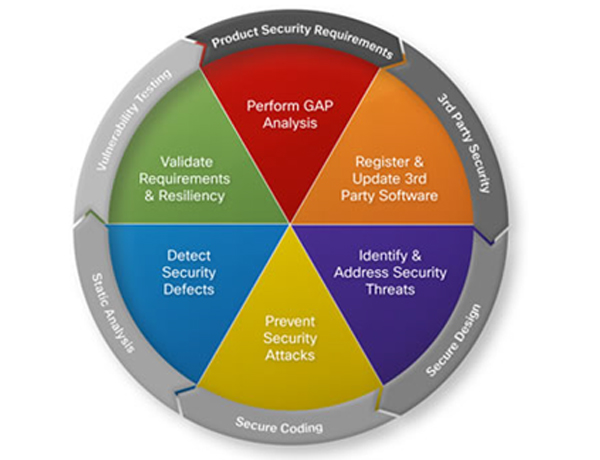
Product Security Requirements
Cisco products must meet two types of product security requirements:
- Internal requirements
- Market-based requirements
Cisco Internal Requirements
The Product Security Baseline (PSB) requirements define the security-related functionality, development process, and documentation expectations for all Cisco products.
The PSB focuses on important security aspects such as credential and key management, cryptography standards, antispoofing capabilities, integrity and tamper protection, and session/data/stream management and administration.
The PSB also characterizes the minimum requirements for resilience and robustness, sensitive data disposal, and logging and documentation of services and protocols.
Market-Based Requirements
Some markets and industries, such as finance, government, and medical, place additional security requirements on Cisco customers. These requirements typically exceed the Cisco baseline, and we strive to meet or surpass them.
Certification types may include:
- Common Criteria certification for all security and security-enabled products
- Cryptographic validation for any product containing encryption functionality
- IPv6 certification
- Department of Defense Unified Capabilities Approved Products List
- North America Electric Reliability Corporation - Critical Infrastructure Protection (NERC-CIP)
Third-Party Security
Many Cisco products incorporate third-party software, both commercial and open source. Consequently, Cisco products and customers are affected when vulnerabilities are found in third-party software.
To minimize the impact to you, our customers, we use two integrated tools to help us gain visibility into third-party software security threats:
- Central repository of intellectual property: Cisco internally tracks which Cisco products use third-party software through a single repository, providing a single point of control. The repository requires entry of any metadata associated with third-party software distributed outside the company.
- Notification of third-party software threats and vulnerabilities: Cisco can automatically alert product owners from a continuously updated list of third-party software threats and vulnerabilities. And the product teams can quickly act to investigate, reduce, or eliminate the issue.
Secure Design
A poor product design can open the way to vulnerabilities. At Cisco, our "secure design" approach requires two types of considerations:
- Design with security in mind
- Use threat modeling to validate the design's security
Designing with Security in Mind is an ongoing commitment to personal and professional improvement through:
- Training
- Applying the Product Security Baseline (PSB) design principles
- Consider other industry-standard secure design principles
- Be aware of common attack methods and design safeguards against them
- Take full advantage of designs and libraries that are known to be highly secure
- Consider all entry points
- Use the STRIDE approach to identify weaknesses in the design
We also reduce design-based vulnerabilities by considering known threats and attacks. With threat modeling, we:
- Follow the flow of data through the system.
- Identify trust boundaries where data may be compromised.
- Based on the data flow diagram, generate a list of threats and mitigations from a database of known threats, tailored by product type.
- Prioritize and implement mitigations to the identified threats.
Secure Coding
Veteran developers know that coding and implementation errors can create security vulnerabilities. While this knowledge comes with experience and training, Cisco requests that developers at all levels follow some best practices to help ensure threat-resistant code:
- Attend Secure Coding training
- Take full advantage of Safe Libraries, which are designed to reduce security issues
- Follow Secure Coding guidelines
- Include security checks in code reviews and when running Static Analysis
Secure Coding Standards
An essential element of secure coding is well-documented and enforceable coding standards. Our coding standards encourage programmers to follow a uniform set of rules and guidelines determined by the requirements of the project and organization.
Secure Analysis
A set of key security checkers maximize efficacy and reduce false positives of the Static Analysis tools in finding:
- Buffer overflow
- Tainted input
- Integer overflow
All Cisco development teams are expected to deploy these security checkers, review any warnings that are generated, and fix high-priority issues.
Vulnerability Testing
Vulnerability testing helps ensure that all Cisco products are tested consistently for security defects. First, we develop test cases for:
- All protocols that are implemented in the product
- Ports and services that are enabled by default
- Protocols, ports, and services that will be used in a typical customer configuration
Then, three regiments of Cisco SDL Vulnerability Testing evaluate the ability of a product to withstand probes and attacks:
- Protocol robustness
- Open source hacker tools
- Web application scanning
We use of a variety of security tools from multiple sources to execute an effective security test plan. Our Security Test Package combines them all into a single, easy-to-install collection of tools. This helps us to test for security defects in a consistent and repeatable manner.
Related Links
- Cisco Security Report
- Platform/Security Blogs
- Security Solutions
- Cisco Security Services
- Security & VPN
- Security Advisories
- Security Vulnerability Policy
- Cisco Trustworthy Systems