integrity at Cisco Cisco Secure Development Practices Cisco Product Security Incident Response Process Assessing Security Risk — Common Vulnerability Scoring System Third-Party Software Vulnerabilities Types of Security Publications Cisco Security Advisories
Communications PlanCisco Security Responses Cisco Event Responses Threat Outbreak Alerts Release Note Enclosures Disclosure Schedule Incident Response Eligibility Security Software Updates Cisco Product Security Incident ResponseThe Cisco Product Security Incident Response Team (PSIRT) is responsible for responding to Cisco product security incidents. The Cisco PSIRT is a dedicated, global team that manages the receipt, investigation, and public reporting of security vulnerability information that is related to Cisco products and networks. The on-call Cisco PSIRT works 24 hours with Cisco customers, independent security researchers, consultants, industry organizations, and other vendors to identify possible security issues with Cisco products and networks. Reporting or Obtaining Support for a Suspected Security VulnerabilityIndividuals or organizations that are experiencing a product security issue are strongly encouraged to contact the Cisco PSIRT. Cisco welcomes reports from independent researchers, industry organizations, vendors, customers, and other sources concerned with product or network security. The minimal data needed for reporting a security issue is a description of the potential vulnerability. Please contact the Cisco PSIRT using one of the following methods.
Cisco encourages the encryption of sensitive information that is sent to Cisco in email messages. The Cisco PSIRT supports encrypted messages via PGP/GNU Privacy Guard (GPG). The Cisco PSIRT team public key General Security-Related QueriesFor general security concerns about Cisco products, the Cisco Technical Assistance Center (TAC) can provide configuration assistance and technical assistance with security matters. The TAC can also help with nonsensitive security incidents and software upgrades for security bug fixes. Use the following information to contact the Cisco TAC.
Receiving Security Vulnerability Information from CiscoThere are several ways to stay connected and receive the latest security vulnerability information from Cisco. Review the following table, and subsequent summaries, to determine the appropriate option.
Cisco.comThe Cisco Security portal on Cisco.com provides Cisco security vulnerability documents and Cisco security functions information, including relevant security products and services. For direct links to specific security functions, see the Types of Security Publications section of this document. Cisco Security Advisories are clear signed with the Cisco PSIRT
PGP key cust-security-announce@cisco.com Only initial and major revisions to a Cisco Security Advisory are posted via email. If a document undergoes a minor revision, the update will be posted to Cisco.com without an accompanying email message. Customers who require automated minor revision alerts should subscribe to the Cisco Security Advisory Really Simple Syndication (RSS) feed or Cisco Notification Service. All security advisories on Cisco.com are displayed in chronological order, with the most recent advisories and updates appearing at the top of the page. Cisco Security Responses are posted to Cisco.com and sent only to the cust-security-announce@cisco.com email alias. This mailing list is an external list that allows subscribers to receive Cisco security announcements. To subscribe to this mailing list, send an email message to cust-security-announce-join@cisco.com. (The content of the message does not matter.) You will receive confirmation, instructions, and a list policy statement. Please note that requests must be sent to cust-security-announce-join@cisco.com and not to the cust-security-announce@cisco.com list itself. You must send messages from the account that will be subscribed to the list. We do not accept subscriptions for one account that are sent from a second account. You may also request access to this mailing list by sending an email message to psirt@cisco.com. RSS FeedsCisco security vulnerability information is also available via RSS feeds from Cisco.com. These feeds are free and do not require an active Cisco.com registration. For information on how to subscribe to the RSS feeds, visit the Cisco Security portal RSS Feeds page. Cisco Notification ServiceCisco Notification Service allows users to subscribe and receive important Cisco product and technology information. This service provides an improved unified subscription experience allowing users to choose the timing of notifications, as well as the notification delivery method (email message or RSS feed). The level of access will be determined by the subscriber's relationship with Cisco. Procedure for Creating a Notification
Public Relations or Press Queries Regarding Cisco Security Vulnerability InformationThe following table shows the Cisco press contacts for Cisco security vulnerability information.
