| 1. |
dnssec-intro [1] provides an introduction into DNSSEC. |
| 2. |
dnssec-records [2] introduces the new records for use in DNSSEC. |
| 3. |
dnssec-protocol [3] is the main document, which details all the protocol changes. |
 |
Verifiable secure—The data has signatures that are valid. |
 |
Verifiable unsecure*—The data has no signatures. |
 |
Old-style DNS—A non-DNSSEC lookup is done. |
| 1. |
Go to a root server and ask our question. |
| 2. |
The root server does not know anything about www.nlnetlabs.nl, but it does know something
about .nl. The root nameserver refers us to the .nl nameservers. This
kind of answer is called a referral.
|
| 3. |
| a. |
Notice that we have a key for .nl anchored. |
| b. |
Go to the .nl nameserver and ask the .nl DNSKEY. |
|
| 4. |
| a. |
Compare the two DNSKEYs. Continue with the secure lookup only if they match.
The .nl DNSKEY is now validated.
|
| b. |
Optionally, the RRSIG on the DNSKEY also can be checked. |
|
| 5. |
Ask a .nl nameserver our question. |
| 6. |
The .nl nameserver is also oblivious about www.nlnetlabs.nl, but it does
know something about nlnetlabs.nl. It returns a secure referral consisting of a DS record plus the
RRSIG and some nameservers.
|
| 7. |
The resolver now checks the signature on the DS record. If the signature is valid, the hash of the
nlnetlabs.nl zone key is ok. The nameservers in the referral do not have any signatures on
them.
The hash of the nlnetlabs.nl DNSKEY is validated with the .nl
DNSKEY.
|
| 8. |
Go to the nameserver as specified in the referral and ask for the nlnetlabs.nl DNSKEY. |
| 9. |
Hash the DNSKEY of nlnetlabs.nl and compare this hash with the hash in the DS record. If they match
continue with the secure lookup.
The nlnetlabs.nl DNSKEY is now validated.
|
| 10. |
Ask the nameserver of nlnetlabs.nl our question. |
| 11. |
The nameserver now responds with an answer consisting of the A record of www.nlnetlabs.nl and an
RRSIG made with the nlnetlabs.nl DNSKEY. |
| 12. |
The resolver now uses the already validated nlnetlabs.nl DNSKEY to check the RRSIG. If that
signature is valid the RR with the answer is ok and can be given to the application.
|
| 13. |
After these steps we find out that the address of www.nlnetlabs.nl is 213.154.224.1. We also know
it is not a spoofed answer.
|
| 1. |
The zone key is added to the zone file. |
| 2. |
The zone file is sorted. |
| 3. |
Each owner name (for example, a host name) in the zone gets a Next SECure (NSEC) record. (Refer to the section
"Authenticated Denial of Existence.")
|
| 4. |
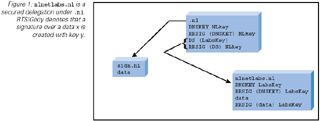
For each secured delegation, a DS record is added. |
| 5. |
The entire zone is then signed with the private key of the zone. Each authoritative RRset gets a signature, including the newly
generated NSEC records.
|
| 1. |
If a resolver asks information about b.nl, the nameserver tries to look up the record fails.
Instead it finds a.nl. It must then return: a.nl NSEC d.nl together with
the signature. The resolver must then be smart enough to process this information and conclude that
b.nl does not exist. If the signature is valid, we have an authenticated denial of
existence. These NSEC records together with their signatures are the major cause of the zone size increase in DNSSEC.
|