Table Of Contents
Configuring Committed Access Rate
Committed Access Rate Configuration Task List
Configuring CAR and DCAR for All IP Traffic
Configuring CAR and DCAR Policies
Configuring a Class-Based DCAR Policy
CAR and DCAR Configuration Examples
Input and Output Rate Limiting on an Interface Example
Rate Limiting in an IXP Example
Rate Limiting by Access List Example
Configuring Committed Access Rate
This chapter describes the tasks for configuring committed access rate (CAR) and distributed CAR (DCAR).
For complete conceptual information about these features, see the section "Committed Access Rate" in the "Classification Overview" chapter and the section "Policing with CAR" in the "Policing and Shaping Overview" chapter in this book.
For a complete description of the CAR commands in this chapter, refer to the Cisco IOS Quality of Service Solutions Command Reference. To locate documentation of other commands that appear in this chapter, use the command reference master index or search online.
To identify the hardware platform or software image information associated with a feature, use the Feature Navigator on Cisco.com to search for information about the feature or refer to the software release notes for a specific release. For more information, see the "Identifying Supported Platforms" section in the "Using Cisco IOS Software" chapter in this book.
Note
CAR and DCAR can only be used with IP traffic. Non-IP traffic is not rate limited.
CAR and DCAR can be configured on an interface or subinterface. However, CAR and DCAR are not supported on the Fast EtherChannel, tunnel, or PRI interfaces, nor on any interface that does not support Cisco Express Forwarding (CEF).
CEF must be enabled on the interface before you configure CAR or DCAR.
CAR is not supported for Internetwork Packet Exchange (IPX) packets.
Committed Access Rate Configuration Task List
The CAR and DCAR services limit the input or output transmission rate on an interface or subinterface based on a flexible set of criteria. CAR is often configured on interfaces at the edge of a network to limit traffic into or out of the network.
CAR can rate limit traffic based on certain matching criteria, such as incoming interface, IP precedence, or IP access list. You configure the actions that CAR will take when traffic conforms to or exceeds the rate limit.
You can set CAR rate policies that are associated with one of the following:
•
All IP traffic
•
IP precedence
•
MAC address
•
IP access list, both standard and extended. Matching to IP access lists is more processor-intensive than matching based on other criteria.
Each interface can have multiple CAR policies, corresponding to different types of traffic. For example, low priority traffic may be limited to a lower rate than high-priority traffic. With multiple rate policies, the router examines each policy in the order entered until the packet matches. If a match is not found, the default action is to send.
The rate policies can be independent; each rate policy deals with a different type of traffic. Alternatively, rate policies can be cascading; a packet can be compared to multiple different rate policies in succession. You can configure up to 100 rate policies on a subinterface.
Note
Because of the linear search for the matching rate-limit statement, the CPU load increases with the number of rate policies.
To configure CAR, perform the tasks described in the following sections. The tasks in the first two sections are required; the tasks in the remaining sections are optional.
•
Configuring CAR and DCAR for All IP Traffic (Required)
•
Configuring CAR and DCAR Policies (Required)
•
Configuring a Class-Based DCAR Policy (Optional)
•
Monitoring CAR and DCAR (Optional)
See the end of this chapter for the section "CAR and DCAR Configuration Examples."
Configuring CAR and DCAR for All IP Traffic
To configure CAR (or DCAR on Cisco 7000 series routers with RSP7000 or Cisco 7500 series routers with a VIP2-40 or greater interface processor) for all IP traffic, use the following commands beginning in global configuration mode:
Step 1
Router(config)# interface interface-type interface-number
Specifies the interface or subinterface. This command puts the router in interface configuration mode.
Step 2
Router(config-if)# rate-limit {input | output} bps burst-normal burst-max conform-action action exceed-action action
Specifies a basic CAR policy for all IP traffic. See Table 7 for a description of conform and exceed action keywords.
Basic CAR and DCAR functionality requires that the following criteria be defined:
•
Packet direction, incoming or outgoing.
•
An average rate, determined by a long-term average of the transmission rate. Traffic that falls under this rate will always conform.
•
A normal burst size, which determines how large traffic bursts can be before some traffic is considered to exceed the rate limit.
•
An excess burst size (Be). Traffic that falls between the normal burst size and the Excess Burst size exceeds the rate limit with a probability that increases as the burst size increases. CAR propagates bursts. It does no smoothing or shaping of traffic.
Conform and exceed actions are described in Table 7.
See the sections "Configuring CAR and DCAR Policies" and "Configuring a Class-Based DCAR Policy" to understand how to configure other CAR and DCAR policy options. See the sections "Subrate IP Services Example" and "Input and Output Rate Limiting on an Interface Example" for examples of how to configure CAR for all IP traffic.
Configuring CAR and DCAR Policies
To configure CAR (or DCAR on Cisco 7000 series routers with the RSP7000 or Cisco 7500 series routers with a VIP2-40 or greater interface processor), use the following commands beginning in interface configuration mode. The tasks listed in this section are required unless noted as optional.
Step 1
Router(config-if)# interface interface-type interface-number
Specifies the interface or subinterface. This command puts the router in interface configuration mode.
