Table Of Contents
Using the SESM Web Services Gateway
Web Services Gateway Introduction
Starting and Stopping the WSG Application
Running the Demonstration Client Interface
Using the SESM Web Services Gateway
This appendix describes how to install, start, and use the WSG application and sample client. Topics are:
•
Web Services Gateway Introduction
•
Starting and Stopping the WSG Application
•
Running the Demonstration Client Interface
Web Services Gateway Introduction
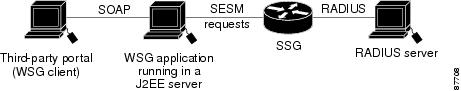
The Web Services Gateway (WSG) application provides a Simple Objects Access Protocol (SOAP)-based interface enabling third-party web portals and subscriber management systems to integrate with the SESM and SSG solution. Any client application can interface with SSG through the WSG using SOAP over HTTP communication. Figure B-1 shows WSG deployment.
Figure B-1 WSG Deployment
The WSG installation includes a web application configured to run in a Jetty container and a command-line client script for demonstration purposes. The WSG web application runs in RADIUS and SPE modes. It does not work in Demo mode.
In this first release, the WSG client interface enables access to the SSG for the following activities:
–
Authenticating, starting, and ending sessions on the SSG
–
Obtaining session status
–
Connecting and disconnecting services
This first release of WSG offers a preview of future development efforts. We invite interested parties to contact us through a Cisco account representative to discuss potential uses for WSG and participate in feature planning efforts for future releases.
Installing WSG
To install WSG:
1.
In the SESM installation program, choose the custom installation option.
2.
Check the WSG box in the list of custom installation options.
WSG is installed in the \install_dir\wsg directory.
Configuring WSG
WSG is configured by default to run in a Jetty container on port 8100.
To change the Jetty container configuration for the WSG application, edit the following file:
jettyconfigwsg.jetty.xmlTo change the WSG application configuration, you can either:
•
Access the MBeans through the WSG AgentView (port 8200)
•
Manually edit the following MBean configuration files:
wsgconfiglib.xmlsesm.xmldessauth.xmlFor explanations of the MBeans, see the Cisco Subscriber Edge Services Manager Web Portal Guide. The contents of the sesm.xml file is the same as the contents of nwsp.xml.
Starting and Stopping the WSG Application
The SESM installation process installs and configures the WSG application to run in a Jetty container. To start and stop WSG, run its startup or stop script:
jettybinWSGstartWSGstopThis script accepts all of the options and parameters that other SESM web applications use, including the mode option, which allows you to switch between LDAP, RADIUS, and Demo modes at run time. For more information, see the Cisco Subscriber Edge Services Manager Web Portal Guide
The installed default port for the WSG is 8100.
Running the Demonstration Client Interface
Note
The client interface is intended for demonstration purposes only. It can provide an understanding of the WSG interface and possibilities for development. Contact us through your Cisco account representative to discuss your development goals and deployment requirements regarding a WSG interface.
The demonstration client interface script provides command line access to the WSG using SOAP remote procedure calls (RPC). The script is located in:
wsgbinwsgClientTo start the client, enter the following command:
wsgClient [endpoint]
Where endpoint is always:
http://WSGhost:8100/services/SESM
If you do not supply the endpoint, the script provides command usage help. The wsgClient command-line prompt is:
wsg>
At the prompt, enter help to display available commands. At subsequent prompts, enter any of the commands.
Examples
The following examples show the WSG client command-line interface and output from various commands.