Commitment to Product Security and Integrity at CiscoCisco product development practices specifically prohibit any intentional behaviors or product features which are designed to allow unauthorized device or network access, exposure of sensitive device information, or a bypass of security features or restrictions. These include, but are not limited to:
Cisco considers such product behaviors to be serious vulnerabilities. Cisco will address any issues of this nature with the highest priority and encourages all parties to report suspected vulnerabilities to the Cisco PSIRT for immediate investigation. Internal and external reports of these vulnerabilities will be managed and disclosed under the terms of the Cisco Security Vulnerability Policy. Cisco Secure Development PracticesCisco has developed and implemented the Cisco Secure Development Lifecycle (CSDL) as a comprehensive security program that combines:
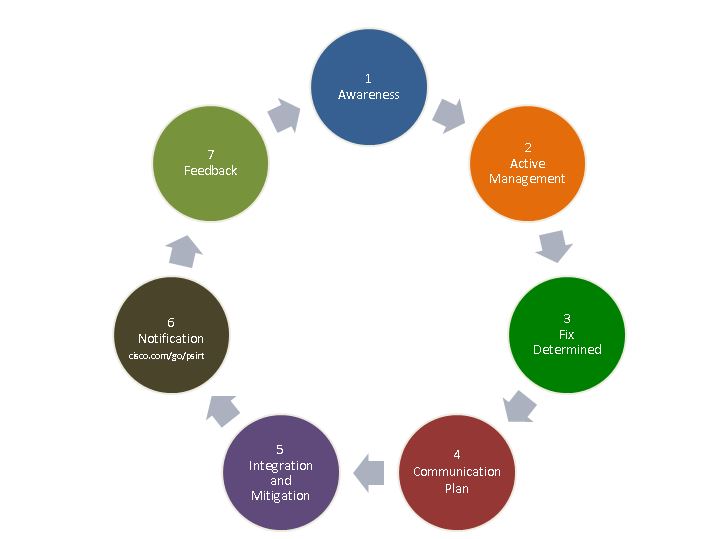
More information can be found on Cisco's CSDL website Cisco Product Security Incident Response ProcessThe following graphic illustrates the Cisco PSIRT process at a high level and provides an overview of the vulnerability lifecycle, disclosure, and resolution process. Figure 1. Cisco Product Security Incident Response Process
The following are the steps in the process illustrated in Figure 1:
The Cisco PSIRT investigates all reports regardless of the Cisco software code version or product lifecycle status. Issues will be prioritized based on the potential severity of the vulnerability and other environmental factors. Ultimately, the resolution of a reported incident may require upgrades to products that are under active support from Cisco. Throughout the investigative process, the Cisco PSIRT strives to work collaboratively with the source of the report (incident reporter) to confirm the nature of the vulnerability, gather required technical information, and ascertain appropriate remedial action. When the initial investigation is complete, results will be delivered to the incident reporter along with a plan for resolution and public disclosure. If the incident reporter disagrees with the conclusion, the Cisco PSIRT will make every effort to address those concerns. In the case of incidents whereby an agreement cannot be reached through the normal process, incident reporters may escalate by contacting the Cisco Technical Assistance Center and requesting the director of the global Cisco PSIRT team. During any investigation, the Cisco PSIRT manages all sensitive information on a highly confidential basis. Internal distribution is limited to those individuals who have a legitimate need to know and can actively assist in the resolution. Similarly, the Cisco PSIRT asks incident reporters to maintain strict confidentiality until complete resolutions are available for customers and have been published by the Cisco PSIRT on the Cisco website through the appropriate coordinated disclosure. With the agreement of the incident reporter, the Cisco PSIRT may acknowledge the reporters contribution during the public disclosure of the vulnerability. Cisco PSIRT works with third-party coordination centers such as CERT/CC, CERT-FI, JP-CERT, or CPNI to manage a coordinated industry disclosure for vulnerabilities reported to Cisco that may impact multiple vendors (for example, a generic protocol issue). In those situations, the Cisco PSIRT either will assist the incident reporter in contacting the coordination center, or may do so on that individual's behalf. If a reported vulnerability involves a vendor product, the Cisco PSIRT will notify the vendor directly, coordinate with the incident reporter, or engage a third-party coordination center. The Cisco PSIRT will coordinate with the incident reporter to determine the frequency of status updates of the incident and documentation updates. In the event Cisco becomes aware of a vulnerability that does not affect a Cisco product, but does involve another vendor's product, our policy for reporting vulnerabilities to vendors is followed. Assessing Security Risk — Common Vulnerability Scoring System and the Security Impact RatingCisco uses version 2.0 of the Common Vulnerability Scoring System (CVSS) as part of its standard process of evaluating reported potential vulnerabilities in Cisco products. The CVSS model uses three distinct measurements or scores that include base, temporal, and environmental calculations. Cisco will provide an evaluation of the base vulnerability score, and in some instances, will provide a temporal vulnerability score. End users are encouraged to compute the environmental score based on their network parameters. The combination of all three scores should be considered the final score, which represents a moment in time and is tailored to a specific environment. Organizations are advised to use this final score to prioritize responses in their own environments. In addition, Cisco uses the Security Impact Rating (SIR) as a way to categorize vulnerability severity in a simpler manner. The SIR is based on the CVSS base score, adjusted by PSIRT to account for Cisco-specific variables, and will be included in every Cisco Security Advisory. Cisco uses the following guidelines when determining which security publication will include a particular vulnerability:
