|
Connection: A logical client/server link that provides a suitable type of service. For SSL, such connections are peer-to-peer relationships. The connections are transient. Every connection is associated with one session.
|
 |
Session: An association between a client and a server. Sessions are created by the Handshake Protocol. Sessions define a set of cryptographic security parameters, which can be shared among multiple connections. Sessions are used to avoid the expensive negotiation of new security parameters for each connection. |
 |
Session identifier: An arbitrary byte sequence chosen by the server to identify an active or resumable session state.
|
 |
Peer certificate: An X509.v3 certificate of the peer. This element of the state may be null.
|
 |
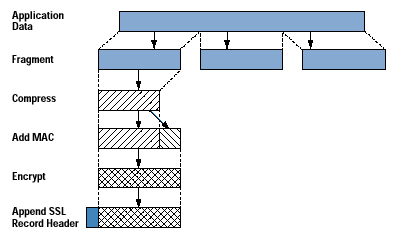
Compression method: The algorithm used to compress data prior to encryption.
|
 |
CipherSpec: Specifies the bulk data encryption algorithm (such as DES) and a hash algorithm (such as MD5 or SHA-1). It also defines cryptographic attributes such as the hash size.
|
 |
Master secret: 48-byte secret shared between the client and server.
|
 |
Is resumable: A flag indicating whether the session can be used to initiate new connections. |
 |
Server and client random: Byte sequences that are chosen by the server and client for each connection.
|
 |
Server write MAC secret: The secret key used in MAC operations on data sent by the server.
|
 |
Client write MAC secret: The secret key used in MAC operations on data sent by the client.
|
 |
Server write key: The conventional encryption key for data encrypted by the server and decrypted by the client.
|
 |
Client write key: The conventional encryption key for data encrypted by the client and decrypted by the server.
|
 |
Initialization vectors: When a block cipher in CBC mode is used, an initialization vector (IV) is maintained for each key. This field is first initialized by the SSL Handshake Protocol. Thereafter the final ciphertext block from each record is preserved for use as the IV for the next record.
|
 |
Sequence numbers: Each party maintains separate sequence numbers for transmitted and received messages for each connection. When a party sends or receives a change CipherSpec message, the appropriate sequence number is set to zero. |
 |
Content Type (8 bits): The higher-layer protocol used to process the enclosed fragment.
|
 |
Major Version (8 bits): Indicates major version of SSL in use. For SSLv3, the value is 3.
|
 |
Minor Version (8 bits): Indicates minor version in use. For SSLv3, the value is 0.
|
 |
Compressed Length (16 bits): The length in bytes of the plain-text fragment (or compressed fragment if compression is used). |
 |
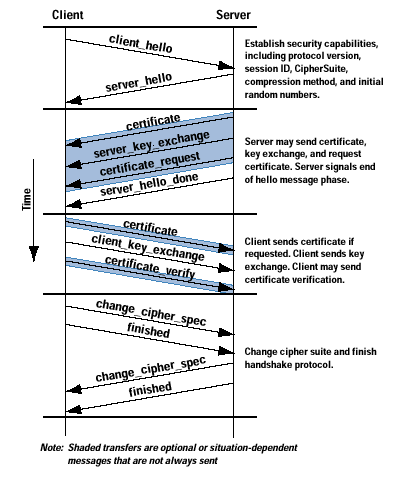
Version: The highest SSL version understood by the client.
|
 |
Random: A client-generated random structure, consisting of a 32-bit timestamp and 28 bytes generated by a secure random number generator. These values serve as nonces and are used during key exchange to prevent replay attacks.
|
 |
Session ID: A variable-length session identifier. A nonzero value indicates that the client wishes to update the parameters of an existing connection or create a new connection on this session. A zero value indicates that the client wishes to establish a new connection on a new session.
|
 |
CipherSuite: A list that contains the combinations of cryptographic algorithms supported by the client, in decreasing order of preference. Each element of the list (each CipherSuite) defines both a key exchange algorithm and a CipherSpec; these are discussed subsequently.
|
 |
Compression Method: A list of the compression methods the client supports. |
 |
RSA: The secret key is encrypted with the receiver's RSA public key. A public-key certificate for the receiver's key must be made available.
|
 |
Fixed Diffie-Hellman: This a Diffie-Hellman key exchange in which the server's certificate contains the Diffie-Hellman public parameters signed by the certificate authority (CA). That is, the public-key certificate contains the Diffie-Hellman public-key parameters. The client provides its Diffie-Hellman public key parameters either in a certificate, if client authentication is required, or in a key exchange message. This method results in a fixed secret key between two peers, based on the Diffie-Hellman calculation using the fixed public keys.
|
 |
Ephemeral Diffie-Hellman: This technique is used to create ephemeral (temporary, one-time) secret keys. In this case, the Diffie-Hellman public keys are exchanged, and signed using the sender's private RSA or DSS key. The receiver can use the corresponding public key to verify the signature. Certificates are used to authenticate the public keys. This option appears to be the most secure of the three Diffie-Hellman options because it results in a temporary, authenticated key.
|
 |
Anonymous Diffie-Hellman: The base Diffie-Hellman algorithm is used, with no authentication. That is, each side sends its public Diffie-Hellman parameters to the other, with no authentication. This approach is vulnerable to man-in-the-middle attacks, in which the attacker conducts anonymous Diffie-Hellman exchanges with both parties. |