user1> wsgClient.sh http://localhost:8100/services/SESMwsg/webapp/WEB-INF/lib/auth.jar:wsg/webapp/WEB-INF/lib/authentication.jar:wsg/webapp/WEB-I NF/lib/axis.jar:wsg/webapp/WEB-INF/lib/com.cisco.sesm.contextlib.jar:wsg/webapp/WEB-INF/li b/com.cisco.sesm.lib.jar:wsg/webapp/WEB-INF/lib/com.cisco.sesm.wsg.jar:wsg/webapp/WEB-INF/ lib/commons-logging.jar:wsg/webapp/WEB-INF/lib/dess.jar:wsg/webapp/WEB-INF/lib/jaxrpc.jar: wsg/webapp/WEB-INF/lib/jmxri.jar:wsg/webapp/WEB-INF/lib/jmxtools.jar:wsg/webapp/WEB-INF/li b/log4j-1.2.4.jar:wsg/webapp/WEB-INF/lib/mail.jar:wsg/webapp/WEB-INF/lib/protect.jar:wsg/w ebapp/WEB-INF/lib/saaj.jar:wsg/webapp/WEB-INF/lib/sesm.jar:wsg/webapp/WEB-INF/lib/tt-bytec ode.jar:wsg/webapp/WEB-INF/lib/wsdl4j.jar:lib/lib/com.cisco.sesm.lib.jar:redist/axis/lib/a xis.jar:redist/axis/lib/commons-logging.jar:redist/axis/lib/jaxrpc.jar:redist/axis/lib/log 4j-1.2.4.jar:redist/axis/lib/mail.jar:redist/axis/lib/saaj.jar:redist/axis/lib/tt-bytecode .jar:redist/axis/lib/wsdl4j.jar:redist/jaxp/lib/crimson.jar:redist/jaxp/lib/jaxp.jar:redis t/jaxp/lib/xalan.jarwsg> helpact[ivateService] svc [user passwd] - Activate serviceauth[enticate] user passwd - Authenticate username/passworddea[ctivate] svc - Deactivate serviceend[session] - End the sessionget[status] - Get statush[elp] - This summaryhost[key] ip[/port][;name=value ..] - Set hostkeyq[uit] - Quit clientwsg> hostkey 121.121.122.3hostkey=121.121.122.3In the preceding command, 121.121.122.3 is the IP address of the subscriber. The SSG must be able to route this address. It uses the address to bind a downlink interface when it creates the edge session for the subscriber.
wsg> authenticate ug1-u1 cisco // username/password respectivelyauthenticate=truewsg> getIdentity user: ug1-u1Service proxy3: offService Chris-PT1: offService proxy2: ONService proxy1: offService tunnel7200uk7: offService ptSg2: offService ptSg1: offService pt2: offService pt1: offService SgMutexSelct1: offService sg1: offService tunnelNrp4: offService Chris-PT-Seq2: offService Chris-PT-Seq1: offService ?????: offService ptMutexSelect3: offService ptMutexSelect2: offService ptMutexSelect1: offwsg> act pt1activate pt1 = truewsg> getIdentity user: ug1-u1Service proxy3: offService Chris-PT1: offService proxy2: ONService proxy1: offService tunnel7200uk7: offService ptSg2: offService ptSg1: offService pt2: offService pt1: ONService SgMutexSelct1: offService sg1: offService tunnelNrp4: offService Chris-PT-Seq2: offService Chris-PT-Seq1: offService ?????: offService ptMutexSelect3: offService ptMutexSelect2: offService ptMutexSelect1: offwsg> dea pt1deactivate pt1wsg> act tunnelNrp4 cisco cisco // An example of activating authenticated tunnel serviceactivate tunnelNrp4 = truewsg> getIdentity user: ug1-u1Service proxy3: offService Chris-PT1: offService proxy2: ONService proxy1: offService tunnel7200uk7: offService ptSg2: offService ptSg1: offService pt2: offService pt1: offService SgMutexSelct1: offService sg1: offService tunnelNrp4: ONService Chris-PT-Seq2: offService Chris-PT-Seq1: offService ?????: offService ptMutexSelect3: offService ptMutexSelect2: offService ptMutexSelect1: offwsg> deactivate tunnelNrp4deactivate tunnelNrp4wsg> getIdentity user: ug1-u1Service proxy3: offService Chris-PT1: offService proxy2: ONService proxy1: offService tunnel7200uk7: offService ptSg2: offService ptSg1: offService pt2: offService pt1: offService SgMutexSelct1: offService sg1: offService tunnelNrp4: offService Chris-PT-Seq2: offService Chris-PT-Seq1: offService ?????: offService ptMutexSelect3: offService ptMutexSelect2: offService ptMutexSelect1: offwsg> endendSessionwsg> quittest-user-u10:165>

 Feedback
Feedback