Step 2
Router(config-if)# rate-limit {input | output} [access-group [rate-limit] acl-index] bps burst-normal burst-max conform-action action exceed-action action
Specifies the rate policy for each particular class of traffic. See Table 7 for a description of the rate-limit command action keywords. Repeat this command for each different class of traffic.
Step 3
Router(config-if) exit
(Optional) Returns to global configuration mode.
Note
This change in configuration mode is needed only if you complete optional Step 4 or Step 5.
Step 4
Router(config)# access-list rate-limit acl-index {precedence | mac-address | mask prec-mask}
(Optional) Specifies a rate-limited access list. Repeat this command if you wish to specify a new access list.
Step 5
Router(config)# access-list acl-index {deny | permit} source [source-wildcard]
or
Router(config)# access-list acl-index {deny | permit} protocol source source-wildcard destination destination-wildcard [precedence precedence][tos tos] [log]
(Optional) Specifies a standard or extended access list. Repeat this command to further configure the access list or specify a new access list.
The following sections describe requirements for specific policies.
IP Precedence or MAC Address
Use the access-list rate-limit command to classify packets using either IP Precedence or MAC addresses. You can then apply CAR policies using the rate-limit command to individual rate-limited access lists. Packets with different IP precedences or MAC addresses are treated differently by the CAR service. See the section "Rate Limiting in an IXP Example" for an example of how to configure a CAR policy using MAC addresses.
IP Access List
Use the access-list command to define CAR policy based on an access list. The acl-index argument is an access list number. Use a number from 1 to 99 to classify packets by precedence or precedence mask. Use a number from 100 to 199 to classify by MAC address.
Note
If an access list is not present, the rate-limit command will act as if no access list is defined and all traffic will be rate limited accordingly.
See the section "Rate Limiting by Access List Example" for an example of how to configure a CAR policy using IP access lists.
Configuring a Class-Based DCAR Policy
When you configure DCAR on Cisco 7000 series routers with RSP7000 or Cisco 7500 series routers with a VIP2-40 or greater interface processor, you can classify packets by group, to allow you to partition your network into multiple priority levels or classes of service. This classification is achieved by setting IP precedences based on different criteria for use by other QoS features such as Weighted Random Early Detection (WRED) or weighted fair queueing (WFQ).
To configure a class-based DCAR policy, use the following commands beginning in interface configuration mode. The tasks listed in this section are required unless noted as optional.
Step 1
Router(config-if)# interface interface-type interface-number
Specifies the interface or subinterface. This command puts the router in interface configuration mode.
Step 2
Router(config-if)# rate-limit {input | output} [access-group [rate-limit] acl-index] bps burst-normal burst-max conform-action action exceed-action action
Specifies the rate policy for each particular class of traffic. See Table 7 for a description of the rate-limit command action keywords. Repeat this command for each different class of traffic.
Step 3
Router(config-if)# random-detect precedence precedence min-threshold max-threshold mark-prob-denominator
Configures WRED and specifies parameters for packets with specific IP Precedence.
Step 4
Router(config-if)# access-list acl-index {deny | permit} source [source-wildcard]
or
Router(config-if)# access-list acl-index {deny | permit} protocol source source-wildcard destination destination-wildcard [precedence precedence]
[tos tos] [log](Optional) Specifies a standard or extended access list. Repeat this command to further configure the access list or specify a new access list.
Monitoring CAR and DCAR
To monitor CAR and DCAR services in your network, use the following commands in EXEC mode, as needed:
CAR and DCAR Configuration Examples
The following sections provide CAR and DCAR configuration examples:
•
Input and Output Rate Limiting on an Interface Example
•
Rate Limiting in an IXP Example
•
Rate Limiting by Access List Example
For information on how to configure CAR and DCAR, see the section "Committed Access Rate Configuration Task List" in this chapter.
Subrate IP Services Example
The following example illustrates how to configure a basic CAR policy that allows all IP traffic. In the example, the network operator delivers a physical T3 link to the customer, but offers a less expensive 15 Mbps subrate service. The customer pays only for the subrate bandwidth, which can be upgraded with additional access bandwidth based on demand. The CAR policy limits the traffic rate available to the customer and delivered to the network to the agreed upon rate limit, plus the ability to temporarily burst over the limit.