Cisco reserves the right to deviate from this on an exception basis in the event that there are additional factors not properly captured in the CVSS score. If there is a security issue with a third-party software component that is used in a Cisco product, Cisco will typically use the CVSS score provided by the component creator. In some cases, Cisco may adjust the CVSS score to reflect the impact to the Cisco product. For more information about CVSS, visit the FIRST.org web site Third-Party Software VulnerabilitiesIf there is a vulnerability in a third-party software component that is used in a Cisco product, Cisco typically uses the CVSS score provided by the component creator. Cisco may adjust the CVSS score to reflect the impact to Cisco products. Cisco will consider a third-party vulnerability “high profile” if it meets the following criteria:
For high profile, third-party vulnerabilities, Cisco will begin assessing all potentially impacted products that have not reached End-of-Support (with priority given to those products that have not reached End-of-Software-Maintenance) and publish a Security Advisory within 24 hours of initial disclosure by the third-party. All known affected Cisco products will be detailed in an update to the initial Security Advisory, which will be published within 7 days of Cisco's initial disclosure. A Cisco bug will be created for each vulnerable product so that registered customers can view them via the Cisco Bug Search Toolkit. Third-party vulnerabilities that are not classified as high profile will be disclosed in a Release Note Enclosure (RNE). Types of Security PublicationsIn all security publications, Cisco discloses the minimum amount of information required for an end user to assess the impact of a vulnerability and any potential steps needed to protect their environment. Cisco does not provide vulnerability details that could enable someone to craft an exploit. Cisco provides the following types of security-related publications via the Cisco Security portal on Cisco.com.
If a Cisco Security Advisory references a bug, the bug entry in the Cisco Bug Search Tool will link to the relevant Cisco Security Advisory. The following table summarizes the methods used to notify customers about the aforementioned security publications. Exceptions may be made on a case-by-case basis to increase communication for a given document.
* For vulnerabilities with a Critical or High Security Impact Rating Communications PlanIf one or more of the following conditions exist, Cisco will publicly disclose Cisco Security Advisories:
All Cisco security publications are disclosed to customers and the public simultaneously. Cisco reserves the right to deviate from this policy on an exception basis to ensure access to Cisco.com for software patch availability. As documented in the Receiving Security Vulnerability Information from Cisco section of this document, Cisco delivers technical security information about software fixes in Cisco products and distributes product updates through several channels. Disclosure ScheduleCisco IOS SoftwareIn direct response to customer feedback, Cisco releases bundles of Cisco IOS Software Security Advisories at 1600 GMT on the fourth Wednesday in March and September each year. This schedule applies to the disclosure of Cisco IOS Software vulnerabilities and does not apply to the disclosure of vulnerabilities in other Cisco products. All Other ProductsCisco generally discloses Cisco Security Advisories at 1600 GMT on any given Wednesday. ExceptionsCisco reserves the right to publish an individual Cisco IOS Software or other product Security Advisory outside the published schedule. Conditions under which an out-of-cycle publication may occur include, but are not limited to, the following:
Incident Response EligibilityCustomers with service contracts receive incident response assistance for any incident in which a Cisco product plays a significant role, regardless of whether there is an identified problem with a Cisco product. Security Software UpdatesPSIRT will investigate and disclose vulnerabilities in Cisco products and services from the date of First Commercial Shipment (FCS) to the Last Day of Support. Cisco customers with service contracts that entitle them to regular software updates should obtain security fixes through their usual update channels, generally from the Cisco website. Cisco recommends contacting the TAC only with specific and imminent problems or questions.
Note: If the End of Security and Vulnerability Fixes milestone is not defined, the End of SW Maintenance and End of Engineering Support milestones will determine the last date Cisco Engineering will provide fixes. All aspects of this process are subject to change without notice and on a case-by-case basis. No particular level of response is guaranteed for any specific issue or class of issues. Last Updated: 2015 October 5 This document is part of the Cisco Security portal. Cisco provides the official information contained on the Cisco Security portal in English only. This document is provided on an "as is" basis and does not imply any kind of guarantee or warranty, including the warranties of merchantability or fitness for a particular use. Your use of the information on the document or materials linked from the document is at your own risk. Cisco reserves the right to change or update this document without notice at any time. |