|
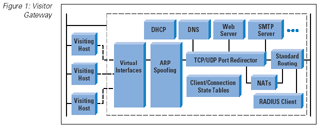
The visiting host is physically attached to the network by connecting to a twisted-pair Ethernet port.
|
 |
Visitors open their browser and attempt to load any page with the Hypertext Transfer Protocol (HTTP).
|
 |
Regardless of the specified URL, the browser loads a default page that requests authentication or billing information.
|
 |
When authenticated, the visitors now have general Internet access.
|
 |
An accounting record describing a visitor’s session is generated and processed by the service provider’s billing system,
resulting in a charge on either the visitor’s account or a corporate account.
|
 |
Authenticate users with traditional username/password—The visitor gateway may, in turn, use a Remote Access Dial-In User
Service (RADIUS) [7] authentication request to validate the user.
|
 |
Provide links within a “walled garden”—sites that can be visited without authentication—These sites are implemented with
either a Web proxy inside the gateway or access control lists effective on the individual visiting host’s virtual interface.
|
 |
Gather and validate credit card information through third-party credit card processing Web sites
|
 |
Offer visitors Web pages they can use to subscribe to services or to change service parameters
|