interface hssi 0/0/0rate-limit output 15000000 2812500 5625000 conform-action transmit exceed-action dropip address 10.1.0.9 255.255.255.0Input and Output Rate Limiting on an Interface Example
In this example, a customer is connected to an Internet service provider (ISP) by a T3 link. The ISP wants to rate limit transmissions from the customer to 15 Mbps of the 45 Mbps. In addition, the customer is allowed to send bursts of 2,812,500 bytes. All packets exceeding this limit are dropped. The following commands are configured on the High-Speed Serial Interface (HSSI) of the ISP connected to the customer:
interface Hssi0/0/0description 45Mbps to R1rate-limit input 15000000 2812500 2812500 conform-action transmit exceed-action dropip address 200.200.14.250 255.255.255.252rate-limit output 15000000 2812500 2812500 conform-action transmit exceed-action dropThe following sample output shows how to verify the configuration and monitor CAR statistics using the show interfaces rate-limit command:
Router# show interfaces hssi 0/0/0 rate-limitHssi0/0/0 45Mbps to R1Inputmatches: all trafficparams: 15000000 bps, 2812500 limit, 2812500 extended limitconformed 8 packets, 428 bytes; action: transmitexceeded 0 packets, 0 bytes; action: droplast packet: 8680ms ago, current burst: 0 byteslast cleared 00:03:59 ago, conformed 0 bps, exceeded 0 bpsOutputmatches: all trafficparams: 15000000 bps, 2812500 limit, 2812500 extended limitconformed 0 packets, 0 bytes; action: transmitexceeded 0 packets, 0 bytes; action: droplast packet: 8680ms ago, current burst: 0 byteslast cleared 00:03:59 ago, conformed 0 bps, exceeded 0 bpsRate Limiting in an IXP Example
The following example uses rate limiting to control traffic in an Internet Exchange Point (IXP). Because an IXP comprises many neighbors around an FDDI ring, MAC address rate-limited access lists are used to control traffic from a particular ISP. Traffic from one ISP (at MAC address 00e0.34b0.7777) is compared to a rate limit of 80 Mbps of the 100 Mbps available on the FDDI connection. Traffic that conforms to this rate is sent. Nonconforming traffic is dropped.
interface Fddi2/1/0rate-limit input access-group rate-limit 100 80000000 15000000 30000000 conform-action transmit exceed-action dropip address 200.200.6.1 255.255.255.0!access-list rate-limit 100 00e0.34b0.7777The following sample output shows how to verify the configuration and monitor the CAR statistics using the show interfaces rate-limit command:
Router# show interfaces fddi2/1/0 rate-limitFddi2/1/0Inputmatches: access-group rate-limit 100params: 800000000 bps, 15000000 limit, 30000000 extended limitconformed 0 packets, 0 bytes; action: transmitexceeded 0 packets, 0 bytes; action: droplast packet: 4737508ms ago, current burst: 0 byteslast cleared 01:05:47 ago, conformed 0 bps, exceeded 0 bpsRate Limiting by Access List Example
The following example shows how CAR can be used to limit the rate by application to ensure capacity for other traffic including mission-critical applications:
•
All World Wide Web traffic is sent. However, the IP precedence for Web traffic that conforms to the first rate policy is set to 5. For nonconforming Web traffic, the IP precedence is set to 0 (best effort).
•
File Transfer Protocol (FTP) traffic is sent with an IP precedence of 5 if it conforms to the second rate policy. If the FTP traffic exceeds the rate policy, it is dropped.
•
Any remaining traffic is limited to 8 Mbps, with a normal burst size of 16,000 bytes and an Excess Burst size of 24,000 bytes. Traffic that conforms is sent with an IP precedence of 5. Traffic that does not conform is dropped.
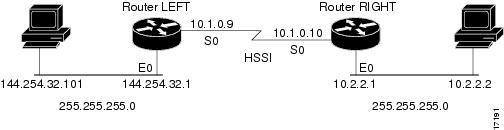
Figure 5 illustrates the configuration. Notice that two access lists are created to classify the Web and FTP traffic so that they can be handled separately by CAR.
Figure 5 Rate Limiting by Access List
Router LEFT Configuration
interface Hssi0/0/0description 45Mbps to R2rate-limit output access-group 101 20000000 3750000 7500000 conform-action set-prec-transmit 5 exceed-action set-prec-transmit 0rate-limit output access-group 102 10000000 1875000 3750000 conform-actionset-prec-transmit 5 exceed-action droprate-limit output 8000000 1500000 3000000 conform-action set-prec-transmit 5exceed-action dropip address 10.1.0.9 255.255.255.0!access-list 101 permit tcp any any eq wwwaccess-list 102 permit tcp any any eq ftpThe following sample output shows how to verify the configuration and monitor CAR statistics using the show interfaces rate-limit command:
Router# show interfaces hssi 0/0/0 rate-limitHssi0/0/0 45Mbps to R2Inputmatches: access-group 101params: 20000000 bps, 3750000 limit, 7500000 extended limitconformed 3 packets, 189 bytes; action: set-prec-transmit 5exceeded 0 packets, 0 bytes; action: set-prec-transmit 0last packet: 309100ms ago, current burst: 0 byteslast cleared 00:08:00 ago, conformed 0 bps, exceeded 0 bpsmatches: access-group 102params: 10000000 bps, 1875000 limit, 3750000 extended limitconformed 0 packets, 0 bytes; action: set-prec-transmit 5exceeded 0 packets, 0 bytes; action: droplast packet: 19522612ms ago, current burst: 0 byteslast cleared 00:07:18 ago, conformed 0 bps, exceeded 0 bpsmatches: all trafficparams: 8000000 bps, 1500000 limit, 3000000 extended limitconformed 5 packets, 315 bytes; action: set-prec-transmit 5exceeded 0 packets, 0 bytes; action: droplast packet: 9632ms ago, current burst: 0 byteslast cleared 00:05:43 ago, conformed 0 bps, exceeded 0 bps

 Feedback
Feedback